Istio 8주차 정리
⚙️ 실습 환경 구성
1. YAML 템플릿 파일 다운로드
1
curl -O https://s3.ap-northeast-2.amazonaws.com/cloudformation.cloudneta.net/K8S/istio-8w.yaml
✅ 출력
1
2
3
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 8744 100 8744 0 0 98738 0 --:--:-- --:--:-- --:--:-- 99363
2. CloudFormation 스택 배포
(1) Step 1: 템플릿 파일 업로드 (istio-8w.yaml 선택) 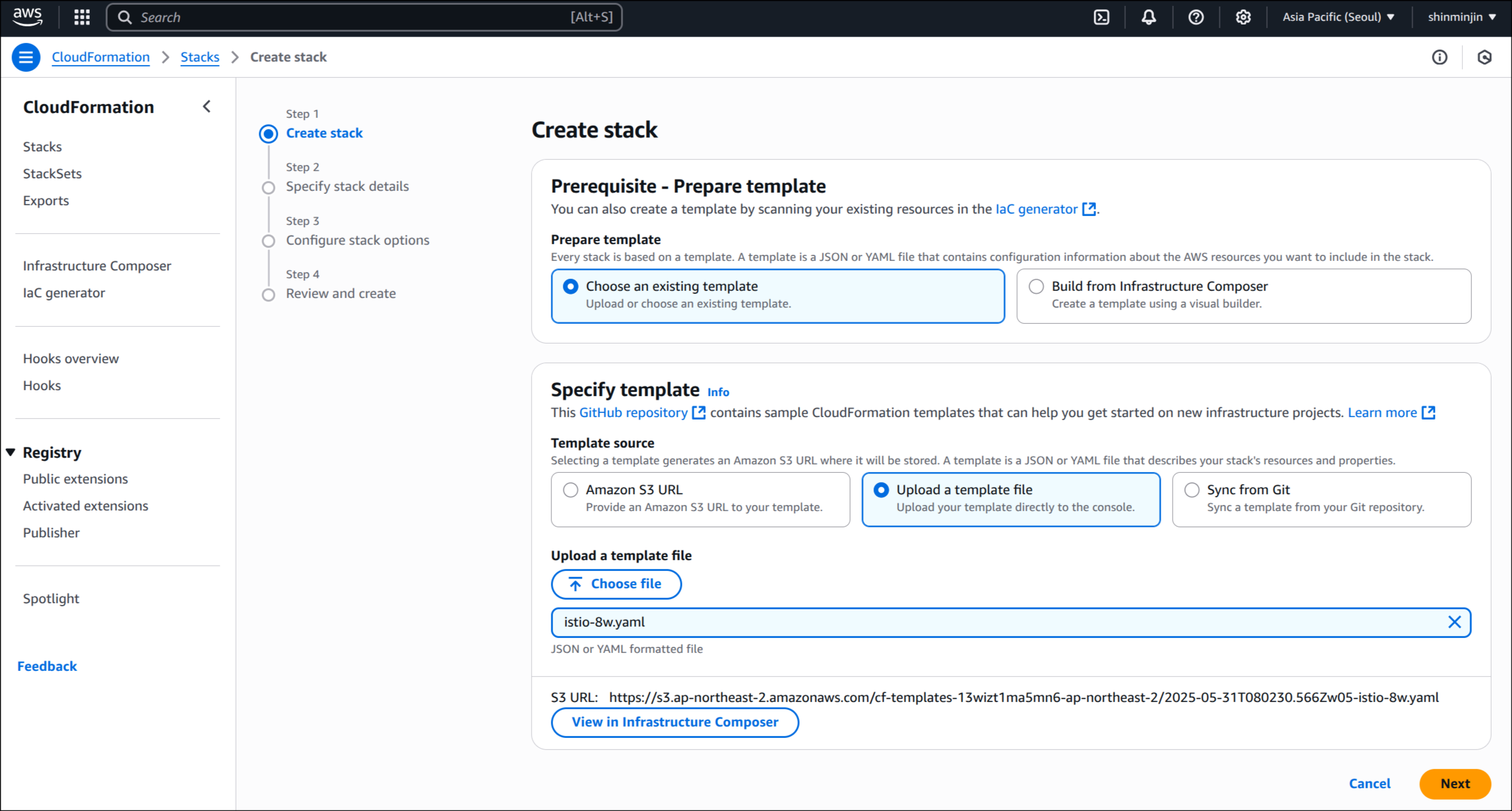
(2) Step 2: SgIngressSshCidr는 본인 공인 IP, 이미지: Ubuntu 22.04 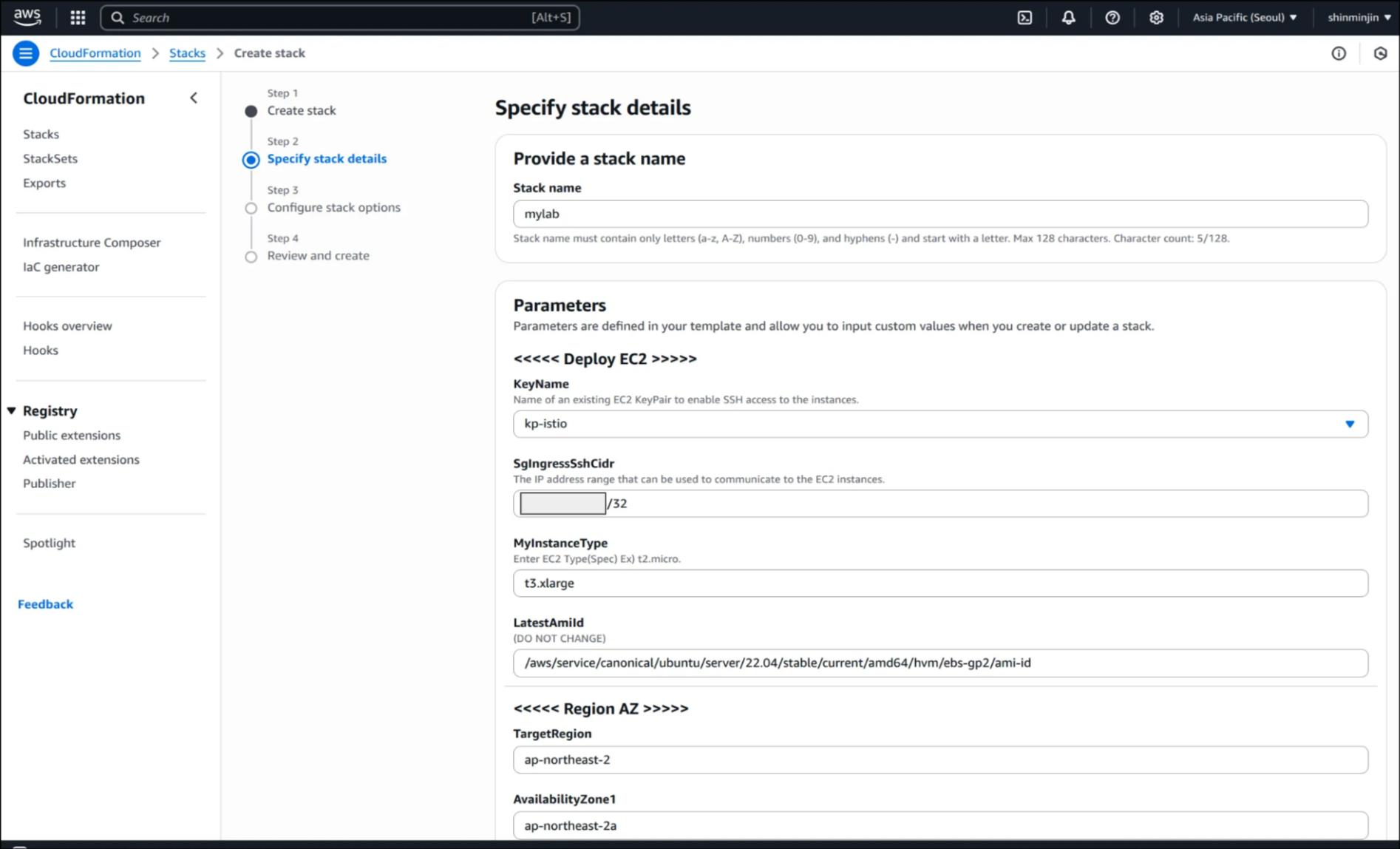
(3) Step 3~4: 기본값 설정 후 스택 배포 완료 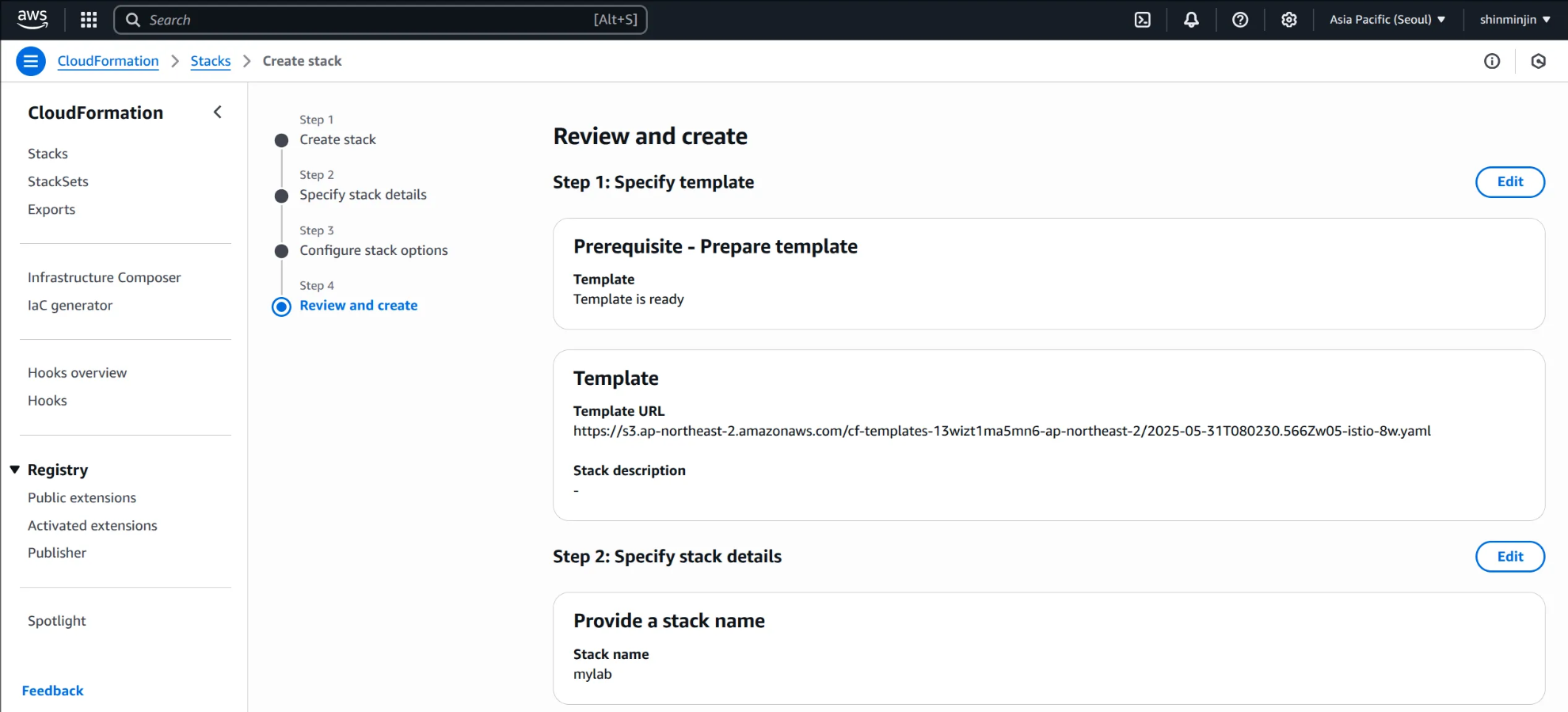
3. EC2 공인 IP 주소 확인
1
aws ec2 describe-instances --query "Reservations[*].Instances[*].{PublicIPAdd:PublicIpAddress,InstanceName:Tags[?Key=='Name']|[0].Value,Status:State.Name}" --filters Name=instance-state-name,Values=running --output text
✅ 출력
1
2
k3s-s 3.35.133.203 running
forum-vm 3.36.50.171 running
4. k3s-s EC2 SSH 접속 (약 3~5분 후 접속)
1
ssh -i kp-istio.pem ubuntu@$(aws cloudformation describe-stacks --stack-name mylab --query 'Stacks[*].Outputs[0].OutputValue' --output text --region ap-northeast-2)
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 6.8.0-1029-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat May 31 17:30:27 KST 2025
System load: 0.09 Processes: 133
Usage of /: 8.5% of 28.89GB Users logged in: 0
Memory usage: 4% IPv4 address for ens5: 192.168.10.10
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
21 updates can be applied immediately.
18 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
New release '24.04.2 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Sat May 31 17:30:28 2025 from 182.230.60.93
(⎈|default:N/A) root@k3s-s:~#
5. K3s 클러스터 상태 확인
1
2
(⎈|default:N/A) root@k3s-s:~# kc get node -owide
hostnamectl
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
k3s-s Ready control-plane,master 22m v1.28.15+k3s1 192.168.10.10 <none> Ubuntu 22.04.5 LTS 6.8.0-1029-aws containerd://1.7.22-k3s1.28
Static hostname: k3s-s
Icon name: computer-vm
Chassis: vm
Machine ID: ec22xxxxxxxxxxxxxxxxxxxxxxxxxxxx
Boot ID: 9f136xxxxxxxxxxxxxxxxxxxxxxxxxxx
Virtualization: amazon
Operating System: Ubuntu 22.04.5 LTS
Kernel: Linux 6.8.0-1029-aws
Architecture: x86-64
Hardware Vendor: Amazon EC2
Hardware Model: t3.xlarge
6. (옵션) krew 설치
1
2
3
(⎈|default:N/A) root@k3s-s:~# wget -O /root/krew-linux_amd64.tar.gz https://github.com/kubernetes-sigs/krew/releases/download/v0.4.4/krew-linux_amd64.tar.gz
tar zxvf /root/krew-linux_amd64.tar.gz
/root/krew-linux_amd64 install krew
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
--2025-05-31 17:35:29-- https://github.com/kubernetes-sigs/krew/releases/download/v0.4.4/krew-linux_amd64.tar.gz
Resolving github.com (github.com)... 20.200.245.247
Connecting to github.com (github.com)|20.200.245.247|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/140747457/16532a8a-5c3e-4ad8-a1f7-5cdcdbea5e39?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=releaseassetproduction%2F20250531%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20250531T083529Z&X-Amz-Expires=300&X-Amz-Signature=937ee121375692109f5d3e546ea0f619fbe7812e7cbef56c3b5bb59c9131511a&X-Amz-SignedHeaders=host&response-content-disposition=attachment%3B%20filename%3Dkrew-linux_amd64.tar.gz&response-content-type=application%2Foctet-stream [following]
--2025-05-31 17:35:29-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/140747457/16532a8a-5c3e-4ad8-a1f7-5cdcdbea5e39?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=releaseassetproduction%2F20250531%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20250531T083529Z&X-Amz-Expires=300&X-Amz-Signature=937ee121375692109f5d3e546ea0f619fbe7812e7cbef56c3b5bb59c9131511a&X-Amz-SignedHeaders=host&response-content-disposition=attachment%3B%20filename%3Dkrew-linux_amd64.tar.gz&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.108.133, 185.199.109.133, 185.199.110.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.108.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4551185 (4.3M) [application/octet-stream]
Saving to: ‘/root/krew-linux_amd64.tar.gz’
/root/krew-linux_amd64.tar.gz 100%[====================================================================>] 4.34M --.-KB/s in 0.03s
2025-05-31 17:35:30 (144 MB/s) - ‘/root/krew-linux_amd64.tar.gz’ saved [4551185/4551185]
./LICENSE
./krew-linux_amd64
Adding "default" plugin index from https://github.com/kubernetes-sigs/krew-index.git.
Updated the local copy of plugin index.
Installing plugin: krew
Installed plugin: krew
\
| Use this plugin:
| kubectl krew
| Documentation:
| https://krew.sigs.k8s.io/
| Caveats:
| \
| | krew is now installed! To start using kubectl plugins, you need to add
| | krew's installation directory to your PATH:
| |
| | * macOS/Linux:
| | - Add the following to your ~/.bashrc or ~/.zshrc:
| | export PATH="${KREW_ROOT:-$HOME/.krew}/bin:$PATH"
| | - Restart your shell.
| |
| | * Windows: Add %USERPROFILE%\.krew\bin to your PATH environment variable
| |
| | To list krew commands and to get help, run:
| | $ kubectl krew
| | For a full list of available plugins, run:
| | $ kubectl krew search
| |
| | You can find documentation at
| | https://krew.sigs.k8s.io/docs/user-guide/quickstart/.
| /
/
7. Krew PATH 환경 변수 설정 및 플러그인 설치
1
2
3
(⎈|default:N/A) root@k3s-s:~# export PATH="$PATH:/root/.krew/bin"
(⎈|default:N/A) root@k3s-s:~# echo 'export PATH="$PATH:/root/.krew/bin:/root/go/bin"' >> /etc/profile
kubectl krew install get-all neat view-secret rolesum pexec
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
Updated the local copy of plugin index.
Installing plugin: get-all
Installed plugin: get-all
\
| Use this plugin:
| kubectl get-all
| Documentation:
| https://github.com/corneliusweig/ketall
/
WARNING: You installed plugin "get-all" from the krew-index plugin repository.
These plugins are not audited for security by the Krew maintainers.
Run them at your own risk.
Installing plugin: neat
Installed plugin: neat
\
| Use this plugin:
| kubectl neat
| Documentation:
| https://github.com/itaysk/kubectl-neat
/
WARNING: You installed plugin "neat" from the krew-index plugin repository.
These plugins are not audited for security by the Krew maintainers.
Run them at your own risk.
Installing plugin: view-secret
Installed plugin: view-secret
\
| Use this plugin:
| kubectl view-secret
| Documentation:
| https://github.com/elsesiy/kubectl-view-secret
/
WARNING: You installed plugin "view-secret" from the krew-index plugin repository.
These plugins are not audited for security by the Krew maintainers.
Run them at your own risk.
Installing plugin: rolesum
Installed plugin: rolesum
\
| Use this plugin:
| kubectl rolesum
| Documentation:
| https://github.com/Ladicle/kubectl-rolesum
/
WARNING: You installed plugin "rolesum" from the krew-index plugin repository.
These plugins are not audited for security by the Krew maintainers.
Run them at your own risk.
Installing plugin: pexec
Installed plugin: pexec
\
| Use this plugin:
| kubectl pexec
| Documentation:
| https://github.com/ssup2/kpexec
| Caveats:
| \
| | pexec requires the privileges to run privileged pods with hostPID.
| /
/
WARNING: You installed plugin "pexec" from the krew-index plugin repository.
These plugins are not audited for security by the Krew maintainers.
Run them at your own risk.
8. termshark 설치 명령 실행 (k3s-s)
1
(⎈|default:N/A) root@k3s-s:~# DEBIAN_FRONTEND=noninteractive apt install termshark -y
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
...
Preconfiguring packages ...
Selecting previously unselected package libbcg729-0:amd64.
(Reading database ... 66126 files and directories currently installed.)
Preparing to unpack .../00-libbcg729-0_1.1.1-2_amd64.deb ...
Unpacking libbcg729-0:amd64 (1.1.1-2) ...
Selecting previously unselected package libdeflate0:amd64.
Preparing to unpack .../01-libdeflate0_1.10-2_amd64.deb ...
Unpacking libdeflate0:amd64 (1.10-2) ...
Selecting previously unselected package libjpeg-turbo8:amd64.
Preparing to unpack .../02-libjpeg-turbo8_2.1.2-0ubuntu1_amd64.deb ...
Unpacking libjpeg-turbo8:amd64 (2.1.2-0ubuntu1) ...
Selecting previously unselected package libjpeg8:amd64.
Preparing to unpack .../03-libjpeg8_8c-2ubuntu10_amd64.deb ...
Unpacking libjpeg8:amd64 (8c-2ubuntu10) ...
Selecting previously unselected package liblua5.2-0:amd64.
Preparing to unpack .../04-liblua5.2-0_5.2.4-2_amd64.deb ...
Unpacking liblua5.2-0:amd64 (5.2.4-2) ...
Selecting previously unselected package libsmi2ldbl:amd64.
Preparing to unpack .../05-libsmi2ldbl_0.4.8+dfsg2-16_amd64.deb ...
Unpacking libsmi2ldbl:amd64 (0.4.8+dfsg2-16) ...
Selecting previously unselected package libjbig0:amd64.
Preparing to unpack .../06-libjbig0_2.1-3.1ubuntu0.22.04.1_amd64.deb ...
Unpacking libjbig0:amd64 (2.1-3.1ubuntu0.22.04.1) ...
Selecting previously unselected package libwebp7:amd64.
Preparing to unpack .../07-libwebp7_1.2.2-2ubuntu0.22.04.2_amd64.deb ...
Unpacking libwebp7:amd64 (1.2.2-2ubuntu0.22.04.2) ...
Selecting previously unselected package libtiff5:amd64.
Preparing to unpack .../08-libtiff5_4.3.0-6ubuntu0.10_amd64.deb ...
Unpacking libtiff5:amd64 (4.3.0-6ubuntu0.10) ...
Selecting previously unselected package libspandsp2:amd64.
Preparing to unpack .../09-libspandsp2_0.0.6+dfsg-2_amd64.deb ...
Unpacking libspandsp2:amd64 (0.0.6+dfsg-2) ...
Selecting previously unselected package libspeexdsp1:amd64.
Preparing to unpack .../10-libspeexdsp1_1.2~rc1.2-1.1ubuntu3_amd64.deb ...
Unpacking libspeexdsp1:amd64 (1.2~rc1.2-1.1ubuntu3) ...
Selecting previously unselected package libssh-gcrypt-4:amd64.
Preparing to unpack .../11-libssh-gcrypt-4_0.9.6-2ubuntu0.22.04.3_amd64.deb ...
Unpacking libssh-gcrypt-4:amd64 (0.9.6-2ubuntu0.22.04.3) ...
Selecting previously unselected package libwireshark-data.
Preparing to unpack .../12-libwireshark-data_3.6.2-2_all.deb ...
Unpacking libwireshark-data (3.6.2-2) ...
Selecting previously unselected package libc-ares2:amd64.
Preparing to unpack .../13-libc-ares2_1.18.1-1ubuntu0.22.04.3_amd64.deb ...
Unpacking libc-ares2:amd64 (1.18.1-1ubuntu0.22.04.3) ...
Selecting previously unselected package libsbc1:amd64.
Preparing to unpack .../14-libsbc1_1.5-3build2_amd64.deb ...
Unpacking libsbc1:amd64 (1.5-3build2) ...
Selecting previously unselected package libsnappy1v5:amd64.
Preparing to unpack .../15-libsnappy1v5_1.1.8-1build3_amd64.deb ...
Unpacking libsnappy1v5:amd64 (1.1.8-1build3) ...
Selecting previously unselected package libwsutil13:amd64.
Preparing to unpack .../16-libwsutil13_3.6.2-2_amd64.deb ...
Unpacking libwsutil13:amd64 (3.6.2-2) ...
Selecting previously unselected package libwiretap12:amd64.
Preparing to unpack .../17-libwiretap12_3.6.2-2_amd64.deb ...
Unpacking libwiretap12:amd64 (3.6.2-2) ...
Selecting previously unselected package libwireshark15:amd64.
Preparing to unpack .../18-libwireshark15_3.6.2-2_amd64.deb ...
Unpacking libwireshark15:amd64 (3.6.2-2) ...
Selecting previously unselected package wireshark-common.
Preparing to unpack .../19-wireshark-common_3.6.2-2_amd64.deb ...
Unpacking wireshark-common (3.6.2-2) ...
Selecting previously unselected package tshark.
Preparing to unpack .../20-tshark_3.6.2-2_amd64.deb ...
Unpacking tshark (3.6.2-2) ...
Selecting previously unselected package termshark.
Preparing to unpack .../21-termshark_2.2.0-2ubuntu0.22.04.3_amd64.deb ...
Unpacking termshark (2.2.0-2ubuntu0.22.04.3) ...
Setting up libssh-gcrypt-4:amd64 (0.9.6-2ubuntu0.22.04.3) ...
Setting up libsbc1:amd64 (1.5-3build2) ...
Setting up libbcg729-0:amd64 (1.1.1-2) ...
Setting up libdeflate0:amd64 (1.10-2) ...
Setting up libc-ares2:amd64 (1.18.1-1ubuntu0.22.04.3) ...
Setting up libjbig0:amd64 (2.1-3.1ubuntu0.22.04.1) ...
Setting up libsnappy1v5:amd64 (1.1.8-1build3) ...
Setting up libsmi2ldbl:amd64 (0.4.8+dfsg2-16) ...
Setting up libwsutil13:amd64 (3.6.2-2) ...
Setting up libwiretap12:amd64 (3.6.2-2) ...
Setting up libjpeg-turbo8:amd64 (2.1.2-0ubuntu1) ...
Setting up libwebp7:amd64 (1.2.2-2ubuntu0.22.04.2) ...
Setting up libwireshark-data (3.6.2-2) ...
Setting up liblua5.2-0:amd64 (5.2.4-2) ...
Setting up libspeexdsp1:amd64 (1.2~rc1.2-1.1ubuntu3) ...
Setting up libjpeg8:amd64 (8c-2ubuntu10) ...
Setting up libtiff5:amd64 (4.3.0-6ubuntu0.10) ...
Setting up libspandsp2:amd64 (0.0.6+dfsg-2) ...
Setting up libwireshark15:amd64 (3.6.2-2) ...
Setting up wireshark-common (3.6.2-2) ...
Setting up tshark (3.6.2-2) ...
Setting up termshark (2.2.0-2ubuntu0.22.04.3) ...
Processing triggers for man-db (2.10.2-1) ...
Processing triggers for shared-mime-info (2.1-2) ...
Processing triggers for libc-bin (2.35-0ubuntu3.9) ...
NEEDRESTART-VER: 3.5
NEEDRESTART-KCUR: 6.8.0-1029-aws
NEEDRESTART-KEXP: 6.8.0-1029-aws
NEEDRESTART-KSTA: 1
9. tshark 인터페이스 목록 확인 (k3s-s)
1
(⎈|default:N/A) root@k3s-s:~# tshark -D
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Running as user "root" and group "root". This could be dangerous.
1. ens5
2. flannel.1
3. cni0
4. veth3c9458ee
5. veth610dd5ea
6. vethe6fc11dc
7. any
8. lo (Loopback)
9. bluetooth-monitor
10. nflog
11. nfqueue
12. dbus-system
13. dbus-session
14. ciscodump (Cisco remote capture)
15. dpauxmon (DisplayPort AUX channel monitor capture)
16. randpkt (Random packet generator)
17. sdjournal (systemd Journal Export)
18. sshdump (SSH remote capture)
19. udpdump (UDP Listener remote capture)
10. termshark 버전 확인 (k3s-s)
1
(⎈|default:N/A) root@k3s-s:~# termshark -v
✅ 출력
1
termshark 2.2.0
11. forum-vm EC2 SSH 접속
1
ssh -i kp-istio.pem ubuntu@3.36.50.171
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
ssh -i kp-istio.pem ubuntu@3.36.50.171
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 6.8.0-1029-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat May 31 17:45:21 KST 2025
System load: 0.08 Processes: 108
Usage of /: 6.6% of 28.89GB Users logged in: 0
Memory usage: 14% IPv4 address for ens5: 192.168.10.200
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
21 updates can be applied immediately.
18 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
New release '24.04.2 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Sat May 31 17:45:22 2025 from 182.230.60.93
root@forum-vm:~#
12. forum-vm 인터페이스 정보 요약 확인
1
root@forum-vm:~# ip -br -c addr
✅ 출력
1
2
lo UNKNOWN 127.0.0.1/8 ::1/128
ens5 UP 192.168.10.200/24 metric 100 fe80::bd:17ff:fe47:37f/64
ens5의 IP: 192.168.10.200/24
13. forum-vm 상세 인터페이스 확인
1
root@forum-vm:~# ip -c a
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9001 qdisc mq state UP group default qlen 1000
link/ether 02:bd:17:47:03:7f brd ff:ff:ff:ff:ff:ff
altname enp0s5
inet 192.168.10.200/24 metric 100 brd 192.168.10.255 scope global dynamic ens5
valid_lft 3108sec preferred_lft 3108sec
inet6 fe80::bd:17ff:fe47:37f/64 scope link
valid_lft forever preferred_lft forever
14. k3s-s 노드 상세 인터페이스 확인
1
(⎈|default:N/A) root@k3s-s:~# ip -c a
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9001 qdisc mq state UP group default qlen 1000
link/ether 02:84:37:eb:1a:e7 brd ff:ff:ff:ff:ff:ff
altname enp0s5
inet 192.168.10.10/24 metric 100 brd 192.168.10.255 scope global dynamic ens5
valid_lft 2923sec preferred_lft 2923sec
inet6 fe80::84:37ff:feeb:1ae7/64 scope link
valid_lft forever preferred_lft forever
3: flannel.1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 8951 qdisc noqueue state UNKNOWN group default
link/ether ae:4b:0f:a2:57:29 brd ff:ff:ff:ff:ff:ff
inet 172.16.0.0/32 scope global flannel.1
valid_lft forever preferred_lft forever
inet6 fe80::ac4b:fff:fea2:5729/64 scope link
valid_lft forever preferred_lft forever
4: cni0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 8951 qdisc noqueue state UP group default qlen 1000
link/ether 76:cf:26:ef:4e:d1 brd ff:ff:ff:ff:ff:ff
inet 172.16.0.1/24 brd 172.16.0.255 scope global cni0
valid_lft forever preferred_lft forever
inet6 fe80::74cf:26ff:feef:4ed1/64 scope link
valid_lft forever preferred_lft forever
5: veth3c9458ee@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 8951 qdisc noqueue master cni0 state UP group default
link/ether 42:cf:7e:20:d9:78 brd ff:ff:ff:ff:ff:ff link-netns cni-dd3b2dcf-bee9-75d7-2dd0-4d967e590601
inet6 fe80::40cf:7eff:fe20:d978/64 scope link
valid_lft forever preferred_lft forever
6: veth610dd5ea@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 8951 qdisc noqueue master cni0 state UP group default
link/ether 26:97:50:7c:3a:3d brd ff:ff:ff:ff:ff:ff link-netns cni-5ecffb97-56dd-67c4-4cbb-d9a64292eaac
inet6 fe80::2497:50ff:fe7c:3a3d/64 scope link
valid_lft forever preferred_lft forever
7: vethe6fc11dc@if2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 8951 qdisc noqueue master cni0 state UP group default
link/ether 22:1e:cb:5c:e9:f9 brd ff:ff:ff:ff:ff:ff link-netns cni-06ed1a45-0d36-9236-3848-0daa7d9b30ea
inet6 fe80::201e:cbff:fe5c:e9f9/64 scope link
valid_lft forever preferred_lft forever
ens5 IP: 192.168.10.10/24
15. forum-vm의 호스트 정보 확인
1
root@forum-vm:~# hostnamectl
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
Static hostname: forum-vm
Icon name: computer-vm
Chassis: vm
Machine ID: ec23989dxxxxxxxxxxxxxxxxxxxxxxxx
Boot ID: 2c80bd4bxxxxxxxxxxxxxxxxxxxxxxxx
Virtualization: amazon
Operating System: Ubuntu 22.04.5 LTS
Kernel: Linux 6.8.0-1029-aws
Architecture: x86-64
Hardware Vendor: Amazon EC2
Hardware Model: t3.small
16. termshark 설치 명령 실행 (forum-vm)
1
root@forum-vm:~# DEBIAN_FRONTEND=noninteractive apt install termshark -y
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
...
Setting up libssh-gcrypt-4:amd64 (0.9.6-2ubuntu0.22.04.3) ...
Setting up libsbc1:amd64 (1.5-3build2) ...
Setting up libbcg729-0:amd64 (1.1.1-2) ...
Setting up libdeflate0:amd64 (1.10-2) ...
Setting up libc-ares2:amd64 (1.18.1-1ubuntu0.22.04.3) ...
Setting up libjbig0:amd64 (2.1-3.1ubuntu0.22.04.1) ...
Setting up libsnappy1v5:amd64 (1.1.8-1build3) ...
Setting up libsmi2ldbl:amd64 (0.4.8+dfsg2-16) ...
Setting up libwsutil13:amd64 (3.6.2-2) ...
Setting up libwiretap12:amd64 (3.6.2-2) ...
Setting up libjpeg-turbo8:amd64 (2.1.2-0ubuntu1) ...
Setting up libwebp7:amd64 (1.2.2-2ubuntu0.22.04.2) ...
Setting up libwireshark-data (3.6.2-2) ...
Setting up liblua5.2-0:amd64 (5.2.4-2) ...
Setting up libspeexdsp1:amd64 (1.2~rc1.2-1.1ubuntu3) ...
Setting up libjpeg8:amd64 (8c-2ubuntu10) ...
Setting up libtiff5:amd64 (4.3.0-6ubuntu0.10) ...
Setting up libspandsp2:amd64 (0.0.6+dfsg-2) ...
Setting up libwireshark15:amd64 (3.6.2-2) ...
Setting up wireshark-common (3.6.2-2) ...
Setting up tshark (3.6.2-2) ...
Setting up termshark (2.2.0-2ubuntu0.22.04.3) ...
Processing triggers for man-db (2.10.2-1) ...
Processing triggers for shared-mime-info (2.1-2) ...
Processing triggers for libc-bin (2.35-0ubuntu3.9) ...
NEEDRESTART-VER: 3.5
NEEDRESTART-KCUR: 6.8.0-1029-aws
NEEDRESTART-KEXP: 6.8.0-1029-aws
NEEDRESTART-KSTA: 1
17. tshark 인터페이스 목록 확인 (forum-vm)
1
root@forum-vm:~# tshark -D
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Running as user "root" and group "root". This could be dangerous.
1. ens5
2. any
3. lo (Loopback)
4. bluetooth-monitor
5. nflog
6. nfqueue
7. dbus-system
8. dbus-session
9. ciscodump (Cisco remote capture)
10. dpauxmon (DisplayPort AUX channel monitor capture)
11. randpkt (Random packet generator)
12. sdjournal (systemd Journal Export)
13. sshdump (SSH remote capture)
14. udpdump (UDP Listener remote capture)
🕸️ 서비스 메시 준비하기
1. Istio in Action 예제 소스코드 클론
1
(⎈|default:N/A) root@k3s-s:~# git clone https://github.com/AcornPublishing/istio-in-action
✅ 출력
1
2
3
4
5
6
7
Cloning into 'istio-in-action'...
remote: Enumerating objects: 448, done.
remote: Counting objects: 100% (448/448), done.
remote: Compressing objects: 100% (341/341), done.
remote: Total 448 (delta 76), reused 448 (delta 76), pack-reused 0 (from 0)
Receiving objects: 100% (448/448), 17.29 MiB | 20.10 MiB/s, done.
Resolving deltas: 100% (76/76), done.
2. 클론한 디렉토리 구조 확인
1
(⎈|default:N/A) root@k3s-s:~# tree istio-in-action/book-source-code-master -L 1
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
istio-in-action/book-source-code-master
├── README.md
├── appendices
├── bin
├── ch10
├── ch11
├── ch12
├── ch13
├── ch14
├── ch2
├── ch3
├── ch4
├── ch5
├── ch6
├── ch7
├── ch8
├── ch9
└── services
16 directories, 1 file
3. istioctl 설치 (버전 1.17.8)
1
2
3
4
5
6
(⎈|default:N/A) root@k3s-s:~# export ISTIOV=1.17.8
echo 'export ISTIOV=1.17.8' >> /root/.bashrc
curl -s -L https://istio.io/downloadIstio | ISTIO_VERSION=$ISTIOV sh -
cp istio-$ISTIOV/bin/istioctl /usr/local/bin/istioctl
istioctl version --remote=false
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
Downloading istio-1.17.8 from https://github.com/istio/istio/releases/download/1.17.8/istio-1.17.8-linux-amd64.tar.gz ...
Istio 1.17.8 download complete!
The Istio release archive has been downloaded to the istio-1.17.8 directory.
To configure the istioctl client tool for your workstation,
add the /root/istio-1.17.8/bin directory to your environment path variable with:
export PATH="$PATH:/root/istio-1.17.8/bin"
Begin the Istio pre-installation check by running:
istioctl x precheck
Try Istio in ambient mode
https://istio.io/latest/docs/ambient/getting-started/
Try Istio in sidecar mode
https://istio.io/latest/docs/setup/getting-started/
Install guides for ambient mode
https://istio.io/latest/docs/ambient/install/
Install guides for sidecar mode
https://istio.io/latest/docs/setup/install/
Need more information? Visit https://istio.io/latest/docs/
4. istio-system 네임스페이스 생성 및 네트워크 레이블 지정
1
2
(⎈|default:N/A) root@k3s-s:~# kubectl create namespace istio-system
kubectl label namespace istio-system topology.istio.io/network=west-network
✅ 출력
1
2
namespace/istio-system created
namespace/istio-system labeled
5. IstioOperator 리소스를 사용한 demo 프로파일 컨트롤 플레인 배포
1
2
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/ch13/controlplane/cluster-in-west-network.yaml
(⎈|default:N/A) root@k3s-s:~# istioctl install -f istio-in-action/book-source-code-master/ch13/controlplane/cluster-in-west-network.yaml --set values.global.proxy.privileged=true -y
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
apiVersion: install.istio.io/v1alpha1
metadata:
name: istio-controlplane
namespace: istio-system
kind: IstioOperator
spec:
profile: demo
components:
egressGateways:
- name: istio-egressgateway
enabled: false
values:
global:
meshID: usmesh
multiCluster:
clusterName: west-cluster
network: west-network
1
2
3
4
5
6
✔ Istio core installed
✔ Istiod installed
✔ Ingress gateways installed
✔ Installation complete Making this installation the default for injection and validation.
Thank you for installing Istio 1.17. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/hMHGiwZHPU7UQRWe9
6. 보조 도구 설치
1
(⎈|default:N/A) root@k3s-s:~# kubectl apply -f istio-$ISTIOV/samples/addons
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
serviceaccount/grafana created
configmap/grafana created
service/grafana created
Warning: spec.template.spec.containers[0].ports[1]: duplicate port definition with spec.template.spec.containers[0].ports[0]
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created
7. 실습용 네임스페이스 생성 및 사이드카 자동주입 설정
1
2
3
4
5
6
(⎈|default:N/A) root@k3s-s:~# kubectl create ns istioinaction
kubectl label namespace istioinaction istio-injection=enabled
# 결과
namespace/istioinaction created
namespace/istioinaction labeled
8. 네임스페이스에 설정된 레이블 확인
1
(⎈|default:N/A) root@k3s-s:~# kubectl get ns --show-labels
✅ 출력
1
2
3
4
5
6
7
NAME STATUS AGE LABELS
default Active 101m kubernetes.io/metadata.name=default
istio-system Active 3m33s kubernetes.io/metadata.name=istio-system,topology.istio.io/network=west-network
istioinaction Active 24s istio-injection=enabled,kubernetes.io/metadata.name=istioinaction
kube-node-lease Active 101m kubernetes.io/metadata.name=kube-node-lease
kube-public Active 101m kubernetes.io/metadata.name=kube-public
kube-system Active 101m kubernetes.io/metadata.name=kube-system
9. istio-ingressgateway NodePort 설정 및 ClientIP 수집 정책 적용
1
2
3
(⎈|default:N/A) root@k3s-s:~# kubectl patch svc -n istio-system istio-ingressgateway -p '{"spec": {"type": "NodePort", "ports": [{"port": 80, "targetPort": 8080, "nodePort": 30000}]}}'
kubectl patch svc -n istio-system istio-ingressgateway -p '{"spec": {"type": "NodePort", "ports": [{"port": 443, "targetPort": 8443, "nodePort": 30005}]}}'
kubectl patch svc -n istio-system istio-ingressgateway -p '{"spec":{"externalTrafficPolicy": "Local"}}'
✅ 출력
1
2
3
service/istio-ingressgateway patched
service/istio-ingressgateway patched
service/istio-ingressgateway patched
10. observability 서비스(NodePort) 설정 변경
1
2
3
4
(⎈|default:N/A) root@k3s-s:~# kubectl patch svc -n istio-system prometheus -p '{"spec": {"type": "NodePort", "ports": [{"port": 9090, "targetPort": 9090, "nodePort": 30001}]}}'
kubectl patch svc -n istio-system grafana -p '{"spec": {"type": "NodePort", "ports": [{"port": 3000, "targetPort": 3000, "nodePort": 30002}]}}'
kubectl patch svc -n istio-system kiali -p '{"spec": {"type": "NodePort", "ports": [{"port": 20001, "targetPort": 20001, "nodePort": 30003}]}}'
kubectl patch svc -n istio-system tracing -p '{"spec": {"type": "NodePort", "ports": [{"port": 80, "targetPort": 16686, "nodePort": 30004}]}}'
✅ 출력
1
2
3
4
service/prometheus patched
service/grafana patched
service/kiali patched
service/tracing patched
11. Kiali 접속 주소 확인 (NodePort + Public IP)
1
(⎈|default:N/A) root@k3s-s:~# echo -e "http://$(curl -s ipinfo.io/ip):30003"
✅ 출력
1
http://3.35.133.203:30003
12. Cool Store 애플리케이션 리소스 배포 (Webapp, Catalog)
1
2
3
(⎈|default:N/A) root@k3s-s:~# kubectl -n istioinaction apply -f istio-in-action/book-source-code-master/ch12/webapp-deployment-svc.yaml
kubectl -n istioinaction apply -f istio-in-action/book-source-code-master/ch12/webapp-gw-vs.yaml
kubectl -n istioinaction apply -f istio-in-action/book-source-code-master/ch12/catalog.yaml
✅ 출력
1
2
3
4
5
6
7
8
serviceaccount/webapp created
service/webapp created
deployment.apps/webapp created
gateway.networking.istio.io/coolstore-gateway created
virtualservice.networking.istio.io/webapp-virtualservice created
serviceaccount/catalog created
service/catalog created
deployment.apps/catalog created
13. 애플리케이션 리소스 배포 상태 확인
1
2
(⎈|default:N/A) root@k3s-s:~# kc get deploy,svc -n istioinaction
kc get gw,vs -n istioinaction
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/catalog 1/1 1 1 25s
deployment.apps/webapp 1/1 1 1 26s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.10.200.37 <none> 80/TCP 25s
service/webapp ClusterIP 10.10.200.134 <none> 80/TCP 26s
NAME AGE
gateway.networking.istio.io/coolstore-gateway 46s
NAME GATEWAYS HOSTS AGE
virtualservice.networking.istio.io/webapp-virtualservice ["coolstore-gateway"] ["webapp.istioinaction.io"] 46s
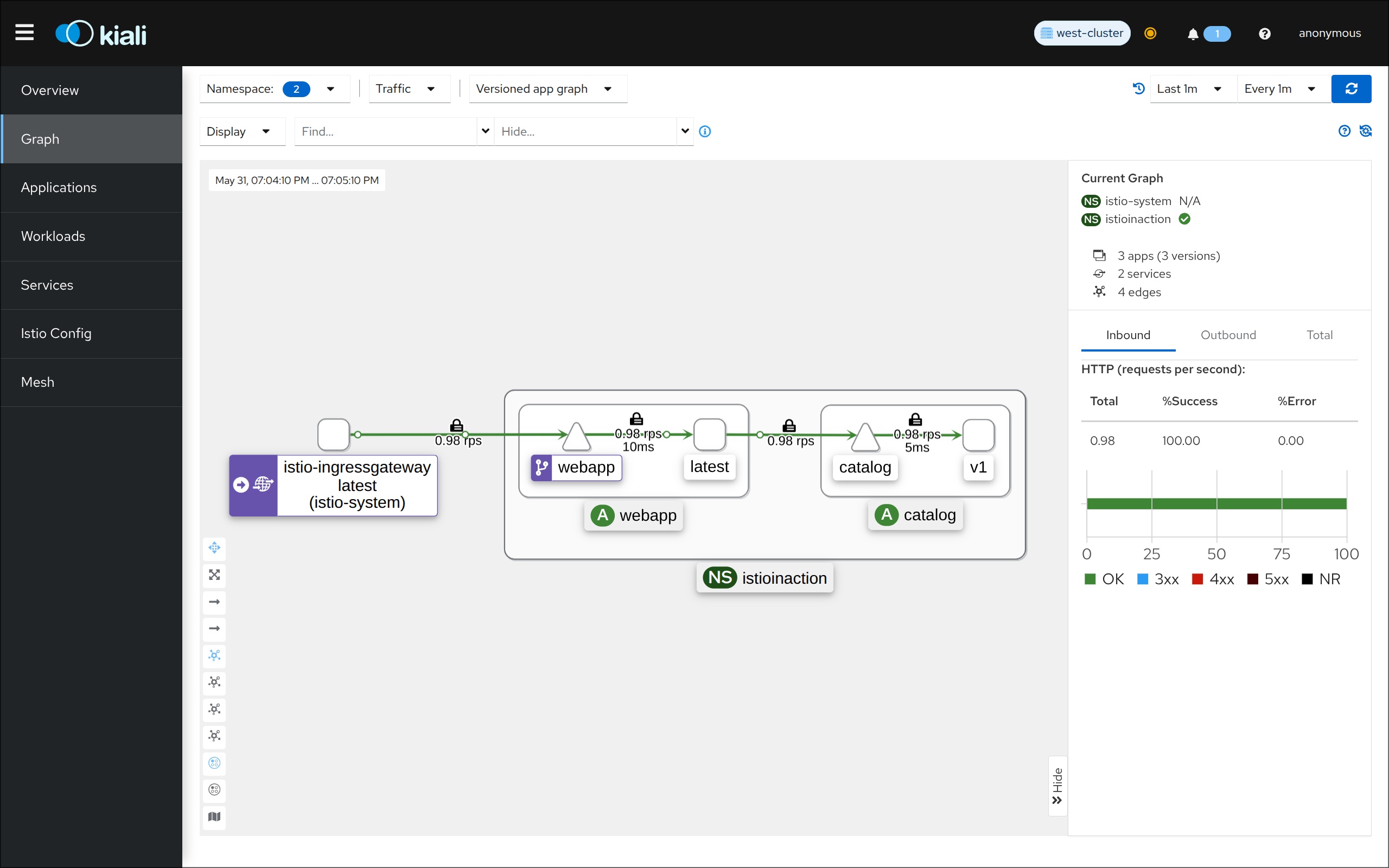
14. 클러스터 내에서 curl로 서비스 호출 테스트
1
(⎈|default:N/A) root@k3s-s:~# curl -s -H "Host: webapp.istioinaction.io" http://192.168.10.10:30000/api/catalog/ | jq
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
[
{
"id": 1,
"color": "amber",
"department": "Eyewear",
"name": "Elinor Glasses",
"price": "282.00"
},
{
"id": 2,
"color": "cyan",
"department": "Clothing",
"name": "Atlas Shirt",
"price": "127.00"
},
{
"id": 3,
"color": "teal",
"department": "Clothing",
"name": "Small Metal Shoes",
"price": "232.00"
},
{
"id": 4,
"color": "red",
"department": "Watches",
"name": "Red Dragon Watch",
"price": "232.00"
}
]
15. catalog 서비스 개별 항목 호출 테스트
1
(⎈|default:N/A) root@k3s-s:~# curl -s -H "Host: webapp.istioinaction.io" http://192.168.10.10:30000/api/catalog/items/1 | jq
✅ 출력
1
2
3
4
5
6
7
{
"id": 1,
"color": "amber",
"department": "Eyewear",
"name": "Elinor Glasses",
"price": "282.00"
}
16. forum-vm에서 클러스터 NodePort 서비스 호출 테스트
1
2
root@forum-vm:~# APP_IP=3.35.133.203
curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/catalog/items/1 | jq
✅ 출력
1
2
3
4
5
6
7
{
"id": 1,
"color": "amber",
"department": "Eyewear",
"name": "Elinor Glasses",
"price": "282.00"
}
17. forum-vm에서 지속적인 요청 시도
1
root@forum-vm:~# while true; do curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/catalog/ ; echo; date; sleep 1; done
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 19:03:56 KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 19:03:57 KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 19:03:58 KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 19:03:59 KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 19:04:00 KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 19:04:01 KST 2025
...
18. 로컬 PC에서 서비스 접근 확인
1
2
APP_IP=3.35.133.203
curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/catalog/items/1 | jq
✅ 출력
1
2
3
4
5
6
7
{
"id": 1,
"color": "amber",
"department": "Eyewear",
"name": "Elinor Glasses",
"price": "282.00"
}
1
while true; do curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/catalog/ ; echo; date; sleep 1; done
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 07:07:27 PM KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 07:07:28 PM KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 07:07:29 PM KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 07:07:30 PM KST 2025
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
Sat May 31 07:07:31 PM KST 2025
...
19. k3s-s 노드에서 forum-vm 웹서버 응답 확인
1
(⎈|default:N/A) root@k3s-s:~# curl 192.168.10.200 -I
✅ 출력
1
2
3
4
5
6
7
8
9
HTTP/1.1 200 OK
Date: Sat, 31 May 2025 10:09:41 GMT
Server: Apache/2.4.52 (Ubuntu)
Last-Modified: Sat, 31 May 2025 08:10:00 GMT
ETag: "29af-6366a0ead7324"
Accept-Ranges: bytes
Content-Length: 10671
Vary: Accept-Encoding
Content-Type: text/html
20. forum-vm의 공인 IP를 통한 웹서버 응답 확인
1
2
(⎈|default:N/A) root@k3s-s:~# VM_IP=3.36.50.171
curl $VM_IP -I
✅ 출력
1
2
3
4
5
6
7
8
9
HTTP/1.1 200 OK
Date: Sat, 31 May 2025 10:12:43 GMT
Server: Apache/2.4.52 (Ubuntu)
Last-Modified: Sat, 31 May 2025 08:10:00 GMT
ETag: "29af-6366a0ead7324"
Accept-Ranges: bytes
Content-Length: 10671
Vary: Accept-Encoding
Content-Type: text/html
🖥️ 컨트롤 플레인 업데이트
1. VM 연동 기능이 포함된 IstioOperator 매니페스트 확인
1
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/ch13/controlplane/cluster-in-west-network-with-vm-features.yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
apiVersion: install.istio.io/v1alpha1
metadata:
name: istio-controlplane
namespace: istio-system
kind: IstioOperator
spec:
profile: demo
components:
egressGateways:
- name: istio-egressgateway
enabled: false
meshConfig:
defaultConfig:
proxyMetadata:
ISTIO_META_DNS_CAPTURE: "true" # DNS 쿼리가 캡처돼 DNS 프록시로 리다이렉트된다
values:
pilot:
env:
PILOT_ENABLE_WORKLOAD_ENTRY_AUTOREGISTRATION: true # 워크로드를 컨트롤 플레인에 자동 등록할 수 있다
PILOT_ENABLE_WORKLOAD_ENTRY_HEALTHCHECKS: true # 가상머신 워크로드의 상태를 검사한다
global:
meshID: usmesh
multiCluster:
clusterName: west-cluster
network: west-network
2. VM 기능이 추가된 컨트롤 플레인 설치
1
(⎈|default:N/A) root@k3s-s:~# istioctl install -f istio-in-action/book-source-code-master/ch13/controlplane/cluster-in-west-network-with-vm-features.yaml --set values.global.proxy.privileged=true -y
✅ 출력
1
2
3
4
5
6
✔ Istio core installed
✔ Istiod installed
✔ Ingress gateways installed
✔ Installation complete Making this installation the default for injection and validation.
Thank you for installing Istio 1.17. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/hMHGiwZHPU7UQRWe9
3. istio-ingressgateway를 NodePort 타입으로 패치
1
(⎈|default:N/A) root@k3s-s:~# kubectl patch svc istio-ingressgateway -n istio-system -p '{"spec": {"type": "NodePort"}}'
✅ 출력
1
service/istio-ingressgateway patched
🌐 istiod와 클러스터 서비스들은 가상머신에 노출하기
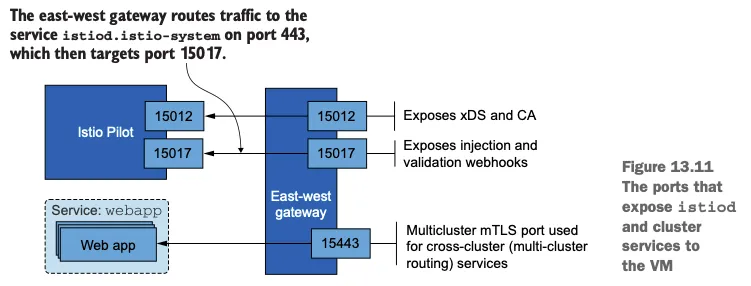
1. east-west 게이트웨이 매니페스트 확인
1
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/ch13/gateways/cluster-east-west-gw.yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
name: istio-eastwestgateway
namespace: istio-system
spec:
profile: empty
components:
ingressGateways:
- name: istio-eastwestgateway
label:
istio: eastwestgateway
app: istio-eastwestgateway
topology.istio.io/network: west-network
enabled: true
k8s:
env:
- name: ISTIO_META_ROUTER_MODE
value: "sni-dnat"
# The network to which traffic is routed
- name: ISTIO_META_REQUESTED_NETWORK_VIEW
value: west-network
service:
ports:
- name: status-port
port: 15021
targetPort: 15021
- name: mtls
port: 15443
targetPort: 15443
- name: tcp-istiod
port: 15012
targetPort: 15012
- name: tcp-webhook
port: 15017
targetPort: 15017
values:
global:
meshID: usmesh
multiCluster:
clusterName: west-cluster
network: west-network
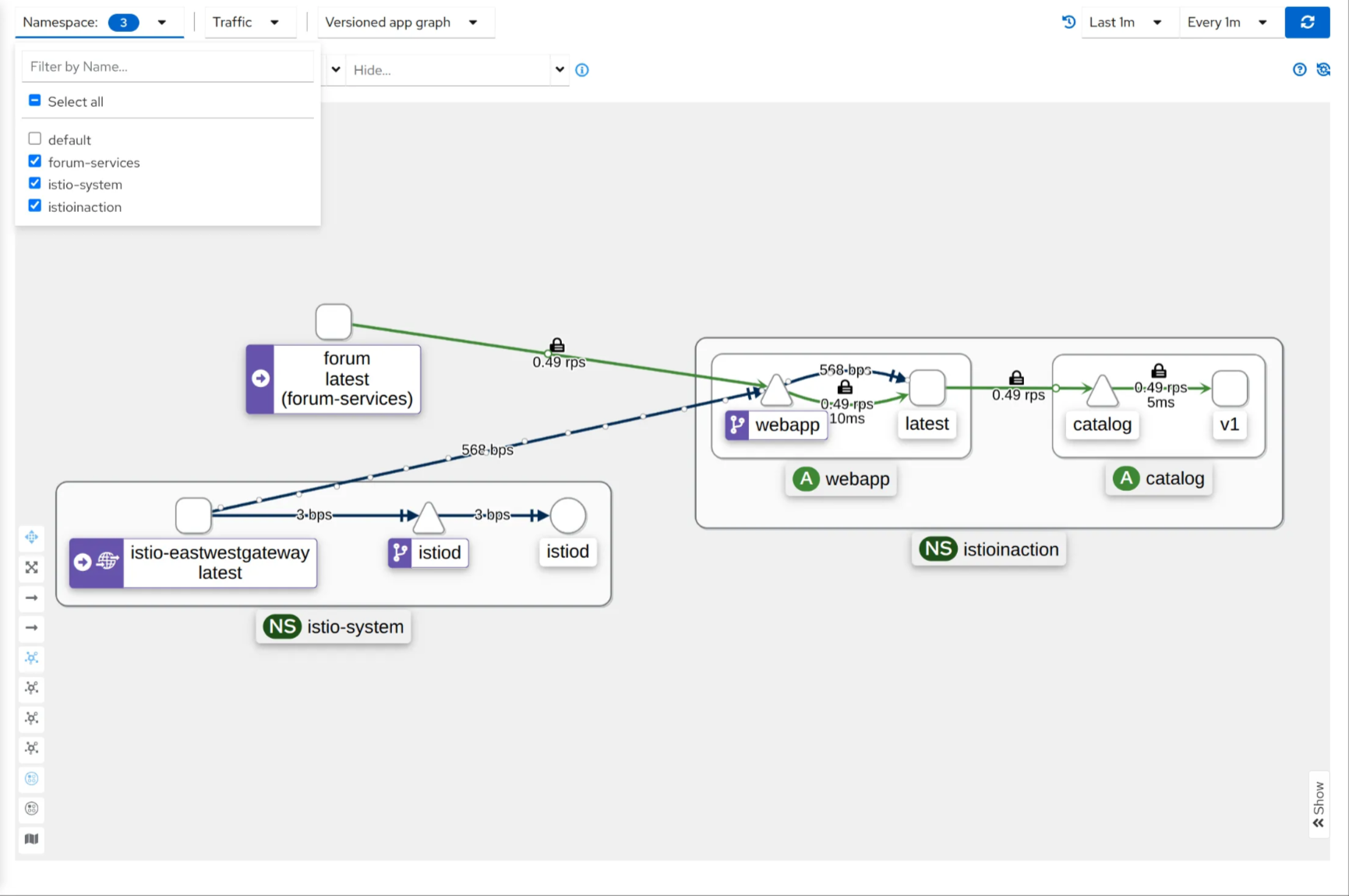
2. east-west 게이트웨이 설치
1
(⎈|default:N/A) root@k3s-s:~# istioctl install -f istio-in-action/book-source-code-master/ch13/gateways/cluster-east-west-gw.yaml -y
✅ 출력
1
2
3
✔ Ingress gateways installed
✔ Installation complete
Thank you for installing Istio 1.17. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/hMHGiwZHPU7UQRWe9
3. 설치된 게이트웨이 파드 확인
1
(⎈|default:N/A) root@k3s-s:~# kubectl get pod -n istio-system -l chart=gateways
✅ 출력
1
2
3
NAME READY STATUS RESTARTS AGE
istio-eastwestgateway-86f6cb4699-gwbwq 1/1 Running 0 29s
istio-ingressgateway-7b7ccd6454-cdvc6 1/1 Running 0 7m40s
4. external-ip 노출된 게이트웨이 서비스 확인
1
(⎈|default:N/A) root@k3s-s:~# kubectl get svc -n istio-system -l istio.io/rev=default
✅ 출력
1
2
3
4
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-eastwestgateway LoadBalancer 10.10.200.254 192.168.10.10 15021:31128/TCP,15443:32755/TCP,15012:31286/TCP,15017:32181/TCP 84s
istio-ingressgateway NodePort 10.10.200.56 <none> 15021:32513/TCP,80:30000/TCP,443:30005/TCP,31400:30959/TCP,15443:32461/TCP 39m
istiod ClusterIP 10.10.200.61 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 40m
5. LoadBalancer 백엔드 파드 확인 (svclb)
1
(⎈|default:N/A) root@k3s-s:~# k get pod -A
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
NAMESPACE NAME READY STATUS RESTARTS AGE
istio-system grafana-545465bf4c-hhtlp 1/1 Running 0 40m
istio-system istio-eastwestgateway-86f6cb4699-gwbwq 1/1 Running 0 2m49s
istio-system istio-ingressgateway-7b7ccd6454-cdvc6 1/1 Running 0 10m
istio-system istiod-d6549b9fc-gxjc5 1/1 Running 0 10m
istio-system jaeger-7cf8c7c56d-59kf2 1/1 Running 0 40m
istio-system kiali-8f985c677-hfcs8 1/1 Running 0 40m
istio-system prometheus-7f467df8b6-qkw5j 2/2 Running 0 40m
istioinaction catalog-77fdb4997c-fhpf9 2/2 Running 0 35m
istioinaction webapp-684c568c59-6x29p 2/2 Running 0 35m
kube-system coredns-559656f558-rkkjj 1/1 Running 0 140m
kube-system local-path-provisioner-7677785564-ktdcb 1/1 Running 0 140m
kube-system metrics-server-7cbbc464f4-2nlxw 1/1 Running 0 140m
kube-system svclb-istio-eastwestgateway-e075595c-lmpqj 4/4 Running 0 2m49s
6. east-west 게이트웨이 서비스의 노출 포트 확인
1
(⎈|default:N/A) root@k3s-s:~# kubectl get svc -n istio-system istio-eastwestgateway -o json | jq
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
...
"ports": [
{
"name": "status-port",
"nodePort": 31128,
"port": 15021,
"protocol": "TCP",
"targetPort": 15021
},
{
"name": "mtls",
"nodePort": 32755,
"port": 15443,
"protocol": "TCP",
"targetPort": 15443
},
{
"name": "tcp-istiod",
"nodePort": 31286,
"port": 15012,
"protocol": "TCP",
"targetPort": 15012
},
{
"name": "tcp-webhook",
"nodePort": 32181,
"port": 15017,
"protocol": "TCP",
"targetPort": 15017
}
],
...
7. istiod 서비스 포트 구성 확인
1
(⎈|default:N/A) root@k3s-s:~# kubectl get svc -n istio-system istiod -o json | jq
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
...
"ports": [
{
"name": "grpc-xds",
"port": 15010,
"protocol": "TCP",
"targetPort": 15010
},
{
"name": "https-dns",
"port": 15012,
"protocol": "TCP",
"targetPort": 15012
},
{
"name": "https-webhook",
"port": 443,
"protocol": "TCP",
"targetPort": 15017
},
{
"name": "http-monitoring",
"port": 15014,
"protocol": "TCP",
"targetPort": 15014
}
],
...
8. 클러스터 서비스 공개용 Gateway 리소스 매니페스트 확인
1
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/ch13/expose-services.yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: cross-network-gateway
namespace: istio-system
spec:
selector:
istio: eastwestgateway
servers:
- port:
number: 15443
name: tls
protocol: TLS
tls:
mode: AUTO_PASSTHROUGH
hosts:
- "*.local"
9. 클러스터 서비스 공개용 Gateway 리소스 적용
1
2
3
4
(⎈|default:N/A) root@k3s-s:~# kubectl apply -f istio-in-action/book-source-code-master/ch13/expose-services.yaml
# 결과
gateway.networking.istio.io/cross-network-gateway created
10. Gateway 및 VirtualService 리소스 생성 상태 확인
1
(⎈|default:N/A) root@k3s-s:~# kubectl get gw,vs -A
✅ 출력
1
2
3
4
5
6
NAMESPACE NAME AGE
istio-system gateway.networking.istio.io/cross-network-gateway 3m4s
istioinaction gateway.networking.istio.io/coolstore-gateway 43m
NAMESPACE NAME GATEWAYS HOSTS AGE
istioinaction virtualservice.networking.istio.io/webapp-virtualservice ["coolstore-gateway"] ["webapp.istioinaction.io"] 43m
11. istiod 노출용 Gateway 및 VirtualService 매니페스트 확인
1
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/ch13/expose-istiod.yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: istiod-gateway
spec:
selector:
istio: eastwestgateway
servers:
- port:
name: tls-istiod
number: 15012
protocol: tls
tls:
mode: PASSTHROUGH
hosts:
- "*"
- port:
name: tls-istiodwebhook
number: 15017
protocol: tls
tls:
mode: PASSTHROUGH
hosts:
- "*"
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: istiod-vs
spec:
hosts:
- "*"
gateways:
- istiod-gateway
tls:
- match:
- port: 15012
sniHosts:
- "*"
route:
- destination:
host: istiod.istio-system.svc.cluster.local
port:
number: 15012
- match:
- port: 15017
sniHosts:
- "*"
route:
- destination:
host: istiod.istio-system.svc.cluster.local
port:
number: 443
12. istiod 노출용 Gateway 및 VirtualService 리소스 적용
1
2
3
4
5
(⎈|default:N/A) root@k3s-s:~# kubectl apply -f istio-in-action/book-source-code-master/ch13/expose-istiod.yaml -n istio-system
# 결과
gateway.networking.istio.io/istiod-gateway created
virtualservice.networking.istio.io/istiod-vs created
13. istiod 관련 Gateway 및 VirtualService 리소스 상태 확인
1
(⎈|default:N/A) root@k3s-s:~# kc get gw,vs -A
✅ 출력
1
2
3
4
5
6
7
8
NAMESPACE NAME AGE
istio-system gateway.networking.istio.io/cross-network-gateway 4m15s
istio-system gateway.networking.istio.io/istiod-gateway 22s
istioinaction gateway.networking.istio.io/coolstore-gateway 44m
NAMESPACE NAME GATEWAYS HOSTS AGE
istio-system virtualservice.networking.istio.io/istiod-vs ["istiod-gateway"] ["*"] 22s
istioinaction virtualservice.networking.istio.io/webapp-virtualservice ["coolstore-gateway"] ["webapp.istioinaction.io"] 44m
🧩 WorkloadGroup으로 워크로드 그룹 나타내기
1. WorkloadGroup 매니페스트 확인
1
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/ch13/workloadgroup.yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
apiVersion: networking.istio.io/v1alpha3
kind: WorkloadGroup
metadata:
name: forum
namespace: forum-services
spec:
metadata:
annotations: {}
labels:
app: forum # 서비스는 레이블을 사용해 이 그룹의 워크로드를 대상으로 삼을 수 있다
template:
serviceAccount: forum-sa # 워크로드가 이 워크로드 그룹에 등록하려면 forum-sa 인증 토큰을 보유하고 있어야 한다
network: vm-network # 이스티오가 동일한 네트워크에 있는 워크로드 사이의 직접 접근을 설정할 수 있도록 한다
probe: # 이 워크로드 그룹의 인스턴스에서 실행되는 istio-agent는 HTTP GET 요청을 8080 포트의 /api/healthz 경로로 보내 앱의 준비 상태를 확인한다
periodSeconds: 5
initialDelaySeconds: 1
httpGet:
port: 8080
path: /api/healthz
2. forum-services 네임스페이스 및 서비스 어카운트 생성
1
2
3
(⎈|default:N/A) root@k3s-s:~# kubectl create namespace forum-services
kubectl create serviceaccount forum-sa -n forum-services
✅ 출력
1
2
namespace/forum-services created
serviceaccount/forum-sa created
3. WorkloadGroup 리소스 생성
1
(⎈|default:N/A) root@k3s-s:~# kubectl apply -f istio-in-action/book-source-code-master/ch13/workloadgroup.yaml
✅ 출력
1
workloadgroup.networking.istio.io/forum created
4. forum-services 네임스페이스 리소스 확인
1
2
(⎈|default:N/A) root@k3s-s:~# kubectl get-all -n forum-services
kubectl get workloadgroup -n forum-services
✅ 출력
1
2
3
4
5
6
7
8
9
NAME NAMESPACE AGE
configmap/istio-ca-root-cert forum-services 67s
configmap/kube-root-ca.crt forum-services 67s
serviceaccount/default forum-services 67s
serviceaccount/forum-sa forum-services 67s
workloadgroup.networking.istio.io/forum forum-services 67s
NAME AGE
forum 67s
⚙️ 가상머신의 사이드카용 설정 생성하기
1. WorkloadEntry 구성 파일 생성
1
(⎈|default:N/A) root@k3s-s:~# istioctl x workload entry configure -f istio-in-action/book-source-code-master/ch13/workloadgroup.yaml -o /tmp/my-workload-files/ --clusterID "west-cluster" --autoregister
✅ 출력
1
2
Warning: a security token for namespace "forum-services" and service account "forum-sa" has been generated and stored at "/tmp/my-workload-files/istio-token"
Configuration generation into directory /tmp/my-workload-files/ was successful
2. 파일 권한 변경 및 생성된 구성 파일 목록 확인
1
2
(⎈|default:N/A) root@k3s-s:~# chown ubuntu:ubuntu -R /tmp/my-workload-files/
tree /tmp/my-workload-files/
✅ 출력
1
2
3
4
5
6
7
8
/tmp/my-workload-files/
├── cluster.env
├── hosts
├── istio-token
├── mesh.yaml
└── root-cert.pem
0 directories, 5 file
3. hosts 파일 내용 확인
1
(⎈|default:N/A) root@k3s-s:~# cat /tmp/my-workload-files/hosts
✅ 출력
1
192.168.10.10 istiod.istio-system.svc
4. eastwestgateway 노출 IP 및 클러스터 서비스 확인
eastwestgateway: 192.168.10.10
1
(⎈|default:N/A) root@k3s-s:~# kc get svc -A
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.10.200.1 <none> 443/TCP 160m
istio-system grafana NodePort 10.10.200.65 <none> 3000:30002/TCP 60m
istio-system istio-eastwestgateway LoadBalancer 10.10.200.254 192.168.10.10 15021:31128/TCP,15443:32755/TCP,15012:31286/TCP,15017:32181/TCP 22m
istio-system istio-ingressgateway NodePort 10.10.200.56 <none> 15021:32513/TCP,80:30000/TCP,443:30005/TCP,31400:30959/TCP,15443:32461/TCP 61m
istio-system istiod ClusterIP 10.10.200.61 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 61m
istio-system jaeger-collector ClusterIP 10.10.200.104 <none> 14268/TCP,14250/TCP,9411/TCP 60m
istio-system kiali NodePort 10.10.200.187 <none> 20001:30003/TCP,9090:32679/TCP 60m
istio-system prometheus NodePort 10.10.200.128 <none> 9090:30001/TCP 60m
istio-system tracing NodePort 10.10.200.67 <none> 80:30004/TCP,16685:31406/TCP 60m
istio-system zipkin ClusterIP 10.10.200.41 <none> 9411/TCP 60m
istioinaction catalog ClusterIP 10.10.200.37 <none> 80/TCP 55m
istioinaction webapp ClusterIP 10.10.200.134 <none> 80/TCP 55m
kube-system kube-dns ClusterIP 10.10.200.10 <none> 53/UDP,53/TCP,9153/TCP 160m
kube-system metrics-server ClusterIP 10.10.200.82 <none> 443/TCP 160m
💾 생성된 파일을 가상머신을 전송하기
1. k3s-s에서 로컬 PC로 구성 파일 복사 (scp)
1
2
3
APP_IP=3.35.133.203 # k3s-s의 IP
mkdir my-workload-files
scp -i kp-istio.pem ubuntu@$APP_IP:/tmp/my-workload-files/\* ./my-workload-files
✅ 출력
1
2
3
4
5
cluster.env 100% 635 58.1KB/s 00:00
hosts 100% 38 3.6KB/s 00:00
istio-token 100% 844 78.8KB/s 00:00
mesh.yaml 100% 792 75.6KB/s 00:00
root-cert.pem 100% 1099 101.8KB/s 00:00
2. 로컬에 복사된 파일 목록 확인
1
ls -al
✅ 출력
1
2
3
4
5
6
7
drwxr-xr-x - devshin 31 May 20:39 .
drwxr-xr-x - devshin 31 May 20:35 ..
.rwxr--r-- 635 devshin 31 May 20:39 cluster.env
.rwxr--r-- 38 devshin 31 May 20:39 hosts
.rwxr--r-- 844 devshin 31 May 20:39 istio-token
.rwxr--r-- 792 devshin 31 May 20:39 mesh.yaml
.rwxr--r-- 1.1k devshin 31 May 20:39 root-cert.pem
3. Istio CA 인증서 정보 확인
1
openssl x509 -in ./my-workload-files/root-cert.pem -noout -text
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
c4:8c:4f:f9:a6:7f:ae:81:fe:8a:84:22:00:11:43:ff
Signature Algorithm: sha256WithRSAEncryption
Issuer: O=cluster.local
Validity
Not Before: May 31 09:49:20 2025 GMT
Not After : May 29 09:49:20 2035 GMT
Subject: O=cluster.local
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:bf:5c:f9:e2:50:af:18:59:a0:64:94:00:91:71:
80:11:ca:fa:5f:79:f0:6d:5d:3b:cc:91:95:2a:5c:
3e:a0:11:c3:8a:1d:c8:ea:27:a0:43:53:79:3e:09:
3c:2a:86:c6:a1:64:37:c7:07:9a:f4:a5:5b:5d:7a:
6f:f4:32:ff:dd:5a:41:79:10:02:52:3e:b5:1b:5d:
95:3f:ab:ae:f8:3d:e2:96:cb:ed:dc:7a:a5:e8:b7:
f0:21:20:e4:03:6a:6f:0c:67:59:54:ad:58:ad:53:
52:9d:2f:73:fe:ed:d7:3a:09:f1:7d:7a:20:f8:6f:
06:eb:6d:19:81:5b:62:13:6b:f6:51:e2:98:4f:68:
f8:4a:f0:38:c8:3f:ca:94:e1:aa:90:0b:c2:b3:09:
cb:c6:24:9f:35:e2:f0:51:98:bc:50:55:69:b3:87:
4a:95:5b:f5:f8:a8:1d:80:97:16:39:c3:81:7f:c4:
be:49:cb:0c:46:f6:50:fc:80:c1:0e:72:64:76:bb:
5a:f5:d2:9e:37:77:20:f1:9d:eb:f3:46:7d:26:6d:
af:53:ec:39:fe:40:c3:5a:cf:83:d5:20:07:3a:e9:
42:bc:cf:8e:af:31:4a:09:92:84:61:23:fc:56:ff:
87:57:dc:84:5f:0e:51:82:98:2e:34:d0:23:7c:08:
e5:c3
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
B4:03:E5:8E:15:2F:6B:EE:83:4A:C0:9E:D7:9B:59:FB:B6:3F:DE:BA
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
22:2d:30:dc:ef:cf:8c:60:d8:b5:10:a2:8f:c9:9f:4e:a4:41:
ae:1f:05:d8:43:f0:39:c9:6f:43:a7:85:41:be:22:33:6f:b7:
9b:70:d2:d8:b5:80:07:74:e3:65:ad:2c:b5:d5:6a:5d:93:49:
7a:c6:26:99:41:66:41:ea:a3:60:05:ac:11:e8:7d:17:73:12:
3b:93:c3:0e:9c:15:cc:e8:ea:df:f2:e7:87:3f:56:c1:d3:c5:
66:79:4b:b3:35:a9:18:4e:85:2a:8d:6c:c6:90:7e:68:7a:78:
f5:4f:8b:27:60:d4:ae:d3:32:a9:bd:d3:b5:3f:a0:3d:4c:a5:
34:21:ee:cb:fa:8d:b1:28:64:07:9d:63:d8:eb:af:7e:3f:01:
26:f4:0a:52:33:e6:ab:03:f4:a4:69:7d:50:11:f1:a7:ec:8c:
b1:51:9f:dd:bf:fa:ff:ff:fd:dd:aa:0a:86:3d:76:df:51:40:
7c:b0:da:9d:a5:6c:f8:22:cf:a2:54:5f:d1:64:eb:eb:3b:4b:
60:e1:ab:99:4a:6f:5b:9f:6f:6e:e2:de:40:11:46:7c:61:ff:
c6:ce:74:c7:65:69:be:2d:69:7f:d0:b3:7e:59:f9:a5:38:44:
8a:99:d6:47:7f:c6:f4:11:4c:36:f2:d6:d1:2b:22:c3:77:b6:
9c:ec:d2:8d
4. 서비스 어카운트 토큰 디코딩
1
jwt decode $(cat ./my-workload-files/istio-token)
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
Token header
------------
{
"alg": "RS256",
"kid": "RJKqWFbDVGPY4omTUQ8JNqzOmyK6d7KeRJhsCCM71aw"
}
Token claims
------------
{
"aud": [
"istio-ca"
],
"exp": 1748692095,
"iat": 1748688495,
"iss": "https://kubernetes.default.svc.cluster.local",
"kubernetes.io": {
"namespace": "forum-services",
"serviceaccount": {
"name": "forum-sa",
"uid": "f4d9a29e-31ad-42a1-b790-083b56f86f94"
}
},
"nbf": 1748688495,
"sub": "system:serviceaccount:forum-services:forum-sa"
}
5. mesh.yaml 파일의 프록시 메타데이터 및 설정 확인
1
cat ./my-workload-files/mesh.yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
defaultConfig:
discoveryAddress: istiod.istio-system.svc:15012
meshId: usmesh
proxyMetadata:
CANONICAL_REVISION: latest
CANONICAL_SERVICE: forum
ISTIO_META_AUTO_REGISTER_GROUP: forum
ISTIO_META_CLUSTER_ID: west-cluster
ISTIO_META_DNS_CAPTURE: "true"
ISTIO_META_MESH_ID: usmesh
ISTIO_META_NETWORK: vm-network
ISTIO_META_WORKLOAD_NAME: forum
ISTIO_METAJSON_LABELS: '{"app":"forum","service.istio.io/canonical-name":"forum","service.istio.io/canonical-revision":"latest"}'
POD_NAMESPACE: forum-services
SERVICE_ACCOUNT: forum-sa
TRUST_DOMAIN: cluster.local
readinessProbe:
httpGet:
path: /api/healthz
port: 8080
initialDelaySeconds: 1
periodSeconds: 5
tracing:
zipkin:
address: zipkin.istio-system:9411
6. 로컬에서 forum-vm으로 설정 파일 전송
1
2
3
4
5
FORUM=3.36.50.171
scp -i kp-istio.pem ./my-workload-files/cluster.env ubuntu@$FORUM:/tmp/
scp -i kp-istio.pem ./my-workload-files/istio-token ubuntu@$FORUM:/tmp/
scp -i kp-istio.pem ./my-workload-files/mesh.yaml ubuntu@$FORUM:/tmp/
scp -i kp-istio.pem ./my-workload-files/root-cert.pem ubuntu@$FORUM:/tmp/
✅ 출력
1
2
3
4
cluster.env 100% 635 69.9KB/s 00:00
istio-token 100% 844 75.2KB/s 00:00
mesh.yaml 100% 792 124.2KB/s 00:00
root-cert.pem 100% 1099 164.9KB/s 00:00
7. forum-vm 내에서 전송된 파일 존재 여부 확인
1
root@forum-vm:~# ls -l /tmp
✅ 출력
1
2
3
4
5
6
7
8
9
10
total 36
-rwxr--r-- 1 ubuntu ubuntu 635 May 31 20:47 cluster.env
-rwxr--r-- 1 ubuntu ubuntu 844 May 31 20:47 istio-token
-rwxr--r-- 1 ubuntu ubuntu 792 May 31 20:47 mesh.yaml
-rwxr--r-- 1 ubuntu ubuntu 1099 May 31 20:47 root-cert.pem
drwx------ 3 root root 4096 May 31 17:09 snap-private-tmp
drwx------ 3 root root 4096 May 31 17:10 systemd-private-2c80bd4b0a5a422abd660bbb9d0caa71-apache2.service-g3XBQh
drwx------ 3 root root 4096 May 31 17:09 systemd-private-2c80bd4b0a5a422abd660bbb9d0caa71-chrony.service-4RVsfV
drwx------ 3 root root 4096 May 31 17:09 systemd-private-2c80bd4b0a5a422abd660bbb9d0caa71-systemd-logind.service-Y9vORu
drwx------ 3 root root 4096 May 31 17:09 systemd-private-2c80bd4b0a5a422abd660bbb9d0caa71-systemd-resolved.service-OQCfOR
🔌 가상머신에 istio-agent 설치 및 설정하기
1. 가상머신 DNS 설정 확인
1
root@forum-vm:~# cat /etc/resolv.conf
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# This is /run/systemd/resolve/stub-resolv.conf managed by man:systemd-resolved(8).
# Do not edit.
#
# This file might be symlinked as /etc/resolv.conf. If you're looking at
# /etc/resolv.conf and seeing this text, you have followed the symlink.
#
# This is a dynamic resolv.conf file for connecting local clients to the
# internal DNS stub resolver of systemd-resolved. This file lists all
# configured search domains.
#
# Run "resolvectl status" to see details about the uplink DNS servers
# currently in use.
#
# Third party programs should typically not access this file directly, but only
# through the symlink at /etc/resolv.conf. To manage man:resolv.conf(5) in a
# different way, replace this symlink by a static file or a different symlink.
#
# See man:systemd-resolved.service(8) for details about the supported modes of
# operation for /etc/resolv.conf.
nameserver 127.0.0.53
options edns0 trust-ad
search ap-northeast-2.compute.internal
1
root@forum-vm:~# resolvectl status
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
Global
Protocols: -LLMNR -mDNS -DNSOverTLS DNSSEC=no/unsupported
resolv.conf mode: stub
Link 2 (ens5)
Current Scopes: DNS
Protocols: +DefaultRoute +LLMNR -mDNS -DNSOverTLS
DNSSEC=no/unsupported
Current DNS Server: 192.168.0.2
DNS Servers: 192.168.0.2
DNS Domain: ap-northeast-2.compute.internal
2. systemd-resolved의 DNS 바인딩 상태 및 포트 확인
1
root@forum-vm:~# ss -tnlp
✅ 출력
1
2
3
4
5
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=354,fd=14))
LISTEN 0 128 0.0.0.0:22 0.0.0.0:* users:(("sshd",pid=673,fd=3))
LISTEN 0 511 *:80 *:* users:(("apache2",pid=2450,fd=4),("apache2",pid=2448,fd=4),("apache2",pid=2447,fd=4))
LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=673,fd=4))
1
root@forum-vm:~# ss -unlp
✅ 출력
1
2
3
4
5
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:* users:(("systemd-resolve",pid=354,fd=13))
UNCONN 0 0 192.168.10.200%ens5:68 0.0.0.0:* users:(("systemd-network",pid=352,fd=15))
UNCONN 0 0 127.0.0.1:323 0.0.0.0:* users:(("chronyd",pid=480,fd=5))
UNCONN 0 0 [::1]:323 [::]:* users:(("chronyd",pid=480,fd=6))
3. iptables 설정 초기 상태 확인
1
2
3
4
root@forum-vm:~# iptables -t nat -L -n -v
iptables -t filter -L -n -v
iptables -t mangle -L -n -v
iptables -t raw -L -n -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
4. istio-sidecar 패키지 다운로드 및 확인
1
2
root@forum-vm:~# curl -LO https://storage.googleapis.com/istio-release/releases/1.17.8/deb/istio-sidecar.deb
file istio-sidecar.deb
✅ 출력
1
2
3
4
5
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 41.4M 0 5503 0 0 14501 0 0:49:56 --:--:-- 0:49:56 43 41.4M 43 18.0M 0 0 12.9M 0 0:00:03 0:00:01 0:00:02 72 41.4M 72 30.0M 0 0 12.0M 0 0:00:03 0:00:02 0:00:01100 41.4M 100 41.4M 0 0 13.9M 0 0:00:02 0:00:02 --:--:-- 13.9M
istio-sidecar.deb: Debian binary package (format 2.0), with control.tar.gz, data compression gz
5. istio-sidecar 패키지 설치
1
root@forum-vm:~# dpkg -i istio-sidecar.deb
✅ 출력
1
2
3
4
5
Selecting previously unselected package istio-sidecar.
(Reading database ... 67385 files and directories currently installed.)
Preparing to unpack istio-sidecar.deb ...
Unpacking istio-sidecar (1.17.8) ...
Setting up istio-sidecar (1.17.8) ...
6. istio 관련 실행 파일 경로 및 버전 확인
1
2
root@forum-vm:~# which pilot-agent
pilot-agent version
✅ 출력
1
2
3
/usr/local/bin/pilot-agent
version.BuildInfo{Version:"1.17.8", GitRevision:"a781f9ee6c511d8f22140d8990c31e577b2a9676", GolangVersion:"go1.20.10", BuildStatus:"Clean", GitTag:"1.17.8"}
1
2
root@forum-vm:~# which envoy
envoy --version
✅ 출력
1
2
3
/usr/local/bin/envoy
envoy version: e1222b5645a29ad3d02b280797ac1219dd88cfbc/1.25.10/Clean/RELEASE/BoringSSL
7. istio 관련 디렉토리 구조 확인
1
root@forum-vm:~# tree /etc/istio
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
/etc/istio
├── config
│ └── mesh
├── envoy
│ ├── cluster.env
│ ├── envoy_bootstrap_tmpl.json
│ └── sidecar.env
├── extensions
│ ├── metadata-exchange-filter.compiled.wasm
│ ├── metadata-exchange-filter.wasm
│ ├── stats-filter.compiled.wasm
│ └── stats-filter.wasm
└── proxy
├── XDS
├── envoy-rev.json
└── grpc-bootstrap.json
4 directories, 11 files
1
root@forum-vm:~# tree /var/lib/istio/
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
/var/lib/istio/
├── config
│ └── mesh
├── envoy
│ ├── cluster.env
│ ├── envoy_bootstrap_tmpl.json
│ └── sidecar.env
├── extensions
│ ├── metadata-exchange-filter.compiled.wasm
│ ├── metadata-exchange-filter.wasm
│ ├── stats-filter.compiled.wasm
│ └── stats-filter.wasm
└── proxy
├── XDS
├── envoy-rev.json
└── grpc-bootstrap.json
4 directories, 11 files
8. 설정 파일 위치에 맞게 복사
1
2
3
4
5
6
7
root@forum-vm:~# mkdir -p /etc/certs
mkdir -p /var/run/secrets/tokens
cp /tmp/root-cert.pem /etc/certs/root-cert.pem
cp /tmp/istio-token /var/run/secrets/tokens/istio-token
cp /tmp/cluster.env /var/lib/istio/envoy/cluster.env
cp /tmp/mesh.yaml /etc/istio/config/mesh
9. /etc/hosts 파일에 istiod 주소 추가
(1) /etc/hosts 파일 내용 확인하기
1
root@forum-vm:~# cat /etc/hosts
✅ 출력
1
2
3
4
5
6
7
8
9
10
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
ff02::3 ip6-allhosts
192.168.10.200 forum-vm
(2) Istio 서비스 도메인 수동 등록하기
1
root@forum-vm:~# echo "192.168.10.10 istiod.istio-system.svc" | sudo sh -c 'cat >> /etc/hosts'
(3) /etc/hosts 수정 내용 확인하기
1
root@forum-vm:~# cat /etc/hosts
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
127.0.0.1 localhost
# The following lines are desirable for IPv6 capable hosts
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
ff02::3 ip6-allhosts
192.168.10.200 forum-vm
192.168.10.10 istiod.istio-system.svc
10. istio-proxy 사용자 확인
1
root@forum-vm:~# cat /etc/passwd | tail -n 3
✅ 출력
1
2
3
ubuntu:x:1000:1000:Ubuntu:/home/ubuntu:/bin/bash
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
istio-proxy:x:998:999::/var/lib/istio:/bin/sh
11. 설정 파일의 소유자 변경
1
2
root@forum-vm:~# tree /etc/istio
chown -R istio-proxy /var/lib/istio /etc/certs /etc/istio/proxy /etc/istio/config /var/run/secrets /etc/certs/root-cert.pem
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
/etc/istio
├── config
│ └── mesh
├── envoy
│ ├── cluster.env
│ ├── envoy_bootstrap_tmpl.json
│ └── sidecar.env
├── extensions
│ ├── metadata-exchange-filter.compiled.wasm
│ ├── metadata-exchange-filter.wasm
│ ├── stats-filter.compiled.wasm
│ └── stats-filter.wasm
└── proxy
├── XDS
├── envoy-rev.json
└── grpc-bootstrap.json
4 directories, 11 files
12. istio-agent 서비스 상태 확인 및 시작
(1) istio 서비스 상태 확인하기
1
root@forum-vm:~# systemctl status istio
✅ 출력
1
2
3
4
○ istio.service - istio-sidecar: The Istio sidecar
Loaded: loaded (/lib/systemd/system/istio.service; disabled; vendo>
Active: inactive (dead)
Docs: http://istio.io/
(2) istio 서비스 시작하기
1
2
root@forum-vm:~# systemctl start istio
systemctl enable istio
✅ 출력
1
Created symlink /etc/systemd/system/multi-user.target.wants/istio.service → /lib/systemd/system/istio.service.
(3) istio 서비스 상태 재확인하기
1
root@forum-vm:~# systemctl status istio
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
● istio.service - istio-sidecar: The Istio sidecar
Loaded: loaded (/lib/systemd/system/istio.service; enabled; vendor preset: enabled)
Active: active (running) since Sat 2025-05-31 21:06:23 KST; 2min 9s ago
Docs: http://istio.io/
Main PID: 7428 (sudo)
Tasks: 17 (limit: 2272)
Memory: 34.0M
CPU: 3.060s
CGroup: /system.slice/istio.service
├─7428 sudo -E -u istio-proxy -s /bin/bash -c "ulimit -n 1024; INSTANCE_IP=192.168.10.200 POD_NAME=forum-vm POD_NAMESPACE=forum-serv>
├─7523 /usr/local/bin/pilot-agent proxy
└─7531 /usr/local/bin/envoy -c etc/istio/proxy/envoy-rev.json --drain-time-s 45 --drain-strategy immediate --local-address-ip-versio>
May 31 21:06:23 forum-vm istio-start.sh[7512]: -A ISTIO_OUTPUT -o lo -p tcp -m tcp ! --dport 53 -m owner ! --gid-owner 998 -j RETURN
May 31 21:06:23 forum-vm istio-start.sh[7512]: -A ISTIO_OUTPUT -m owner --gid-owner 998 -j RETURN
May 31 21:06:23 forum-vm istio-start.sh[7512]: -A ISTIO_OUTPUT -d 127.0.0.53/32 -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 15053
May 31 21:06:23 forum-vm istio-start.sh[7512]: -A ISTIO_OUTPUT -d 127.0.0.1/32 -j RETURN
May 31 21:06:23 forum-vm istio-start.sh[7512]: -A ISTIO_OUTPUT -j ISTIO_REDIRECT
May 31 21:06:23 forum-vm istio-start.sh[7512]: -A ISTIO_REDIRECT -p tcp -j REDIRECT --to-ports 15001
May 31 21:06:23 forum-vm istio-start.sh[7512]: COMMIT
May 31 21:06:23 forum-vm istio-start.sh[7512]: # Completed on Sat May 31 21:06:23 2025
May 31 21:06:23 forum-vm sudo[7428]: root : PWD=/ ; USER=istio-proxy ; COMMAND=/bin/bash -c '\\/bin\\/bash -c ulimit\\ -n\\ 1024\\;\\ INSTANC>
May 31 21:06:23 forum-vm sudo[7428]: pam_unix(sudo:session): session opened for user istio-proxy(uid=998) by (uid=0)
13. istio-agent 서비스 로그 실시간 확인
1
root@forum-vm:~# journalctl -u istio -f
✅ 출력
1
2
3
4
5
6
7
8
9
10
May 31 21:40:53 forum-vm istio-start.sh[17156]: -A ISTIO_OUTPUT -o lo -p tcp -m tcp ! --dport 53 -m owner ! --gid-owner 998 -j RETURN
May 31 21:40:53 forum-vm istio-start.sh[17156]: -A ISTIO_OUTPUT -m owner --gid-owner 998 -j RETURN
May 31 21:40:53 forum-vm istio-start.sh[17156]: -A ISTIO_OUTPUT -d 127.0.0.53/32 -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 15053
May 31 21:40:53 forum-vm istio-start.sh[17156]: -A ISTIO_OUTPUT -d 127.0.0.1/32 -j RETURN
May 31 21:40:53 forum-vm istio-start.sh[17156]: -A ISTIO_OUTPUT -j ISTIO_REDIRECT
May 31 21:40:53 forum-vm istio-start.sh[17156]: -A ISTIO_REDIRECT -p tcp -j REDIRECT --to-ports 15001
May 31 21:40:53 forum-vm istio-start.sh[17156]: COMMIT
May 31 21:40:53 forum-vm istio-start.sh[17156]: # Completed on Sat May 31 21:40:53 2025
May 31 21:40:53 forum-vm sudo[17080]: root : PWD=/ ; USER=istio-proxy ; COMMAND=/bin/bash -c '\\/bin\\/bash -c ulimit\\ -n\\ 1024\\;\\ INSTANCE_IP\\=192\\.168\\.10\\.200\\ POD_NAME\\=forum-vm\\ POD_NAMESPACE\\=forum-services\\ exec\\ \\/usr\\/local\\/bin\\/pilot-agent\\ proxy\\ \\ 2\\>\\>\\ \\.\\/var\\/log\\/istio\\/istio\\.err\\.log\\ \\>\\>\\ \\.\\/var\\/log\\/istio\\/istio\\.log'
May 31 21:40:53 forum-vm sudo[17080]: pam_unix(sudo:session): session opened for user istio-proxy(uid=998) by (uid=0)
14. iptables 설정을 적용하는 스크립트 위치 확인
(1) istio-start.sh 경로 확인하기
1
root@forum-vm:~# which istio-start.sh
✅ 출력
1
/usr/local/bin/istio-start.sh
(2) istio-start.sh 스크립트 내용 확인하기
해당 스크립트 파일이 iptables 셋팅함
1
root@forum-vm:~# cat /usr/local/bin/istio-start.sh
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
...
set -e
# Match pilot/docker/Dockerfile.proxyv2
export ISTIO_META_ISTIO_VERSION="1.17.0"
set -a
# Load optional config variables
ISTIO_SIDECAR_CONFIG=${ISTIO_SIDECAR_CONFIG:-./var/lib/istio/envoy/sidecar.env}
if [[ -r ${ISTIO_SIDECAR_CONFIG} ]]; then
# shellcheck disable=SC1090
. "$ISTIO_SIDECAR_CONFIG"
fi
# Load config variables ISTIO_SYSTEM_NAMESPACE, CONTROL_PLANE_AUTH_POLICY
ISTIO_CLUSTER_CONFIG=${ISTIO_CLUSTER_CONFIG:-./var/lib/istio/envoy/cluster.env}
if [[ -r ${ISTIO_CLUSTER_CONFIG} ]]; then
# shellcheck disable=SC1090
. "$ISTIO_CLUSTER_CONFIG"
fi
set +a
# Set defaults
ISTIO_BIN_BASE=${ISTIO_BIN_BASE:-/usr/local/bin}
ISTIO_LOG_DIR=${ISTIO_LOG_DIR:-./var/log/istio}
NS=${ISTIO_NAMESPACE:-default}
SVC=${ISTIO_SERVICE:-rawvm}
ISTIO_SYSTEM_NAMESPACE=${ISTIO_SYSTEM_NAMESPACE:-istio-system}
# If set, override the default
CONTROL_PLANE_AUTH_POLICY=${ISTIO_CP_AUTH:-"MUTUAL_TLS"}
if [ -z "${ISTIO_SVC_IP:-}" ]; then
ISTIO_SVC_IP=$(hostname --all-ip-addresses | cut -d ' ' -f 1)
fi
if [ -z "${POD_NAME:-}" ]; then
POD_NAME=$(hostname -s)
fi
if [[ ${1-} == "clean" ]] ; then
if [ "${ISTIO_CUSTOM_IP_TABLES}" != "true" ] ; then
# clean the previous Istio iptables chains.
"${ISTIO_BIN_BASE}/pilot-agent" istio-clean-iptables
fi
exit 0
fi
# Init option will only initialize iptables. set ISTIO_CUSTOM_IP_TABLES to true if you would like to ignore this step
if [ "${ISTIO_CUSTOM_IP_TABLES}" != "true" ] ; then
if [[ ${1-} == "init" || ${1-} == "-p" ]] ; then
# clean the previous Istio iptables chains. This part is different from the init image mode,
# where the init container runs in a fresh environment and there cannot be previous Istio chains
"${ISTIO_BIN_BASE}/pilot-agent" istio-clean-iptables
# Update iptables, based on current config. This is for backward compatibility with the init image mode.
# The sidecar image can replace the k8s init image, to avoid downloading 2 different images.
"${ISTIO_BIN_BASE}/pilot-agent" istio-iptables "${@}"
exit 0
fi
if [[ ${1-} != "run" ]] ; then
# clean the previous Istio iptables chains. This part is different from the init image mode,
# where the init container runs in a fresh environment and there cannot be previous Istio chains
"${ISTIO_BIN_BASE}/pilot-agent" istio-clean-iptables
# Update iptables, based on config file
"${ISTIO_BIN_BASE}/pilot-agent" istio-iptables
fi
fi
EXEC_USER=${EXEC_USER:-istio-proxy}
if [ "${ISTIO_INBOUND_INTERCEPTION_MODE}" = "TPROXY" ] ; then
# In order to allow redirect inbound traffic using TPROXY, run envoy with the CAP_NET_ADMIN capability.
# This allows configuring listeners with the "transparent" socket option set to true.
EXEC_USER=root
fi
# The default matches the default istio.yaml - use sidecar.env to override ISTIO_PILOT_PORT or CA_ADDR if you
# enable auth. This requires node-agent to be running.
DEFAULT_PILOT_ADDRESS="istiod.${ISTIO_SYSTEM_NAMESPACE}.svc:15012"
CUSTOM_PILOT_ADDRESS="${PILOT_ADDRESS:-}"
if [ -z "${CUSTOM_PILOT_ADDRESS}" ] && [ -n "${ISTIO_PILOT_PORT:-}" ]; then
CUSTOM_PILOT_ADDRESS=istiod.${ISTIO_SYSTEM_NAMESPACE}.svc:${ISTIO_PILOT_PORT}
fi
# CA_ADDR > PILOT_ADDRESS > ISTIO_PILOT_PORT
CA_ADDR=${CA_ADDR:-${CUSTOM_PILOT_ADDRESS:-${DEFAULT_PILOT_ADDRESS}}}
PROV_CERT=${PROV_CERT-./etc/certs}
OUTPUT_CERTS=${OUTPUT_CERTS-./etc/certs}
export PROV_CERT
export OUTPUT_CERTS
export CA_ADDR
# If predefined ISTIO_AGENT_FLAGS is null, make it an empty string.
ISTIO_AGENT_FLAGS=${ISTIO_AGENT_FLAGS:-}
# Split ISTIO_AGENT_FLAGS by spaces.
IFS=' ' read -r -a ISTIO_AGENT_FLAGS_ARRAY <<< "$ISTIO_AGENT_FLAGS"
DEFAULT_PROXY_CONFIG="
serviceCluster: $SVC
controlPlaneAuthPolicy: ${CONTROL_PLANE_AUTH_POLICY}
"
if [ -n "${CUSTOM_PILOT_ADDRESS}" ]; then
PROXY_CONFIG="$PROXY_CONFIG
discoveryAddress: ${CUSTOM_PILOT_ADDRESS}
"
fi
# PROXY_CONFIG > PILOT_ADDRESS > ISTIO_PILOT_PORT
export PROXY_CONFIG=${PROXY_CONFIG:-${DEFAULT_PROXY_CONFIG}}
if [ "${EXEC_USER}" == "${USER:-}" ] ; then
# if started as istio-proxy (or current user), do a normal start, without
# redirecting stderr.
INSTANCE_IP=${ISTIO_SVC_IP} POD_NAME=${POD_NAME} POD_NAMESPACE=${NS} "${ISTIO_BIN_BASE}/pilot-agent" proxy "${ISTIO_AGENT_FLAGS_ARRAY[@]}"
else
# su will mess with the limits set on the process we run. This may lead to quickly exhausting the file limits
# We will get the host limit and set it in the child as well.
# TODO(https://superuser.com/questions/1645513/why-does-executing-a-command-in-su-change-limits) can we do better?
currentLimit=$(ulimit -n)
# Will run: ${ISTIO_BIN_BASE}/envoy -c $ENVOY_CFG --restart-epoch 0 --drain-time-s 2 --parent-shutdown-time-s 3 --service-cluster $SVC --service-node 'sidecar~${ISTIO_SVC_IP}~${POD_NAME}.${NS}.svc.cluster.local~${NS}.svc.cluster.local' $ISTIO_DEBUG >${ISTIO_LOG_DIR}/istio.log" istio-proxy
exec sudo -E -u "${EXEC_USER}" -s /bin/bash -c "ulimit -n ${currentLimit}; INSTANCE_IP=${ISTIO_SVC_IP} POD_NAME=${POD_NAME} POD_NAMESPACE=${NS} exec ${ISTIO_BIN_BASE}/pilot-agent proxy ${ISTIO_AGENT_FLAGS_ARRAY[*]} 2>> ${ISTIO_LOG_DIR}/istio.err.log >> ${ISTIO_LOG_DIR}/istio.log"
fi
15. 인증서 디렉터리 확인
1
2
3
4
5
6
7
root@forum-vm:~# tree /etc/certs/
/etc/certs/
├── cert-chain.pem
├── key.pem
└── root-cert.pem
0 directories, 3 files
16. istio 관련 프로세스 확인
1
root@forum-vm:~# ps aux |grep istio
✅ 출력
1
2
3
4
root 17080 0.0 0.2 12320 5760 ? Ss 21:40 0:00 sudo -E -u istio-proxy -s /bin/bash -c ulimit -n 1024; INSTANCE_IP=192.168.10.200 POD_NAME=forum-vm POD_NAMESPACE=forum-services exec /usr/local/bin/pilot-agent proxy 2>> ./var/log/istio/istio.err.log >> ./var/log/istio/istio.log
istio-p+ 17166 0.4 2.4 754732 47468 ? Sl 21:40 0:14 /usr/local/bin/pilot-agent proxy
istio-p+ 17174 0.1 3.1 186136 61184 ? Sl 21:40 0:05 /usr/local/bin/envoy -c etc/istio/proxy/envoy-rev.json --drain-time-s 45 --drain-strategy immediate --local-address-ip-version v4 --file-flush-interval-msec 1000 --disable-hot-restart --allow-unknown-static-fields --log-format %Y-%m-%dT%T.%fZ?%l?envoy %n %g:%#?%v?thread=%t -l warning --component-log-level misc:error --concurrency 2
root 17711 0.0 0.1 7008 2432 pts/1 S+ 22:33 0:00 grep --color=auto istio
17. iptables NAT 규칙 재확인
1
root@forum-vm:~# iptables -t nat -L -n -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
12 600 ISTIO_INBOUND tcp -- * * 0.0.0.0/0 0.0.0.0/0
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
268 16080 ISTIO_OUTPUT tcp -- * * 0.0.0.0/0 0.0.0.0/0
109 7117 RETURN udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner UID match 998
0 0 RETURN udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner GID match 998
34 3550 REDIRECT udp -- * * 0.0.0.0/0 127.0.0.53 udp dpt:53 redir ports 15053
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain ISTIO_INBOUND (1 references)
pkts bytes target prot opt in out source destination
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15008
5 300 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15090
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15021
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15020
7 300 ISTIO_IN_REDIRECT tcp -- * * 0.0.0.0/0 0.0.0.0/0
Chain ISTIO_IN_REDIRECT (3 references)
pkts bytes target prot opt in out source destination
7 300 REDIRECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 redir ports 15006
Chain ISTIO_OUTPUT (1 references)
pkts bytes target prot opt in out source destination
62 3720 RETURN all -- * lo 127.0.0.6 0.0.0.0/0
0 0 ISTIO_IN_REDIRECT tcp -- * lo 0.0.0.0/0 !127.0.0.1 tcp dpt:!53 owner UID match 998
0 0 RETURN tcp -- * lo 0.0.0.0/0 0.0.0.0/0 tcp dpt:!53 ! owner UID match 998
203 12180 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 owner UID match 998
0 0 ISTIO_IN_REDIRECT all -- * lo 0.0.0.0/0 !127.0.0.1 owner GID match 998
0 0 RETURN tcp -- * lo 0.0.0.0/0 0.0.0.0/0 tcp dpt:!53 ! owner GID match 998
0 0 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 owner GID match 998
0 0 REDIRECT tcp -- * * 0.0.0.0/0 127.0.0.53 tcp dpt:53 redir ports 15053
0 0 RETURN all -- * * 0.0.0.0/0 127.0.0.1
3 180 ISTIO_REDIRECT all -- * * 0.0.0.0/0 0.0.0.0/0
Chain ISTIO_REDIRECT (1 references)
pkts bytes target prot opt in out source destination
3 180 REDIRECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 redir ports 15001
18. iptables filter/mangle 테이블 재확인
1
2
root@forum-vm:~# iptables -t filter -L -n -v
iptables -t mangle -L -n -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
19. iptables raw 테이블에서 UDP 53 확인
1
root@forum-vm:~# iptables -t raw -L -n -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 CT udp -- * * 0.0.0.0/0 127.0.0.53 udp spt:53 CT zone 1
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
218 17658 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner UID match 998 CT zone 1
40 3680 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:15053 owner UID match 998 CT zone 2
0 0 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner GID match 998 CT zone 1
0 0 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:15053 owner GID match 998 CT zone 2
258 21778 CT udp -- * * 0.0.0.0/0 127.0.0.53 udp dpt:53 CT zone 2
🛰️ 에이전트 로그 확인하기
1
2
3
root@forum-vm:~# cat /var/log/istio/istio.log | grep xdsproxy
2025-05-31T12:06:23.773193Z info xdsproxy Initializing with upstream address "istiod.istio-system.svc:15012" and cluster "west-cluster"
2025-05-31T12:06:23.909784Z info xdsproxy connected to upstream XDS server: istiod.istio-system.svc:15012
🔍 워크로드가 메시에 등록됐는지 확인하기
1. WorkloadEntry 리소스 목록 조회
1
(⎈|default:N/A) root@k3s-s:~# kubectl get workloadentries -n forum-services
✅ 출력
1
2
NAME AGE ADDRESS
forum-192.168.10.200-vm-network 6m38s 192.168.10.200
2. WorkloadEntry 리소스 상세 확인
1
(⎈|default:N/A) root@k3s-s:~# kc get workloadentries -n forum-services -o yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
apiVersion: v1
items:
- apiVersion: networking.istio.io/v1beta1
kind: WorkloadEntry
metadata:
annotations:
istio.io/autoRegistrationGroup: forum
istio.io/connectedAt: "2025-05-31T13:28:46.456729292Z"
istio.io/workloadController: istiod-d6549b9fc-gxjc5
proxy.istio.io/health-checks-enabled: "true"
creationTimestamp: "2025-05-31T13:28:46Z"
generation: 1
labels:
app: forum
service.istio.io/canonical-name: forum
service.istio.io/canonical-revision: latest
name: forum-192.168.10.200-vm-network
namespace: forum-services
ownerReferences:
- apiVersion: networking.istio.io/v1alpha3
controller: true
kind: WorkloadGroup
name: forum
uid: 110b29ea-752c-4c25-940c-64e0a0aae5f1
resourceVersion: "14361"
uid: a52b0887-d4ea-4105-bb9f-1f8889b6c702
spec:
address: 192.168.10.200
labels:
app: forum
service.istio.io/canonical-name: forum
service.istio.io/canonical-revision: latest
network: vm-network
serviceAccount: forum-sa
status:
conditions:
- lastProbeTime: "2025-05-31T13:28:46.519563231Z"
lastTransitionTime: "2025-05-31T13:28:46.519563945Z"
message: 'config not received from XDS server (is Istiod running?): cds updates:
0 successful, 0 rejected; lds updates: 0 successful, 0 rejected'
status: "False"
type: Healthy
kind: List
metadata:
resourceVersion: ""
3. proxy-status 명령으로 동기화 상태 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-status
✅ 출력
1
2
3
4
5
6
NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
catalog-77fdb4997c-fhpf9.istioinaction west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-d6549b9fc-gxjc5 1.17.8
forum-vm.forum-services west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-d6549b9fc-gxjc5 1.17.0
istio-eastwestgateway-86f6cb4699-gwbwq.istio-system west-cluster SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-d6549b9fc-gxjc5 1.17.8
istio-ingressgateway-7b7ccd6454-cdvc6.istio-system west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-d6549b9fc-gxjc5 1.17.8
webapp-684c568c59-6x29p.istioinaction west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-d6549b9fc-gxjc5 1.17.8
🧪 클러스터 서비스로 트래픽 라우팅하기
1. termshark로 DNS 패킷 모니터링 시작하기
1
root@forum-vm:~# tcpdump -i any -w - udp port 53 | termshark
✅ 출력
1
2
3
tcpdump: data link type LINUX_SLL2
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
(The termshark UI will start when packets are detected...)
2. VM에서 서비스 도메인으로 DNS 질의 수행
1
2
root@forum-vm:~# dig +short webapp.istioinaction
10.10.200.134
1
2
root@forum-vm:~# dig +short catalog.istioinaction
10.10.200.37
3. 클러스터 내 서비스 IP 확인
1
(⎈|default:N/A) root@k3s-s:~# k get svc -A
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.10.200.1 <none> 443/TCP 5h34m
istio-system grafana NodePort 10.10.200.65 <none> 3000:30002/TCP 3h54m
istio-system istio-eastwestgateway LoadBalancer 10.10.200.254 192.168.10.10 15021:31128/TCP,15443:32755/TCP,15012:31286/TCP,15017:32181/TCP 3h17m
istio-system istio-ingressgateway NodePort 10.10.200.56 <none> 15021:32513/TCP,80:30000/TCP,443:30005/TCP,31400:30959/TCP,15443:32461/TCP 3h55m
istio-system istiod ClusterIP 10.10.200.61 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 3h55m
istio-system jaeger-collector ClusterIP 10.10.200.104 <none> 14268/TCP,14250/TCP,9411/TCP 3h54m
istio-system kiali NodePort 10.10.200.187 <none> 20001:30003/TCP,9090:32679/TCP 3h54m
istio-system prometheus NodePort 10.10.200.128 <none> 9090:30001/TCP 3h54m
istio-system tracing NodePort 10.10.200.67 <none> 80:30004/TCP,16685:31406/TCP 3h54m
istio-system zipkin ClusterIP 10.10.200.41 <none> 9411/TCP 3h54m
istioinaction catalog ClusterIP 10.10.200.37 <none> 80/TCP 3h49m
istioinaction webapp ClusterIP 10.10.200.134 <none> 80/TCP 3h49m
kube-system kube-dns ClusterIP 10.10.200.10 <none> 53/UDP,53/TCP,9153/TCP 5h34m
kube-system metrics-server ClusterIP 10.10.200.82 <none> 443/TCP 5h34m
4. VM에서 웹 서비스 엔드포인트에 직접 요청 확인
1
root@forum-vm:~# curl -s webapp.istioinaction/api/catalog/items/1 | jq
✅ 출력
1
2
3
4
5
6
7
{
"id": 1,
"color": "amber",
"department": "Eyewear",
"name": "Elinor Glasses",
"price": "282.00"
}
1
root@forum-vm:~# watch curl -s webapp.istioinaction/api/catalog/items/1
✅ 출력
1
2
3
Every 2.0s: curl -s webapp.istioinaction/api/catalog/items/1 forum-vm: Sat May 31 22:56:53 2025
{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"}
5. Envoy가 연결 중인 데이터 플레인 소켓 모니터링
1
root@forum-vm:~# watch -d ss -tnp
✅ 출력
1
2
3
4
5
6
7
8
Every 2.0s: ss -tnp forum-vm: Sat May 31 22:58:38 2025
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
ESTAB 0 0 192.168.10.200:35324 192.168.10.10:15443 users:(("envoy",pid=17174,fd=41))
ESTAB 0 0 192.168.10.200:22 182.230.60.93:38018 users:(("sshd",pid=17844,fd=4),("sshd",pid=17788,fd=4))
ESTAB 0 0 192.168.10.200:58886 192.168.10.10:15443 users:(("envoy",pid=17174,fd=40))
ESTAB 0 0 192.168.10.200:33192 192.168.10.10:15012 users:(("pilot-agent",pid=17166,fd=15))
ESTAB 0 0 192.168.10.200:22 182.230.60.93:44012 users:(("sshd",pid=2920,fd=4),("sshd",pid=2866,fd=4))
6. iptables NAT 테이블을 실시간 모니터링하며 트래픽 흐름 분석
1
root@forum-vm:~# watch -d iptables -t nat -L -n -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
Every 2.0s: iptables -t nat -L -n -v forum-vm: Sat May 31 23:12:31 2025
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
20 968 ISTIO_INBOUND tcp -- * * 0.0.0.0/0 0.0.0.0/0
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1235 74100 ISTIO_OUTPUT tcp -- * * 0.0.0.0/0 0.0.0.0/0
194 12710 RETURN udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner UID match 998
0 0 RETURN udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner GID match 998
530 41938 REDIRECT udp -- * * 0.0.0.0/0 127.0.0.53 udp dpt:53 redir ports 15053
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain ISTIO_INBOUND (1 references)
pkts bytes target prot opt in out source destination
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15008
6 360 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15090
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15021
0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:15020
14 608 ISTIO_IN_REDIRECT tcp -- * * 0.0.0.0/0 0.0.0.0/0
Chain ISTIO_IN_REDIRECT (3 references)
pkts bytes target prot opt in out source destination
14 608 REDIRECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 redir ports 15006
Chain ISTIO_OUTPUT (1 references)
pkts bytes target prot opt in out source destination
526 31560 RETURN all -- * lo 127.0.0.6 0.0.0.0/0
0 0 ISTIO_IN_REDIRECT tcp -- * lo 0.0.0.0/0 !127.0.0.1 tcp dpt:!53 owner UID match 998
20 1200 RETURN tcp -- * lo 0.0.0.0/0 0.0.0.0/0 tcp dpt:!53 ! owner UID match 998
211 12660 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 owner UID match 998
0 0 ISTIO_IN_REDIRECT all -- * lo 0.0.0.0/0 !127.0.0.1 owner GID match 998
0 0 RETURN tcp -- * lo 0.0.0.0/0 0.0.0.0/0 tcp dpt:!53 ! owner GID match 998
0 0 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0 owner GID match 998
7. iptables raw 테이블을 실시간 모니터링하며 DNS 리디렉션 확인
1
root@forum-vm:~# watch -d iptables -t raw -L -n -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
Every 2.0s: iptables -t raw -L -n -v forum-vm: Sat May 31 23:13:41 2025
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 CT udp -- * * 0.0.0.0/0 127.0.0.53 udp spt:53 CT zone 1
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
382 30882 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner UID match 998 CT zone 1
1074 92089 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:15053 owner UID match 998 CT zone 2
0 0 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:53 owner GID match 998 CT zone 1
0 0 CT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:15053 owner GID match 998 CT zone 2
1456 115K CT udp -- * * 0.0.0.0/0 127.0.0.53 udp dpt:53 CT zone 2
8. 클러스터 외부에서 반복적으로 webapp 접근 테스트
1
while true; do curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/catalog/ ; echo; date; sleep 1; done
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
Sat May 31 11:16:48 PM KST 2025
Sat May 31 11:16:49 PM KST 2025
Sat May 31 11:16:50 PM KST 2025
Sat May 31 11:16:51 PM KST 2025
Sat May 31 11:16:52 PM KST 2025
...
🔁 트래픽을 WorkloadEntry로 라우팅하기
1. forum 서비스 리소스 정의 확인
1
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/services/forum/kubernetes/forum-svc.yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
---
apiVersion: v1
kind: Service
metadata:
labels:
app: forum
name: forum
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 8080
selector:
app: forum
2. forum 서비스 리소스 생성
1
2
3
4
(⎈|default:N/A) root@k3s-s:~# kubectl apply -f istio-in-action/book-source-code-master/services/forum/kubernetes/forum-svc.yaml -n forum-services
# 결과
service/forum created
3. forum 서비스와 엔드포인트 조회
1
(⎈|default:N/A) root@k3s-s:~# kubectl get svc,ep -n forum-services
✅ 출력
1
2
3
4
5
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/forum ClusterIP 10.10.200.76 <none> 80/TCP 28s
NAME ENDPOINTS AGE
endpoints/forum <none> 28s
4. webapp 프록시의 라우팅 설정 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config route deploy/webapp.istioinaction
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
NAME DOMAINS MATCH VIRTUAL SERVICE
jaeger-collector.istio-system.svc.cluster.local:14268 * /*
inbound|8080|| * /*
istio-eastwestgateway.istio-system.svc.cluster.local:15021 * /*
jaeger-collector.istio-system.svc.cluster.local:14250 * /*
grafana.istio-system.svc.cluster.local:3000 * /*
20001 kiali.istio-system, 10.10.200.187 /*
kube-dns.kube-system.svc.cluster.local:9153 * /*
80 catalog, catalog.istioinaction + 1 more... /*
80 forum.forum-services, 10.10.200.76 /*
80 istio-ingressgateway.istio-system, 10.10.200.56 /*
80 tracing.istio-system, 10.10.200.67 /*
80 webapp, webapp.istioinaction + 1 more... /*
* /healthz/ready*
istio-ingressgateway.istio-system.svc.cluster.local:15021 * /*
9090 kiali.istio-system, 10.10.200.187 /*
9090 prometheus.istio-system, 10.10.200.128 /*
15014 istiod.istio-system, 10.10.200.61 /*
15010 istiod.istio-system, 10.10.200.61 /*
16685 tracing.istio-system, 10.10.200.67 /*
InboundPassthroughClusterIpv4 * /*
InboundPassthroughClusterIpv4 * /*
* /stats/prometheus*
9411 jaeger-collector.istio-system, 10.10.200.104 /*
9411 zipkin.istio-system, 10.10.200.41 /*
inbound|8080|| * /*
istio-eastwestgateway.istio-system.svc.cluster.local:15443 * /*
5. forum 서비스에 대한 상세 라우팅 정보 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config route deploy/webapp.istioinaction --name 80 -o json
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
...
{
"name": "forum.forum-services.svc.cluster.local:80",
"domains": [
"forum.forum-services.svc.cluster.local",
"forum.forum-services",
"forum.forum-services.svc",
"10.10.200.76"
],
"routes": [
{
"name": "default",
"match": {
"prefix": "/"
},
"route": {
"cluster": "outbound|80||forum.forum-services.svc.cluster.local",
"timeout": "0s",
"retryPolicy": {
"retryOn": "connect-failure,refused-stream,unavailable,cancelled,retriable-status-codes",
"numRetries": 2,
"retryHostPredicate": [
{
"name": "envoy.retry_host_predicates.previous_hosts",
"typedConfig": {
"@type": "type.googleapis.com/envoy.extensions.retry.host.previous_hosts.v3.PreviousHostsPredicate"
}
}
],
"hostSelectionRetryMaxAttempts": "5",
"retriableStatusCodes": [
503
]
},
"maxGrpcTimeout": "0s"
},
"decorator": {
"operation": "forum.forum-services.svc.cluster.local:80/*"
}
}
],
...
6. webapp 프록시의 forum 클러스터 구성 정보 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config cluster deploy/webapp.istioinaction --fqdn forum.forum-services.svc.cluster.local
✅ 출력
1
2
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
forum.forum-services.svc.cluster.local 80 - outbound EDS
7. webapp 프록시에서 forum 엔드포인트 조회 (미존재 확인)
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config endpoint deploy/webapp.istioinaction
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.10.200.41:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.16.0.10:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
172.16.0.11:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
172.16.0.12:8080 HEALTHY OK inbound|8080||
172.16.0.12:8080 HEALTHY OK outbound|80||webapp.istioinaction.svc.cluster.local
172.16.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
172.16.0.14:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
172.16.0.14:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
172.16.0.14:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
172.16.0.14:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
172.16.0.16:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
172.16.0.16:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
172.16.0.16:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
172.16.0.16:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
172.16.0.16:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
172.16.0.18:15012 HEALTHY OK outbound|15012||istio-eastwestgateway.istio-system.svc.cluster.local
172.16.0.18:15017 HEALTHY OK outbound|15017||istio-eastwestgateway.istio-system.svc.cluster.local
172.16.0.18:15021 HEALTHY OK outbound|15021||istio-eastwestgateway.istio-system.svc.cluster.local
172.16.0.18:15443 HEALTHY OK outbound|15443||istio-eastwestgateway.istio-system.svc.cluster.local
172.16.0.3:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
172.16.0.3:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
172.16.0.4:10250 HEALTHY OK outbound|443||metrics-server.kube-system.svc.cluster.local
172.16.0.8:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
172.16.0.8:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
172.16.0.8:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
172.16.0.8:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
172.16.0.8:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
172.16.0.8:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
172.16.0.9:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
172.16.0.9:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
192.168.10.10:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
1
2
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config endpoint deploy/webapp.istioinaction | grep forum
# 없다.
🐞 forum VM의 Envoy 구성을 통한 디버깅
https://istio.io/v1.17/docs/ops/diagnostic-tools/virtual-machines/
1. forum VM에서 istioctl 설치
1
2
3
4
5
root@forum-vm:~# export ISTIOV=1.17.8
echo 'export ISTIOV=1.17.8' >> /root/.bashrc
curl -s -L https://istio.io/downloadIstio | ISTIO_VERSION=$ISTIOV sh -
cp istio-$ISTIOV/bin/istioctl /usr/local/bin/istioctl
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
Downloading istio-1.17.8 from https://github.com/istio/istio/releases/download/1.17.8/istio-1.17.8-linux-amd64.tar.gz ...
Istio 1.17.8 download complete!
The Istio release archive has been downloaded to the istio-1.17.8 directory.
To configure the istioctl client tool for your workstation,
add the /root/istio-1.17.8/bin directory to your environment path variable with:
export PATH="$PATH:/root/istio-1.17.8/bin"
Begin the Istio pre-installation check by running:
istioctl x precheck
Try Istio in ambient mode
https://istio.io/latest/docs/ambient/getting-started/
Try Istio in sidecar mode
https://istio.io/latest/docs/setup/getting-started/
Install guides for ambient mode
https://istio.io/latest/docs/ambient/install/
Install guides for sidecar mode
https://istio.io/latest/docs/setup/install/
Need more information? Visit https://istio.io/latest/docs/
2. forum VM에서 Listener 설정 확인
1
root@forum-vm:~# curl -s localhost:15000/config_dump | istioctl proxy-config listener --file -
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
ADDRESS PORT MATCH DESTINATION
10.10.200.10 53 ALL Cluster: outbound|53||kube-dns.kube-system.svc.cluster.local
0.0.0.0 80 Trans: raw_buffer; App: http/1.1,h2c Route: 80
0.0.0.0 80 ALL PassthroughCluster
10.10.200.1 443 ALL Cluster: outbound|443||kubernetes.default.svc.cluster.local
10.10.200.56 443 ALL Cluster: outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.200.61 443 ALL Cluster: outbound|443||istiod.istio-system.svc.cluster.local
10.10.200.82 443 ALL Cluster: outbound|443||metrics-server.kube-system.svc.cluster.local
10.10.200.65 3000 Trans: raw_buffer; App: http/1.1,h2c Route: grafana.istio-system.svc.cluster.local:3000
10.10.200.65 3000 ALL Cluster: outbound|3000||grafana.istio-system.svc.cluster.local
0.0.0.0 9090 Trans: raw_buffer; App: http/1.1,h2c Route: 9090
0.0.0.0 9090 ALL PassthroughCluster
10.10.200.10 9153 Trans: raw_buffer; App: http/1.1,h2c Route: kube-dns.kube-system.svc.cluster.local:9153
10.10.200.10 9153 ALL Cluster: outbound|9153||kube-dns.kube-system.svc.cluster.local
0.0.0.0 9411 Trans: raw_buffer; App: http/1.1,h2c Route: 9411
0.0.0.0 9411 ALL PassthroughCluster
10.10.200.104 14250 Trans: raw_buffer; App: http/1.1,h2c Route: jaeger-collector.istio-system.svc.cluster.local:14250
10.10.200.104 14250 ALL Cluster: outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.10.200.104 14268 Trans: raw_buffer; App: http/1.1,h2c Route: jaeger-collector.istio-system.svc.cluster.local:14268
10.10.200.104 14268 ALL Cluster: outbound|14268||jaeger-collector.istio-system.svc.cluster.local
0.0.0.0 15001 ALL PassthroughCluster
0.0.0.0 15001 Addr: *:15001 Non-HTTP/Non-TCP
0.0.0.0 15006 Addr: *:15006 Non-HTTP/Non-TCP
0.0.0.0 15006 Trans: tls; App: istio-http/1.0,istio-http/1.1,istio-h2; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: raw_buffer; App: http/1.1,h2c; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: tls; App: TCP TLS; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: raw_buffer; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: tls; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15010 Trans: raw_buffer; App: http/1.1,h2c Route: 15010
0.0.0.0 15010 ALL PassthroughCluster
10.10.200.254 15012 ALL Cluster: outbound|15012||istio-eastwestgateway.istio-system.svc.cluster.local
10.10.200.61 15012 ALL Cluster: outbound|15012||istiod.istio-system.svc.cluster.local
0.0.0.0 15014 Trans: raw_buffer; App: http/1.1,h2c Route: 15014
0.0.0.0 15014 ALL PassthroughCluster
10.10.200.254 15017 ALL Cluster: outbound|15017||istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
10.10.200.254 15021 Trans: raw_buffer; App: http/1.1,h2c Route: istio-eastwestgateway.istio-system.svc.cluster.local:15021
10.10.200.254 15021 ALL Cluster: outbound|15021||istio-eastwestgateway.istio-system.svc.cluster.local
10.10.200.56 15021 Trans: raw_buffer; App: http/1.1,h2c Route: istio-ingressgateway.istio-system.svc.cluster.local:15021
10.10.200.56 15021 ALL Cluster: outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
10.10.200.254 15443 Trans: raw_buffer; App: http/1.1,h2c Route: istio-eastwestgateway.istio-system.svc.cluster.local:15443
10.10.200.254 15443 ALL Cluster: outbound|15443||istio-eastwestgateway.istio-system.svc.cluster.local
10.10.200.56 15443 ALL Cluster: outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 16685 Trans: raw_buffer; App: http/1.1,h2c Route: 16685
0.0.0.0 16685 ALL PassthroughCluster
0.0.0.0 20001 Trans: raw_buffer; App: http/1.1,h2c Route: 20001
0.0.0.0 20001 ALL PassthroughCluster
10.10.200.56 31400 ALL Cluster: outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
3. forum VM에서 Cluster 설정 확인
1
root@forum-vm:~# curl -s localhost:15000/config_dump | istioctl proxy-config clusters --file -
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
InboundPassthroughClusterIpv4 - - - ORIGINAL_DST
PassthroughCluster - - - ORIGINAL_DST
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
forum.forum-services.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15012 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15017 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metrics-server.kube-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
webapp.istioinaction.svc.cluster.local 80 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
📈 라우팅 테스트 및 문제 확인
1. webapp에서 forum 서비스 클러스터 설정 다시 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config cluster deploy/webapp.istioinaction --fqdn forum.forum-services.svc.cluster.local
✅ 출력
1
2
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
forum.forum-services.svc.cluster.local 80 - outbound EDS
2. forum 엔드포인트가 존재하지 않음을 다시 확인
1
2
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config endpoint deploy/webapp.istioinaction | grep forum
# 없다.
3. webapp envoy 로그 실시간 모니터링
1
(⎈|default:N/A) root@k3s-s:~# kubectl logs -n istioinaction deploy/webapp -c istio-proxy -f
✅ 출력
1
2
3
4
...
[2025-05-31T14:37:34.981Z] "GET /api/catalog/items/1 HTTP/1.1" 200 - via_upstream - "-" 0 88 5 5 "-" "curl/7.81.0" "b0a770ab-e83d-4dae-bb0a-59cc2a2642e7" "webapp.istioinaction" "172.16.0.12:8080" inbound|8080|| 127.0.0.6:46585 172.16.0.12:8080 172.16.0.18:56532 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
[2025-05-31T14:37:37.001Z] "GET /items/1 HTTP/1.1" 200 - via_upstream - "-" 0 109 2 2 "-" "beegoServer" "cc7bfecc-49f1-4b7f-a928-6973f974e33f" "catalog.istioinaction.svc.cluster.local:80" "172.16.0.13:3000" outbound|80||catalog.istioinaction.svc.cluster.local 172.16.0.12:46574 10.10.200.37:80 172.16.0.12:57214 - default
[2025-05-31T14:37:36.998Z] "GET /api/catalog/items/1 HTTP/1.1" 200 - via_upstream - "-" 0 88 5 5 "-" "curl/7.81.0" "cc7bfecc-49f1-4b7f-a928-6973f974e33f" "webapp.istioinaction" "172.16.0.12:8080" inbound|8080|| 127.0.0.6:46585 172.16.0.12:8080 172.16.0.18:56532 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
📤 애플리케이션 요청 시도 및 응답 확인
1. 자신의 PC에서 catalog 요청 테스트
1
curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/catalog/
✅ 출력
1
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
1
2
[2025-05-31T14:41:31.899Z] "GET /items HTTP/1.1" 200 - via_upstream - "-" 0 502 3 2 "182.230.60.93" "beegoServer" "9d448c6e-5cb3-4ce7-81ca-88a0255ffc5c" "catalog.istioinaction.svc.cluster.local:80" "172.16.0.13:3000" outbound|80||catalog.istioinaction.svc.cluster.local 172.16.0.12:51912 10.10.200.37:80 182.230.60.93:0 - default
[2025-05-31T14:41:31.894Z] "GET /api/catalog/ HTTP/1.1" 200 - via_upstream - "-" 0 357 8 8 "182.230.60.93" "curl/8.14.0" "9d448c6e-5cb3-4ce7-81ca-88a0255ffc5c" "webapp.istioinaction.io" "172.16.0.12:8080" inbound|8080|| 127.0.0.6:47421 172.16.0.12:8080 182.230.60.93:0 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
2. 자신의 PC에서 forum 요청 테스트 (에러 발생)
1
curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/users
✅ 출력
1
error calling Forum service
1
2
[2025-05-31T14:43:18.580Z] "GET /api/users HTTP/1.1" 503 UH no_healthy_upstream - "-" 0 19 0 - "182.230.60.93" "beegoServer" "559a56bf-3d1c-4710-a1d2-333885b52424" "forum.forum-services:80" "-" outbound|80||forum.forum-services.svc.cluster.local - 10.10.200.76:80 182.230.60.93:0 - default
[2025-05-31T14:43:18.578Z] "GET /api/users HTTP/1.1" 500 - via_upstream - "-" 0 27 11 10 "182.230.60.93" "curl/8.14.0" "559a56bf-3d1c-4710-a1d2-333885b52424" "webapp.istioinaction.io" "172.16.0.12:8080" inbound|8080|| 127.0.0.6:46585 172.16.0.12:8080 182.230.60.93:0 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
3. forum 요청에 대한 HTTP 상태코드 확인
1
curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/users -I
✅ 출력
1
2
3
4
5
6
HTTP/1.1 500 Internal Server Error
date: Sat, 31 May 2025 14:44:33 GMT
content-length: 27
content-type: text/plain; charset=utf-8
x-envoy-upstream-service-time: 14
server: istio-envoy
💬 forum 워크로드 상태 확인하기
1. WorkloadEntry 상태 조회
1
(⎈|default:N/A) root@k3s-s:~# kc get workloadentries -n forum-services -o yaml
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
apiVersion: v1
items:
- apiVersion: networking.istio.io/v1beta1
kind: WorkloadEntry
metadata:
annotations:
istio.io/autoRegistrationGroup: forum
istio.io/connectedAt: "2025-05-31T14:27:29.019644465Z"
istio.io/workloadController: istiod-d6549b9fc-gxjc5
proxy.istio.io/health-checks-enabled: "true"
creationTimestamp: "2025-05-31T13:28:46Z"
generation: 1
labels:
app: forum
service.istio.io/canonical-name: forum
service.istio.io/canonical-revision: latest
name: forum-192.168.10.200-vm-network
namespace: forum-services
ownerReferences:
- apiVersion: networking.istio.io/v1alpha3
controller: true
kind: WorkloadGroup
name: forum
uid: 110b29ea-752c-4c25-940c-64e0a0aae5f1
resourceVersion: "17397"
uid: a52b0887-d4ea-4105-bb9f-1f8889b6c702
spec:
address: 192.168.10.200
labels:
app: forum
service.istio.io/canonical-name: forum
service.istio.io/canonical-revision: latest
network: vm-network
serviceAccount: forum-sa
status:
conditions:
- lastProbeTime: "2025-05-31T14:27:29.033547823Z"
lastTransitionTime: "2025-05-31T14:27:29.033548436Z"
message: 'config not received from XDS server (is Istiod running?): cds updates:
0 successful, 0 rejected; lds updates: 0 successful, 0 rejected'
status: "False" # 헬스체크가 실패하여, 워크로드가 비정상 상태임
type: Healthy
kind: List
metadata:
resourceVersion: ""
2. VM에서 forum 애플리케이션 포트 열림 여부 확인
1
2
# 아직 8080 서비스가 실행되지 않았다!
root@forum-vm:~# ss -tnlp | grep 8080
🚀 가상머신에서 forum 애플리케이션 시작하기
1. forum 바이너리 다운로드
1
root@forum-vm:~# wget -O forum https://git.io/J3QrT
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
--2025-05-31 23:48:04-- https://git.io/J3QrT
Resolving git.io (git.io)... 140.82.114.21
Connecting to git.io (git.io)|140.82.114.21|:443... connected.
HTTP request sent, awaiting response... 301 Moved Permanently
Location: https://github.com/istioinaction/book-source-code/raw/master/services/forum/forum-linux-amd64 [following]
--2025-05-31 23:48:05-- https://github.com/istioinaction/book-source-code/raw/master/services/forum/forum-linux-amd64
Resolving github.com (github.com)... 20.200.245.247
Connecting to github.com (github.com)|20.200.245.247|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://raw.githubusercontent.com/istioinaction/book-source-code/master/services/forum/forum-linux-amd64 [following]
--2025-05-31 23:48:05-- https://raw.githubusercontent.com/istioinaction/book-source-code/master/services/forum/forum-linux-amd64
Resolving raw.githubusercontent.com (raw.githubusercontent.com)... 185.199.109.133, 185.199.110.133, 185.199.111.133, ...
Connecting to raw.githubusercontent.com (raw.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7555365 (7.2M) [application/octet-stream]
Saving to: ‘forum’
forum 100%[=============>] 7.21M --.-KB/s in 0.03s
2025-05-31 23:48:06 (246 MB/s) - ‘forum’ saved [7555365/7555365]
2. forum 바이너리 실행 권한 부여 및 실행
1
2
root@forum-vm:~# chmod +x forum
./forum
✅ 출력
1
Server is listening in port:8080
3. forum 애플리케이션 헬스체크 호출
1
root@forum-vm:~# curl http://localhost:8080/api/healthz -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
* Trying 127.0.0.1:8080...
* Connected to localhost (127.0.0.1) port 8080 (#0)
> GET /api/healthz HTTP/1.1
> Host: localhost:8080
> User-Agent: curl/7.81.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Sat, 31 May 2025 14:49:59 GMT
< Content-Length: 0
<
* Connection #0 to host localhost left intact
4. forum 서비스가 포트 8080에서 수신 대기 중인지 확인
1
root@forum-vm:~# ss -tnlp | grep 8080
✅ 출력
1
LISTEN 0 4096 *:8080 *:* users:(("forum",pid=24755,fd=3))
5. forum 서비스 엔드포인트 생성 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config endpoint deploy/webapp.istioinaction --cluster 'outbound|80||forum.forum-services.svc.cluster.local'
✅ 출력
1
2
ENDPOINT STATUS OUTLIER CHECK CLUSTER
192.168.10.200:8080 HEALTHY OK outbound|80||forum.forum-services.svc.cluster.local
6. WorkloadEntry 상태가 Healthy로 바뀌었는지 재확인
1
(⎈|default:N/A) root@k3s-s:~# kc get workloadentries -n forum-services -o yaml
✅ 출력
1
2
3
4
5
6
7
8
...
status:
conditions:
- lastProbeTime: "2025-05-31T14:48:49.681493895Z"
lastTransitionTime: "2025-05-31T14:48:49.681495038Z"
status: "True"
type: Healthy
...
7. 자신의 PC에서 forum API 호출
1
curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/users
✅ 출력
1
[{"id":1,"name":"Leanne Graham","username":"Bret","email":"Sincere@april.biz","address":{"street":"Kulas Light","suite":"Apt. 556","city":"Gwenborough","zipcode":"92998-3874"},"phone":"1-770-736-8031 x56442","website":"hildegard.org","company":{"name":"Romaguera-Crona","catchPhrase":"Multi-layered client-server neural-net","bs":"harness real-time e-markets"}},{"id":2,"name":"Ervin Howell","username":"Antonette","email":"Shanna@melissa.tv","address":{"street":"Victor Plains","suite":"Suite 879","city":"Wisokyburgh","zipcode":"90566-7771"},"phone":"010-692-6593 x09125","website":"anastasia.net","company":{"name":"Deckow-Crist","catchPhrase":"Proactive didactic contingency","bs":"synergize scalable supply-chains"}},{"id":3,"name":"Clementine Bauch","username":"Samantha","email":"Nathan@yesenia.net","address":{"street":"Douglas Extension","suite":"Suite 847","city":"McKenziehaven","zipcode":"59590-4157"},"phone":"1-463-123-4447","website":"ramiro.info","company":{"name":"Romaguera-Jacobson","catchPhrase":"Face to face bifurcated interface","bs":"e-enable strategic applications"}},{"id":4,"name":"Patricia Lebsack","username":"Karianne","email":"Julianne.OConner@kory.org","address":{"street":"Hoeger Mall","suite":"Apt. 692","city":"South Elvis","zipcode":"53919-4257"},"phone":"493-170-9623 x156","website":"kale.biz","company":{"name":"Robel-Corkery","catchPhrase":"Multi-tiered zero tolerance productivity","bs":"transition cutting-edge web services"}},{"id":5,"name":"Chelsey Dietrich","username":"Kamren","email":"Lucio_Hettinger@annie.ca","address":{"street":"Skiles Walks","suite":"Suite 351","city":"Roscoeview","zipcode":"33263"},"phone":"(254)954-1289","website":"demarco.info","company":{"name":"Keebler LLC","catchPhrase":"User-centric fault-tolerant solution","bs":"revolutionize end-to-end systems"}},{"id":6,"name":"Mrs. Dennis Schulist","username":"Leopoldo_Corkery","email":"Karley_Dach@jasper.info","address":{"street":"Norberto Crossing","suite":"Apt. 950","city":"South Christy","zipcode":"23505-1337"},"phone":"1-477-935-8478 x6430","website":"ola.org","company":{"name":"Considine-Lockman","catchPhrase":"Synchronised bottom-line interface","bs":"e-enable innovative applications"}},{"id":7,"name":"Kurtis Weissnat","username":"Elwyn.Skiles","email":"Telly.Hoeger@billy.biz","address":{"street":"Rex Trail","suite":"Suite 280","city":"Howemouth","zipcode":"58804-1099"},"phone":"210.067.6132","website":"elvis.io","company":{"name":"Johns Group","catchPhrase":"Configurable multimedia task-force","bs":"generate enterprise e-tailers"}},{"id":8,"name":"Nicholas Runolfsdottir V","username":"Maxime_Nienow","email":"Sherwood@rosamond.me","address":{"street":"Ellsworth Summit","suite":"Suite 729","city":"Aliyaview","zipcode":"45169"},"phone":"586.493.6943 x140","website":"jacynthe.com","company":{"name":"Abernathy Group","catchPhrase":"Implemented secondary concept","bs":"e-enable extensible e-tailers"}},{"id":9,"name":"Glenna Reichert","username":"Delphine","email":"Chaim_McDermott@dana.io","address":{"street":"Dayna Park","suite":"Suite 449","city":"Bartholomebury","zipcode":"76495-3109"},"phone":"(775)976-6794 x41206","website":"conrad.com","company":{"name":"Yost and Sons","catchPhrase":"Switchable contextually-based project","bs":"aggregate real-time technologies"}},{"id":10,"name":"Clementina DuBuque","username":"Moriah.Stanton","email":"Rey.Padberg@karina.biz","address":{"street":"Kattie Turnpike","suite":"Suite 198","city":"Lebsackbury","zipcode":"31428-2261"},"phone":"024-648-3804","website":"ambrose.net","company":{"name":"Hoeger LLC","catchPhrase":"Centralized empowering task-force","bs":"target end-to-end models"}}]
8. forum 서비스에 반복 요청 시도
1
while true; do curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/users ; echo; date; sleep 1; done
✅ 출력
1
2
3
4
5
6
7
8
while true; do curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/users ; echo; date; sleep 1; done
[{"id":1,"name":"Leanne Graham","username":"Bret","email":"Sincere@april.biz","address":{"street":"Kulas Light","suite":"Apt. 556","city":"Gwenborough","zipcode":"92998-3874"},"phone":"1-770-736-8031 x56442","website":"hildegard.org","company":{"name":"Romaguera-Crona","catchPhrase":"Multi-layered client-server neural-net","bs":"harness real-time e-markets"}},{"id":2,"name":"Ervin Howell","username":"Antonette","email":"Shanna@melissa.tv","address":{"street":"Victor Plains","suite":"Suite 879","city":"Wisokyburgh","zipcode":"90566-7771"},"phone":"010-692-6593 x09125","website":"anastasia.net","company":{"name":"Deckow-Crist","catchPhrase":"Proactive didactic contingency","bs":"synergize scalable supply-chains"}},{"id":3,"name":"Clementine Bauch","username":"Samantha","email":"Nathan@yesenia.net","address":{"street":"Douglas Extension","suite":"Suite 847","city":"McKenziehaven","zipcode":"59590-4157"},"phone":"1-463-123-4447","website":"ramiro.info","company":{"name":"Romaguera-Jacobson","catchPhrase":"Face to face bifurcated interface","bs":"e-enable strategic applications"}},{"id":4,"name":"Patricia Lebsack","username":"Karianne","email":"Julianne.OConner@kory.org","address":{"street":"Hoeger Mall","suite":"Apt. 692","city":"South Elvis","zipcode":"53919-4257"},"phone":"493-170-9623 x156","website":"kale.biz","company":{"name":"Robel-Corkery","catchPhrase":"Multi-tiered zero tolerance productivity","bs":"transition cutting-edge web services"}},{"id":5,"name":"Chelsey Dietrich","username":"Kamren","email":"Lucio_Hettinger@annie.ca","address":{"street":"Skiles Walks","suite":"Suite 351","city":"Roscoeview","zipcode":"33263"},"phone":"(254)954-1289","website":"demarco.info","company":{"name":"Keebler LLC","catchPhrase":"User-centric fault-tolerant solution","bs":"revolutionize end-to-end systems"}},{"id":6,"name":"Mrs. Dennis Schulist","username":"Leopoldo_Corkery","email":"Karley_Dach@jasper.info","address":{"street":"Norberto Crossing","suite":"Apt. 950","city":"South Christy","zipcode":"23505-1337"},"phone":"1-477-935-8478 x6430","website":"ola.org","company":{"name":"Considine-Lockman","catchPhrase":"Synchronised bottom-line interface","bs":"e-enable innovative applications"}},{"id":7,"name":"Kurtis Weissnat","username":"Elwyn.Skiles","email":"Telly.Hoeger@billy.biz","address":{"street":"Rex Trail","suite":"Suite 280","city":"Howemouth","zipcode":"58804-1099"},"phone":"210.067.6132","website":"elvis.io","company":{"name":"Johns Group","catchPhrase":"Configurable multimedia task-force","bs":"generate enterprise e-tailers"}},{"id":8,"name":"Nicholas Runolfsdottir V","username":"Maxime_Nienow","email":"Sherwood@rosamond.me","address":{"street":"Ellsworth Summit","suite":"Suite 729","city":"Aliyaview","zipcode":"45169"},"phone":"586.493.6943 x140","website":"jacynthe.com","company":{"name":"Abernathy Group","catchPhrase":"Implemented secondary concept","bs":"e-enable extensible e-tailers"}},{"id":9,"name":"Glenna Reichert","username":"Delphine","email":"Chaim_McDermott@dana.io","address":{"street":"Dayna Park","suite":"Suite 449","city":"Bartholomebury","zipcode":"76495-3109"},"phone":"(775)976-6794 x41206","website":"conrad.com","company":{"name":"Yost and Sons","catchPhrase":"Switchable contextually-based project","bs":"aggregate real-time technologies"}},{"id":10,"name":"Clementina DuBuque","username":"Moriah.Stanton","email":"Rey.Padberg@karina.biz","address":{"street":"Kattie Turnpike","suite":"Suite 198","city":"Lebsackbury","zipcode":"31428-2261"},"phone":"024-648-3804","website":"ambrose.net","company":{"name":"Hoeger LLC","catchPhrase":"Centralized empowering task-force","bs":"target end-to-end models"}}]
Sat May 31 11:55:20 PM KST 2025
[{"id":1,"name":"Leanne Graham","username":"Bret","email":"Sincere@april.biz","address":{"street":"Kulas Light","suite":"Apt. 556","city":"Gwenborough","zipcode":"92998-3874"},"phone":"1-770-736-8031 x56442","website":"hildegard.org","company":{"name":"Romaguera-Crona","catchPhrase":"Multi-layered client-server neural-net","bs":"harness real-time e-markets"}},{"id":2,"name":"Ervin Howell","username":"Antonette","email":"Shanna@melissa.tv","address":{"street":"Victor Plains","suite":"Suite 879","city":"Wisokyburgh","zipcode":"90566-7771"},"phone":"010-692-6593 x09125","website":"anastasia.net","company":{"name":"Deckow-Crist","catchPhrase":"Proactive didactic contingency","bs":"synergize scalable supply-chains"}},{"id":3,"name":"Clementine Bauch","username":"Samantha","email":"Nathan@yesenia.net","address":{"street":"Douglas Extension","suite":"Suite 847","city":"McKenziehaven","zipcode":"59590-4157"},"phone":"1-463-123-4447","website":"ramiro.info","company":{"name":"Romaguera-Jacobson","catchPhrase":"Face to face bifurcated interface","bs":"e-enable strategic applications"}},{"id":4,"name":"Patricia Lebsack","username":"Karianne","email":"Julianne.OConner@kory.org","address":{"street":"Hoeger Mall","suite":"Apt. 692","city":"South Elvis","zipcode":"53919-4257"},"phone":"493-170-9623 x156","website":"kale.biz","company":{"name":"Robel-Corkery","catchPhrase":"Multi-tiered zero tolerance productivity","bs":"transition cutting-edge web services"}},{"id":5,"name":"Chelsey Dietrich","username":"Kamren","email":"Lucio_Hettinger@annie.ca","address":{"street":"Skiles Walks","suite":"Suite 351","city":"Roscoeview","zipcode":"33263"},"phone":"(254)954-1289","website":"demarco.info","company":{"name":"Keebler LLC","catchPhrase":"User-centric fault-tolerant solution","bs":"revolutionize end-to-end systems"}},{"id":6,"name":"Mrs. Dennis Schulist","username":"Leopoldo_Corkery","email":"Karley_Dach@jasper.info","address":{"street":"Norberto Crossing","suite":"Apt. 950","city":"South Christy","zipcode":"23505-1337"},"phone":"1-477-935-8478 x6430","website":"ola.org","company":{"name":"Considine-Lockman","catchPhrase":"Synchronised bottom-line interface","bs":"e-enable innovative applications"}},{"id":7,"name":"Kurtis Weissnat","username":"Elwyn.Skiles","email":"Telly.Hoeger@billy.biz","address":{"street":"Rex Trail","suite":"Suite 280","city":"Howemouth","zipcode":"58804-1099"},"phone":"210.067.6132","website":"elvis.io","company":{"name":"Johns Group","catchPhrase":"Configurable multimedia task-force","bs":"generate enterprise e-tailers"}},{"id":8,"name":"Nicholas Runolfsdottir V","username":"Maxime_Nienow","email":"Sherwood@rosamond.me","address":{"street":"Ellsworth Summit","suite":"Suite 729","city":"Aliyaview","zipcode":"45169"},"phone":"586.493.6943 x140","website":"jacynthe.com","company":{"name":"Abernathy Group","catchPhrase":"Implemented secondary concept","bs":"e-enable extensible e-tailers"}},{"id":9,"name":"Glenna Reichert","username":"Delphine","email":"Chaim_McDermott@dana.io","address":{"street":"Dayna Park","suite":"Suite 449","city":"Bartholomebury","zipcode":"76495-3109"},"phone":"(775)976-6794 x41206","website":"conrad.com","company":{"name":"Yost and Sons","catchPhrase":"Switchable contextually-based project","bs":"aggregate real-time technologies"}},{"id":10,"name":"Clementina DuBuque","username":"Moriah.Stanton","email":"Rey.Padberg@karina.biz","address":{"street":"Kattie Turnpike","suite":"Suite 198","city":"Lebsackbury","zipcode":"31428-2261"},"phone":"024-648-3804","website":"ambrose.net","company":{"name":"Hoeger LLC","catchPhrase":"Centralized empowering task-force","bs":"target end-to-end models"}}]
Sat May 31 11:55:21 PM KST 2025
[{"id":1,"name":"Leanne Graham","username":"Bret","email":"Sincere@april.biz","address":{"street":"Kulas Light","suite":"Apt. 556","city":"Gwenborough","zipcode":"92998-3874"},"phone":"1-770-736-8031 x56442","website":"hildegard.org","company":{"name":"Romaguera-Crona","catchPhrase":"Multi-layered client-server neural-net","bs":"harness real-time e-markets"}},{"id":2,"name":"Ervin Howell","username":"Antonette","email":"Shanna@melissa.tv","address":{"street":"Victor Plains","suite":"Suite 879","city":"Wisokyburgh","zipcode":"90566-7771"},"phone":"010-692-6593 x09125","website":"anastasia.net","company":{"name":"Deckow-Crist","catchPhrase":"Proactive didactic contingency","bs":"synergize scalable supply-chains"}},{"id":3,"name":"Clementine Bauch","username":"Samantha","email":"Nathan@yesenia.net","address":{"street":"Douglas Extension","suite":"Suite 847","city":"McKenziehaven","zipcode":"59590-4157"},"phone":"1-463-123-4447","website":"ramiro.info","company":{"name":"Romaguera-Jacobson","catchPhrase":"Face to face bifurcated interface","bs":"e-enable strategic applications"}},{"id":4,"name":"Patricia Lebsack","username":"Karianne","email":"Julianne.OConner@kory.org","address":{"street":"Hoeger Mall","suite":"Apt. 692","city":"South Elvis","zipcode":"53919-4257"},"phone":"493-170-9623 x156","website":"kale.biz","company":{"name":"Robel-Corkery","catchPhrase":"Multi-tiered zero tolerance productivity","bs":"transition cutting-edge web services"}},{"id":5,"name":"Chelsey Dietrich","username":"Kamren","email":"Lucio_Hettinger@annie.ca","address":{"street":"Skiles Walks","suite":"Suite 351","city":"Roscoeview","zipcode":"33263"},"phone":"(254)954-1289","website":"demarco.info","company":{"name":"Keebler LLC","catchPhrase":"User-centric fault-tolerant solution","bs":"revolutionize end-to-end systems"}},{"id":6,"name":"Mrs. Dennis Schulist","username":"Leopoldo_Corkery","email":"Karley_Dach@jasper.info","address":{"street":"Norberto Crossing","suite":"Apt. 950","city":"South Christy","zipcode":"23505-1337"},"phone":"1-477-935-8478 x6430","website":"ola.org","company":{"name":"Considine-Lockman","catchPhrase":"Synchronised bottom-line interface","bs":"e-enable innovative applications"}},{"id":7,"name":"Kurtis Weissnat","username":"Elwyn.Skiles","email":"Telly.Hoeger@billy.biz","address":{"street":"Rex Trail","suite":"Suite 280","city":"Howemouth","zipcode":"58804-1099"},"phone":"210.067.6132","website":"elvis.io","company":{"name":"Johns Group","catchPhrase":"Configurable multimedia task-force","bs":"generate enterprise e-tailers"}},{"id":8,"name":"Nicholas Runolfsdottir V","username":"Maxime_Nienow","email":"Sherwood@rosamond.me","address":{"street":"Ellsworth Summit","suite":"Suite 729","city":"Aliyaview","zipcode":"45169"},"phone":"586.493.6943 x140","website":"jacynthe.com","company":{"name":"Abernathy Group","catchPhrase":"Implemented secondary concept","bs":"e-enable extensible e-tailers"}},{"id":9,"name":"Glenna Reichert","username":"Delphine","email":"Chaim_McDermott@dana.io","address":{"street":"Dayna Park","suite":"Suite 449","city":"Bartholomebury","zipcode":"76495-3109"},"phone":"(775)976-6794 x41206","website":"conrad.com","company":{"name":"Yost and Sons","catchPhrase":"Switchable contextually-based project","bs":"aggregate real-time technologies"}},{"id":10,"name":"Clementina DuBuque","username":"Moriah.Stanton","email":"Rey.Padberg@karina.biz","address":{"street":"Kattie Turnpike","suite":"Suite 198","city":"Lebsackbury","zipcode":"31428-2261"},"phone":"024-648-3804","website":"ambrose.net","company":{"name":"Hoeger LLC","catchPhrase":"Centralized empowering task-force","bs":"target end-to-end models"}}]
Sat May 31 11:55:22 PM KST 2025
...
9. webapp의 envoy 사이드카 로그 실시간 확인
1
kubectl logs -n istioinaction deploy/webapp -c istio-proxy -f
✅ 출력
1
2
3
4
5
6
[2025-05-31T14:56:29.037Z] "GET /api/users HTTP/1.1" 200 - via_upstream - "-" 0 3679 14 14 "182.230.60.93" "curl/8.14.0" "6e9d8d48-588e-4d73-9173-a1d7ee4b008b" "webapp.istioinaction.io" "172.16.0.12:8080" inbound|8080|| 127.0.0.6:47421 172.16.0.12:8080 182.230.60.93:0 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
[2025-05-31T14:56:30.079Z] "GET /api/users HTTP/1.1" 200 - via_upstream - "-" 0 5645 19 19 "182.230.60.93" "beegoServer" "ab66342d-5c6c-4a75-b57b-48ba1edc1b61" "forum.forum-services:80" "192.168.10.200:8080" outbound|80||forum.forum-services.svc.cluster.local 172.16.0.12:41064 10.10.200.76:80 182.230.60.93:0 - default
[2025-05-31T14:56:30.077Z] "GET /api/users HTTP/1.1" 200 - via_upstream - "-" 0 3679 22 21 "182.230.60.93" "curl/8.14.0" "ab66342d-5c6c-4a75-b57b-48ba1edc1b61" "webapp.istioinaction.io" "172.16.0.12:8080" inbound|8080|| 127.0.0.6:47421 172.16.0.12:8080 182.230.60.93:0 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
[2025-05-31T14:56:31.127Z] "GET /api/users HTTP/1.1" 200 - via_upstream - "-" 0 5645 23 23 "182.230.60.93" "beegoServer" "6527fe2e-657e-4f0a-b9c2-ff6269b1b7aa" "forum.forum-services:80" "192.168.10.200:8080" outbound|80||forum.forum-services.svc.cluster.local 172.16.0.12:58686 10.10.200.76:80 182.230.60.93:0 - default
[2025-05-31T14:56:31.125Z] "GET /api/users HTTP/1.1" 200 - via_upstream - "-" 0 3679 27 26 "182.230.60.93" "curl/8.14.0" "6527fe2e-657e-4f0a-b9c2-ff6269b1b7aa" "webapp.istioinaction.io" "172.16.0.12:8080" inbound|8080|| 127.0.0.6:46585 172.16.0.12:8080 182.230.60.93:0 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
...
💠 컨트롤 플레인에 메시 범위의 상호 인증 정책 설정하기
1. forum 서비스 직접 접근 정상 동작 확인
1
curl -is $FORUM:8080/api/users | grep HTTP
✅ 출력
1
HTTP/1.1 200 OK
2. PeerAuthentication 리소스 YAML 내용 확인
1
(⎈|default:N/A) root@k3s-s:~# cat istio-in-action/book-source-code-master/ch13/strict-peer-auth.yaml
✅ 출력
1
2
3
4
5
6
7
8
apiVersion: security.istio.io/v1beta1
kind: PeerAuthentication
metadata:
name: default
namespace: istio-system
spec:
mtls:
mode: STRICT
3. STRICT 모드 PeerAuthentication 리소스 생성
1
2
3
4
(⎈|default:N/A) root@k3s-s:~# kubectl apply -f istio-in-action/book-source-code-master/ch13/strict-peer-auth.yaml
# 결과
peerauthentication.security.istio.io/default created
4. 현재 적용된 PeerAuthentication 정책 조회
1
(⎈|default:N/A) root@k3s-s:~# kubectl get peerauthentication -A
✅ 출력
1
2
NAMESPACE NAME MODE AGE
istio-system default STRICT 19s
5. forum 서비스에 직접 요청 차단 여부 확인
1
curl -is $FORUM:8080/api/users -v
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
* Trying 3.36.50.171:8080...
* Connected to 3.36.50.171 (3.36.50.171) port 8080
* using HTTP/1.x
> GET /api/users HTTP/1.1
> Host: 3.36.50.171:8080
> User-Agent: curl/8.14.0
> Accept: */*
>
* Request completely sent off
* Recv failure: Connection reset by peer
* closing connection #0
6. ingressgateway 경유 forum 요청 반복 수행
1
while true; do curl -s -H "Host: webapp.istioinaction.io" http://$APP_IP:30000/api/users ; echo; date; sleep 1; done
✅ 출력
1
2
3
4
5
[{"id":1,"name":"Leanne Graham","username":"Bret","email":"Sincere@april.biz","address":{"street":"Kulas Light","suite":"Apt. 556","city":"Gwenborough","zipcode":"92998-3874"},"phone":"1-770-736-8031 x56442","website":"hildegard.org","company":{"name":"Romaguera-Crona","catchPhrase":"Multi-layered client-server neural-net","bs":"harness real-time e-markets"}},{"id":2,"name":"Ervin Howell","username":"Antonette","email":"Shanna@melissa.tv","address":{"street":"Victor Plains","suite":"Suite 879","city":"Wisokyburgh","zipcode":"90566-7771"},"phone":"010-692-6593 x09125","website":"anastasia.net","company":{"name":"Deckow-Crist","catchPhrase":"Proactive didactic contingency","bs":"synergize scalable supply-chains"}},{"id":3,"name":"Clementine Bauch","username":"Samantha","email":"Nathan@yesenia.net","address":{"street":"Douglas Extension","suite":"Suite 847","city":"McKenziehaven","zipcode":"59590-4157"},"phone":"1-463-123-4447","website":"ramiro.info","company":{"name":"Romaguera-Jacobson","catchPhrase":"Face to face bifurcated interface","bs":"e-enable strategic applications"}},{"id":4,"name":"Patricia Lebsack","username":"Karianne","email":"Julianne.OConner@kory.org","address":{"street":"Hoeger Mall","suite":"Apt. 692","city":"South Elvis","zipcode":"53919-4257"},"phone":"493-170-9623 x156","website":"kale.biz","company":{"name":"Robel-Corkery","catchPhrase":"Multi-tiered zero tolerance productivity","bs":"transition cutting-edge web services"}},{"id":5,"name":"Chelsey Dietrich","username":"Kamren","email":"Lucio_Hettinger@annie.ca","address":{"street":"Skiles Walks","suite":"Suite 351","city":"Roscoeview","zipcode":"33263"},"phone":"(254)954-1289","website":"demarco.info","company":{"name":"Keebler LLC","catchPhrase":"User-centric fault-tolerant solution","bs":"revolutionize end-to-end systems"}},{"id":6,"name":"Mrs. Dennis Schulist","username":"Leopoldo_Corkery","email":"Karley_Dach@jasper.info","address":{"street":"Norberto Crossing","suite":"Apt. 950","city":"South Christy","zipcode":"23505-1337"},"phone":"1-477-935-8478 x6430","website":"ola.org","company":{"name":"Considine-Lockman","catchPhrase":"Synchronised bottom-line interface","bs":"e-enable innovative applications"}},{"id":7,"name":"Kurtis Weissnat","username":"Elwyn.Skiles","email":"Telly.Hoeger@billy.biz","address":{"street":"Rex Trail","suite":"Suite 280","city":"Howemouth","zipcode":"58804-1099"},"phone":"210.067.6132","website":"elvis.io","company":{"name":"Johns Group","catchPhrase":"Configurable multimedia task-force","bs":"generate enterprise e-tailers"}},{"id":8,"name":"Nicholas Runolfsdottir V","username":"Maxime_Nienow","email":"Sherwood@rosamond.me","address":{"street":"Ellsworth Summit","suite":"Suite 729","city":"Aliyaview","zipcode":"45169"},"phone":"586.493.6943 x140","website":"jacynthe.com","company":{"name":"Abernathy Group","catchPhrase":"Implemented secondary concept","bs":"e-enable extensible e-tailers"}},{"id":9,"name":"Glenna Reichert","username":"Delphine","email":"Chaim_McDermott@dana.io","address":{"street":"Dayna Park","suite":"Suite 449","city":"Bartholomebury","zipcode":"76495-3109"},"phone":"(775)976-6794 x41206","website":"conrad.com","company":{"name":"Yost and Sons","catchPhrase":"Switchable contextually-based project","bs":"aggregate real-time technologies"}},{"id":10,"name":"Clementina DuBuque","username":"Moriah.Stanton","email":"Rey.Padberg@karina.biz","address":{"street":"Kattie Turnpike","suite":"Suite 198","city":"Lebsackbury","zipcode":"31428-2261"},"phone":"024-648-3804","website":"ambrose.net","company":{"name":"Hoeger LLC","catchPhrase":"Centralized empowering task-force","bs":"target end-to-end models"}}]
Sun Jun 1 12:07:09 AM KST 2025
[{"id":1,"name":"Leanne Graham","username":"Bret","email":"Sincere@april.biz","address":{"street":"Kulas Light","suite":"Apt. 556","city":"Gwenborough","zipcode":"92998-3874"},"phone":"1-770-736-8031 x56442","website":"hildegard.org","company":{"name":"Romaguera-Crona","catchPhrase":"Multi-layered client-server neural-net","bs":"harness real-time e-markets"}},{"id":2,"name":"Ervin Howell","username":"Antonette","email":"Shanna@melissa.tv","address":{"street":"Victor Plains","suite":"Suite 879","city":"Wisokyburgh","zipcode":"90566-7771"},"phone":"010-692-6593 x09125","website":"anastasia.net","company":{"name":"Deckow-Crist","catchPhrase":"Proactive didactic contingency","bs":"synergize scalable supply-chains"}},{"id":3,"name":"Clementine Bauch","username":"Samantha","email":"Nathan@yesenia.net","address":{"street":"Douglas Extension","suite":"Suite 847","city":"McKenziehaven","zipcode":"59590-4157"},"phone":"1-463-123-4447","website":"ramiro.info","company":{"name":"Romaguera-Jacobson","catchPhrase":"Face to face bifurcated interface","bs":"e-enable strategic applications"}},{"id":4,"name":"Patricia Lebsack","username":"Karianne","email":"Julianne.OConner@kory.org","address":{"street":"Hoeger Mall","suite":"Apt. 692","city":"South Elvis","zipcode":"53919-4257"},"phone":"493-170-9623 x156","website":"kale.biz","company":{"name":"Robel-Corkery","catchPhrase":"Multi-tiered zero tolerance productivity","bs":"transition cutting-edge web services"}},{"id":5,"name":"Chelsey Dietrich","username":"Kamren","email":"Lucio_Hettinger@annie.ca","address":{"street":"Skiles Walks","suite":"Suite 351","city":"Roscoeview","zipcode":"33263"},"phone":"(254)954-1289","website":"demarco.info","company":{"name":"Keebler LLC","catchPhrase":"User-centric fault-tolerant solution","bs":"revolutionize end-to-end systems"}},{"id":6,"name":"Mrs. Dennis Schulist","username":"Leopoldo_Corkery","email":"Karley_Dach@jasper.info","address":{"street":"Norberto Crossing","suite":"Apt. 950","city":"South Christy","zipcode":"23505-1337"},"phone":"1-477-935-8478 x6430","website":"ola.org","company":{"name":"Considine-Lockman","catchPhrase":"Synchronised bottom-line interface","bs":"e-enable innovative applications"}},{"id":7,"name":"Kurtis Weissnat","username":"Elwyn.Skiles","email":"Telly.Hoeger@billy.biz","address":{"street":"Rex Trail","suite":"Suite 280","city":"Howemouth","zipcode":"58804-1099"},"phone":"210.067.6132","website":"elvis.io","company":{"name":"Johns Group","catchPhrase":"Configurable multimedia task-force","bs":"generate enterprise e-tailers"}},{"id":8,"name":"Nicholas Runolfsdottir V","username":"Maxime_Nienow","email":"Sherwood@rosamond.me","address":{"street":"Ellsworth Summit","suite":"Suite 729","city":"Aliyaview","zipcode":"45169"},"phone":"586.493.6943 x140","website":"jacynthe.com","company":{"name":"Abernathy Group","catchPhrase":"Implemented secondary concept","bs":"e-enable extensible e-tailers"}},{"id":9,"name":"Glenna Reichert","username":"Delphine","email":"Chaim_McDermott@dana.io","address":{"street":"Dayna Park","suite":"Suite 449","city":"Bartholomebury","zipcode":"76495-3109"},"phone":"(775)976-6794 x41206","website":"conrad.com","company":{"name":"Yost and Sons","catchPhrase":"Switchable contextually-based project","bs":"aggregate real-time technologies"}},{"id":10,"name":"Clementina DuBuque","username":"Moriah.Stanton","email":"Rey.Padberg@karina.biz","address":{"street":"Kattie Turnpike","suite":"Suite 198","city":"Lebsackbury","zipcode":"31428-2261"},"phone":"024-648-3804","website":"ambrose.net","company":{"name":"Hoeger LLC","catchPhrase":"Centralized empowering task-force","bs":"target end-to-end models"}}]
Sun Jun 1 12:07:10 AM KST 2025
...
🧱 DNS 프록시 이해하기
1. iptables 규칙에서 DNS 트래픽 리다이렉트 여부 확인
1
root@forum-vm:~# iptables-save | grep 'to-ports 15053'
✅ 출력
1
2
-A OUTPUT -d 127.0.0.53/32 -p udp -m udp --dport 53 -j REDIRECT --to-ports 15053
-A ISTIO_OUTPUT -d 127.0.0.53/32 -p tcp -m tcp --dport 53 -j REDIRECT --to-ports 15053
2. pilot-agent가 15053 포트에서 TCP/UDP 수신 중인지 확인
1
root@forum-vm:~# netstat -ltunp | egrep 'PID|15053'
✅ 출력
1
2
3
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:15053 0.0.0.0:* LISTEN 17166/pilot-agent
udp 0 0 127.0.0.1:15053 0.0.0.0:* 17166/pilot-agent
3. DNS 프록시를 통해 서비스 이름 확인
1
2
3
root@forum-vm:~# dig +short @localhost -p 15053 webapp.istioinaction
dig +short @localhost -p 15053 catalog.istioinaction
dig +short @localhost -p 15053 forum.forum-services
✅ 출력
1
2
3
10.10.200.134
10.10.200.37
10.10.200.76
💡 DNS 프록시가 인식하는 호스트네임은 무엇인가?
1. istioctl proxy-status로 프록시 ID 목록 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-status | awk '{print $1}'
✅ 출력
1
2
3
4
5
6
NAME
catalog-77fdb4997c-fhpf9.istioinaction
forum-vm.forum-services
istio-eastwestgateway-86f6cb4699-gwbwq.istio-system
istio-ingressgateway-7b7ccd6454-cdvc6.istio-system
webapp-684c568c59-6x29p.istioinaction
2. NDS(NameTable) 설정 확인 (proxyID로 forum-vm 지정)
1
(⎈|default:N/A) root@k3s-s:~# kubectl -n istio-system exec deploy/istiod -- curl -Ls "localhost:8080/debug/ndsz?proxyID=forum-vm.forum-services" | jq
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
{
"resource": {
"@type": "type.googleapis.com/istio.networking.nds.v1.NameTable",
"table": {
"catalog.istioinaction.svc.cluster.local": {
"ips": [
"10.10.200.37"
],
"registry": "Kubernetes",
"shortname": "catalog",
"namespace": "istioinaction"
},
"forum.forum-services.svc.cluster.local": {
"ips": [
"10.10.200.76"
],
"registry": "Kubernetes",
"shortname": "forum",
"namespace": "forum-services"
},
"grafana.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.65"
],
"registry": "Kubernetes",
"shortname": "grafana",
"namespace": "istio-system"
},
"istio-eastwestgateway.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.254"
],
"registry": "Kubernetes",
"shortname": "istio-eastwestgateway",
"namespace": "istio-system"
},
"istio-ingressgateway.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.56"
],
"registry": "Kubernetes",
"shortname": "istio-ingressgateway",
"namespace": "istio-system"
},
"istiod.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.61"
],
"registry": "Kubernetes",
"shortname": "istiod",
"namespace": "istio-system"
},
"jaeger-collector.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.104"
],
"registry": "Kubernetes",
"shortname": "jaeger-collector",
"namespace": "istio-system"
},
"kiali.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.187"
],
"registry": "Kubernetes",
"shortname": "kiali",
"namespace": "istio-system"
},
"kube-dns.kube-system.svc.cluster.local": {
"ips": [
"10.10.200.10"
],
"registry": "Kubernetes",
"shortname": "kube-dns",
"namespace": "kube-system"
},
"kubernetes.default.svc.cluster.local": {
"ips": [
"10.10.200.1"
],
"registry": "Kubernetes",
"shortname": "kubernetes",
"namespace": "default"
},
"metrics-server.kube-system.svc.cluster.local": {
"ips": [
"10.10.200.82"
],
"registry": "Kubernetes",
"shortname": "metrics-server",
"namespace": "kube-system"
},
"prometheus.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.128"
],
"registry": "Kubernetes",
"shortname": "prometheus",
"namespace": "istio-system"
},
"tracing.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.67"
],
"registry": "Kubernetes",
"shortname": "tracing",
"namespace": "istio-system"
},
"webapp.istioinaction.svc.cluster.local": {
"ips": [
"10.10.200.134"
],
"registry": "Kubernetes",
"shortname": "webapp",
"namespace": "istioinaction"
},
"zipkin.istio-system.svc.cluster.local": {
"ips": [
"10.10.200.41"
],
"registry": "Kubernetes",
"shortname": "zipkin",
"namespace": "istio-system"
}
}
}
}
3. webapp 서비스에 대한 route 설정 내 도메인 이름 확인
1
(⎈|default:N/A) root@k3s-s:~# istioctl proxy-config route deploy/webapp.istioinaction --name 80 -o json
✅ 출력
1
2
3
4
5
6
7
8
9
10
...
"name": "webapp.istioinaction.svc.cluster.local:80",
"domains": [
"webapp.istioinaction.svc.cluster.local",
"webapp",
"webapp.istioinaction.svc",
"webapp.istioinaction",
"10.10.200.134"
],
...
🗑️ 메시에서 WorkloadEntry 제거하기
1. WorkloadEntry 지속 모니터링
1
(⎈|default:N/A) root@k3s-s:~# watch kubectl get workloadentries -A
✅ 출력
1
2
3
4
Every 2.0s: kubectl get workloadentr... k3s-s: Sun Jun 1 00:25:13 2025
NAMESPACE NAME AGE ADDRESS
forum-services forum-192.168.10.200-vm-network 116m 192.168.10.200
2. 가상머신 종료 후 WorkloadEntry 자동 제거 확인
1
2
3
Every 2.0s: kubectl get workloadentr... k3s-s: Sun Jun 1 00:27:05 2025
No resources found