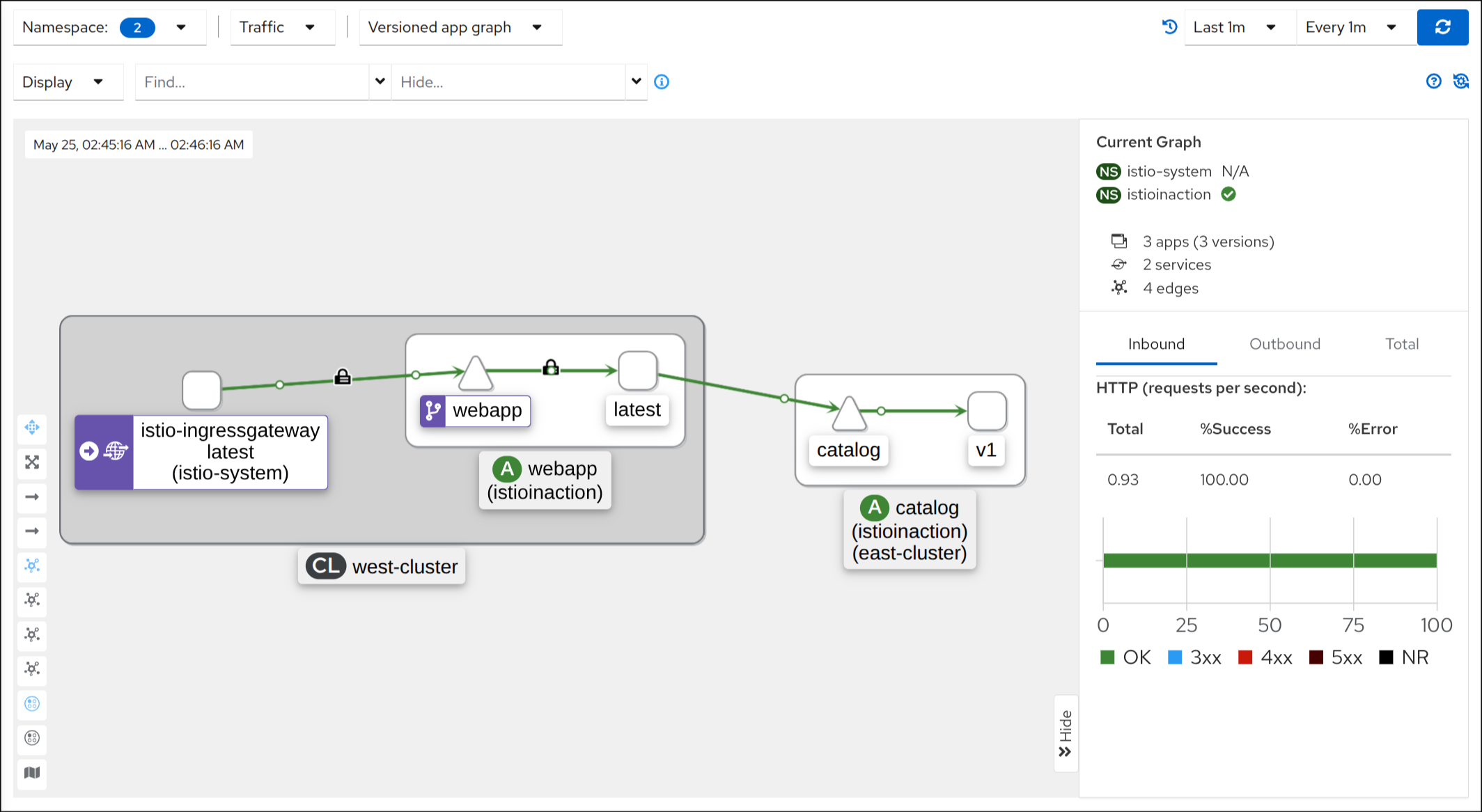
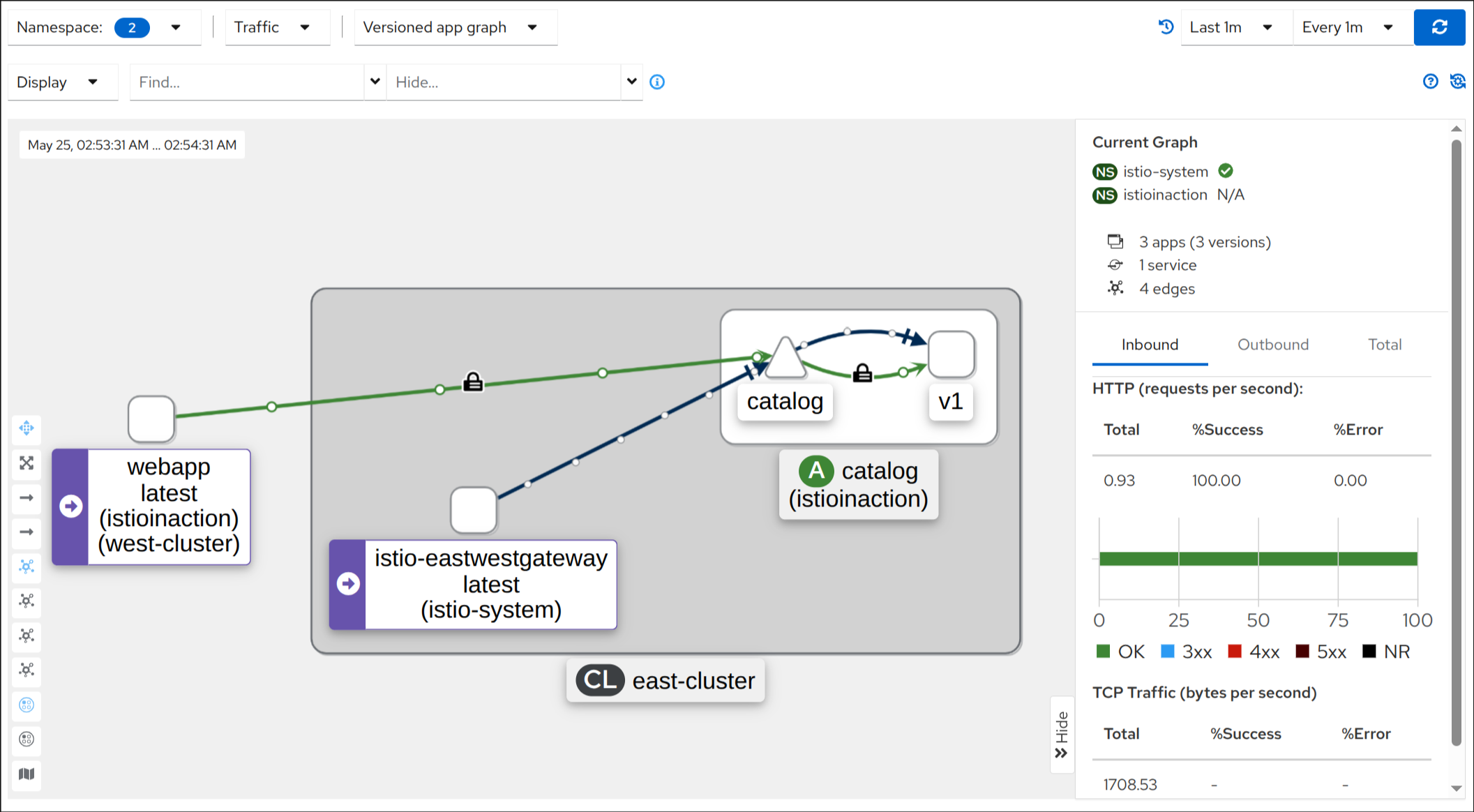
☁️ 클라우드 인프라 준비하기
1. west 클러스터 설정 및 확인
(1) west 클러스터 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| kind create cluster --name west --image kindest/node:v1.23.17 --kubeconfig ./west-kubeconfig --config - <<EOF
kind: Cluster
apiVersion: kind.x-k8s.io/v1alpha4
nodes:
- role: control-plane
extraPortMappings:
- containerPort: 30000 # istio-ingrssgateway HTTP
hostPort: 30000
- containerPort: 30001 # Prometheus
hostPort: 30001
- containerPort: 30002 # Grafana
hostPort: 30002
- containerPort: 30003 # Kiali
hostPort: 30003
- containerPort: 30004 # Tracing
hostPort: 30004
- containerPort: 30005 # kube-ops-view
hostPort: 30005
networking:
podSubnet: 10.10.0.0/16
serviceSubnet: 10.100.0.0/24
EOF
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
| Creating cluster "west" ...
✓ Ensuring node image (kindest/node:v1.23.17) 🖼
✓ Preparing nodes 📦
✓ Writing configuration 📜
✓ Starting control-plane 🕹️
✓ Installing CNI 🔌
✓ Installing StorageClass 💾
Set kubectl context to "kind-west"
You can now use your cluster with:
kubectl cluster-info --context kind-west --kubeconfig ./west-kubeconfig
Thanks for using kind! 😊
|
(2) west 클러스터 상태 확인
✅ 출력
1
2
3
|
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
5034b4c2be0c kindest/node:v1.23.17 "/usr/local/bin/entr…" 37 seconds ago Up 35 seconds 0.0.0.0:30000-30005->30000-30005/tcp, 127.0.0.1:36143->6443/tcp west-control-plane
|
(3) west 클러스터 kubeconfig 내용 확인
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1EVXlOREV4TURZeE9Gb1hEVE0xTURVeU1qRXhNRFl4T0Zvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTThSCi81WkdpQTJ4K2dSOHc0a1FLeFh3M0dEdWhBQXhnVG5rUThMLzBzS2FBM3N3c3VhZnN3RFAzR3Q0WkRVQlI1MDcKVUh4Sml0aUxhMVQ3bHFUYm45WnBiVEwyMmV2alAxVlZxOWNNRUlXbnJLaUVuVlJPR0VFUEFpTWYrbXB3OU15dQpVMXZzMm1UTklZWHcxNTg1K2pYeU01dUhhTFljVjZpSzJMWHFkNWdubVVRdHhGUE5yQTRQTUlVa1lrOUh0MVdPCktOOUxWdFR3aU5MRHd6bjBKenp2T3VGUTBKSjhqazBDbUY2MkJjdmw0STA1N3FSSklqRGZ0aEtEOEk4QjZKSDYKS21kOEU1OWNuME9lOGhEZ2h3Ly84dzhzRnVSZ3daNmpHbGtyRzF0NGlyZnJEanc0bE1YZnFNa2wzTm5BamZEMApnMzVyNUJIOEJseFZodGQ1VTZNQ0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZBT3A0UEkvQTQzQmRUMzR0b0dYaW1TM1doRWhNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBRmZWTVc4ZnE1MmdNMjQzMlhTUQpWRHc1UXlHVm9KdjIwbU5EN2o0VnpTMVZoWm5BYUs2NUNnQzYxVEhzOFZvRVBBZWFNQWlKZEo0WWZzQnQ0bzZ5CkFFQzVvOGFnWEU3SDFzR0lCUkNoZXQxQytxTHU4c3FtUDc4aXlHVS8zRmxRT0cwMTY5VWk5eVZMZHpqSjRBeWwKQjN2dnFYSUxsdXRISjU2TWFzWnFTcnlocnBxNzVRQ0d4VjJHQmN2NHArQ2tUL29VblNzamRiV1EzVFNzVkMxbwpYdGk4UFJLTkhINWhQSnNOL1ZvTUxud0lYdG4zQitlRlF2bVljVG1WT2JVYTJxMWJVU1RwKzk4QWIwNVZ2c0Y2CkpCTXh6ZDJiSkxHZm50TVl2YmZGRmcxNXpmQnhMdzZ4enRSMWtFbUwrclRhTFI0cFRVQmwzM0VLcDRvNXU1Qm0KeDFJPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://127.0.0.1:36143
name: kind-west
contexts:
- context:
cluster: kind-west
user: kind-west
name: kind-west
current-context: kind-west
kind: Config
preferences: {}
users:
- name: kind-west
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURJVENDQWdtZ0F3SUJBZ0lJR1NxWjUvZGFoU013RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TlRBMU1qUXhNVEEyTVRoYUZ3MHlOakExTWpReE1UQTJNakJhTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUcHRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQW9WVWoxOWM1Mlg2NmZCZWUKR2R1eDYweXdKa0loV3JvSGZQQ21mWDdIeVNhNGVndGkzRkNUWmN2cXJrRlJ0dnp4UU5jNnNIUHRFSmRrZENoOAp5azRWSjhkWVhEamNzVk44MWJTL2tneFBqcHMxL2lOd1NTTXhmV1ExR2RPeHE4cGlzVjE3Ujh3VE1DK2FFNTFICkxLSmtPemptQ3ptWFZVSS9MUyt5b0JHY3gxa2p3SVA1Z1lCaDlsaVJyZ0xyQUgreDVjZDRlcVArS1phZVh4b24KZUVsVS9xSVVNWWhKbkNySmtkbmVjcjZSQXM5Qko3UWV5eEhmZWNsU2Vib1gwc0JWN204QUx6N2Z0eEJNcDlORwprUERldWlXbk14T2daMmthclZMVmU5aU82TERCSzlEVHJqaEtjNFIxamFFS0NtOEtuQ1F1ZFkzRUlqdVNMemJ6Ci9FNkxtUUlEQVFBQm8xWXdWREFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RBWURWUjBUQVFIL0JBSXdBREFmQmdOVkhTTUVHREFXZ0JRRHFlRHlQd09Od1hVOStMYUJsNHBrdDFvUgpJVEFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBRm5tbDB5MHVWSXFTR2FLSytJNG5rSDd5TEF2YnJmdkVpTXVECjRzbW1aMzF1TUY4MUdwdU9nb0lYc3hYdThZdEUvUXEwajdjRHhuTWVlaFpaN1BGWmFNNlNnbm0yT09rRkQyVkEKRXBSZWw1Zks2TVRUNVpsckp4Q2FsdFZDdU0waDRsY2VNV0R0c3RQNVlhU0hYSGFIcVdBc2l3RVFtNVlkSXZUbwpUaTFpKzBsUHVoSHV0RFJ2Y1NKdmFwVEtvS2pNZkg4dlI5N1FrZGZ0QzNBaUJOK3hNMTNWcjRzZ28wenFodTV0CmZ3RjREOTNTc2gwTzBMblNNSGhwQjF3Z3BDdmpUWEd0TzB2RDJkZWRlMit0M1VDcm82ZEJvUmV3SDJXT1lOTmwKZ21IN1hHbnc4NUdHSW9MMEl0KzlxV0RSVnVObmVaUkxaeThZMDgzREpjOGQ0ZnlEamc9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFb3dJQkFBS0NBUUVBb1ZVajE5YzUyWDY2ZkJlZUdkdXg2MHl3SmtJaFdyb0hmUENtZlg3SHlTYTRlZ3RpCjNGQ1RaY3ZxcmtGUnR2enhRTmM2c0hQdEVKZGtkQ2g4eWs0Vko4ZFlYRGpjc1ZOODFiUy9rZ3hQanBzMS9pTncKU1NNeGZXUTFHZE94cThwaXNWMTdSOHdUTUMrYUU1MUhMS0prT3pqbUN6bVhWVUkvTFMreW9CR2N4MWtqd0lQNQpnWUJoOWxpUnJnTHJBSCt4NWNkNGVxUCtLWmFlWHhvbmVFbFUvcUlVTVloSm5DckprZG5lY3I2UkFzOUJKN1FlCnl4SGZlY2xTZWJvWDBzQlY3bThBTHo3ZnR4Qk1wOU5Ha1BEZXVpV25NeE9nWjJrYXJWTFZlOWlPNkxEQks5RFQKcmpoS2M0UjFqYUVLQ204S25DUXVkWTNFSWp1U0x6YnovRTZMbVFJREFRQUJBb0lCQVFDUGdlUjRRb0s2N1BlRgpHcDBQODFTNE1XY2ZJUVA2YUMvdyt6K2RzZ0NVOVZSemUxMWRERytReFdyanhrYWh0eTRDdDNFRk5KbFRnTmRpClhBRmxFei9PT294bXZFM1RqcWdra0xzM2RxdnQ5ako0OVowVDhiSThENzhNVWpwZ3pZNHNwekxhRXJXZXp6a0cKNllnK005Vmt1S0FvcS9ucFpSdzlYWWhPeWx2akZnWVZrMWdjeGRDR2YrRnJHdVJPaE5BRC84QnF2aUNtOTJ4Wgo1bGtoWWNIU0x2VTF1MHRwS0Jkclpublk4MGMxMG1EbERLNmJpeUNiWVNhNVhBdUwrR1FRNFVGV2hXZG1SZDZrCmZocS9DM3BYTStSTjlPOThkSENtTGY5YUlpN2Jua3VlSFQ0WWF6S3ZTUGliN3VJN1lSYzNrL2ZsazcyWHFwaWoKbXh3UnlGUUJBb0dCQU02ZXZ0bHhtaHFRd0tHRHdreU0yK1I3K3hoemJUVjkrNk1LcnkxNWNIK3BKWjdnazZkMQpkM2c5ZU5naHVsMFlwTlYzK1pOanAwY2ZOZ0VRWU5BZDQzSDJIaHd3TXlBMmNHVHE0VFE4MU4yeGpudFNPME5WCnJoNDN3U21qV2YyOFJPY3RZVUFlYk12dXh5ektVay9iNHFSVUU5amxvSHNkc3N1ZkhiTkFPdU9wQW9HQkFNZmoKcHV3MVNiOHN2K3JxMjJpeDdCdkpmeEZBM3RYL2JZSHlOdmdpZmdwbVQzNUJDZnp5Qmd4K0Zyd05TOTZUbUlicQpYNEVCRW03ZTN3MGtEdUxZWFBGcmFzVy8yY1FFcUx5V05kZStFb3cyQmRHZVZpM1kxZ1BCU0VzWUhDa2YvMVhHCnY5VVhaU1RSYWhnbnR0MGdsam1PaGRDVm1pYTIvOHhlRGprZitGNXhBb0dBVCtwT1hzUDFtcmpLQ0s1eGhESW4KQ3FSNVplZWZJY1ZzZ284cldpZFNQODRvWXQ3eHZSOU42Zys4b2J2SjNTQWZBUUc2WWl0MUU2a2F0aWFqaTF0RQpFVnZrSVhyekMwNkRBa1ZtZlZIWjh6VXRxcjBQZHVlNHhLOUQ0dHJ2ZjVoRi9qUXJIU1duWnVrZjJFOFlyeEtaCkFuNFNmeDJ4aUd6Z0xxbUlUMEJVaHFFQ2dZQVVsemZYdHptTWp2Q0tJMzFNa0o5dzBWWGNraUVpVERpY25UWGEKWTdzMkdRbnhTSVBkNFpTTDd1VXFvL2YveXBaNHQyWDFKUVlnRTZkSWRFRndUcmRzU3hOcG9YU3VRNGlhUEtMNQpRV1FwdTFyb0YvWnFySjZITG43aTlXM1pNcW1ieldodmJBU0lRV1k3Yk1QaWpYdk1IQWxlempwZDZKWDdHR2xBCnF6RnJrUUtCZ0NOVGVZbHpmc256UEY1K0d2QjBncXpLSExVcWVhUHRLMTI1WjB4WHYyZkdYL1loTzNLKys5dWwKZ0ZOV0sxTVMvNGVOM2FONExZTGNqZm0xaW5nMEVVc2lXRHI1cVBiR1BzTDM4OWhPNjdOUytCTE1LTUhicHBmOAoyQjFYN1gwYy9IbVh2Z3F4N0JMeWtyYmxZRTFmNmdJUzY3Z2xGMXZLVkpyZzRLYm52YWtiCi0tLS0tRU5EIFJTQSBQUklWQVRFIEtFWS0tLS0tCg==
|
(4) west 클러스터 노드 확인
1
| kubectl get node --kubeconfig=./west-kubeconfig
|
✅ 출력
1
2
| NAME STATUS ROLES AGE VERSION
west-control-plane Ready control-plane,master 87s v1.23.17
|
(5) west 클러스터 전체 파드 확인
1
| kubectl get pod -A --kubeconfig=./west-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
| NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system coredns-bd6b6df9f-9jdh2 1/1 Running 0 93s
kube-system coredns-bd6b6df9f-l529w 1/1 Running 0 93s
kube-system etcd-west-control-plane 1/1 Running 0 108s
kube-system kindnet-57wjw 1/1 Running 0 93s
kube-system kube-apiserver-west-control-plane 1/1 Running 0 109s
kube-system kube-controller-manager-west-control-plane 1/1 Running 0 108s
kube-system kube-proxy-4z8dz 1/1 Running 0 93s
kube-system kube-scheduler-west-control-plane 1/1 Running 0 107s
local-path-storage local-path-provisioner-6668df4555-bmsxs 1/1 Running 0 93s
|
(6) west 노드에 필수 유틸리티 설치
1
| docker exec -it west-control-plane sh -c 'apt update && apt install tree psmisc lsof wget bridge-utils net-tools dnsutils tcpdump ngrep iputils-ping git vim -y'
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| ...
update-alternatives: using /usr/bin/vim.basic to provide /usr/bin/vim (vim) in auto mode
update-alternatives: using /usr/bin/vim.basic to provide /usr/bin/vimdiff (vimdiff) in auto mode
Setting up bind9-libs:amd64 (1:9.18.33-1~deb12u2) ...
Setting up openssh-client (1:9.2p1-2+deb12u6) ...
Setting up libxext6:amd64 (2:1.3.4-1+b1) ...
Setting up dbus-daemon (1.14.10-1~deb12u1) ...
Setting up libnet1:amd64 (1.1.6+dfsg-3.2) ...
Setting up libpcap0.8:amd64 (1.10.3-1) ...
Setting up dbus (1.14.10-1~deb12u1) ...
invoke-rc.d: policy-rc.d denied execution of start.
/usr/sbin/policy-rc.d returned 101, not running 'start dbus.service'
Setting up libgdbm-compat4:amd64 (1.23-3) ...
Setting up xauth (1:1.1.2-1) ...
Setting up bind9-host (1:9.18.33-1~deb12u2) ...
Setting up libperl5.36:amd64 (5.36.0-7+deb12u2) ...
Setting up tcpdump (4.99.3-1) ...
Setting up ngrep (1.47+ds1-5+b1) ...
Setting up perl (5.36.0-7+deb12u2) ...
Setting up bind9-dnsutils (1:9.18.33-1~deb12u2) ...
Setting up dnsutils (1:9.18.33-1~deb12u2) ...
Setting up liberror-perl (0.17029-2) ...
Setting up git (1:2.39.5-0+deb12u2) ...
Processing triggers for libc-bin (2.36-9+deb12u4) ...
|
(7) west 클러스터에 kube-ops-view 설치
1
| helm install kube-ops-view geek-cookbook/kube-ops-view --version 1.2.2 --set service.main.type=NodePort,service.main.ports.http.nodePort=30005 --set env.TZ="Asia/Seoul" --namespace kube-system --kubeconfig=./west-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| NAME: kube-ops-view
LAST DEPLOYED: Sat May 24 20:09:33 2025
NAMESPACE: kube-system
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
1. Get the application URL by running these commands:
export NODE_PORT=$(kubectl get --namespace kube-system -o jsonpath="{.spec.ports[0].nodePort}" services kube-ops-view)
export NODE_IP=$(kubectl get nodes --namespace kube-system -o jsonpath="{.items[0].status.addresses[0].address}")
echo http://$NODE_IP:$NODE_PORT
|
(8) kube-ops-view 접속: http://localhost:31005/#scale=1.5
2. east 클러스터 설정 및 확인
(1) east 클러스터 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| kind create cluster --name east --image kindest/node:v1.23.17 --kubeconfig ./east-kubeconfig --config - <<EOF
kind: Cluster
apiVersion: kind.x-k8s.io/v1alpha4
nodes:
- role: control-plane
extraPortMappings:
- containerPort: 31000 # istio-ingrssgateway HTTP
hostPort: 31000
- containerPort: 31001 # Prometheus
hostPort: 31001
- containerPort: 31002 # Grafana
hostPort: 31002
- containerPort: 31003 # Kiali
hostPort: 31003
- containerPort: 31004 # Tracing
hostPort: 31004
- containerPort: 31005 # kube-ops-view
hostPort: 31005
networking:
podSubnet: 10.20.0.0/16
serviceSubnet: 10.200.0.0/24
EOF
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
| Creating cluster "east" ...
✓ Ensuring node image (kindest/node:v1.23.17) 🖼
✓ Preparing nodes 📦
✓ Writing configuration 📜
✓ Starting control-plane 🕹️
✓ Installing CNI 🔌
✓ Installing StorageClass 💾
Set kubectl context to "kind-east"
You can now use your cluster with:
kubectl cluster-info --context kind-east --kubeconfig ./east-kubeconfig
Not sure what to do next? 😅 Check out https://kind.sigs.k8s.io/docs/user/quick-start/
|
(2) east 클러스터 상태 확인
✅ 출력
1
2
3
| CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
73615dfe014f kindest/node:v1.23.17 "/usr/local/bin/entr…" About a minute ago Up About a minute 0.0.0.0:31000-31005->31000-31005/tcp, 127.0.0.1:40783->6443/tcp east-control-plane
5034b4c2be0c kindest/node:v1.23.17 "/usr/local/bin/entr…" 7 minutes ago Up 7 minutes 0.0.0.0:30000-30005->30000-30005/tcp, 127.0.0.1:36143->6443/tcp west-control-plane
|
(3) east 클러스터 kubeconfig 내용 확인
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1EVXlOREV4TVRJek1Gb1hEVE0xTURVeU1qRXhNVEl6TUZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTlhICkR5Q2F3bGdNdXJ1Q0N3bFlTTkEwS2VTZWdtYUhHSnlYVnc1Y25RTm04ZUErM2E3dWcxR2hlYWUxWm9Hb2g4SlUKVC9laW9IcTM1Wk9zdVNLTExyOWc5YTAvUmpsRnVwVnNnQXltcGcxc3FFNzN2Y2dhYVFEYXBDMFhDODZ6cnZtcAplc2dVNHZCZGNzWkRrRnJUZHlyaWFCSm85L3FRZmtoU3J0cFV1cGE3T0Yrbzd5MTRWV245Z1lLbjlrWnI4VVVLCjJLYUFVc0xSMWZrRi9LTXA3UGptNnNFcUtLc3NsTXRhQnpvTm5jRnIrSWM4aGwwclpPMEgzVXJDV242STlIcEQKLy9Sd0JKWXFNRElsS1pRVkowOUsweGVjcmNjdjdkdFltcUtzMjNIYXVHbXk4eFl0Q3phSjBPOGVScnpiMERycQptWlNERWJtRzh4YjZsTFM4b2RrQ0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZKTjJxL2FYQjc4Q0E2aEhYTFcxMGxIcVVrNXlNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBTExSUkZqOEpzN3ROZnZ4YUtMaQpqbFIxbWdsNytrYzRtam1ReExBUGx1NnNxQ1BHR1BNcGFqdG9jaHhHdVhOVTQvWEF4SWZ6d0pDNUpBMUZFMGMvCkRWUVhpRy9XQ3FDUkl1ZExFQTY3bkljQ0RJRnR0NmRHbkk0by9VbDluWW82S2RnTjNXVm9RcmNjMTIyMUpIencKM0FqNDdKK0k4WDR1RWppU2pTdDlXQWtwYThFN3ZEelFXelpJZU9yMmZadEx0SHo1dkZaZVNPWVIvNVpWZmtWNAo2ejNXeW13TE8rN3ZjOU5nV0VCeUM1RmJDWG9raWNiOWhlTVhjT0hxelVORERBaTJNdTcvNFNZRXg1Ty84RlpvCmVrMzJHdVpyKzVnRzNLc2hSaU9laHdyQWJWOHJRemJpVUZBcXdLSVozeXUyZXYwSzdqUCt4Y2c0OXo4cHF0N2sKeUxJPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://127.0.0.1:40783
name: kind-east
contexts:
- context:
cluster: kind-east
user: kind-east
name: kind-east
current-context: kind-east
kind: Config
preferences: {}
users:
- name: kind-east
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURJVENDQWdtZ0F3SUJBZ0lJY0U1MFFVRERFK0F3RFFZSktvWklodmNOQVFFTEJRQXdGVEVUTUJFR0ExVUUKQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TlRBMU1qUXhNVEV5TXpCYUZ3MHlOakExTWpReE1URXlNek5hTURReApGekFWQmdOVkJBb1REbk41YzNSbGJUcHRZWE4wWlhKek1Sa3dGd1lEVlFRREV4QnJkV0psY201bGRHVnpMV0ZrCmJXbHVNSUlCSWpBTkJna3Foa2lHOXcwQkFRRUZBQU9DQVE4QU1JSUJDZ0tDQVFFQXc1VjRlZFdNWk9ob2RMQkoKNEl4dFV5VjZYY2xXVmN2U3pBMUlaOUhVU1A2d016QlVsVE5SanBXWlo0QkJmQStZYmpzN1J5RlQ1Q05WVUxOSQpoVmtXbitKcGorM2NDTWVrby9kWktrTEI2TTB3TjVVSnNpb3JZS1M0YjRpUUVZdEVudEErd0xEZnN4VVdqZ3hJCmt4K3JWOHFaZWowWWVOYk54KzF4K1ByWDlLNGhGT0hIZHBwQTJ0aGdxdEU4eXdhaVhqamVUYjRhYlh1bDVyUUkKVVBvRFJ0YUorYjFWWjdnS1FubHY3SGo0ZTk2Vm52di9vNlZPZEJLRnRWWWZnQUNCMGY4R1VWOWU0dUx3R3k2NgpyRW1UWFJzNjRJSlNMT3lWUUpNVnRja3ZrZ0h2Qk5IMEVnNWZNejY3aGVuZHFFV2wvbUJockI2aU0yY2JqTGlWCitZcy94d0lEQVFBQm8xWXdWREFPQmdOVkhROEJBZjhFQkFNQ0JhQXdFd1lEVlIwbEJBd3dDZ1lJS3dZQkJRVUgKQXdJd0RBWURWUjBUQVFIL0JBSXdBREFmQmdOVkhTTUVHREFXZ0JTVGRxdjJsd2UvQWdPb1IxeTF0ZEpSNmxKTwpjakFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBV3I5YU1DM1dTMFFhVk1MSEc3Vnd3czhtbURRbzdTb0o5cG0yCkUrSkdOWXFtbHg2MVFVcWd5YkE0OGdGSG95OXlUQWxrZ0tmSm9ERXZKa3NRb09COWl4YjkxbDNld2Z1L2sxak0KN2dpSzgxM0t0V2hYSUxmZU1DaXNWVStMNjk0bm5jNU5Ka09JSG5rODQzSjdwbTg5bU1EU2d2ejM0dVZiUE9ELwo3SUdITXY0MWJzNExWR1g3Q2x0clFhK0VxNlBvZHgzOFJDUHI3bFF2N1BBenBoY0wrVnZCR29aMkN1bWxPQTI4Ck9vd3VxNGJzMGdrMFdhbG9KMzkyb3REdUcyR2Z2b29FT2xPcS9oa0t0eDFuS25icjJxUzJxc0FzYVVLeVNsVCsKSXNZdk5JbW9QcVFYdWkwL1grNGZ1TFhua0IzOUVKQWpaWCtPZEI4czhmQUN5SjY5eXc9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBdzVWNGVkV01aT2hvZExCSjRJeHRVeVY2WGNsV1ZjdlN6QTFJWjlIVVNQNndNekJVCmxUTlJqcFdaWjRCQmZBK1lianM3UnlGVDVDTlZVTE5JaFZrV24rSnBqKzNjQ01la28vZFpLa0xCNk0wd041VUoKc2lvcllLUzRiNGlRRVl0RW50QSt3TERmc3hVV2pneElreCtyVjhxWmVqMFllTmJOeCsxeCtQclg5SzRoRk9ISApkcHBBMnRoZ3F0RTh5d2FpWGpqZVRiNGFiWHVsNXJRSVVQb0RSdGFKK2IxVlo3Z0tRbmx2N0hqNGU5NlZudnYvCm82Vk9kQktGdFZZZmdBQ0IwZjhHVVY5ZTR1THdHeTY2ckVtVFhSczY0SUpTTE95VlFKTVZ0Y2t2a2dIdkJOSDAKRWc1Zk16NjdoZW5kcUVXbC9tQmhyQjZpTTJjYmpMaVYrWXMveHdJREFRQUJBb0lCQVFDQ3dKbFRNZTF5eEdDWQpxZ1lwcFJldFAxL245U0xQcHJ5ZEI4QkJEK2tRaDV2NkRMUnZMbWkybnRKNGZDakxMSTNtRzVrTWUzNWZCVFFUCkNGaFNOWFhIbTVDZzFRNkZuQm80TjdNWGFwdkI2L0x4SmFUZXhBeE54ckU2ZHh5QmJnNkk4WVVTUXV5NkJ6NFYKNXFaYUhSRHFWeHAxdXdSeVBJQkR5VHlwaStEMXhJd3JhM25TTkNzWVdFUUxaOFF3L3BwOWdyRWwrdlhlV1VVegptdFFtWU8wN3M3R1pOUFRzVFRCaUZkYkFEeHVobitZNFlyZGVxdkJRTW4yb3d0QkpSSklxRUhhRjg1TzVRSHpKCjhpZDdtZVJZWGEwd25pVzNMWmZ2cUViMDZFbWlqVlE2b3RWVUlsS3BTb2tsQTFlOE1BaU53a0FBdXFaVkRDMzEKWXM5Z2RkRUpBb0dCQU5qMjdUOWVLL01NZW5OMHVkMUdGMndld1RQcHkxSEtqR2VtQnZnTE16TXRiTHFxMVE5cgozNnVxVUsxZExLZGk3RkRVT3daeDIyeDhtcEpJdUZMTVpZT3daTVRqYmpVY3ovSlo3M1pBWWNUM1NPcXd4VVNoCjRvYzJ3aHBZcEV5bGJieTY1aFoyTnFTWnB6REZhdXJGaDU4ZFBSUGhSRHE1ZCtQWWZvRVI2WE9GQW9HQkFPYkYKeDhSU1BlR1JMcjN5OWtaWlZjV0JtL3RlNUw1dFNmemh1SlRpYU94N0lHRCtJVmRoL0h5dHJ2K1Z0Vzgyd3BveApITExRS1dZSG1pNGFyVk1BdDI4WXJUWjFydmEyYm1NdVpSMm1FSTVFNXVDY3hlUTFMaUtCUlFuQkRXZncrUm5LCkNQRFNIdGh1U2NsVlVJdUdpUGZNd2pTLzFkS3JEYjNRdjN3ak9zbmJBb0dCQUlLNzk2VlJWMll5eEs1QlRhVzUKa0crRDhLTVpZM3c3Y25NYUplVGN5dE14c2V5Zzk1VTlTUitsbHN0LzgySkJSMmhGR2ZQK00xdWhrWHBIKzFsWQo5R3B2cGFqRjZpaHkzaEtJZ3JSY2d3MHVmRzkrYUwrOFZFVnBoM2hjcFZQUjh0ZmdQcmlXTHNMc0cwUldFT0M2CmVjZzAxQkxna0Q1YWQ1V0JaR2pkcERBSkFvR0FZdTBaNjhETm9pcVlmUGp3TmN3S0JyYSs1UTBTeGNjWDFuMzAKb0c1R1NFbW40YXhQSXFSd2xnbm1ZTTRPanZSTWk4ak40cUYxZmJWNGxKYi9BZnZtcG90UGhXOEJaK1ZnZ01mYwp0TThCZmR0dmxZM2ZEeXIwOGZtMFhMQVRUU0Z4eDJwaVZzbmNTeTlNRmpDcWJJVnBwY0J5NkNYc1JYanFWUnB0Clc0dkdvYzBDZ1lCU1dYVjJwa1BUVU1PeTBIVTVhSVluTWM4bG9IYmpHYy90eWdVYkYxYUlEQnNIR1k3SUx1Tk8KSmQwS3htMjlkaXBsNWw3aS9sdnRxYlNVaDI5cXBoM21zYloxTjVUWXdEUUZpQlI5U1E2VElPd0FxRVphM3lSSwpRdE43MUdoS2FmY2xZYURCWHhEdUlaR2sycG5iUGEzV0EvNGpMdGxkSXd6bHpnOGNrWk04SWc9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
|
(4) east 클러스터 노드 확인
1
| kubectl get node --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
| NAME STATUS ROLES AGE VERSION
east-control-plane Ready control-plane,master 108s v1.23.17
|
(5) east 클러스터 전체 파드 확인
1
| kubectl get pod -A --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
| NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system coredns-bd6b6df9f-vwdrq 1/1 Running 0 2m2s
kube-system coredns-bd6b6df9f-wglvp 1/1 Running 0 2m2s
kube-system etcd-east-control-plane 1/1 Running 0 2m17s
kube-system kindnet-6k8jk 1/1 Running 0 2m3s
kube-system kube-apiserver-east-control-plane 1/1 Running 0 2m18s
kube-system kube-controller-manager-east-control-plane 1/1 Running 0 2m17s
kube-system kube-proxy-57w4c 1/1 Running 0 2m3s
kube-system kube-scheduler-east-control-plane 1/1 Running 0 2m18s
local-path-storage local-path-provisioner-6668df4555-pns5j 1/1 Running 0 2m2s
|
(6) east 노드에 필수 유틸리티 설치
1
| docker exec -it east-control-plane sh -c 'apt update && apt install tree psmisc lsof wget bridge-utils net-tools dnsutils tcpdump ngrep iputils-ping git vim -y'
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| ...
update-alternatives: using /usr/bin/vim.basic to provide /usr/bin/vim (vim) in auto mode
update-alternatives: using /usr/bin/vim.basic to provide /usr/bin/vimdiff (vimdiff) in auto mode
Setting up bind9-libs:amd64 (1:9.18.33-1~deb12u2) ...
Setting up openssh-client (1:9.2p1-2+deb12u6) ...
Setting up libxext6:amd64 (2:1.3.4-1+b1) ...
Setting up dbus-daemon (1.14.10-1~deb12u1) ...
Setting up libnet1:amd64 (1.1.6+dfsg-3.2) ...
Setting up libpcap0.8:amd64 (1.10.3-1) ...
Setting up dbus (1.14.10-1~deb12u1) ...
invoke-rc.d: policy-rc.d denied execution of start.
/usr/sbin/policy-rc.d returned 101, not running 'start dbus.service'
Setting up libgdbm-compat4:amd64 (1.23-3) ...
Setting up xauth (1:1.1.2-1) ...
Setting up bind9-host (1:9.18.33-1~deb12u2) ...
Setting up libperl5.36:amd64 (5.36.0-7+deb12u2) ...
Setting up tcpdump (4.99.3-1) ...
Setting up ngrep (1.47+ds1-5+b1) ...
Setting up perl (5.36.0-7+deb12u2) ...
Setting up bind9-dnsutils (1:9.18.33-1~deb12u2) ...
Setting up dnsutils (1:9.18.33-1~deb12u2) ...
Setting up liberror-perl (0.17029-2) ...
Setting up git (1:2.39.5-0+deb12u2) ...
Processing triggers for libc-bin (2.36-9+deb12u4) ...
|
(7) east 클러스터에 kube-ops-view 설치
1
| helm install kube-ops-view geek-cookbook/kube-ops-view --version 1.2.2 --set service.main.type=NodePort,service.main.ports.http.nodePort=31005 --set env.TZ="Asia/Seoul" --namespace kube-system --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| NAME: kube-ops-view
LAST DEPLOYED: Sat May 24 20:16:44 2025
NAMESPACE: kube-system
STATUS: deployed
REVISION: 1
TEST SUITE: None
NOTES:
1. Get the application URL by running these commands:
export NODE_PORT=$(kubectl get --namespace kube-system -o jsonpath="{.spec.ports[0].nodePort}" services kube-ops-view)
export NODE_IP=$(kubectl get nodes --namespace kube-system -o jsonpath="{.items[0].status.addresses[0].address}")
echo http://$NODE_IP:$NODE_PORT
|
(8) east 클러스터 kube-ops-view 리소스 확인
1
| kubectl get deploy,pod,svc,ep -n kube-system -l app.kubernetes.io/instance=kube-ops-view --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/kube-ops-view 1/1 1 1 22s
NAME READY STATUS RESTARTS AGE
pod/kube-ops-view-79df45849b-ffhdt 1/1 Running 0 22s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kube-ops-view NodePort 10.200.0.202 <none> 8080:31005/TCP 22s
NAME ENDPOINTS AGE
endpoints/kube-ops-view 10.20.0.5:8080 22s
|
(9) kube-ops-view 접속: http://localhost:31005/#scale=1.5
3. kind docker network 에 테스트용 PC(실제로는 컨테이너) 배포
(1) kind 도커 네트워크 존재 여부 확인
✅ 출력
1
2
3
4
5
| NETWORK ID NAME DRIVER SCOPE
6a9f11e74d24 bridge bridge local
bb4d74152d4a host host local
dbf072d0a217 kind bridge local
056dcb2c01d1 none null local
|
(2) kind 네트워크 상세 정보 확인
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| [
{
"Name": "kind",
"Id": "dbf072d0a217f53e0b62f42cee01bcecc1b2f6ea216475178db001f2e38681f5",
"Created": "2025-01-26T16:18:22.33980443+09:00",
"Scope": "local",
"Driver": "bridge",
"EnableIPv4": true,
"EnableIPv6": true,
"IPAM": {
"Driver": "default",
"Options": {},
"Config": [
{
"Subnet": "172.18.0.0/16",
"Gateway": "172.18.0.1"
},
{
"Subnet": "fc00:f853:ccd:e793::/64",
"Gateway": "fc00:f853:ccd:e793::1"
}
]
},
"Internal": false,
"Attachable": false,
"Ingress": false,
"ConfigFrom": {
"Network": ""
},
"ConfigOnly": false,
"Containers": {
"5034b4c2be0c6366c4af3f74729bc403f4b185071f24f78f8c9204a0fd70505b": {
"Name": "west-control-plane",
"EndpointID": "2b771bb71deb46ca3c77803fe7c5aa8efe0310231db4f70d89c524684d7b5e7d",
"MacAddress": "be:87:27:44:67:ba",
"IPv4Address": "172.18.0.2/16",
"IPv6Address": "fc00:f853:ccd:e793::2/64"
},
"73615dfe014f7131cb6ee7e0313d0fad8753486ba666cd0540d47f70013a635d": {
"Name": "east-control-plane",
"EndpointID": "3b9e29234a6e859af628da2d702a83b79a1bb64b6ca0f0736338ec1022ff71bb",
"MacAddress": "36:d5:ec:c8:4d:2b",
"IPv4Address": "172.18.0.3/16",
"IPv6Address": "fc00:f853:ccd:e793::3/64"
}
},
"Options": {
"com.docker.network.bridge.enable_ip_masquerade": "true",
"com.docker.network.driver.mtu": "1500"
},
"Labels": {}
}
]
|
(3) 테스트용 컨테이너(mypc) kind 네트워크로 실행
1
| docker run -d --rm --name mypc --network kind --ip 172.18.0.100 nicolaka/netshoot sleep infinity
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
| Unable to find image 'nicolaka/netshoot:latest' locally
latest: Pulling from nicolaka/netshoot
4abcf2066143: Pull complete
f72249ed6705: Pull complete
d21093198226: Pull complete
ff793c57efef: Pull complete
b8cdfec6d24e: Pull complete
b6621d484422: Pull complete
452eb7889eb5: Pull complete
4f4fb700ef54: Pull complete
89065cf5c037: Pull complete
a4b421d4901a: Pull complete
d5c3ad7ea15a: Pull complete
ab073295bbd0: Pull complete
737c1bf9f2ef: Pull complete
097ac21093f8: Pull complete
59e353e0ee74: Pull complete
Digest: sha256:a20c2531bf35436ed3766cd6cfe89d352b050ccc4d7005ce6400adf97503da1b
Status: Downloaded newer image for nicolaka/netshoot:latest
f977b6273bccb6808733f26d59307c4f0a26cf682e37bfe686c3e8446e4bee9d
|
(4) 실행 중인 컨테이너 목록 확인
✅ 출력
1
2
3
4
| CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
f977b6273bcc nicolaka/netshoot "sleep infinity" 39 seconds ago Up 36 seconds mypc
73615dfe014f kindest/node:v1.23.17 "/usr/local/bin/entr…" 10 minutes ago Up 10 minutes 0.0.0.0:31000-31005->31000-31005/tcp, 127.0.0.1:40783->6443/tcp east-control-plane
5034b4c2be0c kindest/node:v1.23.17 "/usr/local/bin/entr…" 16 minutes ago Up 16 minutes 0.0.0.0:30000-30005->30000-30005/tcp, 127.0.0.1:36143->6443/tcp west-control-plane
|
(5) kind 네트워크 내 각 컨테이너의 IP 주소 확인
1
| docker ps -q | xargs docker inspect --format ' '
|
✅ 출력
1
2
3
| /mypc 172.18.0.100
/east-control-plane 172.18.0.3
/west-control-plane 172.18.0.2
|
(6) 컨테이너 간 IP 기반 네트워크 통신 확인
mypc에서 west-control-plane, east-control-plane의 IP로 ping 테스트
1
| docker exec -it mypc ping -c 1 172.18.0.2
|
✅ 출력
1
2
3
4
5
6
| PING 172.18.0.2 (172.18.0.2) 56(84) bytes of data.
64 bytes from 172.18.0.2: icmp_seq=1 ttl=64 time=0.097 ms
--- 172.18.0.2 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.097/0.097/0.097/0.000 ms
|
1
| docker exec -it mypc ping -c 1 172.18.0.3
|
✅ 출력
1
2
3
4
5
6
| PING 172.18.0.3 (172.18.0.3) 56(84) bytes of data.
64 bytes from 172.18.0.3: icmp_seq=1 ttl=64 time=0.082 ms
--- 172.18.0.3 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.082/0.082/0.082/0.000 ms
|
(7) 컨테이너 간 도메인 기반 네트워크 통신 확인
mypc에서 컨테이너 이름(west-control-plane, east-control-plane)으로 ping
1
| docker exec -it mypc ping -c 1 west-control-plane
|
✅ 출력
1
2
3
4
5
6
| PING west-control-plane (172.18.0.2) 56(84) bytes of data.
64 bytes from west-control-plane.kind (172.18.0.2): icmp_seq=1 ttl=64 time=0.041 ms
--- west-control-plane ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.041/0.041/0.041/0.000 ms
|
1
| docker exec -it mypc ping -c 1 east-control-plane
|
✅ 출력
1
2
3
4
5
6
| PING east-control-plane (172.18.0.3) 56(84) bytes of data.
64 bytes from east-control-plane.kind (172.18.0.3): icmp_seq=1 ttl=64 time=0.059 ms
--- east-control-plane ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.059/0.059/0.059/0.000 ms
|
(8) west → east 컨테이너 이름 기반 ping 테스트
west-control-plane에서 east-control-plane으로 ping 수행
1
| docker exec -it west-control-plane ping -c 1 east-control-plane
|
✅ 출력
1
2
3
4
5
6
| PING east-control-plane(east-control-plane.kind (fc00:f853:ccd:e793::3)) 56 data bytes
64 bytes from east-control-plane.kind (fc00:f853:ccd:e793::3): icmp_seq=1 ttl=64 time=0.119 ms
--- east-control-plane ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.119/0.119/0.119/0.000 ms
|
(9) east → west 컨테이너 이름 기반 ping 테스트
east-control-plane에서 west-control-plane으로 ping 수행
1
| docker exec -it east-control-plane ping -c 1 west-control-plane
|
✅ 출력
1
2
3
4
5
6
| PING west-control-plane(west-control-plane.kind (fc00:f853:ccd:e793::2)) 56 data bytes
64 bytes from west-control-plane.kind (fc00:f853:ccd:e793::2): icmp_seq=1 ttl=64 time=0.076 ms
--- west-control-plane ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.076/0.076/0.076/0.000 ms
|
(10) west → mypc 컨테이너 이름 기반 ping 테스트
west-control-plane에서 mypc로 ping 수행
1
| docker exec -it west-control-plane ping -c 1 mypc
|
✅ 출력
1
2
3
4
5
6
| PING mypc(mypc.kind (fc00:f853:ccd:e793::4)) 56 data bytes
64 bytes from mypc.kind (fc00:f853:ccd:e793::4): icmp_seq=1 ttl=64 time=0.076 ms
--- mypc ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.076/0.076/0.076/0.000 ms
|
(11) east → mypc 컨테이너 이름 기반 ping 테스트
east-control-plane에서 mypc로 ping 수행
1
| docker exec -it east-control-plane ping -c 1 mypc
|
✅ 출력
1
2
3
4
5
6
| PING mypc(mypc.kind (fc00:f853:ccd:e793::4)) 56 data bytes
64 bytes from mypc.kind (fc00:f853:ccd:e793::4): icmp_seq=1 ttl=64 time=0.089 ms
--- mypc ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.089/0.089/0.089/0.000 ms
|
1
2
| kubectl apply -f https://raw.githubusercontent.com/metallb/metallb/v0.14.9/config/manifests/metallb-native.yaml \
--kubeconfig=./west-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| namespace/metallb-system created
customresourcedefinition.apiextensions.k8s.io/bfdprofiles.metallb.io created
customresourcedefinition.apiextensions.k8s.io/bgpadvertisements.metallb.io created
customresourcedefinition.apiextensions.k8s.io/bgppeers.metallb.io created
customresourcedefinition.apiextensions.k8s.io/communities.metallb.io created
customresourcedefinition.apiextensions.k8s.io/ipaddresspools.metallb.io created
customresourcedefinition.apiextensions.k8s.io/l2advertisements.metallb.io created
customresourcedefinition.apiextensions.k8s.io/servicel2statuses.metallb.io created
serviceaccount/controller created
serviceaccount/speaker created
role.rbac.authorization.k8s.io/controller created
role.rbac.authorization.k8s.io/pod-lister created
clusterrole.rbac.authorization.k8s.io/metallb-system:controller created
clusterrole.rbac.authorization.k8s.io/metallb-system:speaker created
rolebinding.rbac.authorization.k8s.io/controller created
rolebinding.rbac.authorization.k8s.io/pod-lister created
clusterrolebinding.rbac.authorization.k8s.io/metallb-system:controller created
clusterrolebinding.rbac.authorization.k8s.io/metallb-system:speaker created
configmap/metallb-excludel2 created
secret/metallb-webhook-cert created
service/metallb-webhook-service created
deployment.apps/controller created
daemonset.apps/speaker created
validatingwebhookconfiguration.admissionregistration.k8s.io/metallb-webhook-configuration created
|
1
2
| kubectl apply -f https://raw.githubusercontent.com/metallb/metallb/v0.14.9/config/manifests/metallb-native.yaml \
--kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| namespace/metallb-system created
customresourcedefinition.apiextensions.k8s.io/bfdprofiles.metallb.io created
customresourcedefinition.apiextensions.k8s.io/bgpadvertisements.metallb.io created
customresourcedefinition.apiextensions.k8s.io/bgppeers.metallb.io created
customresourcedefinition.apiextensions.k8s.io/communities.metallb.io created
customresourcedefinition.apiextensions.k8s.io/ipaddresspools.metallb.io created
customresourcedefinition.apiextensions.k8s.io/l2advertisements.metallb.io created
customresourcedefinition.apiextensions.k8s.io/servicel2statuses.metallb.io created
serviceaccount/controller created
serviceaccount/speaker created
role.rbac.authorization.k8s.io/controller created
role.rbac.authorization.k8s.io/pod-lister created
clusterrole.rbac.authorization.k8s.io/metallb-system:controller created
clusterrole.rbac.authorization.k8s.io/metallb-system:speaker created
rolebinding.rbac.authorization.k8s.io/controller created
rolebinding.rbac.authorization.k8s.io/pod-lister created
clusterrolebinding.rbac.authorization.k8s.io/metallb-system:controller created
clusterrolebinding.rbac.authorization.k8s.io/metallb-system:speaker created
configmap/metallb-excludel2 created
secret/metallb-webhook-cert created
service/metallb-webhook-service created
deployment.apps/controller created
daemonset.apps/speaker created
validatingwebhookconfiguration.admissionregistration.k8s.io/metallb-webhook-configuration created
|
3. 각 클러스터의 CRD 생성 확인
1
2
| kubectl get crd --kubeconfig=./west-kubeconfig
kubectl get crd --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| NAME CREATED AT
bfdprofiles.metallb.io 2025-05-24T11:28:41Z
bgpadvertisements.metallb.io 2025-05-24T11:28:41Z
bgppeers.metallb.io 2025-05-24T11:28:41Z
communities.metallb.io 2025-05-24T11:28:41Z
ipaddresspools.metallb.io 2025-05-24T11:28:41Z
l2advertisements.metallb.io 2025-05-24T11:28:41Z
servicel2statuses.metallb.io 2025-05-24T11:28:41Z
NAME CREATED AT
bfdprofiles.metallb.io 2025-05-24T11:29:05Z
bgpadvertisements.metallb.io 2025-05-24T11:29:05Z
bgppeers.metallb.io 2025-05-24T11:29:05Z
communities.metallb.io 2025-05-24T11:29:06Z
ipaddresspools.metallb.io 2025-05-24T11:29:06Z
l2advertisements.metallb.io 2025-05-24T11:29:06Z
servicel2statuses.metallb.io 2025-05-24T11:29:06Z
|
1
2
| kubectl get pod -n metallb-system --kubeconfig=./west-kubeconfig
kubectl get pod -n metallb-system --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
| NAME READY STATUS RESTARTS AGE
controller-686c7db689-wlhwf 1/1 Running 0 92s
speaker-9mzbd 1/1 Running 0 92s
NAME READY STATUS RESTARTS AGE
controller-686c7db689-5wf5v 1/1 Running 0 67s
speaker-f4cj7 1/1 Running 0 67s
|
5. west 클러스터 IPAddressPool 및 L2Advertisement 설정
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| cat << EOF | kubectl apply --kubeconfig=./west-kubeconfig -f -
apiVersion: metallb.io/v1beta1
kind: IPAddressPool
metadata:
name: default
namespace: metallb-system
spec:
addresses:
- 172.18.255.101-172.18.255.120
---
apiVersion: metallb.io/v1beta1
kind: L2Advertisement
metadata:
name: default
namespace: metallb-system
spec:
ipAddressPools:
- default
EOF
# 결과
ipaddresspool.metallb.io/default created
l2advertisement.metallb.io/default created
|
6. east 클러스터 IPAddressPool 및 L2Advertisement 설정
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| cat << EOF | kubectl apply --kubeconfig=./east-kubeconfig -f -
apiVersion: metallb.io/v1beta1
kind: IPAddressPool
metadata:
name: default
namespace: metallb-system
spec:
addresses:
- 172.18.255.201-172.18.255.220
---
apiVersion: metallb.io/v1beta1
kind: L2Advertisement
metadata:
name: default
namespace: metallb-system
spec:
ipAddressPools:
- default
EOF
# 결과
ipaddresspool.metallb.io/default created
l2advertisement.metallb.io/default created
|
7. 설정된 IPAddressPool, L2Advertisement 확인
1
2
| kubectl get IPAddressPool,L2Advertisement -A --kubeconfig=./west-kubeconfig
kubectl get IPAddressPool,L2Advertisement -A --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| NAMESPACE NAME AUTO ASSIGN AVOID BUGGY IPS ADDRESSES
metallb-system ipaddresspool.metallb.io/default true false ["172.18.255.101-172.18.255.120"]
NAMESPACE NAME IPADDRESSPOOLS IPADDRESSPOOL SELECTORS INTERFACES
metallb-system l2advertisement.metallb.io/default ["default"]
NAMESPACE NAME AUTO ASSIGN AVOID BUGGY IPS ADDRESSES
metallb-system ipaddresspool.metallb.io/default true false ["172.18.255.201-172.18.255.220"]
NAMESPACE NAME IPADDRESSPOOLS IPADDRESSPOOL SELECTORS INTERFACES
metallb-system l2advertisement.metallb.io/default ["default"]
|
🚀 nginx 샘플 서비스 테스트
1. west 클러스터에 nginx 배포 및 LoadBalancer Service 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| cat << EOF | kubectl apply --kubeconfig=./west-kubeconfig -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
spec:
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:latest
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx-service
spec:
selector:
app: nginx
ports:
- port: 80
targetPort: 80
type: LoadBalancer
EOF
# 결과
deployment.apps/nginx created
service/nginx-service created
|
2. east 클러스터에 nginx 배포 및 LoadBalancer Service 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| cat << EOF | kubectl apply --kubeconfig=./east-kubeconfig -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
spec:
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:latest
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx-service
spec:
selector:
app: nginx
ports:
- port: 80
targetPort: 80
type: LoadBalancer
EOF
# 결과
deployment.apps/nginx created
service/nginx-service created
|
3. nginx 서비스 리소스 상태 확인
1
2
| kubectl get deploy,pod,svc,ep --kubeconfig=./west-kubeconfig
kubectl get deploy,pod,svc,ep --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/nginx 1/1 1 1 53s
NAME READY STATUS RESTARTS AGE
pod/nginx-8d545c96d-9c8x9 1/1 Running 0 53s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.100.0.1 <none> 443/TCP 27m
service/nginx-service LoadBalancer 10.100.0.115 172.18.255.101 80:31719/TCP 53s
NAME ENDPOINTS AGE
endpoints/kubernetes 172.18.0.2:6443 27m
endpoints/nginx-service 10.10.0.7:80 53s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/nginx 1/1 1 1 24s
NAME READY STATUS RESTARTS AGE
pod/nginx-8d545c96d-2p7sp 1/1 Running 0 24s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.200.0.1 <none> 443/TCP 21m
service/nginx-service LoadBalancer 10.200.0.38 172.18.255.201 80:30652/TCP 24s
NAME ENDPOINTS AGE
endpoints/kubernetes 172.18.0.3:6443 21m
endpoints/nginx-service 10.20.0.7:80 24s
|
4. LoadBalancer 외부 IP 확인
1
2
3
4
| kubectl get svc nginx-service --kubeconfig=./west-kubeconfig -o jsonpath='{.status.loadBalancer.ingress[0].ip}'
kubectl get svc nginx-service --kubeconfig=./east-kubeconfig -o jsonpath='{.status.loadBalancer.ingress[0].ip}'
WNIP=$(kubectl get svc nginx-service --kubeconfig=./west-kubeconfig -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
ENIP=$(kubectl get svc nginx-service --kubeconfig=./east-kubeconfig -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
|
✅ 출력
1
2
| 172.18.255.101
172.18.255.201
|
5. 외부 컨테이너에서 west nginx 서비스 접근 확인
1
| docker exec -it mypc curl -s $WNIP
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
|
1
| docker exec -it mypc curl -s $WNIP -v -I
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| * Trying 172.18.255.101:80...
* Connected to 172.18.255.101 (172.18.255.101) port 80
> HEAD / HTTP/1.1
> Host: 172.18.255.101
> User-Agent: curl/8.7.1
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
HTTP/1.1 200 OK
< Server: nginx/1.27.5
Server: nginx/1.27.5
< Date: Sat, 24 May 2025 11:36:00 GMT
Date: Sat, 24 May 2025 11:36:00 GMT
< Content-Type: text/html
Content-Type: text/html
< Content-Length: 615
Content-Length: 615
< Last-Modified: Wed, 16 Apr 2025 12:01:11 GMT
Last-Modified: Wed, 16 Apr 2025 12:01:11 GMT
< Connection: keep-alive
Connection: keep-alive
< ETag: "67ff9c07-267"
ETag: "67ff9c07-267"
< Accept-Ranges: bytes
Accept-Ranges: bytes
<
* Connection #0 to host 172.18.255.101 left intact
|
6. 외부 컨테이너에서 east nginx 서비스 접근 확인
1
| docker exec -it mypc curl -s $ENIP
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
|
1
| docker exec -it mypc curl -s $ENIP -v -I
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| * Trying 172.18.255.201:80...
* Connected to 172.18.255.201 (172.18.255.201) port 80
> HEAD / HTTP/1.1
> Host: 172.18.255.201
> User-Agent: curl/8.7.1
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
HTTP/1.1 200 OK
< Server: nginx/1.27.5
Server: nginx/1.27.5
< Date: Sat, 24 May 2025 11:36:45 GMT
Date: Sat, 24 May 2025 11:36:45 GMT
< Content-Type: text/html
Content-Type: text/html
< Content-Length: 615
Content-Length: 615
< Last-Modified: Wed, 16 Apr 2025 12:01:11 GMT
Last-Modified: Wed, 16 Apr 2025 12:01:11 GMT
< Connection: keep-alive
Connection: keep-alive
< ETag: "67ff9c07-267"
ETag: "67ff9c07-267"
< Accept-Ranges: bytes
Accept-Ranges: bytes
<
* Connection #0 to host 172.18.255.201 left intact
|
7. nginx 테스트 리소스 삭제
1
2
| kubectl delete deploy,svc --all --kubeconfig=./west-kubeconfig
kubectl delete deploy,svc --all --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
| deployment.apps "nginx" deleted
service "kubernetes" deleted
service "nginx-service" deleted
deployment.apps "nginx" deleted
service "kubernetes" deleted
service "nginx-service" deleted
|
8. kubectl 및 istioctl alias 설정
1
2
3
4
5
| alias kwest='kubectl --kubeconfig=./west-kubeconfig'
alias keast='kubectl --kubeconfig=./east-kubeconfig'
alias iwest='docker exec -it west-control-plane istioctl'
alias ieast='docker exec -it east-control-plane istioctl'
|
9. alias로 노드 상태 확인
1
2
| kwest get node
keast get node
|
✅ 출력
1
2
3
4
| NAME STATUS ROLES AGE VERSION
west-control-plane Ready control-plane,master 34m v1.23.17
NAME STATUS ROLES AGE VERSION
east-control-plane Ready control-plane,master 28m v1.23.17
|
🔐 플러그인 CA 인증서 설정하기
1. CA 인증서 디렉터리 구조 확인
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
| ch12/certs
├── east-cluster
│ ├── ca-cert.pem
│ ├── ca-key.pem
│ └── cert-chain.pem
├── root-ca.key
├── root-cert.pem
└── west-cluster
├── ca-cert.pem
├── ca-key.pem
└── cert-chain.pem
3 directories, 8 files
|
2. 루트 CA 인증서 상세 정보 확인
1
| openssl x509 -in ch12/certs/root-cert.pem -noout -text
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
| Certificate:
Data:
Version: 3 (0x2)
Serial Number:
4b:e8:d2:7d:f6:57:ee:2b:68:86:3c:ab:6a:eb:5c:cc
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=root.istio.in.action
Validity
Not Before: Jun 28 14:11:35 2022 GMT
Not After : Jun 25 14:11:35 2032 GMT
Subject: CN=root.istio.in.action
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b0:10:9e:72:c4:db:8c:e6:9f:5a:57:de:42:6d:
54:31:ab:46:42:f6:5f:40:81:d3:84:ac:f8:fc:dc:
36:ce:db:a4:68:01:42:71:da:0f:a2:17:c5:04:4b:
78:68:b8:9a:ea:48:ec:43:08:e2:8d:94:77:37:b5:
c5:ea:6a:60:cd:a5:e1:23:36:56:93:d4:40:ba:92:
f2:b6:b8:58:80:ed:23:5c:4c:86:e3:b9:f1:10:e0:
44:ae:84:2c:9d:af:43:68:9d:81:af:4d:ae:62:cf:
46:76:16:4a:e2:c3:2b:ff:c4:12:99:cf:06:3a:46:
ea:85:a4:d3:5b:5a:19:4c:87:0f:8d:2b:1a:78:8d:
1a:fe:00:f8:c7:57:01:91:01:0f:3e:6e:de:80:41:
27:16:40:32:b8:42:22:fd:22:02:53:7a:e7:fd:f3:
2a:9c:44:a6:f0:ca:e0:8d:ba:07:95:46:1e:f7:8d:
71:c9:59:44:02:52:df:1b:fd:3e:e6:d0:80:c3:20:
87:48:23:ae:53:c0:32:57:fd:46:01:07:a2:fd:4d:
e6:c2:34:1f:b1:cf:49:a4:b1:a9:d5:44:c4:96:ae:
e2:1c:73:03:5e:82:66:61:05:d7:96:78:87:5a:27:
c4:da:69:56:84:83:8c:a9:ca:52:78:c0:2a:d8:b9:
00:95
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:1
X509v3 Subject Key Identifier:
0F:46:FF:6F:FA:67:00:A3:6D:41:94:45:39:BA:38:D1:B7:E3:8D:E3
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
30:0f:be:ab:33:a9:4c:39:62:f8:fb:36:fa:aa:a9:15:6d:19:
4b:82:21:d7:45:ce:2b:b6:18:7f:94:7e:de:30:90:0b:b3:be:
a7:57:26:8e:d7:bb:7c:8f:90:69:dc:d8:51:02:71:ab:f5:c1:
cc:db:68:fa:50:e2:7f:b8:24:f9:bd:d3:c8:a5:ce:4b:9b:d4:
68:fb:9c:a6:bf:d4:68:c4:81:79:2c:f8:75:bb:3a:27:4d:9c:
9c:26:ab:63:d8:8b:62:25:10:c8:d7:db:0b:fd:45:da:cb:c0:
09:ca:65:d3:31:ed:eb:8e:2f:a4:11:90:d1:c6:6f:a6:af:46:
44:9d:0e:ad:fe:6a:43:8a:64:51:08:83:d0:64:23:6e:fc:48:
0a:2f:87:e2:b9:cd:22:29:09:6d:e7:57:3a:b8:95:c6:f4:c8:
fa:0a:a9:81:f6:4b:0f:8c:a8:eb:15:a6:7a:a2:fc:81:d0:f3:
df:d1:c5:4d:d3:0b:62:84:fa:7e:03:dd:f4:6d:0c:0a:4d:1d:
b6:e6:8b:b5:97:ac:cf:a9:1b:80:fe:06:e9:36:15:41:07:25:
5a:6e:d7:a0:a1:d8:ad:af:a5:1c:e9:92:58:aa:7a:cf:93:ff:
91:3d:da:e6:3d:a1:be:cc:06:0b:7a:d6:0e:15:67:fa:7c:f9:
13:09:59:8c
|
3. east 클러스터 CA 인증서 검증
1
| openssl x509 -in ch12/certs/east-cluster/ca-cert.pem -noout -text
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
| Certificate:
Data:
Version: 3 (0x2)
Serial Number:
3f:c6:33:9a:95:cc:4c:7d:b3:6f:a9:4b:7f:d6:24:60
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=root.istio.in.action
Validity
Not Before: Jun 28 14:11:35 2022 GMT
Not After : Jun 25 14:11:35 2032 GMT
Subject: CN=east.intermediate.istio.in.action
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:af:88:9d:88:aa:cf:eb:da:15:75:83:b2:25:0b:
c1:6d:7e:0e:cd:06:49:fd:0c:51:19:88:03:06:47:
dc:a0:f7:28:b3:28:16:93:b3:72:8e:d0:56:e0:a4:
29:f8:4d:44:f4:3a:bb:f0:3e:18:8f:07:89:29:59:
0e:be:17:ff:f0:6f:b2:40:20:89:a9:3d:a6:8b:9c:
6b:b7:b5:a2:d0:48:2c:4e:c5:4b:10:9f:09:cf:48:
51:97:15:08:36:2d:aa:8a:24:aa:73:cc:ce:f6:8a:
fd:d3:41:b2:d1:13:15:84:39:58:6d:d3:cd:44:cf:
c6:0f:0b:cc:45:27:d4:66:24:71:54:13:34:63:ea:
0c:85:07:00:0f:02:59:94:aa:97:1f:b6:f6:2d:87:
eb:26:b9:5c:a6:7f:6d:ec:7b:22:ae:77:0d:42:81:
7c:0c:52:5d:17:38:55:86:6d:ab:6f:c6:02:de:8b:
1e:17:15:23:1b:6d:75:bd:09:24:15:94:04:d9:e9:
be:ee:a8:6a:c9:cf:61:36:a5:63:07:be:e2:1a:c6:
d0:c2:29:ec:e9:2a:35:0c:90:01:b9:77:ba:99:0a:
d4:d7:98:de:c9:32:ca:e2:0c:f8:56:0b:34:82:18:
8b:0a:a9:43:05:9b:7b:63:69:29:84:dd:9e:05:2c:
df:01
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Subject Key Identifier:
1A:0F:88:C9:F1:CE:73:D7:70:52:66:28:76:CD:88:32:13:6E:D9:5A
X509v3 Authority Key Identifier:
0F:46:FF:6F:FA:67:00:A3:6D:41:94:45:39:BA:38:D1:B7:E3:8D:E3
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
7e:67:ae:8b:13:cd:43:72:d0:5e:ea:e2:9d:08:7d:51:5f:79:
f4:5c:2a:1e:4f:63:5c:e7:82:85:1f:cb:68:f2:70:c5:45:e3:
0b:76:0e:58:fb:a2:19:81:b0:8c:d2:b1:b8:5b:c2:6d:cb:a1:
88:e5:01:2a:5e:86:62:ea:16:65:8e:12:57:16:aa:2e:b3:42:
f8:85:96:5a:58:f9:ab:f5:1b:45:df:0d:9f:2b:96:05:50:37:
9d:a2:aa:7b:07:36:46:98:97:92:0a:a5:a1:e8:fe:59:fe:92:
b6:5d:db:79:3c:15:81:99:1f:33:e0:4c:d9:57:c8:20:63:27:
d0:1e:88:a1:89:7f:18:bd:7c:c8:74:17:8b:fa:1a:8e:9b:4a:
d8:a4:b0:29:4b:16:7c:6d:39:2e:9c:db:16:e1:fc:38:44:c5:
04:7d:58:d9:60:69:92:3e:95:8a:b4:f5:f4:ce:8d:f4:bb:b6:
dd:a9:0d:6e:96:ab:40:8a:38:ac:e5:3d:57:9a:ca:08:dd:2b:
ac:9a:20:54:ac:dc:53:61:e3:6d:e8:12:d8:9f:52:12:db:d8:
b1:6d:b1:72:f7:98:09:18:f3:1b:cc:d0:48:b7:49:7f:75:d4:
cb:9c:1a:4d:2d:9b:cf:96:9f:d6:a0:23:e4:a8:20:5e:24:e6:
66:01:1c:52
|
4. east 클러스터 인증서 체인 검증
1
| openssl x509 -in ch12/certs/east-cluster/cert-chain.pem -noout -text
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
| Certificate:
Data:
Version: 3 (0x2)
Serial Number:
3f:c6:33:9a:95:cc:4c:7d:b3:6f:a9:4b:7f:d6:24:60
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=root.istio.in.action
Validity
Not Before: Jun 28 14:11:35 2022 GMT
Not After : Jun 25 14:11:35 2032 GMT
Subject: CN=east.intermediate.istio.in.action
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:af:88:9d:88:aa:cf:eb:da:15:75:83:b2:25:0b:
c1:6d:7e:0e:cd:06:49:fd:0c:51:19:88:03:06:47:
dc:a0:f7:28:b3:28:16:93:b3:72:8e:d0:56:e0:a4:
29:f8:4d:44:f4:3a:bb:f0:3e:18:8f:07:89:29:59:
0e:be:17:ff:f0:6f:b2:40:20:89:a9:3d:a6:8b:9c:
6b:b7:b5:a2:d0:48:2c:4e:c5:4b:10:9f:09:cf:48:
51:97:15:08:36:2d:aa:8a:24:aa:73:cc:ce:f6:8a:
fd:d3:41:b2:d1:13:15:84:39:58:6d:d3:cd:44:cf:
c6:0f:0b:cc:45:27:d4:66:24:71:54:13:34:63:ea:
0c:85:07:00:0f:02:59:94:aa:97:1f:b6:f6:2d:87:
eb:26:b9:5c:a6:7f:6d:ec:7b:22:ae:77:0d:42:81:
7c:0c:52:5d:17:38:55:86:6d:ab:6f:c6:02:de:8b:
1e:17:15:23:1b:6d:75:bd:09:24:15:94:04:d9:e9:
be:ee:a8:6a:c9:cf:61:36:a5:63:07:be:e2:1a:c6:
d0:c2:29:ec:e9:2a:35:0c:90:01:b9:77:ba:99:0a:
d4:d7:98:de:c9:32:ca:e2:0c:f8:56:0b:34:82:18:
8b:0a:a9:43:05:9b:7b:63:69:29:84:dd:9e:05:2c:
df:01
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Subject Key Identifier:
1A:0F:88:C9:F1:CE:73:D7:70:52:66:28:76:CD:88:32:13:6E:D9:5A
X509v3 Authority Key Identifier:
0F:46:FF:6F:FA:67:00:A3:6D:41:94:45:39:BA:38:D1:B7:E3:8D:E3
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
7e:67:ae:8b:13:cd:43:72:d0:5e:ea:e2:9d:08:7d:51:5f:79:
f4:5c:2a:1e:4f:63:5c:e7:82:85:1f:cb:68:f2:70:c5:45:e3:
0b:76:0e:58:fb:a2:19:81:b0:8c:d2:b1:b8:5b:c2:6d:cb:a1:
88:e5:01:2a:5e:86:62:ea:16:65:8e:12:57:16:aa:2e:b3:42:
f8:85:96:5a:58:f9:ab:f5:1b:45:df:0d:9f:2b:96:05:50:37:
9d:a2:aa:7b:07:36:46:98:97:92:0a:a5:a1:e8:fe:59:fe:92:
b6:5d:db:79:3c:15:81:99:1f:33:e0:4c:d9:57:c8:20:63:27:
d0:1e:88:a1:89:7f:18:bd:7c:c8:74:17:8b:fa:1a:8e:9b:4a:
d8:a4:b0:29:4b:16:7c:6d:39:2e:9c:db:16:e1:fc:38:44:c5:
04:7d:58:d9:60:69:92:3e:95:8a:b4:f5:f4:ce:8d:f4:bb:b6:
dd:a9:0d:6e:96:ab:40:8a:38:ac:e5:3d:57:9a:ca:08:dd:2b:
ac:9a:20:54:ac:dc:53:61:e3:6d:e8:12:d8:9f:52:12:db:d8:
b1:6d:b1:72:f7:98:09:18:f3:1b:cc:d0:48:b7:49:7f:75:d4:
cb:9c:1a:4d:2d:9b:cf:96:9f:d6:a0:23:e4:a8:20:5e:24:e6:
66:01:1c:52
|
5. west 클러스터 CA 인증서 검증
1
| openssl x509 -in ch12/certs/west-cluster/ca-cert.pem -noout -text
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
| Certificate:
Data:
Version: 3 (0x2)
Serial Number:
c9:09:db:7b:28:b6:9a:a2:89:6a:6c:fb:7f:03:7f:f6
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=root.istio.in.action
Validity
Not Before: Jun 28 14:11:35 2022 GMT
Not After : Jun 25 14:11:35 2032 GMT
Subject: CN=west.intermediate.istio.in.action
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b7:a2:8e:6d:ff:f2:9d:34:3b:e7:b2:85:ed:d9:
57:72:28:49:03:ce:39:df:c7:a8:df:14:71:a8:10:
01:ad:78:77:b4:81:ad:72:ad:fd:54:f3:97:cf:23:
8d:b9:4a:c5:c3:ec:a7:ff:91:b1:b7:6a:b2:20:e7:
89:3f:c3:70:1e:91:78:09:cc:d4:33:ae:e9:70:d1:
db:71:77:24:b7:b5:bb:2e:21:04:a5:b5:30:b7:fc:
bc:6d:93:cf:45:8d:8d:f8:f5:2e:ae:ae:8f:99:36:
78:57:15:86:0f:44:e0:78:6e:93:cf:b5:90:80:1d:
44:61:13:6e:4f:b0:0f:eb:93:d1:52:56:59:d6:1d:
71:4b:6d:79:01:7b:88:58:63:2e:10:89:39:db:31:
01:e2:34:ac:21:90:6a:8b:7d:75:4f:6c:31:a4:83:
26:cb:4f:58:67:9d:56:62:bf:0e:d6:6a:47:c5:e9:
3b:1b:b1:fe:a1:27:f1:58:0d:20:8e:d2:77:6d:62:
ca:b3:2d:bf:c2:54:72:c9:34:8c:b9:40:9d:48:d7:
32:a7:a2:e2:32:ab:b9:fe:cf:cf:40:9e:4d:bd:14:
52:2d:97:f5:11:43:f3:ec:05:49:d8:aa:46:d7:36:
40:ca:e9:24:30:f7:4a:49:89:2a:40:5c:b5:a3:3e:
c4:b5
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Subject Key Identifier:
D3:83:9A:3A:51:D9:03:62:35:8F:6A:A4:DA:99:88:BB:74:70:4F:33
X509v3 Authority Key Identifier:
0F:46:FF:6F:FA:67:00:A3:6D:41:94:45:39:BA:38:D1:B7:E3:8D:E3
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
66:87:f6:ab:52:c3:3e:47:6e:b5:08:04:b3:da:36:91:83:66:
37:6d:02:1f:17:c6:ce:b4:59:51:c4:7b:b7:7c:c9:c4:2b:c5:
9b:b5:3e:ef:05:8b:94:42:4d:bc:ee:11:5e:00:5f:ad:fc:6f:
fb:c7:42:ef:47:f0:d3:70:bd:26:5c:15:33:b8:bf:d7:43:4f:
ca:27:93:8c:80:c8:56:4f:23:b0:da:1f:9d:f7:f3:84:e2:c6:
21:07:46:99:e0:06:d7:a4:bb:1f:7a:8c:3d:9c:7a:78:27:e6:
90:cf:6c:31:0a:ad:20:9a:04:bf:f7:72:8c:8d:43:85:57:0e:
b4:2b:36:c3:b4:d2:8e:b1:d4:4c:e0:c9:20:46:74:c1:77:40:
70:bc:9b:aa:1d:05:43:89:fb:14:d1:75:3d:7b:17:05:9b:3b:
8b:c1:60:d2:cb:2d:9f:f0:14:58:aa:10:0c:dd:e6:10:5e:35:
1f:04:29:79:5e:c2:07:6f:8d:9b:42:1b:ba:c4:a3:88:ce:8a:
47:be:f1:a2:0b:25:a1:d6:d0:c3:84:10:1b:ec:39:1d:03:b0:
31:ad:64:f1:64:c2:36:ba:65:c5:db:27:69:02:63:76:a5:30:
09:d8:b1:89:ca:b6:0d:e1:ee:4a:4c:f8:73:29:00:23:f3:56:
73:67:19:23
|
6. west 클러스터 인증서 체인 검증
1
| openssl x509 -in ch12/certs/west-cluster/cert-chain.pem -noout -text
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
| Certificate:
Data:
Version: 3 (0x2)
Serial Number:
c9:09:db:7b:28:b6:9a:a2:89:6a:6c:fb:7f:03:7f:f6
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=root.istio.in.action
Validity
Not Before: Jun 28 14:11:35 2022 GMT
Not After : Jun 25 14:11:35 2032 GMT
Subject: CN=west.intermediate.istio.in.action
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:b7:a2:8e:6d:ff:f2:9d:34:3b:e7:b2:85:ed:d9:
57:72:28:49:03:ce:39:df:c7:a8:df:14:71:a8:10:
01:ad:78:77:b4:81:ad:72:ad:fd:54:f3:97:cf:23:
8d:b9:4a:c5:c3:ec:a7:ff:91:b1:b7:6a:b2:20:e7:
89:3f:c3:70:1e:91:78:09:cc:d4:33:ae:e9:70:d1:
db:71:77:24:b7:b5:bb:2e:21:04:a5:b5:30:b7:fc:
bc:6d:93:cf:45:8d:8d:f8:f5:2e:ae:ae:8f:99:36:
78:57:15:86:0f:44:e0:78:6e:93:cf:b5:90:80:1d:
44:61:13:6e:4f:b0:0f:eb:93:d1:52:56:59:d6:1d:
71:4b:6d:79:01:7b:88:58:63:2e:10:89:39:db:31:
01:e2:34:ac:21:90:6a:8b:7d:75:4f:6c:31:a4:83:
26:cb:4f:58:67:9d:56:62:bf:0e:d6:6a:47:c5:e9:
3b:1b:b1:fe:a1:27:f1:58:0d:20:8e:d2:77:6d:62:
ca:b3:2d:bf:c2:54:72:c9:34:8c:b9:40:9d:48:d7:
32:a7:a2:e2:32:ab:b9:fe:cf:cf:40:9e:4d:bd:14:
52:2d:97:f5:11:43:f3:ec:05:49:d8:aa:46:d7:36:
40:ca:e9:24:30:f7:4a:49:89:2a:40:5c:b5:a3:3e:
c4:b5
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Subject Key Identifier:
D3:83:9A:3A:51:D9:03:62:35:8F:6A:A4:DA:99:88:BB:74:70:4F:33
X509v3 Authority Key Identifier:
0F:46:FF:6F:FA:67:00:A3:6D:41:94:45:39:BA:38:D1:B7:E3:8D:E3
Signature Algorithm: sha256WithRSAEncryption
Signature Value:
66:87:f6:ab:52:c3:3e:47:6e:b5:08:04:b3:da:36:91:83:66:
37:6d:02:1f:17:c6:ce:b4:59:51:c4:7b:b7:7c:c9:c4:2b:c5:
9b:b5:3e:ef:05:8b:94:42:4d:bc:ee:11:5e:00:5f:ad:fc:6f:
fb:c7:42:ef:47:f0:d3:70:bd:26:5c:15:33:b8:bf:d7:43:4f:
ca:27:93:8c:80:c8:56:4f:23:b0:da:1f:9d:f7:f3:84:e2:c6:
21:07:46:99:e0:06:d7:a4:bb:1f:7a:8c:3d:9c:7a:78:27:e6:
90:cf:6c:31:0a:ad:20:9a:04:bf:f7:72:8c:8d:43:85:57:0e:
b4:2b:36:c3:b4:d2:8e:b1:d4:4c:e0:c9:20:46:74:c1:77:40:
70:bc:9b:aa:1d:05:43:89:fb:14:d1:75:3d:7b:17:05:9b:3b:
8b:c1:60:d2:cb:2d:9f:f0:14:58:aa:10:0c:dd:e6:10:5e:35:
1f:04:29:79:5e:c2:07:6f:8d:9b:42:1b:ba:c4:a3:88:ce:8a:
47:be:f1:a2:0b:25:a1:d6:d0:c3:84:10:1b:ec:39:1d:03:b0:
31:ad:64:f1:64:c2:36:ba:65:c5:db:27:69:02:63:76:a5:30:
09:d8:b1:89:ca:b6:0d:e1:ee:4a:4c:f8:73:29:00:23:f3:56:
73:67:19:23
|
7. istio-system 네임스페이스 및 인증서 시크릿 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| # west-cluster용 인증서 설정하기
kwest create namespace istio-system
kwest create secret generic cacerts -n istio-system \
--from-file=ch12/certs/west-cluster/ca-cert.pem \
--from-file=ch12/certs/west-cluster/ca-key.pem \
--from-file=ch12/certs/root-cert.pem \
--from-file=ch12/certs/west-cluster/cert-chain.pem
# east-cluster용 인증서 설정하기
keast create namespace istio-system
keast create secret generic cacerts -n istio-system \
--from-file=ch12/certs/east-cluster/ca-cert.pem \
--from-file=ch12/certs/east-cluster/ca-key.pem \
--from-file=ch12/certs/root-cert.pem \
--from-file=ch12/certs/east-cluster/cert-chain.pem
|
✅ 출력
1
2
3
4
| namespace/istio-system created
secret/cacerts created
namespace/istio-system created
secret/cacerts created
|
8. 클러스터에 시크릿 생성 완료 확인
(1) istio-system 네임스페이스 존재 확인
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get ns istio-system --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
| >> k8s cluster : west <<
NAME STATUS AGE
istio-system Active 48s
>> k8s cluster : east <<
NAME STATUS AGE
istio-system Active 49s
|
(2) cacerts 시크릿 존재 및 데이터 확인
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get secret cacerts -n istio-system --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
| >> k8s cluster : west <<
NAME TYPE DATA AGE
cacerts Opaque 4 70s
>> k8s cluster : east <<
NAME TYPE DATA AGE
cacerts Opaque 4 70s
|
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl view-secret cacerts -n istio-system --all --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
|
>> k8s cluster : west <<
ca-cert.pem='-----BEGIN CERTIFICATE-----
MIIDPDCCAiSgAwIBAgIRAMkJ23sotpqiiWps+38Df/YwDQYJKoZIhvcNAQELBQAw
HzEdMBsGA1UEAxMUcm9vdC5pc3Rpby5pbi5hY3Rpb24wHhcNMjIwNjI4MTQxMTM1
WhcNMzIwNjI1MTQxMTM1WjAsMSowKAYDVQQDEyF3ZXN0LmludGVybWVkaWF0ZS5p
c3Rpby5pbi5hY3Rpb24wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC3
oo5t//KdNDvnsoXt2VdyKEkDzjnfx6jfFHGoEAGteHe0ga1yrf1U85fPI425SsXD
7Kf/kbG3arIg54k/w3AekXgJzNQzrulw0dtxdyS3tbsuIQSltTC3/Lxtk89FjY34
9S6uro+ZNnhXFYYPROB4bpPPtZCAHURhE25PsA/rk9FSVlnWHXFLbXkBe4hYYy4Q
iTnbMQHiNKwhkGqLfXVPbDGkgybLT1hnnVZivw7WakfF6Tsbsf6hJ/FYDSCO0ndt
YsqzLb/CVHLJNIy5QJ1I1zKnouIyq7n+z89Ank29FFItl/URQ/PsBUnYqkbXNkDK
6SQw90pJiSpAXLWjPsS1AgMBAAGjZjBkMA4GA1UdDwEB/wQEAwIBBjASBgNVHRMB
Af8ECDAGAQH/AgEAMB0GA1UdDgQWBBTTg5o6UdkDYjWPaqTamYi7dHBPMzAfBgNV
HSMEGDAWgBQPRv9v+mcAo21BlEU5ujjRt+ON4zANBgkqhkiG9w0BAQsFAAOCAQEA
Zof2q1LDPkdutQgEs9o2kYNmN20CHxfGzrRZUcR7t3zJxCvFm7U+7wWLlEJNvO4R
XgBfrfxv+8dC70fw03C9JlwVM7i/10NPyieTjIDIVk8jsNofnffzhOLGIQdGmeAG
16S7H3qMPZx6eCfmkM9sMQqtIJoEv/dyjI1DhVcOtCs2w7TSjrHUTODJIEZ0wXdA
cLybqh0FQ4n7FNF1PXsXBZs7i8Fg0sstn/AUWKoQDN3mEF41HwQpeV7CB2+Nm0Ib
usSjiM6KR77xogslodbQw4QQG+w5HQOwMa1k8WTCNrplxdsnaQJjdqUwCdixicq2
DeHuSkz4cykAI/NWc2cZIw==
-----END CERTIFICATE-----'
ca-key.pem='-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAt6KObf/ynTQ757KF7dlXcihJA84538eo3xRxqBABrXh3tIGt
cq39VPOXzyONuUrFw+yn/5Gxt2qyIOeJP8NwHpF4CczUM67pcNHbcXckt7W7LiEE
pbUwt/y8bZPPRY2N+PUurq6PmTZ4VxWGD0TgeG6Tz7WQgB1EYRNuT7AP65PRUlZZ
1h1xS215AXuIWGMuEIk52zEB4jSsIZBqi311T2wxpIMmy09YZ51WYr8O1mpHxek7
G7H+oSfxWA0gjtJ3bWLKsy2/wlRyyTSMuUCdSNcyp6LiMqu5/s/PQJ5NvRRSLZf1
EUPz7AVJ2KpG1zZAyukkMPdKSYkqQFy1oz7EtQIDAQABAoIBACrU2Y/CoR4VrttO
AnsFtKXFy7H9ifYuJa9Sn2fpw9poPNN3Y7NZ7brAzmncCxRq4lHegxjTLLZxRnby
Skr7FM2sdGkkw2ICrCRKbnq6pW/MDYqm3OShrGldo72TOkcoyzKETY0k3g2IbO0y
8f/hutGcSRGrcbbQHMDfvV0M3cm+XTWUBRkgDlBIGGo632PEXSj0Qr7v4LGN0Px6
YN6N91InuEI8X60pyeLBF9NDIYjeV7Q1Ku8ByMSgZcMRfpJMYV/3Xu9JD9U5INVt
/pWnDwwjogoFOIuGUVcFMFrcWbdLE1kgD4jD/g6pdmKhbiD7RdnfcgragIjtnv9+
egWra4ECgYEAypCOHrcmJbMLnbyWjWGxgFtC56Ob2OVjNu54JJq0SSECarH2MzQN
qG5MoxHRmIb/ETqKgas/KGs2kWqE+Cc0cvpu5BAvFLY1WhazAESezA3X9zR4DnZL
AyZHa28YLjWlqXtA0XDnevZBnusE+2zAodeIIv48Ly2I8OuDF6gQvKUCgYEA6BOn
9tbu3TDpB4stov7wGN57ncLX2q+9BFnb3BTpoYtxrMnxxaTUtilL986M2Z89HWF0
G75HOv1Ip8hupBIW3ynjaAyaiKS9oD2yN1n57h3HOeGlLHv8jPR98zVcHHQXsiwa
gLHAveomU1aN3nv0JmJTPWIVUT8RNP3wq2j8GtECgYEArSu1hAa5IwOVC61827NI
Bt5+LP9Orbc1AXIO3eQv+lCw+zvWqWF3x6U7+TCziXznM/hjDoWywcAeb2Sr9mW1
zhHQmUJIraEzrSe4saL4SqQPHDQL6vkwGaow5mScPGz6ihBnkmW+Tv2VjeGHadZI
PFPA+4FzPDXmW2hLsv6oCE0CgYEAkX/BToByQTro3lHjys0KuozB86a0reaAGro7
nT9/OkiyfCIf8knlEk/R0QsuQ0ISjtkKclpZTiJ96rM+qp6suD0K1bERMZoXSN9l
XE6M4zzIKwHNDJavP7AJRvGtTil6sbn047qNnIOwg49AYrxT1bzPcyyLMOTZZN/Q
g6bOaAECgYEAjdTi0pD1XV1qOSTvpt7g7SOPpHW7++rLDjhbLvUyItIk1VFSIQ51
u42q2Mw5RZ7iOccg+IuO3K6aZ0RYkHgk3BTr4QXF3FtB1ILNETf74bHpCZPjCQWV
Y6NekYS6YnKQVh251quBOp/5/HEC12idK8u5l2GOU7DI+Ykqmb3MrNI=
-----END RSA PRIVATE KEY-----'
cert-chain.pem='-----BEGIN CERTIFICATE-----
MIIDPDCCAiSgAwIBAgIRAMkJ23sotpqiiWps+38Df/YwDQYJKoZIhvcNAQELBQAw
HzEdMBsGA1UEAxMUcm9vdC5pc3Rpby5pbi5hY3Rpb24wHhcNMjIwNjI4MTQxMTM1
WhcNMzIwNjI1MTQxMTM1WjAsMSowKAYDVQQDEyF3ZXN0LmludGVybWVkaWF0ZS5p
c3Rpby5pbi5hY3Rpb24wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQC3
oo5t//KdNDvnsoXt2VdyKEkDzjnfx6jfFHGoEAGteHe0ga1yrf1U85fPI425SsXD
7Kf/kbG3arIg54k/w3AekXgJzNQzrulw0dtxdyS3tbsuIQSltTC3/Lxtk89FjY34
9S6uro+ZNnhXFYYPROB4bpPPtZCAHURhE25PsA/rk9FSVlnWHXFLbXkBe4hYYy4Q
iTnbMQHiNKwhkGqLfXVPbDGkgybLT1hnnVZivw7WakfF6Tsbsf6hJ/FYDSCO0ndt
YsqzLb/CVHLJNIy5QJ1I1zKnouIyq7n+z89Ank29FFItl/URQ/PsBUnYqkbXNkDK
6SQw90pJiSpAXLWjPsS1AgMBAAGjZjBkMA4GA1UdDwEB/wQEAwIBBjASBgNVHRMB
Af8ECDAGAQH/AgEAMB0GA1UdDgQWBBTTg5o6UdkDYjWPaqTamYi7dHBPMzAfBgNV
HSMEGDAWgBQPRv9v+mcAo21BlEU5ujjRt+ON4zANBgkqhkiG9w0BAQsFAAOCAQEA
Zof2q1LDPkdutQgEs9o2kYNmN20CHxfGzrRZUcR7t3zJxCvFm7U+7wWLlEJNvO4R
XgBfrfxv+8dC70fw03C9JlwVM7i/10NPyieTjIDIVk8jsNofnffzhOLGIQdGmeAG
16S7H3qMPZx6eCfmkM9sMQqtIJoEv/dyjI1DhVcOtCs2w7TSjrHUTODJIEZ0wXdA
cLybqh0FQ4n7FNF1PXsXBZs7i8Fg0sstn/AUWKoQDN3mEF41HwQpeV7CB2+Nm0Ib
usSjiM6KR77xogslodbQw4QQG+w5HQOwMa1k8WTCNrplxdsnaQJjdqUwCdixicq2
DeHuSkz4cykAI/NWc2cZIw==
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIDDTCCAfWgAwIBAgIQS+jSffZX7itohjyrautczDANBgkqhkiG9w0BAQsFADAf
MR0wGwYDVQQDExRyb290LmlzdGlvLmluLmFjdGlvbjAeFw0yMjA2MjgxNDExMzVa
Fw0zMjA2MjUxNDExMzVaMB8xHTAbBgNVBAMTFHJvb3QuaXN0aW8uaW4uYWN0aW9u
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsBCecsTbjOafWlfeQm1U
MatGQvZfQIHThKz4/Nw2ztukaAFCcdoPohfFBEt4aLia6kjsQwjijZR3N7XF6mpg
zaXhIzZWk9RAupLytrhYgO0jXEyG47nxEOBEroQsna9DaJ2Br02uYs9GdhZK4sMr
/8QSmc8GOkbqhaTTW1oZTIcPjSsaeI0a/gD4x1cBkQEPPm7egEEnFkAyuEIi/SIC
U3rn/fMqnESm8MrgjboHlUYe941xyVlEAlLfG/0+5tCAwyCHSCOuU8AyV/1GAQei
/U3mwjQfsc9JpLGp1UTElq7iHHMDXoJmYQXXlniHWifE2mlWhIOMqcpSeMAq2LkA
lQIDAQABo0UwQzAOBgNVHQ8BAf8EBAMCAQYwEgYDVR0TAQH/BAgwBgEB/wIBATAd
BgNVHQ4EFgQUD0b/b/pnAKNtQZRFObo40bfjjeMwDQYJKoZIhvcNAQELBQADggEB
ADAPvqszqUw5Yvj7NvqqqRVtGUuCIddFziu2GH+Uft4wkAuzvqdXJo7Xu3yPkGnc
2FECcav1wczbaPpQ4n+4JPm908ilzkub1Gj7nKa/1GjEgXks+HW7OidNnJwmq2PY
i2IlEMjX2wv9RdrLwAnKZdMx7euOL6QRkNHGb6avRkSdDq3+akOKZFEIg9BkI278
SAovh+K5zSIpCW3nVzq4lcb0yPoKqYH2Sw+MqOsVpnqi/IHQ89/RxU3TC2KE+n4D
3fRtDApNHbbmi7WXrM+pG4D+Buk2FUEHJVpu16Ch2K2vpRzpkliqes+T/5E92uY9
ob7MBgt61g4VZ/p8+RMJWYw=
-----END CERTIFICATE-----'
root-cert.pem='-----BEGIN CERTIFICATE-----
MIIDDTCCAfWgAwIBAgIQS+jSffZX7itohjyrautczDANBgkqhkiG9w0BAQsFADAf
MR0wGwYDVQQDExRyb290LmlzdGlvLmluLmFjdGlvbjAeFw0yMjA2MjgxNDExMzVa
Fw0zMjA2MjUxNDExMzVaMB8xHTAbBgNVBAMTFHJvb3QuaXN0aW8uaW4uYWN0aW9u
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsBCecsTbjOafWlfeQm1U
MatGQvZfQIHThKz4/Nw2ztukaAFCcdoPohfFBEt4aLia6kjsQwjijZR3N7XF6mpg
zaXhIzZWk9RAupLytrhYgO0jXEyG47nxEOBEroQsna9DaJ2Br02uYs9GdhZK4sMr
/8QSmc8GOkbqhaTTW1oZTIcPjSsaeI0a/gD4x1cBkQEPPm7egEEnFkAyuEIi/SIC
U3rn/fMqnESm8MrgjboHlUYe941xyVlEAlLfG/0+5tCAwyCHSCOuU8AyV/1GAQei
/U3mwjQfsc9JpLGp1UTElq7iHHMDXoJmYQXXlniHWifE2mlWhIOMqcpSeMAq2LkA
lQIDAQABo0UwQzAOBgNVHQ8BAf8EBAMCAQYwEgYDVR0TAQH/BAgwBgEB/wIBATAd
BgNVHQ4EFgQUD0b/b/pnAKNtQZRFObo40bfjjeMwDQYJKoZIhvcNAQELBQADggEB
ADAPvqszqUw5Yvj7NvqqqRVtGUuCIddFziu2GH+Uft4wkAuzvqdXJo7Xu3yPkGnc
2FECcav1wczbaPpQ4n+4JPm908ilzkub1Gj7nKa/1GjEgXks+HW7OidNnJwmq2PY
i2IlEMjX2wv9RdrLwAnKZdMx7euOL6QRkNHGb6avRkSdDq3+akOKZFEIg9BkI278
SAovh+K5zSIpCW3nVzq4lcb0yPoKqYH2Sw+MqOsVpnqi/IHQ89/RxU3TC2KE+n4D
3fRtDApNHbbmi7WXrM+pG4D+Buk2FUEHJVpu16Ch2K2vpRzpkliqes+T/5E92uY9
ob7MBgt61g4VZ/p8+RMJWYw=
-----END CERTIFICATE-----'
>> k8s cluster : east <<
ca-cert.pem='-----BEGIN CERTIFICATE-----
MIIDOzCCAiOgAwIBAgIQP8YzmpXMTH2zb6lLf9YkYDANBgkqhkiG9w0BAQsFADAf
MR0wGwYDVQQDExRyb290LmlzdGlvLmluLmFjdGlvbjAeFw0yMjA2MjgxNDExMzVa
Fw0zMjA2MjUxNDExMzVaMCwxKjAoBgNVBAMTIWVhc3QuaW50ZXJtZWRpYXRlLmlz
dGlvLmluLmFjdGlvbjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAK+I
nYiqz+vaFXWDsiULwW1+Ds0GSf0MURmIAwZH3KD3KLMoFpOzco7QVuCkKfhNRPQ6
u/A+GI8HiSlZDr4X//BvskAgiak9pouca7e1otBILE7FSxCfCc9IUZcVCDYtqook
qnPMzvaK/dNBstETFYQ5WG3TzUTPxg8LzEUn1GYkcVQTNGPqDIUHAA8CWZSqlx+2
9i2H6ya5XKZ/bex7Iq53DUKBfAxSXRc4VYZtq2/GAt6LHhcVIxttdb0JJBWUBNnp
vu6oasnPYTalYwe+4hrG0MIp7OkqNQyQAbl3upkK1NeY3skyyuIM+FYLNIIYiwqp
QwWbe2NpKYTdngUs3wECAwEAAaNmMGQwDgYDVR0PAQH/BAQDAgEGMBIGA1UdEwEB
/wQIMAYBAf8CAQAwHQYDVR0OBBYEFBoPiMnxznPXcFJmKHbNiDITbtlaMB8GA1Ud
IwQYMBaAFA9G/2/6ZwCjbUGURTm6ONG3443jMA0GCSqGSIb3DQEBCwUAA4IBAQB+
Z66LE81DctBe6uKdCH1RX3n0XCoeT2Nc54KFH8to8nDFReMLdg5Y+6IZgbCM0rG4
W8Jty6GI5QEqXoZi6hZljhJXFqous0L4hZZaWPmr9RtF3w2fK5YFUDedoqp7BzZG
mJeSCqWh6P5Z/pK2Xdt5PBWBmR8z4EzZV8ggYyfQHoihiX8YvXzIdBeL+hqOm0rY
pLApSxZ8bTkunNsW4fw4RMUEfVjZYGmSPpWKtPX0zo30u7bdqQ1ulqtAijis5T1X
msoI3SusmiBUrNxTYeNt6BLYn1IS29ixbbFy95gJGPMbzNBIt0l/ddTLnBpNLZvP
lp/WoCPkqCBeJOZmARxS
-----END CERTIFICATE-----'
ca-key.pem='-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAr4idiKrP69oVdYOyJQvBbX4OzQZJ/QxRGYgDBkfcoPcosygW
k7NyjtBW4KQp+E1E9Dq78D4YjweJKVkOvhf/8G+yQCCJqT2mi5xrt7Wi0EgsTsVL
EJ8Jz0hRlxUINi2qiiSqc8zO9or900Gy0RMVhDlYbdPNRM/GDwvMRSfUZiRxVBM0
Y+oMhQcADwJZlKqXH7b2LYfrJrlcpn9t7HsirncNQoF8DFJdFzhVhm2rb8YC3ose
FxUjG211vQkkFZQE2em+7qhqyc9hNqVjB77iGsbQwins6So1DJABuXe6mQrU15je
yTLK4gz4Vgs0ghiLCqlDBZt7Y2kphN2eBSzfAQIDAQABAoIBACiYqv5xqta8QFxG
UgwZVOnyzo+CVdhNYfBKsZBhTFh58RLGQbp1NRhsfLtFnGNN05W8g7zDT8C8mG9U
poE2Yb4Exy/nlo7qsDr3uT3qpzYOixjIrlywu38SFbSga57EHv4GDtnrUy5X5O5X
8nhCNqa28ImuA3pXp1HRg7O2y3u3rYQ0khMFK2OuLuQB3ONd+9M0neM6/UFhD5JJ
hCpXSSMzzqYpODn4QIjrA84MkrEJqs3pOUhkF6Ga/xMLDRanDEhGKIBxiUw9dsak
8Bk3MPqzGiLxbRdK2z15LCwuQJdc1ZiGH+KzB1lPn7GPTqhAQErVlOQsZrHK0Ds7
w7fr8WUCgYEAwjcPbmbZMZrXg/0ebB+EmbmNuvQ1ZpXWJMhO4O7gK65OZzLMZEc7
eTux2Oe+IN9KXSotDNnRumIrkwVeZqmRK0LhHb1BxtkwflFXOTZJITblGitphJnx
AKZVIiRli6+ZXGI/gQnBLn1ZimTY6z1rhm6UivtzJ+ZWDoy4hLsrWuMCgYEA52Ai
OJw3Ee18edqlzu8HKZ0UWpdMu7jcT6ScTPJVCFrtC/m4DxXU9del9RPT2+D9s7r0
O2cpKWzr3u72Wo20Qy4bNlqyMXbMROfpRHwX9e0efF5hawzl08RIZCl1WP24huj7
YktPdXCGNxSqSQFnrQRtxFtGUyXDIZ+GFNGNj8sCgYBFxjREDK0xNhkBcVmRrM0d
0V0K8puQzHoP4ur7wrZE2y2Nw+FMkY7bYkflznQvKSl1SSbAPC0uEgDnpAEjTv45
laB857aO8w6KAz0b79XcGfW7LieNnSTJf/iL+JmG0sJ9P0rjWBbQVfZqUwrfkMRl
mqrBN89KYWU/euz7uqa70wKBgQDHWOODJMypzJSvpDuxg+4G44iS2MLLBmYC1I+6
GBw9O6H67Gexz5yRSAB7nF6vljTf8pbUy3gCcg7zH63vrSF/tCzL8u6OgY1TXQB0
+fnm8CqQ+vwyMIWfpAC/E51AVDH1Qqy8LqjCRXXN5ScmCWja//LW99EqeGGcCYaL
T1UJawKBgBBTSnZcwXVVv3ib4jRuQByQeGA8o8P2aJtkOgvpmDfJ8q3f5Uti+7vG
qJJCi2P6TYJo06FVy9jRiDVAlbz5VYq6jonNg7Q67U859wqkzEbvcYrVwCmvf+pA
ImBubULYCAv7onV6qHkgnYhwCvEuCbn2KKdhjtS2uiyWiuI311hV
-----END RSA PRIVATE KEY-----'
cert-chain.pem='-----BEGIN CERTIFICATE-----
MIIDOzCCAiOgAwIBAgIQP8YzmpXMTH2zb6lLf9YkYDANBgkqhkiG9w0BAQsFADAf
MR0wGwYDVQQDExRyb290LmlzdGlvLmluLmFjdGlvbjAeFw0yMjA2MjgxNDExMzVa
Fw0zMjA2MjUxNDExMzVaMCwxKjAoBgNVBAMTIWVhc3QuaW50ZXJtZWRpYXRlLmlz
dGlvLmluLmFjdGlvbjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAK+I
nYiqz+vaFXWDsiULwW1+Ds0GSf0MURmIAwZH3KD3KLMoFpOzco7QVuCkKfhNRPQ6
u/A+GI8HiSlZDr4X//BvskAgiak9pouca7e1otBILE7FSxCfCc9IUZcVCDYtqook
qnPMzvaK/dNBstETFYQ5WG3TzUTPxg8LzEUn1GYkcVQTNGPqDIUHAA8CWZSqlx+2
9i2H6ya5XKZ/bex7Iq53DUKBfAxSXRc4VYZtq2/GAt6LHhcVIxttdb0JJBWUBNnp
vu6oasnPYTalYwe+4hrG0MIp7OkqNQyQAbl3upkK1NeY3skyyuIM+FYLNIIYiwqp
QwWbe2NpKYTdngUs3wECAwEAAaNmMGQwDgYDVR0PAQH/BAQDAgEGMBIGA1UdEwEB
/wQIMAYBAf8CAQAwHQYDVR0OBBYEFBoPiMnxznPXcFJmKHbNiDITbtlaMB8GA1Ud
IwQYMBaAFA9G/2/6ZwCjbUGURTm6ONG3443jMA0GCSqGSIb3DQEBCwUAA4IBAQB+
Z66LE81DctBe6uKdCH1RX3n0XCoeT2Nc54KFH8to8nDFReMLdg5Y+6IZgbCM0rG4
W8Jty6GI5QEqXoZi6hZljhJXFqous0L4hZZaWPmr9RtF3w2fK5YFUDedoqp7BzZG
mJeSCqWh6P5Z/pK2Xdt5PBWBmR8z4EzZV8ggYyfQHoihiX8YvXzIdBeL+hqOm0rY
pLApSxZ8bTkunNsW4fw4RMUEfVjZYGmSPpWKtPX0zo30u7bdqQ1ulqtAijis5T1X
msoI3SusmiBUrNxTYeNt6BLYn1IS29ixbbFy95gJGPMbzNBIt0l/ddTLnBpNLZvP
lp/WoCPkqCBeJOZmARxS
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIDDTCCAfWgAwIBAgIQS+jSffZX7itohjyrautczDANBgkqhkiG9w0BAQsFADAf
MR0wGwYDVQQDExRyb290LmlzdGlvLmluLmFjdGlvbjAeFw0yMjA2MjgxNDExMzVa
Fw0zMjA2MjUxNDExMzVaMB8xHTAbBgNVBAMTFHJvb3QuaXN0aW8uaW4uYWN0aW9u
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsBCecsTbjOafWlfeQm1U
MatGQvZfQIHThKz4/Nw2ztukaAFCcdoPohfFBEt4aLia6kjsQwjijZR3N7XF6mpg
zaXhIzZWk9RAupLytrhYgO0jXEyG47nxEOBEroQsna9DaJ2Br02uYs9GdhZK4sMr
/8QSmc8GOkbqhaTTW1oZTIcPjSsaeI0a/gD4x1cBkQEPPm7egEEnFkAyuEIi/SIC
U3rn/fMqnESm8MrgjboHlUYe941xyVlEAlLfG/0+5tCAwyCHSCOuU8AyV/1GAQei
/U3mwjQfsc9JpLGp1UTElq7iHHMDXoJmYQXXlniHWifE2mlWhIOMqcpSeMAq2LkA
lQIDAQABo0UwQzAOBgNVHQ8BAf8EBAMCAQYwEgYDVR0TAQH/BAgwBgEB/wIBATAd
BgNVHQ4EFgQUD0b/b/pnAKNtQZRFObo40bfjjeMwDQYJKoZIhvcNAQELBQADggEB
ADAPvqszqUw5Yvj7NvqqqRVtGUuCIddFziu2GH+Uft4wkAuzvqdXJo7Xu3yPkGnc
2FECcav1wczbaPpQ4n+4JPm908ilzkub1Gj7nKa/1GjEgXks+HW7OidNnJwmq2PY
i2IlEMjX2wv9RdrLwAnKZdMx7euOL6QRkNHGb6avRkSdDq3+akOKZFEIg9BkI278
SAovh+K5zSIpCW3nVzq4lcb0yPoKqYH2Sw+MqOsVpnqi/IHQ89/RxU3TC2KE+n4D
3fRtDApNHbbmi7WXrM+pG4D+Buk2FUEHJVpu16Ch2K2vpRzpkliqes+T/5E92uY9
ob7MBgt61g4VZ/p8+RMJWYw=
-----END CERTIFICATE-----'
root-cert.pem='-----BEGIN CERTIFICATE-----
MIIDDTCCAfWgAwIBAgIQS+jSffZX7itohjyrautczDANBgkqhkiG9w0BAQsFADAf
MR0wGwYDVQQDExRyb290LmlzdGlvLmluLmFjdGlvbjAeFw0yMjA2MjgxNDExMzVa
Fw0zMjA2MjUxNDExMzVaMB8xHTAbBgNVBAMTFHJvb3QuaXN0aW8uaW4uYWN0aW9u
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsBCecsTbjOafWlfeQm1U
MatGQvZfQIHThKz4/Nw2ztukaAFCcdoPohfFBEt4aLia6kjsQwjijZR3N7XF6mpg
zaXhIzZWk9RAupLytrhYgO0jXEyG47nxEOBEroQsna9DaJ2Br02uYs9GdhZK4sMr
/8QSmc8GOkbqhaTTW1oZTIcPjSsaeI0a/gD4x1cBkQEPPm7egEEnFkAyuEIi/SIC
U3rn/fMqnESm8MrgjboHlUYe941xyVlEAlLfG/0+5tCAwyCHSCOuU8AyV/1GAQei
/U3mwjQfsc9JpLGp1UTElq7iHHMDXoJmYQXXlniHWifE2mlWhIOMqcpSeMAq2LkA
lQIDAQABo0UwQzAOBgNVHQ8BAf8EBAMCAQYwEgYDVR0TAQH/BAgwBgEB/wIBATAd
BgNVHQ4EFgQUD0b/b/pnAKNtQZRFObo40bfjjeMwDQYJKoZIhvcNAQELBQADggEB
ADAPvqszqUw5Yvj7NvqqqRVtGUuCIddFziu2GH+Uft4wkAuzvqdXJo7Xu3yPkGnc
2FECcav1wczbaPpQ4n+4JPm908ilzkub1Gj7nKa/1GjEgXks+HW7OidNnJwmq2PY
i2IlEMjX2wv9RdrLwAnKZdMx7euOL6QRkNHGb6avRkSdDq3+akOKZFEIg9BkI278
SAovh+K5zSIpCW3nVzq4lcb0yPoKqYH2Sw+MqOsVpnqi/IHQ89/RxU3TC2KE+n4D
3fRtDApNHbbmi7WXrM+pG4D+Buk2FUEHJVpu16Ch2K2vpRzpkliqes+T/5E92uY9
ob7MBgt61g4VZ/p8+RMJWYw=
-----END CERTIFICATE-----'
|
🔗 클러스터 간 연결을 위해 네트워크에 레이블 붙이기
1. istio-system 네임스페이스에 topology.istio.io/network 레이블 추가
1
2
| kwest label namespace istio-system topology.istio.io/network=west-network
keast label namespace istio-system topology.istio.io/network=east-network
|
✅ 출력
1
2
| namespace/istio-system labeled
namespace/istio-system labeled
|
2. 레이블이 정상적으로 적용됐는지 확인
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get ns istio-system --show-labels --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
| >> k8s cluster : west <<
NAME STATUS AGE LABELS
istio-system Active 5m7s kubernetes.io/metadata.name=istio-system,topology.istio.io/network=west-network
>> k8s cluster : east <<
NAME STATUS AGE LABELS
istio-system Active 5m7s kubernetes.io/metadata.name=istio-system,topology.istio.io/network=east-network
|
⚙️ IstioOperator 리소스를 사용해 컨트롤 플레인 설치하기
1. west 클러스터용 IstioOperator 리소스 확인
1
| cat ./ch12/controlplanes/cluster-west.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| apiVersion: install.istio.io/v1alpha1
metadata:
name: istio-controlplane
namespace: istio-system
kind: IstioOperator
spec:
profile: demo
components:
egressGateways:
- name: istio-egressgateway
enabled: false
values:
global:
meshID: usmesh
multiCluster:
clusterName: west-cluster
network: west-network
|
2. east 클러스터용 IstioOperator 리소스 확인
1
| cat ./ch12/controlplanes/cluster-east.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| apiVersion: install.istio.io/v1alpha1
metadata:
name: istio-controlplane
namespace: istio-system
kind: IstioOperator
spec:
meshConfig:
accessLogFile: /dev/stdout
accessLogEncoding: JSON
values:
global:
meshID: usmesh
multiCluster:
clusterName: east-cluster
network: east-network
|
3. west 클러스터 설정 및 확인
(1) west-control-plane 컨테이너 진입
1
2
3
| docker exec -it west-control-plane bash
root@west-control-plane:/#
|
(2) Istioctl 설치 및 환경변수 설정
1
2
3
4
5
| root@west-control-plane:/# export ISTIOV=1.17.8
echo 'export ISTIOV=1.17.8' >> /root/.bashrc
curl -s -L https://istio.io/downloadIstio | ISTIO_VERSION=$ISTIOV sh -
cp istio-$ISTIOV/bin/istioctl /usr/local/bin/istioctl
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| Downloading istio-1.17.8 from https://github.com/istio/istio/releases/download/1.17.8/istio-1.17.8-linux-amd64.tar.gz ...
Istio 1.17.8 download complete!
The Istio release archive has been downloaded to the istio-1.17.8 directory.
To configure the istioctl client tool for your workstation,
add the /istio-1.17.8/bin directory to your environment path variable with:
export PATH="$PATH:/istio-1.17.8/bin"
Begin the Istio pre-installation check by running:
istioctl x precheck
Try Istio in ambient mode
https://istio.io/latest/docs/ambient/getting-started/
Try Istio in sidecar mode
https://istio.io/latest/docs/setup/getting-started/
Install guides for ambient mode
https://istio.io/latest/docs/ambient/install/
Install guides for sidecar mode
https://istio.io/latest/docs/setup/install/
Need more information? Visit https://istio.io/latest/docs/
|
(3) west-cluster용 IstioOperator 설정 파일 작성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| root@west-control-plane:/# cat << EOF > west-istio.yaml
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
name: istio-controlplane
namespace: istio-system
spec:
profile: demo
components:
egressGateways:
- name: istio-egressgateway
enabled: false
values:
global:
meshID: usmesh
multiCluster:
clusterName: west-cluster
network: west-network
EOF
|
(4) west-cluster에 Istio 컨트롤 플레인 설치
1
| root@west-control-plane:/# istioctl install -f west-istio.yaml --set values.global.proxy.privileged=true -y
|
✅ 출력
1
2
3
4
5
6
| ✔ Istio core installed
✔ Istiod installed
✔ Ingress gateways installed
✔ Installation complete Making this installation the default for injection and validation.
Thank you for installing Istio 1.17. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/hMHGiwZHPU7UQRWe9
|
(5) west-cluster에 Istio observability 도구 설치
1
| root@west-control-plane:/# kubectl apply -f istio-$ISTIOV/samples/addons
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| serviceaccount/grafana created
configmap/grafana created
service/grafana created
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created
|
(6) west-control-plane 컨테이너에서 나가기
1
2
| root@west-control-plane:/# exit
exit
|
(7) west 클러스터 Istio 리소스 확인
1
| kwest get all,svc,ep,sa,cm,secret,pdb -n istio-system
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
| NAME READY STATUS RESTARTS AGE
pod/grafana-b854c6c8-vgwtq 1/1 Running 0 51s
pod/istio-ingressgateway-5db74c978c-7k7tr 1/1 Running 25 (4m47s ago) 103m
pod/istiod-5585445f4c-gphfz 1/1 Running 1 (2m21s ago) 103m
pod/jaeger-5556cd8fcf-fqb7t 1/1 Running 0 51s
pod/kiali-648847c8c4-jvz2z 0/1 Running 0 51s
pod/prometheus-7b8b9dd44c-87xpj 2/2 Running 0 51s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/grafana ClusterIP 10.100.0.152 <none> 3000/TCP 51s
service/istio-ingressgateway LoadBalancer 10.100.0.246 172.18.255.101 15021:30545/TCP,80:32147/TCP,443:31928/TCP,31400:31839/TCP,15443:30833/TCP 103m
service/istiod ClusterIP 10.100.0.4 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP 103m
service/jaeger-collector ClusterIP 10.100.0.124 <none> 14268/TCP,14250/TCP,9411/TCP 51s
service/kiali ClusterIP 10.100.0.122 <none> 20001/TCP,9090/TCP 51s
service/prometheus ClusterIP 10.100.0.48 <none> 9090/TCP 51s
service/tracing ClusterIP 10.100.0.39 <none> 80/TCP,16685/TCP 51s
service/zipkin ClusterIP 10.100.0.69 <none> 9411/TCP 51s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/grafana 1/1 1 1 51s
deployment.apps/istio-ingressgateway 1/1 1 1 103m
deployment.apps/istiod 1/1 1 1 103m
deployment.apps/jaeger 1/1 1 1 51s
deployment.apps/kiali 0/1 1 0 51s
deployment.apps/prometheus 1/1 1 1 51s
NAME DESIRED CURRENT READY AGE
replicaset.apps/grafana-b854c6c8 1 1 1 51s
replicaset.apps/istio-ingressgateway-5db74c978c 1 1 1 103m
replicaset.apps/istiod-5585445f4c 1 1 1 103m
replicaset.apps/jaeger-5556cd8fcf 1 1 1 51s
replicaset.apps/kiali-648847c8c4 1 1 0 51s
replicaset.apps/prometheus-7b8b9dd44c 1 1 1 51s
NAME ENDPOINTS AGE
endpoints/grafana 10.10.0.9:3000 51s
endpoints/istio-ingressgateway 10.10.0.7:15443,10.10.0.7:15021,10.10.0.7:31400 + 2 more... 103m
endpoints/istiod 10.10.0.4:15012,10.10.0.4:15010,10.10.0.4:15017 + 1 more... 103m
endpoints/jaeger-collector 10.10.0.10:9411,10.10.0.10:14250,10.10.0.10:14268 51s
endpoints/kiali 51s
endpoints/prometheus 10.10.0.12:9090 51s
endpoints/tracing 10.10.0.10:16685,10.10.0.10:16686 51s
endpoints/zipkin 10.10.0.10:9411 51s
NAME SECRETS AGE
serviceaccount/default 1 4h21m
serviceaccount/grafana 1 51s
serviceaccount/istio-ingressgateway-service-account 1 103m
serviceaccount/istio-reader-service-account 1 103m
serviceaccount/istiod 1 103m
serviceaccount/istiod-service-account 1 103m
serviceaccount/kiali 1 51s
serviceaccount/prometheus 1 51s
NAME DATA AGE
configmap/grafana 4 51s
configmap/istio 2 103m
configmap/istio-ca-root-cert 1 103m
configmap/istio-gateway-deployment-leader 0 103m
configmap/istio-gateway-status-leader 0 103m
configmap/istio-grafana-dashboards 2 51s
configmap/istio-leader 0 103m
configmap/istio-namespace-controller-election 0 103m
configmap/istio-services-grafana-dashboards 4 51s
configmap/istio-sidecar-injector 2 103m
configmap/kiali 1 51s
configmap/kube-root-ca.crt 1 4h21m
configmap/prometheus 5 51s
NAME TYPE DATA AGE
secret/cacerts Opaque 4 4h21m
secret/default-token-n42mk kubernetes.io/service-account-token 3 4h21m
secret/grafana-token-pn74b kubernetes.io/service-account-token 3 51s
secret/istio-ingressgateway-service-account-token-94z7g kubernetes.io/service-account-token 3 103m
secret/istio-reader-service-account-token-kllhn kubernetes.io/service-account-token 3 103m
secret/istiod-service-account-token-gr2qt kubernetes.io/service-account-token 3 103m
secret/istiod-token-8czdk kubernetes.io/service-account-token 3 103m
secret/kiali-token-vshmr kubernetes.io/service-account-token 3 51s
secret/prometheus-token-7bsqd kubernetes.io/service-account-token 3 51s
NAME MIN AVAILABLE MAX UNAVAILABLE ALLOWED DISRUPTIONS AGE
poddisruptionbudget.policy/istio-ingressgateway 1 N/A 0 103m
poddisruptionbudget.policy/istiod 1 N/A 0 103m
|
(8) west 클러스터 cacerts 인증서/키 확인
1
| kwest get secret -n istio-system cacerts -o json
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| {
"apiVersion": "v1",
"data": {
"ca-cert.pem": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURQRENDQWlTZ0F3SUJBZ0lSQU1rSjIzc290cHFpaVdwcyszOERmL1l3RFFZSktvWklodmNOQVFFTEJRQXcKSHpFZE1Cc0dBMVVFQXhNVWNtOXZkQzVwYzNScGJ5NXBiaTVoWTNScGIyNHdIaGNOTWpJd05qSTRNVFF4TVRNMQpXaGNOTXpJd05qSTFNVFF4TVRNMVdqQXNNU293S0FZRFZRUURFeUYzWlhOMExtbHVkR1Z5YldWa2FXRjBaUzVwCmMzUnBieTVwYmk1aFkzUnBiMjR3Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRQzMKb281dC8vS2RORHZuc29YdDJWZHlLRWtEempuZng2amZGSEdvRUFHdGVIZTBnYTF5cmYxVTg1ZlBJNDI1U3NYRAo3S2Yva2JHM2FySWc1NGsvdzNBZWtYZ0p6TlF6cnVsdzBkdHhkeVMzdGJzdUlRU2x0VEMzL0x4dGs4OUZqWTM0CjlTNnVybytaTm5oWEZZWVBST0I0YnBQUHRaQ0FIVVJoRTI1UHNBL3JrOUZTVmxuV0hYRkxiWGtCZTRoWVl5NFEKaVRuYk1RSGlOS3doa0dxTGZYVlBiREdrZ3liTFQxaG5uVlppdnc3V2FrZkY2VHNic2Y2aEovRllEU0NPMG5kdApZc3F6TGIvQ1ZITEpOSXk1UUoxSTF6S25vdUl5cTduK3o4OUFuazI5RkZJdGwvVVJRL1BzQlVuWXFrYlhOa0RLCjZTUXc5MHBKaVNwQVhMV2pQc1MxQWdNQkFBR2paakJrTUE0R0ExVWREd0VCL3dRRUF3SUJCakFTQmdOVkhSTUIKQWY4RUNEQUdBUUgvQWdFQU1CMEdBMVVkRGdRV0JCVFRnNW82VWRrRFlqV1BhcVRhbVlpN2RIQlBNekFmQmdOVgpIU01FR0RBV2dCUVBSdjl2K21jQW8yMUJsRVU1dWpqUnQrT040ekFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBClpvZjJxMUxEUGtkdXRRZ0VzOW8ya1lObU4yMENIeGZHenJSWlVjUjd0M3pKeEN2Rm03VSs3d1dMbEVKTnZPNFIKWGdCZnJmeHYrOGRDNzBmdzAzQzlKbHdWTTdpLzEwTlB5aWVUaklESVZrOGpzTm9mbmZmemhPTEdJUWRHbWVBRwoxNlM3SDNxTVBaeDZlQ2Zta005c01RcXRJSm9Fdi9keWpJMURoVmNPdENzMnc3VFNqckhVVE9ESklFWjB3WGRBCmNMeWJxaDBGUTRuN0ZORjFQWHNYQlpzN2k4Rmcwc3N0bi9BVVdLb1FETjNtRUY0MUh3UXBlVjdDQjIrTm0wSWIKdXNTamlNNktSNzd4b2dzbG9kYlF3NFFRRyt3NUhRT3dNYTFrOFdUQ05ycGx4ZHNuYVFKamRxVXdDZGl4aWNxMgpEZUh1U2t6NGN5a0FJL05XYzJjWkl3PT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=",
"ca-key.pem": "LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcFFJQkFBS0NBUUVBdDZLT2JmL3luVFE3NTdLRjdkbFhjaWhKQTg0NTM4ZW8zeFJ4cUJBQnJYaDN0SUd0CmNxMzlWUE9YenlPTnVVckZ3K3luLzVHeHQycXlJT2VKUDhOd0hwRjRDY3pVTTY3cGNOSGJjWGNrdDdXN0xpRUUKcGJVd3QveThiWlBQUlkyTitQVXVycTZQbVRaNFZ4V0dEMFRnZUc2VHo3V1FnQjFFWVJOdVQ3QVA2NVBSVWxaWgoxaDF4UzIxNUFYdUlXR011RUlrNTJ6RUI0alNzSVpCcWkzMTFUMnd4cElNbXkwOVlaNTFXWXI4TzFtcEh4ZWs3Ckc3SCtvU2Z4V0EwZ2p0SjNiV0xLc3kyL3dsUnl5VFNNdVVDZFNOY3lwNkxpTXF1NS9zL1BRSjVOdlJSU0xaZjEKRVVQejdBVkoyS3BHMXpaQXl1a2tNUGRLU1lrcVFGeTFvejdFdFFJREFRQUJBb0lCQUNyVTJZL0NvUjRWcnR0TwpBbnNGdEtYRnk3SDlpZll1SmE5U24yZnB3OXBvUE5OM1k3Tlo3YnJBem1uY0N4UnE0bEhlZ3hqVExMWnhSbmJ5ClNrcjdGTTJzZEdra3cySUNyQ1JLYm5xNnBXL01EWXFtM09TaHJHbGRvNzJUT2tjb3l6S0VUWTBrM2cySWJPMHkKOGYvaHV0R2NTUkdyY2JiUUhNRGZ2VjBNM2NtK1hUV1VCUmtnRGxCSUdHbzYzMlBFWFNqMFFyN3Y0TEdOMFB4NgpZTjZOOTFJbnVFSThYNjBweWVMQkY5TkRJWWplVjdRMUt1OEJ5TVNnWmNNUmZwSk1ZVi8zWHU5SkQ5VTVJTlZ0Ci9wV25Ed3dqb2dvRk9JdUdVVmNGTUZyY1diZExFMWtnRDRqRC9nNnBkbUtoYmlEN1JkbmZjZ3JhZ0lqdG52OSsKZWdXcmE0RUNnWUVBeXBDT0hyY21KYk1MbmJ5V2pXR3hnRnRDNTZPYjJPVmpOdTU0SkpxMFNTRUNhckgyTXpRTgpxRzVNb3hIUm1JYi9FVHFLZ2FzL0tHczJrV3FFK0NjMGN2cHU1QkF2RkxZMVdoYXpBRVNlekEzWDl6UjREblpMCkF5WkhhMjhZTGpXbHFYdEEwWERuZXZaQm51c0UrMnpBb2RlSUl2NDhMeTJJOE91REY2Z1F2S1VDZ1lFQTZCT24KOXRidTNURHBCNHN0b3Y3d0dONTduY0xYMnErOUJGbmIzQlRwb1l0eHJNbnh4YVRVdGlsTDk4Nk0yWjg5SFdGMApHNzVIT3YxSXA4aHVwQklXM3luamFBeWFpS1M5b0QyeU4xbjU3aDNIT2VHbExIdjhqUFI5OHpWY0hIUVhzaXdhCmdMSEF2ZW9tVTFhTjNudjBKbUpUUFdJVlVUOFJOUDN3cTJqOEd0RUNnWUVBclN1MWhBYTVJd09WQzYxODI3TkkKQnQ1K0xQOU9yYmMxQVhJTzNlUXYrbEN3K3p2V3FXRjN4NlU3K1RDemlYem5NL2hqRG9XeXdjQWViMlNyOW1XMQp6aEhRbVVKSXJhRXpyU2U0c2FMNFNxUVBIRFFMNnZrd0dhb3c1bVNjUEd6NmloQm5rbVcrVHYyVmplR0hhZFpJClBGUEErNEZ6UERYbVcyaExzdjZvQ0UwQ2dZRUFrWC9CVG9CeVFUcm8zbEhqeXMwS3VvekI4NmEwcmVhQUdybzcKblQ5L09raXlmQ0lmOGtubEVrL1IwUXN1UTBJU2p0a0tjbHBaVGlKOTZyTStxcDZzdUQwSzFiRVJNWm9YU045bApYRTZNNHp6SUt3SE5ESmF2UDdBSlJ2R3RUaWw2c2JuMDQ3cU5uSU93ZzQ5QVlyeFQxYnpQY3l5TE1PVFpaTi9RCmc2Yk9hQUVDZ1lFQWpkVGkwcEQxWFYxcU9TVHZwdDdnN1NPUHBIVzcrK3JMRGpoYkx2VXlJdElrMVZGU0lRNTEKdTQycTJNdzVSWjdpT2NjZytJdU8zSzZhWjBSWWtIZ2szQlRyNFFYRjNGdEIxSUxORVRmNzRiSHBDWlBqQ1FXVgpZNk5la1lTNlluS1FWaDI1MXF1Qk9wLzUvSEVDMTJpZEs4dTVsMkdPVTdESStZa3FtYjNNck5JPQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=",
"cert-chain.pem": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURQRENDQWlTZ0F3SUJBZ0lSQU1rSjIzc290cHFpaVdwcyszOERmL1l3RFFZSktvWklodmNOQVFFTEJRQXcKSHpFZE1Cc0dBMVVFQXhNVWNtOXZkQzVwYzNScGJ5NXBiaTVoWTNScGIyNHdIaGNOTWpJd05qSTRNVFF4TVRNMQpXaGNOTXpJd05qSTFNVFF4TVRNMVdqQXNNU293S0FZRFZRUURFeUYzWlhOMExtbHVkR1Z5YldWa2FXRjBaUzVwCmMzUnBieTVwYmk1aFkzUnBiMjR3Z2dFaU1BMEdDU3FHU0liM0RRRUJBUVVBQTRJQkR3QXdnZ0VLQW9JQkFRQzMKb281dC8vS2RORHZuc29YdDJWZHlLRWtEempuZng2amZGSEdvRUFHdGVIZTBnYTF5cmYxVTg1ZlBJNDI1U3NYRAo3S2Yva2JHM2FySWc1NGsvdzNBZWtYZ0p6TlF6cnVsdzBkdHhkeVMzdGJzdUlRU2x0VEMzL0x4dGs4OUZqWTM0CjlTNnVybytaTm5oWEZZWVBST0I0YnBQUHRaQ0FIVVJoRTI1UHNBL3JrOUZTVmxuV0hYRkxiWGtCZTRoWVl5NFEKaVRuYk1RSGlOS3doa0dxTGZYVlBiREdrZ3liTFQxaG5uVlppdnc3V2FrZkY2VHNic2Y2aEovRllEU0NPMG5kdApZc3F6TGIvQ1ZITEpOSXk1UUoxSTF6S25vdUl5cTduK3o4OUFuazI5RkZJdGwvVVJRL1BzQlVuWXFrYlhOa0RLCjZTUXc5MHBKaVNwQVhMV2pQc1MxQWdNQkFBR2paakJrTUE0R0ExVWREd0VCL3dRRUF3SUJCakFTQmdOVkhSTUIKQWY4RUNEQUdBUUgvQWdFQU1CMEdBMVVkRGdRV0JCVFRnNW82VWRrRFlqV1BhcVRhbVlpN2RIQlBNekFmQmdOVgpIU01FR0RBV2dCUVBSdjl2K21jQW8yMUJsRVU1dWpqUnQrT040ekFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBClpvZjJxMUxEUGtkdXRRZ0VzOW8ya1lObU4yMENIeGZHenJSWlVjUjd0M3pKeEN2Rm03VSs3d1dMbEVKTnZPNFIKWGdCZnJmeHYrOGRDNzBmdzAzQzlKbHdWTTdpLzEwTlB5aWVUaklESVZrOGpzTm9mbmZmemhPTEdJUWRHbWVBRwoxNlM3SDNxTVBaeDZlQ2Zta005c01RcXRJSm9Fdi9keWpJMURoVmNPdENzMnc3VFNqckhVVE9ESklFWjB3WGRBCmNMeWJxaDBGUTRuN0ZORjFQWHNYQlpzN2k4Rmcwc3N0bi9BVVdLb1FETjNtRUY0MUh3UXBlVjdDQjIrTm0wSWIKdXNTamlNNktSNzd4b2dzbG9kYlF3NFFRRyt3NUhRT3dNYTFrOFdUQ05ycGx4ZHNuYVFKamRxVXdDZGl4aWNxMgpEZUh1U2t6NGN5a0FJL05XYzJjWkl3PT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQotLS0tLUJFR0lOIENFUlRJRklDQVRFLS0tLS0KTUlJRERUQ0NBZldnQXdJQkFnSVFTK2pTZmZaWDdpdG9oanlyYXV0Y3pEQU5CZ2txaGtpRzl3MEJBUXNGQURBZgpNUjB3R3dZRFZRUURFeFJ5YjI5MExtbHpkR2x2TG1sdUxtRmpkR2x2YmpBZUZ3MHlNakEyTWpneE5ERXhNelZhCkZ3MHpNakEyTWpVeE5ERXhNelZhTUI4eEhUQWJCZ05WQkFNVEZISnZiM1F1YVhOMGFXOHVhVzR1WVdOMGFXOXUKTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUFzQkNlY3NUYmpPYWZXbGZlUW0xVQpNYXRHUXZaZlFJSFRoS3o0L053Mnp0dWthQUZDY2RvUG9oZkZCRXQ0YUxpYTZranNRd2ppalpSM043WEY2bXBnCnphWGhJelpXazlSQXVwTHl0cmhZZ08walhFeUc0N254RU9CRXJvUXNuYTlEYUoyQnIwMnVZczlHZGhaSzRzTXIKLzhRU21jOEdPa2JxaGFUVFcxb1pUSWNQalNzYWVJMGEvZ0Q0eDFjQmtRRVBQbTdlZ0VFbkZrQXl1RUlpL1NJQwpVM3JuL2ZNcW5FU204TXJnamJvSGxVWWU5NDF4eVZsRUFsTGZHLzArNXRDQXd5Q0hTQ091VThBeVYvMUdBUWVpCi9VM213alFmc2M5SnBMR3AxVVRFbHE3aUhITURYb0ptWVFYWGxuaUhXaWZFMm1sV2hJT01xY3BTZU1BcTJMa0EKbFFJREFRQUJvMFV3UXpBT0JnTlZIUThCQWY4RUJBTUNBUVl3RWdZRFZSMFRBUUgvQkFnd0JnRUIvd0lCQVRBZApCZ05WSFE0RUZnUVVEMGIvYi9wbkFLTnRRWlJGT2JvNDBiZmpqZU13RFFZSktvWklodmNOQVFFTEJRQURnZ0VCCkFEQVB2cXN6cVV3NVl2ajdOdnFxcVJWdEdVdUNJZGRGeml1MkdIK1VmdDR3a0F1enZxZFhKbzdYdTN5UGtHbmMKMkZFQ2NhdjF3Y3piYVBwUTRuKzRKUG05MDhpbHprdWIxR2o3bkthLzFHakVnWGtzK0hXN09pZE5uSndtcTJQWQppMklsRU1qWDJ3djlSZHJMd0FuS1pkTXg3ZXVPTDZRUmtOSEdiNmF2UmtTZERxMytha09LWkZFSWc5QmtJMjc4ClNBb3ZoK0s1elNJcENXM25WenE0bGNiMHlQb0txWUgyU3crTXFPc1ZwbnFpL0lIUTg5L1J4VTNUQzJLRStuNEQKM2ZSdERBcE5IYmJtaTdXWHJNK3BHNEQrQnVrMkZVRUhKVnB1MTZDaDJLMnZwUnpwa2xpcWVzK1QvNUU5MnVZOQpvYjdNQmd0NjFnNFZaL3A4K1JNSldZdz0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=",
"root-cert.pem": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUREVENDQWZXZ0F3SUJBZ0lRUytqU2ZmWlg3aXRvaGp5cmF1dGN6REFOQmdrcWhraUc5dzBCQVFzRkFEQWYKTVIwd0d3WURWUVFERXhSeWIyOTBMbWx6ZEdsdkxtbHVMbUZqZEdsdmJqQWVGdzB5TWpBMk1qZ3hOREV4TXpWYQpGdzB6TWpBMk1qVXhOREV4TXpWYU1COHhIVEFiQmdOVkJBTVRGSEp2YjNRdWFYTjBhVzh1YVc0dVlXTjBhVzl1Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBc0JDZWNzVGJqT2FmV2xmZVFtMVUKTWF0R1F2WmZRSUhUaEt6NC9OdzJ6dHVrYUFGQ2Nkb1BvaGZGQkV0NGFMaWE2a2pzUXdqaWpaUjNON1hGNm1wZwp6YVhoSXpaV2s5UkF1cEx5dHJoWWdPMGpYRXlHNDdueEVPQkVyb1FzbmE5RGFKMkJyMDJ1WXM5R2RoWks0c01yCi84UVNtYzhHT2ticWhhVFRXMW9aVEljUGpTc2FlSTBhL2dENHgxY0JrUUVQUG03ZWdFRW5Ga0F5dUVJaS9TSUMKVTNybi9mTXFuRVNtOE1yZ2pib0hsVVllOTQxeHlWbEVBbExmRy8wKzV0Q0F3eUNIU0NPdVU4QXlWLzFHQVFlaQovVTNtd2pRZnNjOUpwTEdwMVVURWxxN2lISE1EWG9KbVlRWFhsbmlIV2lmRTJtbFdoSU9NcWNwU2VNQXEyTGtBCmxRSURBUUFCbzBVd1F6QU9CZ05WSFE4QkFmOEVCQU1DQVFZd0VnWURWUjBUQVFIL0JBZ3dCZ0VCL3dJQkFUQWQKQmdOVkhRNEVGZ1FVRDBiL2IvcG5BS050UVpSRk9ibzQwYmZqamVNd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQgpBREFQdnFzenFVdzVZdmo3TnZxcXFSVnRHVXVDSWRkRnppdTJHSCtVZnQ0d2tBdXp2cWRYSm83WHUzeVBrR25jCjJGRUNjYXYxd2N6YmFQcFE0bis0SlBtOTA4aWx6a3ViMUdqN25LYS8xR2pFZ1hrcytIVzdPaWRObkp3bXEyUFkKaTJJbEVNalgyd3Y5UmRyTHdBbktaZE14N2V1T0w2UVJrTkhHYjZhdlJrU2REcTMrYWtPS1pGRUlnOUJrSTI3OApTQW92aCtLNXpTSXBDVzNuVnpxNGxjYjB5UG9LcVlIMlN3K01xT3NWcG5xaS9JSFE4OS9SeFUzVEMyS0UrbjRECjNmUnREQXBOSGJibWk3V1hyTStwRzREK0J1azJGVUVISlZwdTE2Q2gySzJ2cFJ6cGtsaXFlcytULzVFOTJ1WTkKb2I3TUJndDYxZzRWWi9wOCtSTUpXWXc9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K"
},
"kind": "Secret",
"metadata": {
"creationTimestamp": "2025-05-24T11:53:02Z",
"name": "cacerts",
"namespace": "istio-system",
"resourceVersion": "4077",
"uid": "b1833706-09dc-41b4-8b7b-158e36793a48"
},
"type": "Opaque"
}
|
(9) istio-ingressgateway 서비스 NodePort 및 정책 수정
1
2
3
| kwest patch svc -n istio-system istio-ingressgateway -p '{"spec": {"type": "LoadBalancer", "ports": [{"port": 80, "targetPort": 8080, "nodePort": 30000}]}}'
kwest patch svc -n istio-system istio-ingressgateway -p '{"spec":{"externalTrafficPolicy": "Local"}}'
kwest describe svc -n istio-system istio-ingressgateway
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| service/istio-ingressgateway patched
service/istio-ingressgateway patched
Name: istio-ingressgateway
Namespace: istio-system
Labels: app=istio-ingressgateway
install.operator.istio.io/owning-resource=istio-controlplane
install.operator.istio.io/owning-resource-namespace=istio-system
istio=ingressgateway
istio.io/rev=default
operator.istio.io/component=IngressGateways
operator.istio.io/managed=Reconcile
operator.istio.io/version=1.17.8
release=istio
Annotations: metallb.io/ip-allocated-from-pool: default
Selector: app=istio-ingressgateway,istio=ingressgateway
Type: LoadBalancer
IP Family Policy: SingleStack
IP Families: IPv4
IP: 10.100.0.246
IPs: 10.100.0.246
LoadBalancer Ingress: 172.18.255.101
Port: status-port 15021/TCP
TargetPort: 15021/TCP
NodePort: status-port 30545/TCP
Endpoints: 10.10.0.7:15021
Port: http2 80/TCP
TargetPort: 8080/TCP
NodePort: http2 30000/TCP
Endpoints: 10.10.0.7:8080
Port: https 443/TCP
TargetPort: 8443/TCP
NodePort: https 31928/TCP
Endpoints: 10.10.0.7:8443
Port: tcp 31400/TCP
TargetPort: 31400/TCP
NodePort: tcp 31839/TCP
Endpoints: 10.10.0.7:31400
Port: tls 15443/TCP
TargetPort: 15443/TCP
NodePort: tls 30833/TCP
Endpoints: 10.10.0.7:15443
Session Affinity: None
External Traffic Policy: Local
Internal Traffic Policy: Cluster
HealthCheck NodePort: 30252
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal nodeAssigned 1s (x3 over 3m29s) metallb-speaker announcing from node "west-control-plane" with protocol "layer2"
Normal ExternalTrafficPolicy 1s service-controller Cluster -> Local
|
(10) observability 서비스 NodePort 포트 재설정
1
2
3
4
5
6
7
8
9
10
| kwest patch svc -n istio-system prometheus -p '{"spec": {"type": "NodePort", "ports": [{"port": 9090, "targetPort": 9090, "nodePort": 30001}]}}'
kwest patch svc -n istio-system grafana -p '{"spec": {"type": "NodePort", "ports": [{"port": 3000, "targetPort": 3000, "nodePort": 30002}]}}'
kwest patch svc -n istio-system kiali -p '{"spec": {"type": "NodePort", "ports": [{"port": 20001, "targetPort": 20001, "nodePort": 30003}]}}'
kwest patch svc -n istio-system tracing -p '{"spec": {"type": "NodePort", "ports": [{"port": 80, "targetPort": 16686, "nodePort": 30004}]}}'
# 결과
service/prometheus patched
service/grafana patched
service/kiali patched
service/tracing patched
|
4. east 클러스터 설정 및 확인
(1) east-control-plane 컨테이너 진입
1
2
| docker exec -it east-control-plane bash
root@east-control-plane:/#
|
(2) Istioctl 설치 및 환경변수 설정
1
2
3
4
5
| root@east-control-plane:/# export ISTIOV=1.17.8
echo 'export ISTIOV=1.17.8' >> /root/.bashrc
curl -s -L https://istio.io/downloadIstio | ISTIO_VERSION=$ISTIOV sh -
cp istio-$ISTIOV/bin/istioctl /usr/local/bin/istioctl
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| Downloading istio-1.17.8 from https://github.com/istio/istio/releases/download/1.17.8/istio-1.17.8-linux-amd64.tar.gz ...
Istio 1.17.8 download complete!
The Istio release archive has been downloaded to the istio-1.17.8 directory.
To configure the istioctl client tool for your workstation,
add the /istio-1.17.8/bin directory to your environment path variable with:
export PATH="$PATH:/istio-1.17.8/bin"
Begin the Istio pre-installation check by running:
istioctl x precheck
Try Istio in ambient mode
https://istio.io/latest/docs/ambient/getting-started/
Try Istio in sidecar mode
https://istio.io/latest/docs/setup/getting-started/
Install guides for ambient mode
https://istio.io/latest/docs/ambient/install/
Install guides for sidecar mode
https://istio.io/latest/docs/setup/install/
Need more information? Visit https://istio.io/latest/docs/
|
(3) east-cluster용 IstioOperator 설정 파일 작성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| root@east-control-plane:/# cat << EOF > east-istio.yaml
apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
name: istio-controlplane
namespace: istio-system
spec:
profile: demo
components:
egressGateways:
- name: istio-egressgateway
enabled: false
values:
global:
meshID: usmesh
multiCluster:
clusterName: east-cluster
network: east-network
EOF
|
(4) east-cluster에 Istio 컨트롤 플레인 설치
1
| root@east-control-plane:/# istioctl install -f east-istio.yaml --set values.global.proxy.privileged=true -y
|
✅ 출력
1
2
3
4
5
6
| ✔ Istio core installed
✔ Istiod installed
✔ Ingress gateways installed
✔ Installation complete Making this installation the default for injection and validation.
Thank you for installing Istio 1.17. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/hMHGiwZHPU7UQRWe9
|
(5) east-cluster에 Istio observability 도구 설치
1
| root@east-control-plane:/# kubectl apply -f istio-$ISTIOV/samples/addons
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| serviceaccount/grafana created
configmap/grafana created
service/grafana created
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created
|
(6) east-control-plane 컨테이너에서 나가기
1
2
| root@east-control-plane:/# exit
exit
|
(7) observability 서비스 NodePort 포트 재설정
1
2
3
4
5
6
7
8
9
10
| keast patch svc -n istio-system prometheus -p '{"spec": {"type": "NodePort", "ports": [{"port": 9090, "targetPort": 9090, "nodePort": 31001}]}}'
keast patch svc -n istio-system grafana -p '{"spec": {"type": "NodePort", "ports": [{"port": 3000, "targetPort": 3000, "nodePort": 31002}]}}'
keast patch svc -n istio-system kiali -p '{"spec": {"type": "NodePort", "ports": [{"port": 20001, "targetPort": 20001, "nodePort": 31003}]}}'
keast patch svc -n istio-system tracing -p '{"spec": {"type": "NodePort", "ports": [{"port": 80, "targetPort": 16686, "nodePort": 31004}]}}'
# 결과
service/prometheus patched
service/grafana patched
service/kiali patched
service/tracing patched
|
🧾 다중 클러스터에서 istioctl 별칭과 인증서 적용 상태 확인
1. istioctl 기본 명령어 확인 (west/east)
1
| docker exec -it west-control-plane istioctl -h
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| Istio configuration command line utility for service operators to
debug and diagnose their Istio mesh.
Usage:
istioctl [command]
Available Commands:
admin Manage control plane (istiod) configuration
analyze Analyze Istio configuration and print validation messages
authz (authz is experimental. Use `istioctl experimental authz`)
bug-report Cluster information and log capture support tool.
completion Generate the autocompletion script for the specified shell
create-remote-secret Create a secret with credentials to allow Istio to access remote Kubernetes apiservers
dashboard Access to Istio web UIs
experimental Experimental commands that may be modified or deprecated
help Help about any command
install Applies an Istio manifest, installing or reconfiguring Istio on a cluster.
kube-inject Inject Istio sidecar into Kubernetes pod resources
manifest Commands related to Istio manifests
operator Commands related to Istio operator controller.
profile Commands related to Istio configuration profiles
proxy-config Retrieve information about proxy configuration from Envoy [kube only]
proxy-status Retrieves the synchronization status of each Envoy in the mesh [kube only]
remote-clusters Lists the remote clusters each istiod instance is connected to.
tag Command group used to interact with revision tags
uninstall Uninstall Istio from a cluster
upgrade Upgrade Istio control plane in-place
validate Validate Istio policy and rules files
verify-install Verifies Istio Installation Status
version Prints out build version information
Flags:
--context string The name of the kubeconfig context to use
-h, --help help for istioctl
-i, --istioNamespace string Istio system namespace (default "istio-system")
-c, --kubeconfig string Kubernetes configuration file
-n, --namespace string Config namespace
--vklog Level number for the log level verbosity. Like -v flag. ex: --vklog=9
Additional help topics:
istioctl options Displays istioctl global options
Use "istioctl [command] --help" for more information about a command.
|
1
| docker exec -it east-control-plane istioctl -h
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| Istio configuration command line utility for service operators to
debug and diagnose their Istio mesh.
Usage:
istioctl [command]
Available Commands:
admin Manage control plane (istiod) configuration
analyze Analyze Istio configuration and print validation messages
authz (authz is experimental. Use `istioctl experimental authz`)
bug-report Cluster information and log capture support tool.
completion Generate the autocompletion script for the specified shell
create-remote-secret Create a secret with credentials to allow Istio to access remote Kubernetes apiservers
dashboard Access to Istio web UIs
experimental Experimental commands that may be modified or deprecated
help Help about any command
install Applies an Istio manifest, installing or reconfiguring Istio on a cluster.
kube-inject Inject Istio sidecar into Kubernetes pod resources
manifest Commands related to Istio manifests
operator Commands related to Istio operator controller.
profile Commands related to Istio configuration profiles
proxy-config Retrieve information about proxy configuration from Envoy [kube only]
proxy-status Retrieves the synchronization status of each Envoy in the mesh [kube only]
remote-clusters Lists the remote clusters each istiod instance is connected to.
tag Command group used to interact with revision tags
uninstall Uninstall Istio from a cluster
upgrade Upgrade Istio control plane in-place
validate Validate Istio policy and rules files
verify-install Verifies Istio Installation Status
version Prints out build version information
Flags:
--context string The name of the kubeconfig context to use
-h, --help help for istioctl
-i, --istioNamespace string Istio system namespace (default "istio-system")
-c, --kubeconfig string Kubernetes configuration file
-n, --namespace string Config namespace
--vklog Level number for the log level verbosity. Like -v flag. ex: --vklog=9
Additional help topics:
istioctl options Displays istioctl global options
Use "istioctl [command] --help" for more information about a command.
|
2. proxy-status 확인
✅ 출력
1
2
| NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
istio-ingressgateway-5db74c978c-7k7tr.istio-system west-cluster SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-5585445f4c-gphfz 1.17.8
|
✅ 출력
1
2
| NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
istio-ingressgateway-7f6f8f8d99-cg2t4.istio-system east-cluster SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-85976468f-4ctv8 1.17.8
|
3. Istio 인증서(secret) 구성 확인
1
| iwest proxy-config secret deploy/istio-ingressgateway.istio-system
|
✅ 출력
1
2
3
| RESOURCE NAME TYPE STATUS VALID CERT SERIAL NUMBER NOT AFTER NOT BEFORE
default Cert Chain ACTIVE true 166493759875349142908167651258595250305 2025-05-25T16:13:02Z 2025-05-24T16:11:02Z
ROOTCA CA ACTIVE true 100900981840825465297757884708490534092 2032-06-25T14:11:35Z 2022-06-28T14:11:35Z
|
4. 인증서 상세 정보(json) 확인
1
| iwest proxy-config secret deploy/istio-ingressgateway.istio-system -o json
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| {
"dynamicActiveSecrets": [
{
"name": "default",
"lastUpdated": "2025-05-24T16:13:02.544Z",
"secret": {
"@type": "type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.Secret",
"name": "default",
"tlsCertificate": {
"certificateChain": {
"inlineBytes": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURkakNDQWw2Z0F3SUJBZ0lRZlVHSUloQU1BVENyNEk4czJ5ZVFnVEFOQmdrcWhraUc5dzBCQVFzRkFEQXMKTVNvd0tBWURWUVFERXlGM1pYTjBMbWx1ZEdWeWJXVmthV0YwWlM1cGMzUnBieTVwYmk1aFkzUnBiMjR3SGhjTgpNalV3TlRJME1UWXhNVEF5V2hjTk1qVXdOVEkxTVRZeE16QXlXakFBTUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGCkFBT0NBUThBTUlJQkNnS0NBUUVBdWFzLy9BQjdPV29tdjJCVzhhL1JZd3Z2NkNKZDlHcWZxWEc0OEZXbnk5SHkKV0l0ejZsSkZZa2lKZEttbXFtOGJPU0VyUlFUNDRDWm9NY296bVJoWjJSZ1J2VGtXMzV5L1RsSDNhYmk1S1hPaQpTUkFSTWRsS1BIbVRkVXFNWThOaXk4ZW4ramszZXJ0NkJQSEpIREdrV3c1NVB0Y3hja0l4eDQ4VkFPUzh5aHZYCmF6cDdDeGtHcnpUcFZtMFF1dFYrSjh2ZlJPNldha3lneE5RNUJCRHRLRG5uRXlkY2pTUERNVkk3NGJLRlBSWm4Kb2QyUERHbXR1NjE5MDVjNHcyR29CMTl1VytmZm1DQlhVQTk4SzI2UVlOMzVnWEQrSVJiazhYSDNhZzRTZHBBVQpWM0YxcjJ0Mnl1RlRXWktSVHdXbnlqZHloZlVSYk5aL21veHZBUmRia3dJREFRQUJvNEcvTUlHOE1BNEdBMVVkCkR3RUIvd1FFQXdJRm9EQWRCZ05WSFNVRUZqQVVCZ2dyQmdFRkJRY0RBUVlJS3dZQkJRVUhBd0l3REFZRFZSMFQKQVFIL0JBSXdBREFmQmdOVkhTTUVHREFXZ0JUVGc1bzZVZGtEWWpXUGFxVGFtWWk3ZEhCUE16QmNCZ05WSFJFQgpBZjhFVWpCUWhrNXpjR2xtWm1VNkx5OWpiSFZ6ZEdWeUxteHZZMkZzTDI1ekwybHpkR2x2TFhONWMzUmxiUzl6CllTOXBjM1JwYnkxcGJtZHlaWE56WjJGMFpYZGhlUzF6WlhKMmFXTmxMV0ZqWTI5MWJuUXdEUVlKS29aSWh2Y04KQVFFTEJRQURnZ0VCQUNxTVVtU2ZzNnY4WnFhelNMVm5CaWtLejZKMjFjcVFReTFPMWpvQzA2Sm1xcWJnQzVteQpJbzNHY0pIVElOemtPQithNUI4ZUh5a2VOdU84VzJpa0xTUTJLSkhzSUFYa28veEZvelRCOTBVNnd3cE5qdldqCmprdVV4eGR3enRoL0ZVdFFiWU8vQmlmU0tkcFRqVkRBN1RGbFF6aWpHb2ZCdkNVMGR1RWNLdklpWUVDWVdxZGQKWnYzajhQRzA4Ni9GcitqMmtydFlHcjVZc1BUZ1V4OGl6bkxmUE1sSFlRVDJJelZaMVMvRWRLUDBKYWVZQ0dIbQp2Q3VpMGpnSC8vaHBuVzdseDh6L2k2NC9oOVI3eG1CS2dpVHNmUTFUdlZFQmhFMUxGeEhPVm1NZlNEMHo0YzNECnJVZHY5UmJ2QjVtQ3dGR0pZZmxKOWJiZFpoN1liaEh2Y0lVPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCi0tLS0tQkVHSU4gQ0VSVElGSUNBVEUtLS0tLQpNSUlEUERDQ0FpU2dBd0lCQWdJUkFNa0oyM3NvdHBxaWlXcHMrMzhEZi9Zd0RRWUpLb1pJaHZjTkFRRUxCUUF3Ckh6RWRNQnNHQTFVRUF4TVVjbTl2ZEM1cGMzUnBieTVwYmk1aFkzUnBiMjR3SGhjTk1qSXdOakk0TVRReE1UTTEKV2hjTk16SXdOakkxTVRReE1UTTFXakFzTVNvd0tBWURWUVFERXlGM1pYTjBMbWx1ZEdWeWJXVmthV0YwWlM1cApjM1JwYnk1cGJpNWhZM1JwYjI0d2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUMzCm9vNXQvL0tkTkR2bnNvWHQyVmR5S0VrRHpqbmZ4NmpmRkhHb0VBR3RlSGUwZ2ExeXJmMVU4NWZQSTQyNVNzWEQKN0tmL2tiRzNhcklnNTRrL3czQWVrWGdKek5RenJ1bHcwZHR4ZHlTM3Ric3VJUVNsdFRDMy9MeHRrODlGalkzNAo5UzZ1cm8rWk5uaFhGWVlQUk9CNGJwUFB0WkNBSFVSaEUyNVBzQS9yazlGU1ZsbldIWEZMYlhrQmU0aFlZeTRRCmlUbmJNUUhpTkt3aGtHcUxmWFZQYkRHa2d5YkxUMWhublZaaXZ3N1dha2ZGNlRzYnNmNmhKL0ZZRFNDTzBuZHQKWXNxekxiL0NWSExKTkl5NVFKMUkxektub3VJeXE3bit6ODlBbmsyOUZGSXRsL1VSUS9Qc0JVbllxa2JYTmtESwo2U1F3OTBwSmlTcEFYTFdqUHNTMUFnTUJBQUdqWmpCa01BNEdBMVVkRHdFQi93UUVBd0lCQmpBU0JnTlZIUk1CCkFmOEVDREFHQVFIL0FnRUFNQjBHQTFVZERnUVdCQlRUZzVvNlVka0RZaldQYXFUYW1ZaTdkSEJQTXpBZkJnTlYKSFNNRUdEQVdnQlFQUnY5dittY0FvMjFCbEVVNXVqalJ0K09ONHpBTkJna3Foa2lHOXcwQkFRc0ZBQU9DQVFFQQpab2YycTFMRFBrZHV0UWdFczlvMmtZTm1OMjBDSHhmR3pyUlpVY1I3dDN6SnhDdkZtN1UrN3dXTGxFSk52TzRSClhnQmZyZnh2KzhkQzcwZncwM0M5Smx3Vk03aS8xME5QeWllVGpJRElWazhqc05vZm5mZnpoT0xHSVFkR21lQUcKMTZTN0gzcU1QWng2ZUNmbWtNOXNNUXF0SUpvRXYvZHlqSTFEaFZjT3RDczJ3N1RTanJIVVRPREpJRVowd1hkQQpjTHlicWgwRlE0bjdGTkYxUFhzWEJaczdpOEZnMHNzdG4vQVVXS29RRE4zbUVGNDFId1FwZVY3Q0IyK05tMEliCnVzU2ppTTZLUjc3eG9nc2xvZGJRdzRRUUcrdzVIUU93TWExazhXVENOcnBseGRzbmFRSmpkcVV3Q2RpeGljcTIKRGVIdVNrejRjeWtBSS9OV2MyY1pJdz09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0KLS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUREVENDQWZXZ0F3SUJBZ0lRUytqU2ZmWlg3aXRvaGp5cmF1dGN6REFOQmdrcWhraUc5dzBCQVFzRkFEQWYKTVIwd0d3WURWUVFERXhSeWIyOTBMbWx6ZEdsdkxtbHVMbUZqZEdsdmJqQWVGdzB5TWpBMk1qZ3hOREV4TXpWYQpGdzB6TWpBMk1qVXhOREV4TXpWYU1COHhIVEFiQmdOVkJBTVRGSEp2YjNRdWFYTjBhVzh1YVc0dVlXTjBhVzl1Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBc0JDZWNzVGJqT2FmV2xmZVFtMVUKTWF0R1F2WmZRSUhUaEt6NC9OdzJ6dHVrYUFGQ2Nkb1BvaGZGQkV0NGFMaWE2a2pzUXdqaWpaUjNON1hGNm1wZwp6YVhoSXpaV2s5UkF1cEx5dHJoWWdPMGpYRXlHNDdueEVPQkVyb1FzbmE5RGFKMkJyMDJ1WXM5R2RoWks0c01yCi84UVNtYzhHT2ticWhhVFRXMW9aVEljUGpTc2FlSTBhL2dENHgxY0JrUUVQUG03ZWdFRW5Ga0F5dUVJaS9TSUMKVTNybi9mTXFuRVNtOE1yZ2pib0hsVVllOTQxeHlWbEVBbExmRy8wKzV0Q0F3eUNIU0NPdVU4QXlWLzFHQVFlaQovVTNtd2pRZnNjOUpwTEdwMVVURWxxN2lISE1EWG9KbVlRWFhsbmlIV2lmRTJtbFdoSU9NcWNwU2VNQXEyTGtBCmxRSURBUUFCbzBVd1F6QU9CZ05WSFE4QkFmOEVCQU1DQVFZd0VnWURWUjBUQVFIL0JBZ3dCZ0VCL3dJQkFUQWQKQmdOVkhRNEVGZ1FVRDBiL2IvcG5BS050UVpSRk9ibzQwYmZqamVNd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQgpBREFQdnFzenFVdzVZdmo3TnZxcXFSVnRHVXVDSWRkRnppdTJHSCtVZnQ0d2tBdXp2cWRYSm83WHUzeVBrR25jCjJGRUNjYXYxd2N6YmFQcFE0bis0SlBtOTA4aWx6a3ViMUdqN25LYS8xR2pFZ1hrcytIVzdPaWRObkp3bXEyUFkKaTJJbEVNalgyd3Y5UmRyTHdBbktaZE14N2V1T0w2UVJrTkhHYjZhdlJrU2REcTMrYWtPS1pGRUlnOUJrSTI3OApTQW92aCtLNXpTSXBDVzNuVnpxNGxjYjB5UG9LcVlIMlN3K01xT3NWcG5xaS9JSFE4OS9SeFUzVEMyS0UrbjRECjNmUnREQXBOSGJibWk3V1hyTStwRzREK0J1azJGVUVISlZwdTE2Q2gySzJ2cFJ6cGtsaXFlcytULzVFOTJ1WTkKb2I3TUJndDYxZzRWWi9wOCtSTUpXWXc9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0KLS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUREVENDQWZXZ0F3SUJBZ0lRUytqU2ZmWlg3aXRvaGp5cmF1dGN6REFOQmdrcWhraUc5dzBCQVFzRkFEQWYKTVIwd0d3WURWUVFERXhSeWIyOTBMbWx6ZEdsdkxtbHVMbUZqZEdsdmJqQWVGdzB5TWpBMk1qZ3hOREV4TXpWYQpGdzB6TWpBMk1qVXhOREV4TXpWYU1COHhIVEFiQmdOVkJBTVRGSEp2YjNRdWFYTjBhVzh1YVc0dVlXTjBhVzl1Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBc0JDZWNzVGJqT2FmV2xmZVFtMVUKTWF0R1F2WmZRSUhUaEt6NC9OdzJ6dHVrYUFGQ2Nkb1BvaGZGQkV0NGFMaWE2a2pzUXdqaWpaUjNON1hGNm1wZwp6YVhoSXpaV2s5UkF1cEx5dHJoWWdPMGpYRXlHNDdueEVPQkVyb1FzbmE5RGFKMkJyMDJ1WXM5R2RoWks0c01yCi84UVNtYzhHT2ticWhhVFRXMW9aVEljUGpTc2FlSTBhL2dENHgxY0JrUUVQUG03ZWdFRW5Ga0F5dUVJaS9TSUMKVTNybi9mTXFuRVNtOE1yZ2pib0hsVVllOTQxeHlWbEVBbExmRy8wKzV0Q0F3eUNIU0NPdVU4QXlWLzFHQVFlaQovVTNtd2pRZnNjOUpwTEdwMVVURWxxN2lISE1EWG9KbVlRWFhsbmlIV2lmRTJtbFdoSU9NcWNwU2VNQXEyTGtBCmxRSURBUUFCbzBVd1F6QU9CZ05WSFE4QkFmOEVCQU1DQVFZd0VnWURWUjBUQVFIL0JBZ3dCZ0VCL3dJQkFUQWQKQmdOVkhRNEVGZ1FVRDBiL2IvcG5BS050UVpSRk9ibzQwYmZqamVNd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQgpBREFQdnFzenFVdzVZdmo3TnZxcXFSVnRHVXVDSWRkRnppdTJHSCtVZnQ0d2tBdXp2cWRYSm83WHUzeVBrR25jCjJGRUNjYXYxd2N6YmFQcFE0bis0SlBtOTA4aWx6a3ViMUdqN25LYS8xR2pFZ1hrcytIVzdPaWRObkp3bXEyUFkKaTJJbEVNalgyd3Y5UmRyTHdBbktaZE14N2V1T0w2UVJrTkhHYjZhdlJrU2REcTMrYWtPS1pGRUlnOUJrSTI3OApTQW92aCtLNXpTSXBDVzNuVnpxNGxjYjB5UG9LcVlIMlN3K01xT3NWcG5xaS9JSFE4OS9SeFUzVEMyS0UrbjRECjNmUnREQXBOSGJibWk3V1hyTStwRzREK0J1azJGVUVISlZwdTE2Q2gySzJ2cFJ6cGtsaXFlcytULzVFOTJ1WTkKb2I3TUJndDYxZzRWWi9wOCtSTUpXWXc9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K"
},
"privateKey": {
"inlineBytes": "W3JlZGFjdGVkXQ=="
}
}
}
},
{
"name": "ROOTCA",
"lastUpdated": "2025-05-24T16:13:02.541Z",
"secret": {
"@type": "type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.Secret",
"name": "ROOTCA",
"validationContext": {
"trustedCa": {
"inlineBytes": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUREVENDQWZXZ0F3SUJBZ0lRUytqU2ZmWlg3aXRvaGp5cmF1dGN6REFOQmdrcWhraUc5dzBCQVFzRkFEQWYKTVIwd0d3WURWUVFERXhSeWIyOTBMbWx6ZEdsdkxtbHVMbUZqZEdsdmJqQWVGdzB5TWpBMk1qZ3hOREV4TXpWYQpGdzB6TWpBMk1qVXhOREV4TXpWYU1COHhIVEFiQmdOVkJBTVRGSEp2YjNRdWFYTjBhVzh1YVc0dVlXTjBhVzl1Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBc0JDZWNzVGJqT2FmV2xmZVFtMVUKTWF0R1F2WmZRSUhUaEt6NC9OdzJ6dHVrYUFGQ2Nkb1BvaGZGQkV0NGFMaWE2a2pzUXdqaWpaUjNON1hGNm1wZwp6YVhoSXpaV2s5UkF1cEx5dHJoWWdPMGpYRXlHNDdueEVPQkVyb1FzbmE5RGFKMkJyMDJ1WXM5R2RoWks0c01yCi84UVNtYzhHT2ticWhhVFRXMW9aVEljUGpTc2FlSTBhL2dENHgxY0JrUUVQUG03ZWdFRW5Ga0F5dUVJaS9TSUMKVTNybi9mTXFuRVNtOE1yZ2pib0hsVVllOTQxeHlWbEVBbExmRy8wKzV0Q0F3eUNIU0NPdVU4QXlWLzFHQVFlaQovVTNtd2pRZnNjOUpwTEdwMVVURWxxN2lISE1EWG9KbVlRWFhsbmlIV2lmRTJtbFdoSU9NcWNwU2VNQXEyTGtBCmxRSURBUUFCbzBVd1F6QU9CZ05WSFE4QkFmOEVCQU1DQVFZd0VnWURWUjBUQVFIL0JBZ3dCZ0VCL3dJQkFUQWQKQmdOVkhRNEVGZ1FVRDBiL2IvcG5BS050UVpSRk9ibzQwYmZqamVNd0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQgpBREFQdnFzenFVdzVZdmo3TnZxcXFSVnRHVXVDSWRkRnppdTJHSCtVZnQ0d2tBdXp2cWRYSm83WHUzeVBrR25jCjJGRUNjYXYxd2N6YmFQcFE0bis0SlBtOTA4aWx6a3ViMUdqN25LYS8xR2pFZ1hrcytIVzdPaWRObkp3bXEyUFkKaTJJbEVNalgyd3Y5UmRyTHdBbktaZE14N2V1T0w2UVJrTkhHYjZhdlJrU2REcTMrYWtPS1pGRUlnOUJrSTI3OApTQW92aCtLNXpTSXBDVzNuVnpxNGxjYjB5UG9LcVlIMlN3K01xT3NWcG5xaS9JSFE4OS9SeFUzVEMyS0UrbjRECjNmUnREQXBOSGJibWk3V1hyTStwRzREK0J1azJGVUVISlZwdTE2Q2gySzJ2cFJ6cGtsaXFlcytULzVFOTJ1WTkKb2I3TUJndDYxZzRWWi9wOCtSTUpXWXc9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0="
}
}
}
}
]
}
|
5. Proxy 리스너 구성 확인
1
| iwest proxy-config listener deploy/istio-ingressgateway.istio-system
|
✅ 출력
1
2
3
| ADDRESS PORT MATCH DESTINATION
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
|
6. Proxy 라우트 설정 확인
1
| iwest proxy-config route deploy/istio-ingressgateway.istio-system
|
✅ 출력
1
2
3
| NAME DOMAINS MATCH VIRTUAL SERVICE
* /stats/prometheus*
* /healthz/ready*
|
7. Proxy 클러스터 정보 확인
1
| iwest proxy-config cluster deploy/istio-ingressgateway.istio-system
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
|
8. Proxy 엔드포인트 정보 확인 (iwest)
1
| iwest proxy-config endpoint deploy/istio-ingressgateway.istio-system
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.10.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.10.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.10.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.10.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.10.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.10.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.10.0.2:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.10.0.3:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.3:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.4:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.10.0.4:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.10.0.4:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.10.0.4:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.10.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.10.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.7:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.100.0.69:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.2:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
9. Proxy 엔드포인트 정보 확인 (ieast)
1
| ieast proxy-config endpoint deploy/istio-ingressgateway.istio-system
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.2:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.2:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.4:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.7:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.20.0.7:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.20.0.7:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.20.0.7:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.200.0.162:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.3:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
10. west 클러스터 전체 파드 상태 및 IP 확인
1
| kwest get pod -owide -A
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
istio-system grafana-b854c6c8-vgwtq 1/1 Running 0 17m 10.10.0.9 west-control-plane <none> <none>
istio-system istio-ingressgateway-5db74c978c-7k7tr 1/1 Running 25 (21m ago) 119m 10.10.0.7 west-control-plane <none> <none>
istio-system istiod-5585445f4c-gphfz 1/1 Running 1 (19m ago) 120m 10.10.0.4 west-control-plane <none> <none>
istio-system jaeger-5556cd8fcf-fqb7t 1/1 Running 0 17m 10.10.0.10 west-control-plane <none> <none>
istio-system kiali-648847c8c4-jvz2z 1/1 Running 0 17m 10.10.0.11 west-control-plane <none> <none>
istio-system prometheus-7b8b9dd44c-87xpj 2/2 Running 0 17m 10.10.0.12 west-control-plane <none> <none>
kube-system coredns-bd6b6df9f-9jdh2 1/1 Running 1 (19m ago) 5h24m 10.10.0.6 west-control-plane <none> <none>
kube-system coredns-bd6b6df9f-l529w 1/1 Running 1 (19m ago) 5h24m 10.10.0.3 west-control-plane <none> <none>
kube-system etcd-west-control-plane 1/1 Running 1 (19m ago) 5h25m 172.18.0.2 west-control-plane <none> <none>
kube-system kindnet-57wjw 1/1 Running 1 (19m ago) 5h24m 172.18.0.2 west-control-plane <none> <none>
kube-system kube-apiserver-west-control-plane 1/1 Running 1 (19m ago) 5h25m 172.18.0.2 west-control-plane <none> <none>
kube-system kube-controller-manager-west-control-plane 1/1 Running 1 (19m ago) 5h25m 172.18.0.2 west-control-plane <none> <none>
kube-system kube-ops-view-79df45849b-6qt7s 1/1 Running 1 (19m ago) 5h22m 10.10.0.2 west-control-plane <none> <none>
kube-system kube-proxy-4z8dz 1/1 Running 1 (19m ago) 5h24m 172.18.0.2 west-control-plane <none> <none>
kube-system kube-scheduler-west-control-plane 1/1 Running 1 (19m ago) 5h25m 172.18.0.2 west-control-plane <none> <none>
local-path-storage local-path-provisioner-6668df4555-bmsxs 1/1 Running 1 (19m ago) 5h24m 10.10.0.8 west-control-plane <none> <none>
metallb-system controller-686c7db689-wlhwf 1/1 Running 2 (18m ago) 5h2m 10.10.0.5 west-control-plane <none> <none>
metallb-system speaker-9mzbd 1/1 Running 2 (18m ago) 5h2m 172.18.0.2 west-control-plane <none> <none>
|
11. east 클러스터 전체 파드 상태 및 IP 확인
1
| keast get pod -owide -A
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| NAMESPACE NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
istio-system grafana-b854c6c8-svh96 1/1 Running 0 11m 10.20.0.9 east-control-plane <none> <none>
istio-system istio-ingressgateway-7f6f8f8d99-cg2t4 1/1 Running 0 11m 10.20.0.8 east-control-plane <none> <none>
istio-system istiod-85976468f-4ctv8 1/1 Running 0 12m 10.20.0.7 east-control-plane <none> <none>
istio-system jaeger-5556cd8fcf-qx794 1/1 Running 0 11m 10.20.0.10 east-control-plane <none> <none>
istio-system kiali-648847c8c4-gqp7j 1/1 Running 0 11m 10.20.0.11 east-control-plane <none> <none>
istio-system prometheus-7b8b9dd44c-vt8td 2/2 Running 0 11m 10.20.0.12 east-control-plane <none> <none>
kube-system coredns-bd6b6df9f-vwdrq 1/1 Running 1 (19m ago) 5h19m 10.20.0.2 east-control-plane <none> <none>
kube-system coredns-bd6b6df9f-wglvp 1/1 Running 1 (19m ago) 5h19m 10.20.0.6 east-control-plane <none> <none>
kube-system etcd-east-control-plane 1/1 Running 1 (19m ago) 5h19m 172.18.0.3 east-control-plane <none> <none>
kube-system kindnet-6k8jk 1/1 Running 1 (19m ago) 5h19m 172.18.0.3 east-control-plane <none> <none>
kube-system kube-apiserver-east-control-plane 1/1 Running 1 (19m ago) 5h19m 172.18.0.3 east-control-plane <none> <none>
kube-system kube-controller-manager-east-control-plane 1/1 Running 1 (19m ago) 5h19m 172.18.0.3 east-control-plane <none> <none>
kube-system kube-ops-view-79df45849b-ffhdt 1/1 Running 1 (19m ago) 5h15m 10.20.0.4 east-control-plane <none> <none>
kube-system kube-proxy-57w4c 1/1 Running 1 (19m ago) 5h19m 172.18.0.3 east-control-plane <none> <none>
kube-system kube-scheduler-east-control-plane 1/1 Running 1 (19m ago) 5h19m 172.18.0.3 east-control-plane <none> <none>
local-path-storage local-path-provisioner-6668df4555-pns5j 1/1 Running 2 (19m ago) 5h19m 10.20.0.3 east-control-plane <none> <none>
metallb-system controller-686c7db689-5wf5v 1/1 Running 2 (19m ago) 5h2m 10.20.0.5 east-control-plane <none> <none>
metallb-system speaker-f4cj7 1/1 Running 2 (19m ago) 5h2m 172.18.0.3 east-control-plane <none> <none>
|
🧱 두 클러스터 모두에 워크로드 실행하기
1. west 클러스터에 Webapp 및 Catalog 서비스 배포
1
2
3
4
5
| kwest create ns istioinaction
kwest label namespace istioinaction istio-injection=enabled
kwest -n istioinaction apply -f ch12/webapp-deployment-svc.yaml
kwest -n istioinaction apply -f ch12/webapp-gw-vs.yaml
kwest -n istioinaction apply -f ch12/catalog-svc.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
| namespace/istioinaction created
namespace/istioinaction labeled
serviceaccount/webapp created
service/webapp created
deployment.apps/webapp created
gateway.networking.istio.io/coolstore-gateway created
virtualservice.networking.istio.io/webapp-virtualservice created
service/catalog created
|
2. west 클러스터에서 Catalog 서비스 구성 확인
1
| cat ch12/catalog-svc.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| ---
apiVersion: v1
kind: Service
metadata:
labels:
app: catalog
name: catalog
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 3000
selector:
app: catalog
|
3. west 클러스터의 Istio 리소스 상태 점검
1
2
| kwest get deploy,pod,svc,ep -n istioinaction
kwest get svc,ep catalog -n istioinaction
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/webapp 1/1 1 1 77s
NAME READY STATUS RESTARTS AGE
pod/webapp-5c8b4fff64-rzp6q 2/2 Running 0 77s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.100.0.103 <none> 80/TCP 76s
service/webapp ClusterIP 10.100.0.165 <none> 80/TCP 77s
NAME ENDPOINTS AGE
endpoints/catalog <none> 76s
endpoints/webapp 10.10.0.13:8080 77s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.100.0.103 <none> 80/TCP 76s
NAME ENDPOINTS AGE
endpoints/catalog <none> 76s
|
4. Istio Gateway 및 VirtualService 리소스 확인
✅ 출력
1
2
3
4
5
| NAMESPACE NAME AGE
istioinaction gateway.networking.istio.io/coolstore-gateway 110s
NAMESPACE NAME GATEWAYS HOSTS AGE
istioinaction virtualservice.networking.istio.io/webapp-virtualservice ["coolstore-gateway"] ["webapp.istioinaction.io"] 110s
|
✅ 출력
1
2
3
| NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
istio-ingressgateway-5db74c978c-7k7tr.istio-system west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-5585445f4c-gphfz 1.17.8
webapp-5c8b4fff64-rzp6q.istioinaction west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-5585445f4c-gphfz 1.17.8
|
5. Istio 프록시 동기화 상태 확인
1
| for i in listener route cluster endpoint; do echo ">> k8s cluster : west - istio-config $i <<"; docker exec -it west-control-plane istioctl proxy-config $i deploy/istio-ingressgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
| >> k8s cluster : west - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 8080 ALL Route: http.8080
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
>> k8s cluster : west - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
http.8080 webapp.istioinaction.io /* webapp-virtualservice.istioinaction
* /stats/prometheus*
* /healthz/ready*
>> k8s cluster : west - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
webapp.istioinaction.svc.cluster.local 80 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> k8s cluster : west - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.10.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.10.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.10.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.10.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.10.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.10.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.10.0.13:8080 HEALTHY OK outbound|80||webapp.istioinaction.svc.cluster.local
10.10.0.2:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.10.0.3:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.3:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.4:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.10.0.4:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.10.0.4:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.10.0.4:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.10.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.10.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.7:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.100.0.69:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.2:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
6. west 클러스터 IngressGateway 구성 정보 확인
1
| iwest proxy-config cluster deploy/istio-ingressgateway.istio-system | grep catalog
|
✅ 출력
1
| catalog.istioinaction.svc.cluster.local 80 - outbound EDS
|
1
2
| iwest proxy-config endpoint deploy/istio-ingressgateway.istio-system | grep catalog
# 없음
|
7. east 클러스터에 네임스페이스 생성 및 사이드카 주입 설정
1
2
3
| keast create ns istioinaction
keast label namespace istioinaction istio-injection=enabled
|
✅ 출력
1
2
| namespace/istioinaction created
namespace/istioinaction labeled
|
8. catalog 서비스 리소스 확인 및 적용
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
| apiVersion: v1
kind: ServiceAccount
metadata:
name: catalog
---
apiVersion: v1
kind: Service
metadata:
labels:
app: catalog
name: catalog
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 3000
selector:
app: catalog
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: catalog
version: v1
name: catalog
spec:
replicas: 1
selector:
matchLabels:
app: catalog
version: v1
template:
metadata:
labels:
app: catalog
version: v1
spec:
serviceAccountName: catalog
containers:
- env:
- name: KUBERNETES_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
image: istioinaction/catalog:latest
imagePullPolicy: IfNotPresent
name: catalog
ports:
- containerPort: 3000
name: http
protocol: TCP
securityContext:
privileged: false
|
1
| keast -n istioinaction apply -f ch12/catalog.yaml
|
✅ 출력
1
2
3
| serviceaccount/catalog created
service/catalog created
deployment.apps/catalog created
|
9. catalog 리소스 배포 상태 점검
1
| keast get deploy,pod,svc,ep -n istioinaction
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/catalog 1/1 1 1 88s
NAME READY STATUS RESTARTS AGE
pod/catalog-6cf4b97d-dd2dv 2/2 Running 0 88s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.200.0.251 <none> 80/TCP 88s
NAME ENDPOINTS AGE
endpoints/catalog 10.20.0.13:3000 88s
|
10. east 클러스터에 Istio 리소스 미존재 확인
1
2
3
4
| keast get gw,vs,dr -A
# 결과
No resources found
|
11. east 클러스터의 프록시 동기화 상태 확인
✅ 출력
1
2
3
| NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
catalog-6cf4b97d-dd2dv.istioinaction east-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-85976468f-4ctv8 1.17.8
istio-ingressgateway-7f6f8f8d99-cg2t4.istio-system east-cluster SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-85976468f-4ctv8 1.17.8
|
12. east 클러스터의 Istio IngressGateway 설정 조회
1
| for i in listener route cluster endpoint; do echo ">> k8s cluster : east - istio-config $i <<"; docker exec -it east-control-plane istioctl proxy-config $i deploy/istio-ingressgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
| >> k8s cluster : east - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
>> k8s cluster : east - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
* /stats/prometheus*
* /healthz/ready*
>> k8s cluster : east - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> k8s cluster : east - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
10.20.0.2:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.2:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.4:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.7:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.20.0.7:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.20.0.7:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.20.0.7:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.200.0.162:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.3:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
13. east IngressGateway에서 catalog 서비스의 Cluster 확인
1
| ieast proxy-config cluster deploy/istio-ingressgateway.istio-system | grep catalog
|
✅ 출력
1
| catalog.istioinaction.svc.cluster.local 80 - outbound EDS
|
14. east IngressGateway에서 catalog 서비스의 Endpoint 확인
1
| ieast proxy-config endpoint deploy/istio-ingressgateway.istio-system | grep catalog
|
✅ 출력
1
| 10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
|
🔑 원격 클러스터 접근용 시크릿 만들기
1. 클러스터별 istio-system 네임스페이스의 서비스 어카운트 조회
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get sa -n istio-system --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| >> k8s cluster : west <<
NAME SECRETS AGE
default 1 4h53m
grafana 1 32m
istio-ingressgateway-service-account 1 134m
istio-reader-service-account 1 134m
istiod 1 134m
istiod-service-account 1 134m
kiali 1 32m
prometheus 1 32m
>> k8s cluster : east <<
NAME SECRETS AGE
default 1 4h53m
grafana 1 25m
istio-ingressgateway-service-account 1 25m
istio-reader-service-account 1 26m
istiod 1 26m
istiod-service-account 1 26m
kiali 1 25m
prometheus 1 25m
|
2. istio-reader-service-account 정보 상세 조회
1
| keast describe sa -n istio-system istio-reader-service-account
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| Name: istio-reader-service-account
Namespace: istio-system
Labels: app=istio-reader
install.operator.istio.io/owning-resource=istio-controlplane
install.operator.istio.io/owning-resource-namespace=istio-system
istio.io/rev=default
operator.istio.io/component=Base
operator.istio.io/managed=Reconcile
operator.istio.io/version=1.17.8
release=istio
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: istio-reader-service-account-token-v4qbx
Tokens: istio-reader-service-account-token-v4qbx
Events: <none>
|
3. istio-reader-service-account YAML 형식으로 출력
1
| keast get sa -n istio-system istio-reader-service-account -o yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| apiVersion: v1
kind: ServiceAccount
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","kind":"ServiceAccount","metadata":{"annotations":{},"labels":{"app":"istio-reader","install.operator.istio.io/owning-resource":"istio-controlplane","install.operator.istio.io/owning-resource-namespace":"istio-system","istio.io/rev":"default","operator.istio.io/component":"Base","operator.istio.io/managed":"Reconcile","operator.istio.io/version":"1.17.8","release":"istio"},"name":"istio-reader-service-account","namespace":"istio-system"}}
creationTimestamp: "2025-05-24T16:19:58Z"
labels:
app: istio-reader
install.operator.istio.io/owning-resource: istio-controlplane
install.operator.istio.io/owning-resource-namespace: istio-system
istio.io/rev: default
operator.istio.io/component: Base
operator.istio.io/managed: Reconcile
operator.istio.io/version: 1.17.8
release: istio
name: istio-reader-service-account
namespace: istio-system
resourceVersion: "22948"
uid: 58fa8822-5578-40bc-81fa-55f57d0866f9
secrets:
- name: istio-reader-service-account-token-v4qbx
|
4. 서비스 어카운트에 연결된 시크릿 이름 추출 및 시크릿 조회
1
2
3
| keast get sa -n istio-system istio-reader-service-account -o jsonpath='{.secrets[0].name}'
eirsa=$(keast get sa -n istio-system istio-reader-service-account -o jsonpath='{.secrets[0].name}')
keast get secret -n istio-system $eirsa
|
✅ 출력
1
2
3
4
| istio-reader-service-account-token-v4qbx
NAME TYPE DATA AGE
istio-reader-service-account-token-v4qbx kubernetes.io/service-account-token 3 28m
|
5. 시크릿 정보 JSON 형태로 확인
1
| keast get secret -n istio-system $eirsa -o json
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| {
"apiVersion": "v1",
"data": {
"ca.crt": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1EVXlOREV4TVRJek1Gb1hEVE0xTURVeU1qRXhNVEl6TUZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTlhICkR5Q2F3bGdNdXJ1Q0N3bFlTTkEwS2VTZWdtYUhHSnlYVnc1Y25RTm04ZUErM2E3dWcxR2hlYWUxWm9Hb2g4SlUKVC9laW9IcTM1Wk9zdVNLTExyOWc5YTAvUmpsRnVwVnNnQXltcGcxc3FFNzN2Y2dhYVFEYXBDMFhDODZ6cnZtcAplc2dVNHZCZGNzWkRrRnJUZHlyaWFCSm85L3FRZmtoU3J0cFV1cGE3T0Yrbzd5MTRWV245Z1lLbjlrWnI4VVVLCjJLYUFVc0xSMWZrRi9LTXA3UGptNnNFcUtLc3NsTXRhQnpvTm5jRnIrSWM4aGwwclpPMEgzVXJDV242STlIcEQKLy9Sd0JKWXFNRElsS1pRVkowOUsweGVjcmNjdjdkdFltcUtzMjNIYXVHbXk4eFl0Q3phSjBPOGVScnpiMERycQptWlNERWJtRzh4YjZsTFM4b2RrQ0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZKTjJxL2FYQjc4Q0E2aEhYTFcxMGxIcVVrNXlNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBTExSUkZqOEpzN3ROZnZ4YUtMaQpqbFIxbWdsNytrYzRtam1ReExBUGx1NnNxQ1BHR1BNcGFqdG9jaHhHdVhOVTQvWEF4SWZ6d0pDNUpBMUZFMGMvCkRWUVhpRy9XQ3FDUkl1ZExFQTY3bkljQ0RJRnR0NmRHbkk0by9VbDluWW82S2RnTjNXVm9RcmNjMTIyMUpIencKM0FqNDdKK0k4WDR1RWppU2pTdDlXQWtwYThFN3ZEelFXelpJZU9yMmZadEx0SHo1dkZaZVNPWVIvNVpWZmtWNAo2ejNXeW13TE8rN3ZjOU5nV0VCeUM1RmJDWG9raWNiOWhlTVhjT0hxelVORERBaTJNdTcvNFNZRXg1Ty84RlpvCmVrMzJHdVpyKzVnRzNLc2hSaU9laHdyQWJWOHJRemJpVUZBcXdLSVozeXUyZXYwSzdqUCt4Y2c0OXo4cHF0N2sKeUxJPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==",
"namespace": "aXN0aW8tc3lzdGVt",
"token": "ZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklsVkpTSEZITTAxd1RWcFZSMlEyZHpCVk16RXphRE5sWkdOdVRuVlJTelJETWxGT1MySjJObG93YXpRaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUpwYzNScGJ5MXplWE4wWlcwaUxDSnJkV0psY201bGRHVnpMbWx2TDNObGNuWnBZMlZoWTJOdmRXNTBMM05sWTNKbGRDNXVZVzFsSWpvaWFYTjBhVzh0Y21WaFpHVnlMWE5sY25acFkyVXRZV05qYjNWdWRDMTBiMnRsYmkxMk5IRmllQ0lzSW10MVltVnlibVYwWlhNdWFXOHZjMlZ5ZG1salpXRmpZMjkxYm5RdmMyVnlkbWxqWlMxaFkyTnZkVzUwTG01aGJXVWlPaUpwYzNScGJ5MXlaV0ZrWlhJdGMyVnlkbWxqWlMxaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXpaWEoyYVdObExXRmpZMjkxYm5RdWRXbGtJam9pTlRobVlUZzRNakl0TlRVM09DMDBNR0pqTFRneFptRXROVFZtTlRka01EZzJObVk1SWl3aWMzVmlJam9pYzNsemRHVnRPbk5sY25acFkyVmhZMk52ZFc1ME9tbHpkR2x2TFhONWMzUmxiVHBwYzNScGJ5MXlaV0ZrWlhJdGMyVnlkbWxqWlMxaFkyTnZkVzUwSW4wLkpSRkEwbVZETm9QMnV1a3lsX0ROMWM4bTdUNm1VS2E5MkNZWmtwdXlQSno1WTdDQ2k2TjQzZTZDSzkySUVuci1QV3NXTkRqTFRqa0FvVWZFZ2gxbFYzMFpOSGEyeXRhUDdKM1hHcnpCWnBCbS1GSDVfbW9uUWRLME9HTE9Vc2hQcUlCU2J0b0RPcmVGVTRxT1k1bk1mV0NtOEEwbFRpNXhjcExyU20xQTVOV0x0QUNMaG5feXVJc0lDc1FyRGg4UFFhS0taMVJReFB2NzQyU0lfbFJsQk5DZV9UamREb1liQWNpWTdSaGJqekFxMkpmWld3NENiUTVrMkhGYVo0Vko3bU1WTGpVVDRaYlgzeXEwTG5BMVBaS2JTRHU4cDlDdVRKTGlpd0VZel91Z2gzQmdZUG1teGhmMVNEay03VlU5UUNYMi1MaHRaMjdJdXh2Q3FOTUVKdw=="
},
"kind": "Secret",
"metadata": {
"annotations": {
"kubernetes.io/service-account.name": "istio-reader-service-account",
"kubernetes.io/service-account.uid": "58fa8822-5578-40bc-81fa-55f57d0866f9"
},
"creationTimestamp": "2025-05-24T16:19:58Z",
"name": "istio-reader-service-account-token-v4qbx",
"namespace": "istio-system",
"resourceVersion": "22946",
"uid": "90037307-b681-43fc-a06a-73f298990204"
},
"type": "kubernetes.io/service-account-token"
}
|
6. istio-reader-service-account의 권한 요약 조회
1
| kubectl rolesum istio-reader-service-account -n istio-system --kubeconfig=./east-kubeconfig
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
| ServiceAccount: istio-system/istio-reader-service-account
Secrets:
• */istio-reader-service-account-token-v4qbx
Policies:
• [CRB] */istio-reader-clusterrole-istio-system ⟶ [CR] */istio-reader-clusterrole-istio-system
Resource Name Exclude Verbs G L W C U P D DC
*.[config.istio.io,security.istio.io,networking.istio.io,authentication.istio.io,rbac.istio.io] [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
customresourcedefinitions.apiextensions.k8s.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
endpoints [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
endpointslices.discovery.k8s.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
namespaces [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
nodes [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
pods [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
replicasets.apps [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
replicationcontrollers [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
secrets [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
serviceexports.multicluster.x-k8s.io [*] [-] [-] ✔ ✔ ✔ ✔ ✖ ✖ ✔ ✖
serviceimports.multicluster.x-k8s.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
services [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
subjectaccessreviews.authorization.k8s.io [*] [-] [-] ✖ ✖ ✖ ✔ ✖ ✖ ✖ ✖
tokenreviews.authentication.k8s.io [*] [-] [-] ✖ ✖ ✖ ✔ ✖ ✖ ✖ ✖
workloadentries.networking.istio.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
• [CRB] */istio-reader-istio-system ⟶ [CR] */istio-reader-istio-system
Resource Name Exclude Verbs G L W C U P D DC
*.[config.istio.io,security.istio.io,networking.istio.io,authentication.istio.io,rbac.istio.io] [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
customresourcedefinitions.apiextensions.k8s.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
endpoints [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
endpointslices.discovery.k8s.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
namespaces [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
nodes [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
pods [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
replicasets.apps [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
replicationcontrollers [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
secrets [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
serviceexports.multicluster.x-k8s.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
serviceimports.multicluster.x-k8s.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
services [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
subjectaccessreviews.authorization.k8s.io [*] [-] [-] ✖ ✖ ✖ ✔ ✖ ✖ ✖ ✖
tokenreviews.authentication.k8s.io [*] [-] [-] ✖ ✖ ✖ ✔ ✖ ✖ ✖ ✖
workloadentries.networking.istio.io [*] [-] [-] ✔ ✔ ✔ ✖ ✖ ✖ ✖ ✖
|
7. 해당 서비스 어카운트로 가능한 작업 목록 확인
1
| keast auth can-i --as=system:serviceaccount:istio-system:istio-reader-service-account --list
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
| Resources Non-Resource URLs Resource Names Verbs
tokenreviews.authentication.k8s.io [] [] [create]
selfsubjectaccessreviews.authorization.k8s.io [] [] [create]
selfsubjectrulesreviews.authorization.k8s.io [] [] [create]
subjectaccessreviews.authorization.k8s.io [] [] [create]
endpoints [] [] [get list watch]
namespaces [] [] [get list watch]
nodes [] [] [get list watch]
pods [] [] [get list watch]
replicationcontrollers [] [] [get list watch]
secrets [] [] [get list watch]
services [] [] [get list watch]
customresourcedefinitions.apiextensions.k8s.io [] [] [get list watch]
replicasets.apps [] [] [get list watch]
*.authentication.istio.io [] [] [get list watch]
*.config.istio.io [] [] [get list watch]
endpointslices.discovery.k8s.io [] [] [get list watch]
*.networking.istio.io [] [] [get list watch]
*.rbac.istio.io [] [] [get list watch]
*.security.istio.io [] [] [get list watch]
serviceexports.multicluster.x-k8s.io [] [] [get watch list create delete]
serviceimports.multicluster.x-k8s.io [] [] [get watch list]
workloadentries.networking.istio.io [] [] [get watch list]
[/.well-known/openid-configuration] [] [get]
[/api/*] [] [get]
[/api] [] [get]
[/apis/*] [] [get]
[/apis] [] [get]
[/healthz] [] [get]
[/healthz] [] [get]
[/livez] [] [get]
[/livez] [] [get]
[/openapi/*] [] [get]
[/openapi] [] [get]
[/openid/v1/jwks] [] [get]
[/readyz] [] [get]
[/readyz] [] [get]
[/version/] [] [get]
[/version/] [] [get]
[/version] [] [get]
[/version] [] [get]
|
8. east 클러스터용 Remote Secret 생성
1
| ieast x create-remote-secret --name="east-cluster"
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| # This file is autogenerated, do not edit.
apiVersion: v1
kind: Secret
metadata:
annotations:
networking.istio.io/cluster: east-cluster
creationTimestamp: null
labels:
istio/multiCluster: "true"
name: istio-remote-secret-east-cluster
namespace: istio-system
stringData:
east-cluster: |
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUMvakNDQWVhZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJMU1EVXlOREV4TVRJek1Gb1hEVE0xTURVeU1qRXhNVEl6TUZvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTlhICkR5Q2F3bGdNdXJ1Q0N3bFlTTkEwS2VTZWdtYUhHSnlYVnc1Y25RTm04ZUErM2E3dWcxR2hlYWUxWm9Hb2g4SlUKVC9laW9IcTM1Wk9zdVNLTExyOWc5YTAvUmpsRnVwVnNnQXltcGcxc3FFNzN2Y2dhYVFEYXBDMFhDODZ6cnZtcAplc2dVNHZCZGNzWkRrRnJUZHlyaWFCSm85L3FRZmtoU3J0cFV1cGE3T0Yrbzd5MTRWV245Z1lLbjlrWnI4VVVLCjJLYUFVc0xSMWZrRi9LTXA3UGptNnNFcUtLc3NsTXRhQnpvTm5jRnIrSWM4aGwwclpPMEgzVXJDV242STlIcEQKLy9Sd0JKWXFNRElsS1pRVkowOUsweGVjcmNjdjdkdFltcUtzMjNIYXVHbXk4eFl0Q3phSjBPOGVScnpiMERycQptWlNERWJtRzh4YjZsTFM4b2RrQ0F3RUFBYU5aTUZjd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0hRWURWUjBPQkJZRUZKTjJxL2FYQjc4Q0E2aEhYTFcxMGxIcVVrNXlNQlVHQTFVZEVRUU8KTUF5Q0NtdDFZbVZ5Ym1WMFpYTXdEUVlKS29aSWh2Y05BUUVMQlFBRGdnRUJBTExSUkZqOEpzN3ROZnZ4YUtMaQpqbFIxbWdsNytrYzRtam1ReExBUGx1NnNxQ1BHR1BNcGFqdG9jaHhHdVhOVTQvWEF4SWZ6d0pDNUpBMUZFMGMvCkRWUVhpRy9XQ3FDUkl1ZExFQTY3bkljQ0RJRnR0NmRHbkk0by9VbDluWW82S2RnTjNXVm9RcmNjMTIyMUpIencKM0FqNDdKK0k4WDR1RWppU2pTdDlXQWtwYThFN3ZEelFXelpJZU9yMmZadEx0SHo1dkZaZVNPWVIvNVpWZmtWNAo2ejNXeW13TE8rN3ZjOU5nV0VCeUM1RmJDWG9raWNiOWhlTVhjT0hxelVORERBaTJNdTcvNFNZRXg1Ty84RlpvCmVrMzJHdVpyKzVnRzNLc2hSaU9laHdyQWJWOHJRemJpVUZBcXdLSVozeXUyZXYwSzdqUCt4Y2c0OXo4cHF0N2sKeUxJPQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg==
server: https://east-control-plane:6443
name: east-cluster
contexts:
- context:
cluster: east-cluster
user: east-cluster
name: east-cluster
current-context: east-cluster
kind: Config
preferences: {}
users:
- name: east-cluster
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlVJSHFHM01wTVpVR2Q2dzBVMzEzaDNlZGNuTnVRSzRDMlFOS2J2NlowazQifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJpc3Rpby1zeXN0ZW0iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoiaXN0aW8tcmVhZGVyLXNlcnZpY2UtYWNjb3VudC10b2tlbi12NHFieCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJpc3Rpby1yZWFkZXItc2VydmljZS1hY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNThmYTg4MjItNTU3OC00MGJjLTgxZmEtNTVmNTdkMDg2NmY5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmlzdGlvLXN5c3RlbTppc3Rpby1yZWFkZXItc2VydmljZS1hY2NvdW50In0.JRFA0mVDNoP2uukyl_DN1c8m7T6mUKa92CYZkpuyPJz5Y7CCi6N43e6CK92IEnr-PWsWNDjLTjkAoUfEgh1lV30ZNHa2ytaP7J3XGrzBZpBm-FH5_monQdK0OGLOUshPqIBSbtoDOreFU4qOY5nMfWCm8A0lTi5xcpLrSm1A5NWLtACLhn_yuIsICsQrDh8PQaKKZ1RQxPv742SI_lRlBNCe_TjdDoYbAciY7RhbjzAq2JfZWw4CbQ5k2HFaZ4VJ7mMVLjUT4ZbX3yq0LnA1PZKbSDu8p9CuTJLiiwEYz_ugh3BgYPmmxhf1SDk-7VU9QCX2-LhtZ27IuxvCqNMEJw
---
|
9. 생성된 Remote Secret 내 JWT 디코딩하여 토큰 클레임 확인
1
| jwt decode eyJhbGciOiJSUzI1NiIsImtpZCI6IlVJSHFHM01wTVpVR2Q2dzBVMzEzaDNlZGNuTnVRSzRDMlFOS2J2NlowazQifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJpc3Rpby1zeXN0ZW0iLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlY3JldC5uYW1lIjoiaXN0aW8tcmVhZGVyLXNlcnZpY2UtYWNjb3VudC10b2tlbi12NHFieCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJpc3Rpby1yZWFkZXItc2VydmljZS1hY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNThmYTg4MjItNTU3OC00MGJjLTgxZmEtNTVmNTdkMDg2NmY5Iiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50OmlzdGlvLXN5c3RlbTppc3Rpby1yZWFkZXItc2VydmljZS1hY2NvdW50In0.JRFA0mVDNoP2uukyl_DN1c8m7T6mUKa92CYZkpuyPJz5Y7CCi6N43e6CK92IEnr-PWsWNDjLTjkAoUfEgh1lV30ZNHa2ytaP7J3XGrzBZpBm-FH5_monQdK0OGLOUshPqIBSbtoDOreFU4qOY5nMfWCm8A0lTi5xcpLrSm1A5NWLtACLhn_yuIsICsQrDh8PQaKKZ1RQxPv742SI_lRlBNCe_TjdDoYbAciY7RhbjzAq2JfZWw4CbQ5k2HFaZ4VJ7mMVLjUT4ZbX3yq0LnA1PZKbSDu8p9CuTJLiiwEYz_ugh3BgYPmmxhf1SDk-7VU9QCX2-LhtZ27IuxvCqNMEJw
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| Token header
------------
{
"alg": "RS256",
"kid": "UIHqG3MpMZUGd6w0U313h3edcnNuQK4C2QNKbv6Z0k4"
}
Token claims
------------
{
"iss": "kubernetes/serviceaccount",
"kubernetes.io/serviceaccount/namespace": "istio-system",
"kubernetes.io/serviceaccount/secret.name": "istio-reader-service-account-token-v4qbx",
"kubernetes.io/serviceaccount/service-account.name": "istio-reader-service-account",
"kubernetes.io/serviceaccount/service-account.uid": "58fa8822-5578-40bc-81fa-55f57d0866f9",
"sub": "system:serviceaccount:istio-system:istio-reader-service-account"
}
|
🌐 원격 클러스터 연결 상태 확인 및 리소스 검증
1. east 클러스터 시크릿을 west에 적용
1
| ieast x create-remote-secret --name="east-cluster" | kwest apply -f -
|
✅ 출력
1
| secret/istio-remote-secret-east-cluster created
|
2. istiod 로그를 통해 클러스터 추가 인식 여부 확인
1
| kwest logs deploy/istiod -n istio-system | grep 'Adding cluster'
|
✅ 출력
1
| 2025-05-24T16:57:47.606922Z info Adding cluster cluster=east-cluster secret=istio-system/istio-remote-secret-east-cluster
|
3. west, east 클러스터의 istio-system 네임스페이스에 존재하는 시크릿 전체 목록 조회
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get secret -n istio-system --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| >> k8s cluster : west <<
NAME TYPE DATA AGE
cacerts Opaque 4 5h5m
default-token-n42mk kubernetes.io/service-account-token 3 5h5m
grafana-token-pn74b kubernetes.io/service-account-token 3 44m
istio-ingressgateway-service-account-token-94z7g kubernetes.io/service-account-token 3 147m
istio-reader-service-account-token-kllhn kubernetes.io/service-account-token 3 147m
istio-remote-secret-east-cluster Opaque 1 49s
istiod-service-account-token-gr2qt kubernetes.io/service-account-token 3 147m
istiod-token-8czdk kubernetes.io/service-account-token 3 147m
kiali-token-vshmr kubernetes.io/service-account-token 3 44m
prometheus-token-7bsqd kubernetes.io/service-account-token 3 44m
>> k8s cluster : east <<
NAME TYPE DATA AGE
cacerts Opaque 4 5h5m
default-token-w86kh kubernetes.io/service-account-token 3 5h5m
grafana-token-wh5xs kubernetes.io/service-account-token 3 37m
istio-ingressgateway-service-account-token-v8qn4 kubernetes.io/service-account-token 3 38m
istio-reader-service-account-token-v4qbx kubernetes.io/service-account-token 3 38m
istiod-service-account-token-9srmr kubernetes.io/service-account-token 3 38m
istiod-token-tj62n kubernetes.io/service-account-token 3 38m
kiali-token-rrb2g kubernetes.io/service-account-token 3 37m
prometheus-token-pvfvx kubernetes.io/service-account-token 3 37m
|
4. west 클러스터에서 Istio Proxy의 CDS/EDS 상태 전체 확인
1
| for i in listener route cluster endpoint; do echo ">> k8s cluster : west - istio-config $i <<"; docker exec -it west-control-plane istioctl proxy-config $i deploy/istio-ingressgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
| >> k8s cluster : west - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 8080 ALL Route: http.8080
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
>> k8s cluster : west - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
http.8080 webapp.istioinaction.io /* webapp-virtualservice.istioinaction
* /stats/prometheus*
* /healthz/ready*
>> k8s cluster : west - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
webapp.istioinaction.svc.cluster.local 80 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> k8s cluster : west - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.10.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.10.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.10.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.10.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.10.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.10.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.10.0.13:8080 HEALTHY OK outbound|80||webapp.istioinaction.svc.cluster.local
10.10.0.2:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.10.0.3:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.3:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.4:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.10.0.4:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.10.0.4:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.10.0.4:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.10.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.10.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.7:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.100.0.69:9411 HEALTHY OK zipkin
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.2:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
5. west에서 catalog 서비스로 향하는 IP (10.20.0.13) 접근 가능 여부 확인
1
| iwest proxy-config endpoint deploy/istio-ingressgateway.istio-system --cluster 'outbound|80||catalog.istioinaction.svc.cluster.local' -o json
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
| [
{
"name": "outbound|80||catalog.istioinaction.svc.cluster.local",
"addedViaApi": true,
"hostStatuses": [
{
"address": {
"socketAddress": {
"address": "10.20.0.13",
"portValue": 3000
}
},
"stats": [
{
"name": "cx_connect_fail"
},
{
"name": "cx_total"
},
{
"name": "rq_error"
},
{
"name": "rq_success"
},
{
"name": "rq_timeout"
},
{
"name": "rq_total"
},
{
"type": "GAUGE",
"name": "cx_active"
},
{
"type": "GAUGE",
"name": "rq_active"
}
],
"healthStatus": {
"edsHealthStatus": "HEALTHY"
},
"weight": 1,
"locality": {}
}
],
"circuitBreakers": {
"thresholds": [
{
"maxConnections": 4294967295,
"maxPendingRequests": 4294967295,
"maxRequests": 4294967295,
"maxRetries": 4294967295
},
{
"priority": "HIGH",
"maxConnections": 1024,
"maxPendingRequests": 1024,
"maxRequests": 1024,
"maxRetries": 3
}
]
},
"observabilityName": "outbound|80||catalog.istioinaction.svc.cluster.local",
"edsServiceName": "outbound|80||catalog.istioinaction.svc.cluster.local"
}
]
|
6. east 클러스터에서 catalog 리소스 상태 확인
(1) east 클러스터의 Istio 프록시 설정 전체 조회
1
| for i in listener route cluster endpoint; do echo ">> k8s cluster : east - istio-config $i <<"; docker exec -it east-control-plane istioctl proxy-config $i deploy/istio-ingressgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
| >> k8s cluster : east - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
>> k8s cluster : east - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
* /stats/prometheus*
* /healthz/ready*
>> k8s cluster : east - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> k8s cluster : east - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
10.20.0.2:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.2:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.4:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.7:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.20.0.7:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.20.0.7:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.20.0.7:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.200.0.162:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.3:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
(2) catalog 관련 클러스터 및 엔드포인트 필터링 조회
1
2
| ieast proxy-config cluster deploy/istio-ingressgateway.istio-system | grep catalog
ieast proxy-config endpoint deploy/istio-ingressgateway.istio-system | grep catalog
|
✅ 출력
1
2
3
| catalog.istioinaction.svc.cluster.local 80 - outbound EDS
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
|
7. west 클러스터에서 catalog, webapp 서비스 및 엔드포인트 확인
1
| kwest get svc,ep -n istioinaction
|
✅ 출력
1
2
3
4
5
6
7
| NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.100.0.103 <none> 80/TCP 29m
service/webapp ClusterIP 10.100.0.165 <none> 80/TCP 29m
NAME ENDPOINTS AGE
endpoints/catalog <none> 29m
endpoints/webapp 10.10.0.13:8080 29m
|
8. east 클러스터에서 catalog 서비스 및 endpoint 확인
1
| keast get svc,ep -n istioinaction
|
✅ 출력
1
2
3
4
5
| NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.200.0.251 <none> 80/TCP 23m
NAME ENDPOINTS AGE
endpoints/catalog 10.20.0.13:3000 23m
|
🧭 SNI 클러스터가 있는 east-west 게이트웨이 설치하기
1. east-west 게이트웨이용 IstioOperator 설정 파일 확인
1
| cat ch12/gateways/cluster-east-eastwest-gateway.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
| apiVersion: install.istio.io/v1alpha1
kind: IstioOperator
metadata:
name: istio-eastwestgateway # IstioOperator 이름은 앞 선 이스티오 설정 이름과 겹치지 않아야 한다
namespace: istio-system
spec:
meshConfig:
accessLogFile: /dev/stdout
profile: empty # empty 프로필은 추가 이스티오 구성 요소를 설치하지 않는다
components:
ingressGateways:
- name: istio-eastwestgateway # 게이트웨이 이름
label:
istio: eastwestgateway
app: istio-eastwestgateway
topology.istio.io/network: east-network
enabled: true
k8s:
env:
- name: ISTIO_META_ROUTER_MODE # sni-dnat 모드는 트래픽을 프록시하는 데 필요한 SNI 클러스터를 추가한다
value: "sni-dnat"
# The network to which traffic is routed
- name: ISTIO_META_REQUESTED_NETWORK_VIEW # 게이트웨이가 트래픽을 라우팅하는 네트워크
value: east-network
service:
ports:
- name: status-port
port: 15021
targetPort: 15021
- name: mtls
port: 15443
targetPort: 15443
- name: tcp-istiod
port: 15012
targetPort: 15012
- name: tcp-webhook
port: 15017
targetPort: 15017
values:
global:
meshID: usmesh # 메시, 클러스터, 네트워크 식별 정보
multiCluster:
clusterName: east-cluster
network: east-network
|
2. 설치 전 확인
(1) east/west 클러스터의 Istio 구성 Pod 상태 확인
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get pod -n istio-system -l istio.io/rev=default --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
| >> k8s cluster : west <<
NAME READY STATUS RESTARTS AGE
istio-ingressgateway-5db74c978c-7k7tr 1/1 Running 25 (85m ago) 3h3m
istiod-5585445f4c-gphfz 1/1 Running 1 (82m ago) 3h3m
>> k8s cluster : east <<
NAME READY STATUS RESTARTS AGE
istio-eastwestgateway-866794c798-tlrvs 1/1 Running 0 24m
istio-ingressgateway-7f6f8f8d99-cg2t4 1/1 Running 0 74m
istiod-85976468f-4ctv8 1/1 Running 0 75m
|
(2) east/west 클러스터의 IstioOperator 리소스 존재 여부 확인
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get IstioOperator -n istio-system --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
| >> k8s cluster : west <<
NAME REVISION STATUS AGE
installed-state-istio-controlplane 82m
>> k8s cluster : east <<
NAME REVISION STATUS AGE
installed-state-istio-controlplane 75m
installed-state-istio-eastwestgateway 24m
|
(3) west 클러스터의 ingressgateway에 반영된 Istio 프록시 설정 점검
1
| for i in listener route cluster endpoint; do echo ">> k8s cluster : west - istio-config $i <<"; docker exec -it west-control-plane istioctl proxy-config $i deploy/istio-ingressgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
| >> k8s cluster : west - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 8080 ALL Route: http.8080
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
>> k8s cluster : west - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
http.8080 webapp.istioinaction.io /* webapp-virtualservice.istioinaction
* /stats/prometheus*
* /healthz/ready*
>> k8s cluster : west - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15012 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15017 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
webapp.istioinaction.svc.cluster.local 80 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> k8s cluster : west - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.10.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.10.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.10.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.10.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.10.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.10.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.10.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.10.0.13:8080 HEALTHY OK outbound|80||webapp.istioinaction.svc.cluster.local
10.10.0.2:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.10.0.3:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.3:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.4:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.10.0.4:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.10.0.4:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.10.0.4:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.10.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.10.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.10.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.10.0.7:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.7:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.10.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.100.0.69:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.2:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
172.18.255.202:15443 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
3. east-west 게이트웨이 설치용 IstioOperator YAML 파일 컨트롤 플레인에 복사 후 IstioOperator 설치
1
2
| docker cp ./ch12/gateways/cluster-east-eastwest-gateway.yaml east-control-plane:/cluster-east-eastwest-gateway.yaml
ieast install -f /cluster-east-eastwest-gateway.yaml --set values.global.proxy.privileged=true -y
|
✅ 출력
1
2
3
4
| Successfully copied 3.07kB to east-control-plane:/cluster-east-eastwest-gateway.yaml
✔ Ingress gateways installed
✔ Installation complete
Thank you for installing Istio 1.17. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/hMHGiwZHPU7UQRWe9
|
4. east 클러스터에 installed-state-istio-eastwestgateway 리소스 생성 여부 확인
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get IstioOperator -n istio-system --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
| >> k8s cluster : west <<
NAME REVISION STATUS AGE
installed-state-istio-controlplane 84m
>> k8s cluster : east <<
NAME REVISION STATUS AGE
installed-state-istio-controlplane 77m
installed-state-istio-eastwestgateway 27m
|
5. east 클러스터의 istio-eastwestgateway Pod 정상 실행 확인
1
| for i in west east; do echo ">> k8s cluster : $i <<"; kubectl get pod -n istio-system -l istio.io/rev=default --kubeconfig=./$i-kubeconfig; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
| >> k8s cluster : west <<
NAME READY STATUS RESTARTS AGE
istio-ingressgateway-5db74c978c-7k7tr 1/1 Running 25 (88m ago) 3h6m
istiod-5585445f4c-gphfz 1/1 Running 1 (85m ago) 3h6m
>> k8s cluster : east <<
NAME READY STATUS RESTARTS AGE
istio-eastwestgateway-866794c798-tlrvs 1/1 Running 0 27m
istio-ingressgateway-7f6f8f8d99-cg2t4 1/1 Running 0 77m
istiod-85976468f-4ctv8 1/1 Running 0 78m
|
6. 설치된 east-west 게이트웨이 리소스의 설정 YAML 확인
1
| keast get IstioOperator -n istio-system installed-state-istio-eastwestgateway -o yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| ...
ingressGateways:
- enabled: true
k8s:
env:
- name: ISTIO_META_ROUTER_MODE
value: sni-dnat
- name: ISTIO_META_REQUESTED_NETWORK_VIEW
value: east-network
service:
ports:
- name: status-port
port: 15021
targetPort: 15021
- name: mtls
port: 15443
targetPort: 15443
- name: tcp-istiod
port: 15012
targetPort: 15012
- name: tcp-webhook
port: 15017
targetPort: 15017
label:
app: istio-eastwestgateway
istio: eastwestgateway
topology.istio.io/network: east-network
name: istio-eastwestgateway
- enabled: false
name: istio-ingressgateway
...
|
7. east 클러스터 전체 프록시 동기화 상태 확인 (proxy-status)
✅ 출력
1
2
3
4
| NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
catalog-6cf4b97d-dd2dv.istioinaction east-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-85976468f-4ctv8 1.17.8
istio-eastwestgateway-866794c798-tlrvs.istio-system east-cluster SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-85976468f-4ctv8 1.17.8
istio-ingressgateway-7f6f8f8d99-cg2t4.istio-system east-cluster SYNCED SYNCED SYNCED NOT SENT NOT SENT istiod-85976468f-4ctv8 1.17.8
|
8. east 클러스터의 ingressgateway 프록시 구성 정보 확인
east에 istio-ingressgateway에 istio-config 정보 확인 : west 의 CDS/EDS 모두 알고 있음
1
| for i in listener route cluster endpoint; do echo ">> east k8s cluster : ingressgateway - istio-config $i <<"; docker exec -it east-control-plane istioctl proxy-config $i deploy/istio-ingressgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
| >> east k8s cluster : ingressgateway - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
>> east k8s cluster : ingressgateway - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
* /stats/prometheus*
* /healthz/ready*
>> east k8s cluster : ingressgateway - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15012 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15017 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> east k8s cluster : ingressgateway - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
10.20.0.14:15012 HEALTHY OK outbound|15012||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15017 HEALTHY OK outbound|15017||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15021 HEALTHY OK outbound|15021||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15443 HEALTHY OK outbound|15443||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.2:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.2:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.4:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.7:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.20.0.7:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.20.0.7:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.20.0.7:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.200.0.162:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.3:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
east에 istio-eastwestgateway 에 istio-config 정보 확인 : webapp(CDS) OK, west에 EDS 아직 모름
1
| for i in listener route cluster endpoint; do echo ">> east k8s cluster : eastwestgateway - istio-config $i <<"; docker exec -it east-control-plane istioctl proxy-config $i deploy/istio-eastwestgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
| >> east k8s cluster : eastwestgateway - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
0.0.0.0 15443 SNI: outbound_.9411_._.zipkin.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9411_._.zipkin.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9411_._.jaeger-collector.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9411_._.jaeger-collector.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9153_._.kube-dns.kube-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9153_._.kube-dns.kube-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9090_._.prometheus.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9090_._.prometheus.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9090_._.kiali.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9090_._.kiali.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.80_._.tracing.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.80_._.tracing.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.80_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.80_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.80_._.catalog.istioinaction.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.80_._.catalog.istioinaction.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.8080_._.kube-ops-view.kube-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.8080_._.kube-ops-view.kube-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.53_._.kube-dns.kube-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.53_._.kube-dns.kube-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.metallb-webhook-service.metallb-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.metallb-webhook-service.metallb-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.kubernetes.default.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.kubernetes.default.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.31400_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.31400_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.3000_._.grafana.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.3000_._.grafana.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.20001_._.kiali.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.20001_._.kiali.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.16685_._.tracing.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.16685_._.tracing.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15443_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15443_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15443_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15443_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15021_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15021_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15021_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15021_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15017_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15017_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15014_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15014_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15012_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15012_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15012_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15012_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15010_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15010_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.14268_._.jaeger-collector.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.14268_._.jaeger-collector.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.14250_._.jaeger-collector.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.14250_._.jaeger-collector.istio-system.svc.cluster.local
>> east k8s cluster : eastwestgateway - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
* /stats/prometheus*
* /healthz/ready*
>> east k8s cluster : eastwestgateway - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15012 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15017 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
outbound_.14250_._.jaeger-collector.istio-system.svc.cluster.local - - - EDS
outbound_.14268_._.jaeger-collector.istio-system.svc.cluster.local - - - EDS
outbound_.15010_._.istiod.istio-system.svc.cluster.local - - - EDS
outbound_.15012_._.istio-eastwestgateway.istio-system.svc.cluster.local - - - EDS
outbound_.15012_._.istiod.istio-system.svc.cluster.local - - - EDS
outbound_.15014_._.istiod.istio-system.svc.cluster.local - - - EDS
outbound_.15017_._.istio-eastwestgateway.istio-system.svc.cluster.local - - - EDS
outbound_.15021_._.istio-eastwestgateway.istio-system.svc.cluster.local - - - EDS
outbound_.15021_._.istio-ingressgateway.istio-system.svc.cluster.local - - - EDS
outbound_.15443_._.istio-eastwestgateway.istio-system.svc.cluster.local - - - EDS
outbound_.15443_._.istio-ingressgateway.istio-system.svc.cluster.local - - - EDS
outbound_.16685_._.tracing.istio-system.svc.cluster.local - - - EDS
outbound_.20001_._.kiali.istio-system.svc.cluster.local - - - EDS
outbound_.3000_._.grafana.istio-system.svc.cluster.local - - - EDS
outbound_.31400_._.istio-ingressgateway.istio-system.svc.cluster.local - - - EDS
outbound_.443_._.istio-ingressgateway.istio-system.svc.cluster.local - - - EDS
outbound_.443_._.istiod.istio-system.svc.cluster.local - - - EDS
outbound_.443_._.kubernetes.default.svc.cluster.local - - - EDS
outbound_.443_._.metallb-webhook-service.metallb-system.svc.cluster.local - - - EDS
outbound_.53_._.kube-dns.kube-system.svc.cluster.local - - - EDS
outbound_.8080_._.kube-ops-view.kube-system.svc.cluster.local - - - EDS
outbound_.80_._.catalog.istioinaction.svc.cluster.local - - - EDS
outbound_.80_._.istio-ingressgateway.istio-system.svc.cluster.local - - - EDS
outbound_.80_._.tracing.istio-system.svc.cluster.local - - - EDS
outbound_.9090_._.kiali.istio-system.svc.cluster.local - - - EDS
outbound_.9090_._.prometheus.istio-system.svc.cluster.local - - - EDS
outbound_.9153_._.kube-dns.kube-system.svc.cluster.local - - - EDS
outbound_.9411_._.jaeger-collector.istio-system.svc.cluster.local - - - EDS
outbound_.9411_._.zipkin.istio-system.svc.cluster.local - - - EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> east k8s cluster : eastwestgateway - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound_.80_._.catalog.istioinaction.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
10.20.0.14:15012 HEALTHY OK outbound|15012||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15017 HEALTHY OK outbound|15017||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15021 HEALTHY OK outbound|15021||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15443 HEALTHY OK outbound|15443||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.2:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.2:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.4:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.7:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.20.0.7:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.20.0.7:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.20.0.7:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.200.0.162:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.3:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
9. west 클러스터의 프록시 동기화 상태 확인 (proxy-status)
✅ 출력
1
2
3
| NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
istio-ingressgateway-5db74c978c-7k7tr.istio-system west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-5585445f4c-gphfz 1.17.8
webapp-5c8b4fff64-rzp6q.istioinaction west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-5585445f4c-gphfz 1.17.8
|
10. catalog 서비스에 대한 SNI 기반 라우팅 설정 확인
1
| iwest proxy-config cluster deploy/istio-ingressgateway.istio-system --fqdn catalog.istioinaction.svc.cluster.local -o json | grep sni
|
✅ 출력
1
| "sni": "outbound_.80_._.catalog.istioinaction.svc.cluster.local"
|
11. catalog 서비스에 대한 실제 endpoint 정보 확인
1
| iwest proxy-config endpoint deploy/istio-ingressgateway.istio-system | grep istioinaction
|
✅ 출력
1
2
| 10.10.0.13:8080 HEALTHY OK outbound|80||webapp.istioinaction.svc.cluster.local
172.18.255.202:15443 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
|
12. east 클러스터에서 eastwestgateway의 External-IP 및 포트 확인
1
| keast get svc,ep -n istio-system istio-eastwestgateway
|
✅ 출력
1
2
3
4
5
| NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/istio-eastwestgateway LoadBalancer 10.200.0.64 172.18.255.202 15021:30177/TCP,15443:30700/TCP,15012:31464/TCP,15017:32767/TCP 8m30s
NAME ENDPOINTS AGE
endpoints/istio-eastwestgateway 10.20.0.14:15021,10.20.0.14:15017,10.20.0.14:15012 + 1 more... 8m30s
|
13. west 클러스터의 webapp 프록시가 catalog endpoint 인식하는지 확인
1
| iwest proxy-config endpoint deploy/webapp.istioinaction | grep istioinaction
|
✅ 출력
1
2
| 10.10.0.13:8080 HEALTHY OK outbound|80||webapp.istioinaction.svc.cluster.local
172.18.255.202:15443 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
|
14. stub service의 endpoint 미존재 확인 (catalog = <none>), webapp은 정상
1
| kwest get svc,ep -n istioinaction
|
✅ 출력
1
2
3
4
5
6
7
| NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.100.0.103 <none> 80/TCP 46m
service/webapp ClusterIP 10.100.0.165 <none> 80/TCP 46m
NAME ENDPOINTS AGE
endpoints/catalog <none> 46m
endpoints/webapp 10.10.0.13:8080 46m
|
15. webapp 컨테이너에서 catalog DNS 주소로 curl 테스트 실행
1
| kwest exec -it deploy/webapp -c istio-proxy -n istioinaction -- curl catalog.istioinaction.svc.cluster.local -v
|
✅ 출력
1
2
3
4
5
6
| * Trying 10.100.0.103:80...
* connect to 10.100.0.103 port 80 failed: Connection refused
* Failed to connect to catalog.istioinaction.svc.cluster.local port 80 after 10 ms: Connection refused
* Closing connection 0
curl: (7) Failed to connect to catalog.istioinaction.svc.cluster.local port 80 after 10 ms: Connection refused
command terminated with exit code 7
|
🔁 SNI 자동 통과를 통한 클러스터 간 트래픽 라우팅 설정
1. SNI 자동 통과 게이트웨이 리소스 정의
1
| cat ch12/gateways/expose-services.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: cross-network-gateway
namespace: istio-system
spec:
selector:
istio: eastwestgateway
servers:
- port:
number: 15443
name: tls
protocol: TLS
tls:
mode: AUTO_PASSTHROUGH
hosts:
- "*.local"
|
2. east 클러스터에 cross-network-gateway 리소스 적용
1
2
3
4
| keast apply -n istio-system -f ch12/gateways/expose-services.yaml
# 결과
gateway.networking.istio.io/cross-network-gateway creat
|
3. gateway 리소스가 정상적으로 생성되었는지 확인
✅ 출력
1
2
| NAMESPACE NAME AGE
istio-system gateway.networking.istio.io/cross-network-gateway 26s
|
4. west 클러스터의 catalog stub 서비스 상태 점검
1
| kwest get svc,ep -n istioinaction
|
✅ 출력
1
2
3
4
5
6
7
| NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/catalog ClusterIP 10.100.0.103 <none> 80/TCP 66m
service/webapp ClusterIP 10.100.0.165 <none> 80/TCP 66m
NAME ENDPOINTS AGE
endpoints/catalog <none> 66m
endpoints/webapp 10.10.0.13:8080 66m
|
5. webapp pod 내부에서 catalog 서비스로 curl 요청 시도
1
| kwest exec -it deploy/webapp -c istio-proxy -n istioinaction -- curl catalog.istioinaction.svc.cluster.local -v
|
✅ 출력
1
2
3
4
5
6
7
|
* Trying 10.100.0.103:80...
* connect to 10.100.0.103 port 80 failed: Connection refused
* Failed to connect to catalog.istioinaction.svc.cluster.local port 80 after 10 ms: Connection refused
* Closing connection 0
curl: (7) Failed to connect to catalog.istioinaction.svc.cluster.local port 80 after 10 ms: Connection refused
command terminated with exit code 7
|
6. east 클러스터의 ingressgateway에 대한 listener/route/cluster/endpoint 확인
1
| for i in listener route cluster endpoint; do echo ">> east k8s cluster : ingressgateway - istio-config $i <<"; docker exec -it east-control-plane istioctl proxy-config $i deploy/istio-ingressgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
| >> east k8s cluster : ingressgateway - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
>> east k8s cluster : ingressgateway - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
* /stats/prometheus*
* /healthz/ready*
>> east k8s cluster : ingressgateway - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15012 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15017 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> east k8s cluster : ingressgateway - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
10.20.0.14:15012 HEALTHY OK outbound|15012||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15017 HEALTHY OK outbound|15017||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15021 HEALTHY OK outbound|15021||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15443 HEALTHY OK outbound|15443||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.2:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.2:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.4:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.7:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.20.0.7:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.20.0.7:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.20.0.7:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.200.0.162:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.3:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
7. east 클러스터의 eastwestgateway cluster 및 endpoint 구성 확인
1
| for i in listener route cluster endpoint; do echo ">> east k8s cluster : eastwestgateway - istio-config $i <<"; docker exec -it east-control-plane istioctl proxy-config $i deploy/istio-eastwestgateway.istio-system; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
| >> east k8s cluster : eastwestgateway - istio-config listener <<
ADDRESS PORT MATCH DESTINATION
0.0.0.0 15021 ALL Inline Route: /healthz/ready*
0.0.0.0 15090 ALL Inline Route: /stats/prometheus*
0.0.0.0 15443 SNI: outbound_.9411_._.zipkin.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9411_._.zipkin.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9411_._.jaeger-collector.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9411_._.jaeger-collector.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9153_._.kube-dns.kube-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9153_._.kube-dns.kube-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9090_._.prometheus.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9090_._.prometheus.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.9090_._.kiali.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.9090_._.kiali.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.80_._.tracing.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.80_._.tracing.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.80_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.80_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.80_._.catalog.istioinaction.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.80_._.catalog.istioinaction.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.8080_._.kube-ops-view.kube-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.8080_._.kube-ops-view.kube-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.53_._.kube-dns.kube-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.53_._.kube-dns.kube-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.metallb-webhook-service.metallb-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.metallb-webhook-service.metallb-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.kubernetes.default.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.kubernetes.default.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.443_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.443_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.31400_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.31400_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.3000_._.grafana.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.3000_._.grafana.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.20001_._.kiali.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.20001_._.kiali.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.16685_._.tracing.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.16685_._.tracing.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15443_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15443_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15443_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15443_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15021_._.istio-ingressgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15021_._.istio-ingressgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15021_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15021_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15017_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15017_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15014_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15014_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15012_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15012_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15012_._.istio-eastwestgateway.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15012_._.istio-eastwestgateway.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.15010_._.istiod.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.15010_._.istiod.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.14268_._.jaeger-collector.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.14268_._.jaeger-collector.istio-system.svc.cluster.local
0.0.0.0 15443 SNI: outbound_.14250_._.jaeger-collector.istio-system.svc.cluster.local; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2 Cluster: outbound_.14250_._.jaeger-collector.istio-system.svc.cluster.local
>> east k8s cluster : eastwestgateway - istio-config route <<
NAME DOMAINS MATCH VIRTUAL SERVICE
* /stats/prometheus*
* /healthz/ready*
>> east k8s cluster : eastwestgateway - istio-config cluster <<
SERVICE FQDN PORT SUBSET DIRECTION TYPE DESTINATION RULE
BlackHoleCluster - - - STATIC
agent - - - STATIC
catalog.istioinaction.svc.cluster.local 80 - outbound EDS
grafana.istio-system.svc.cluster.local 3000 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15012 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15017 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-eastwestgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 80 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15021 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 15443 - outbound EDS
istio-ingressgateway.istio-system.svc.cluster.local 31400 - outbound EDS
istiod.istio-system.svc.cluster.local 443 - outbound EDS
istiod.istio-system.svc.cluster.local 15010 - outbound EDS
istiod.istio-system.svc.cluster.local 15012 - outbound EDS
istiod.istio-system.svc.cluster.local 15014 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 9411 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14250 - outbound EDS
jaeger-collector.istio-system.svc.cluster.local 14268 - outbound EDS
kiali.istio-system.svc.cluster.local 9090 - outbound EDS
kiali.istio-system.svc.cluster.local 20001 - outbound EDS
kube-dns.kube-system.svc.cluster.local 53 - outbound EDS
kube-dns.kube-system.svc.cluster.local 9153 - outbound EDS
kube-ops-view.kube-system.svc.cluster.local 8080 - outbound EDS
kubernetes.default.svc.cluster.local 443 - outbound EDS
metallb-webhook-service.metallb-system.svc.cluster.local 443 - outbound EDS
prometheus.istio-system.svc.cluster.local 9090 - outbound EDS
prometheus_stats - - - STATIC
sds-grpc - - - STATIC
tracing.istio-system.svc.cluster.local 80 - outbound EDS
tracing.istio-system.svc.cluster.local 16685 - outbound EDS
xds-grpc - - - STATIC
zipkin - - - STRICT_DNS
zipkin.istio-system.svc.cluster.local 9411 - outbound EDS
>> east k8s cluster : eastwestgateway - istio-config endpoint <<
ENDPOINT STATUS OUTLIER CHECK CLUSTER
10.20.0.10:9411 HEALTHY OK outbound|9411||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:9411 HEALTHY OK outbound|9411||zipkin.istio-system.svc.cluster.local
10.20.0.10:14250 HEALTHY OK outbound|14250||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:14268 HEALTHY OK outbound|14268||jaeger-collector.istio-system.svc.cluster.local
10.20.0.10:16685 HEALTHY OK outbound|16685||tracing.istio-system.svc.cluster.local
10.20.0.10:16686 HEALTHY OK outbound|80||tracing.istio-system.svc.cluster.local
10.20.0.11:9090 HEALTHY OK outbound|9090||kiali.istio-system.svc.cluster.local
10.20.0.11:20001 HEALTHY OK outbound|20001||kiali.istio-system.svc.cluster.local
10.20.0.12:9090 HEALTHY OK outbound|9090||prometheus.istio-system.svc.cluster.local
10.20.0.13:3000 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
10.20.0.14:15012 HEALTHY OK outbound|15012||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15017 HEALTHY OK outbound|15017||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15021 HEALTHY OK outbound|15021||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.14:15443 HEALTHY OK outbound|15443||istio-eastwestgateway.istio-system.svc.cluster.local
10.20.0.2:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.2:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.4:8080 HEALTHY OK outbound|8080||kube-ops-view.kube-system.svc.cluster.local
10.20.0.5:9443 HEALTHY OK outbound|443||metallb-webhook-service.metallb-system.svc.cluster.local
10.20.0.6:53 HEALTHY OK outbound|53||kube-dns.kube-system.svc.cluster.local
10.20.0.6:9153 HEALTHY OK outbound|9153||kube-dns.kube-system.svc.cluster.local
10.20.0.7:15010 HEALTHY OK outbound|15010||istiod.istio-system.svc.cluster.local
10.20.0.7:15012 HEALTHY OK outbound|15012||istiod.istio-system.svc.cluster.local
10.20.0.7:15014 HEALTHY OK outbound|15014||istiod.istio-system.svc.cluster.local
10.20.0.7:15017 HEALTHY OK outbound|443||istiod.istio-system.svc.cluster.local
10.20.0.8:8080 HEALTHY OK outbound|80||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:8443 HEALTHY OK outbound|443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15021 HEALTHY OK outbound|15021||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:15443 HEALTHY OK outbound|15443||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.8:31400 HEALTHY OK outbound|31400||istio-ingressgateway.istio-system.svc.cluster.local
10.20.0.9:3000 HEALTHY OK outbound|3000||grafana.istio-system.svc.cluster.local
10.200.0.162:9411 HEALTHY OK zipkin
127.0.0.1:15000 HEALTHY OK prometheus_stats
127.0.0.1:15020 HEALTHY OK agent
172.18.0.3:6443 HEALTHY OK outbound|443||kubernetes.default.svc.cluster.local
unix://./etc/istio/proxy/XDS HEALTHY OK xds-grpc
unix://./var/run/secrets/workload-spiffe-uds/socket HEALTHY OK sds-grpc
|
8. west 클러스터의 ingressgateway 및 webapp proxy 상태 점검
✅ 출력
1
2
3
| NAME CLUSTER CDS LDS EDS RDS ECDS ISTIOD VERSION
istio-ingressgateway-5db74c978c-7k7tr.istio-system west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-5585445f4c-gphfz 1.17.8
webapp-5c8b4fff64-rzp6q.istioinaction west-cluster SYNCED SYNCED SYNCED SYNCED NOT SENT istiod-5585445f4c-gphfz 1.17.8
|
클러스터 간 워크로드 디스커버리 검증하기
1. east 클러스터의 eastwestgateway 외부 IP 확인
1
| keast -n istio-system get svc istio-eastwestgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}'
|
✅ 출력
2. west 클러스터에서 catalog 클러스터 IP 확인
1
| iwest pc endpoints deploy/webapp.istioinaction | grep catalog
|
✅ 출력
1
| 172.18.255.202:15443 HEALTHY OK outbound|80||catalog.istioinaction.svc.cluster.local
|
3. west 클러스터 ingressgateway 외부 IP 확인
1
| kwest get svc -n istio-system istio-ingressgateway
|
✅ 출력
1
2
| NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-ingressgateway LoadBalancer 10.100.0.246 172.18.255.101 15021:30545/TCP,80:30000/TCP,443:31928/TCP,31400:31839/TCP,15443:30833/TCP 178m
|
4. west ingressgateway IP 변수로 저장 및 출력
1
2
| EXT_IP=$(kwest -n istio-system get svc istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
echo $EXT_IP
|
✅ 출력
5. 외부 curl 요청으로 webapp → catalog 응답 확인
1
| docker exec -it mypc curl -s -H "Host: webapp.istioinaction.io" http://$EXT_IP/api/catalog | jq
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| [
{
"id": 1,
"color": "amber",
"department": "Eyewear",
"name": "Elinor Glasses",
"price": "282.00"
},
{
"id": 2,
"color": "cyan",
"department": "Clothing",
"name": "Atlas Shirt",
"price": "127.00"
},
{
"id": 3,
"color": "teal",
"department": "Clothing",
"name": "Small Metal Shoes",
"price": "232.00"
},
{
"id": 4,
"color": "red",
"department": "Watches",
"name": "Red Dragon Watch",
"price": "232.00"
}
]
|
6. 반복 curl 요청 및 timestamp 출력 (반복 확인)
1
2
3
| alias kwest='kubectl --kubeconfig=./west-kubeconfig'
EXT_IP=$(kwest -n istio-system get svc istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
while true; do docker exec -it mypc curl -s -H "Host: webapp.istioinaction.io" http://$EXT_IP/api/catalog ; date "+%Y-%m-%d %H:%M:%S" ; sleep 1; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| [{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]2025-05-25 02:42:43
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]2025-05-25 02:42:44
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]2025-05-25 02:42:45
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]2025-05-25 02:42:46
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]2025-05-25 02:42:47
...
|
7. west 클러스터 Kiali 트래픽 흐름 확인
8. east-cluster Kiali 트래픽 흐름 확인 (mTLS 포함, TCP+HTTP 이중 확인)
9. west 클러스터 Jaeger 트레이싱 정보 확인
10. east 클러스터 Jaeger 트레이싱 정보 확인
11. west istio-ingressgateway 로그 실시간 확인
1
| kwest logs -n istio-system -l app=istio-ingressgateway -f
|
✅ 출력
1
2
3
4
5
| [2025-05-24T18:01:10.027Z] "GET /api/catalog HTTP/1.1" 200 - via_upstream - "-" 0 357 7 7 "172.18.0.100" "curl/8.7.1" "bd3dde36-8f97-9a2f-91da-1f49300ca2cb" "webapp.istioinaction.io" "10.10.0.13:8080" outbound|80||webapp.istioinaction.svc.cluster.local 10.10.0.7:54220 10.10.0.7:8080 172.18.0.100:39394 - -
[2025-05-24T18:01:11.105Z] "GET /api/catalog HTTP/1.1" 200 - via_upstream - "-" 0 357 7 7 "172.18.0.100" "curl/8.7.1" "aeca0d7c-d6bc-9c3d-8e11-360e2c3d6e36" "webapp.istioinaction.io" "10.10.0.13:8080" outbound|80||webapp.istioinaction.svc.cluster.local 10.10.0.7:54208 10.10.0.7:8080 172.18.0.100:39410 - -
[2025-05-24T18:01:12.170Z] "GET /api/catalog HTTP/1.1" 200 - via_upstream - "-" 0 357 12 12 "172.18.0.100" "curl/8.7.1" "1402c09c-930a-96c1-815d-fbec781dc6b2" "webapp.istioinaction.io" "10.10.0.13:8080" outbound|80||webapp.istioinaction.svc.cluster.local 10.10.0.7:54208 10.10.0.7:8080 172.18.0.100:39422 - -
[2025-05-24T18:01:13.253Z] "GET /api/catalog HTTP/1.1" 200 - via_upstream - "-" 0 357 6 6 "172.18.0.100" "curl/8.7.1" "f1fa47b0-b9d9-93db-a9e2-6f263accde35" "webapp.istioinaction.io" "10.10.0.13:8080" outbound|80||webapp.istioinaction.svc.cluster.local 10.10.0.7:57282 10.10.0.7:8080 172.18.0.100:39432 - -
...
|
12. webapp → catalog 요청 로그 확인 (istio-proxy container)
1
| kwest logs -n istioinaction -l app=webapp -c istio-proxy -f
|
✅ 출력
1
2
3
4
5
6
| [2025-05-24T18:02:18.402Z] "GET /items HTTP/1.1" 200 - via_upstream - "-" 0 502 2 2 "172.18.0.100" "beegoServer" "1086c306-0cb7-997c-820f-8387269bd88d" "catalog.istioinaction.svc.cluster.local:80" "172.18.255.202:15443" outbound|80||catalog.istioinaction.svc.cluster.local 10.10.0.13:59466 10.100.0.103:80 172.18.0.100:0 - default
[2025-05-24T18:02:18.400Z] "GET /api/catalog HTTP/1.1" 200 - via_upstream - "-" 0 357 5 4 "172.18.0.100" "curl/8.7.1" "1086c306-0cb7-997c-820f-8387269bd88d" "webapp.istioinaction.io" "10.10.0.13:8080" inbound|8080|| 127.0.0.6:59803 10.10.0.13:8080 172.18.0.100:0 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
[2025-05-24T18:02:19.493Z] "GET /items HTTP/1.1" 200 - via_upstream - "-" 0 502 3 3 "172.18.0.100" "beegoServer" "c44cf529-3d68-93a1-bae1-9a3e79f430c6" "catalog.istioinaction.svc.cluster.local:80" "172.18.255.202:15443" outbound|80||catalog.istioinaction.svc.cluster.local 10.10.0.13:60216 10.100.0.103:80 172.18.0.100:0 - default
[2025-05-24T18:02:19.490Z] "GET /api/catalog HTTP/1.1" 200 - via_upstream - "-" 0 357 6 6 "172.18.0.100" "curl/8.7.1" "c44cf529-3d68-93a1-bae1-9a3e79f430c6" "webapp.istioinaction.io" "10.10.0.13:8080" inbound|8080|| 127.0.0.6:59803 10.10.0.13:8080 172.18.0.100:0 outbound_.80_._.webapp.istioinaction.svc.cluster.local default
[2025-05-24T18:02:20.558Z] "GET /items HTTP/1.1" 200 - via_upstream - "-" 0 502 2 2 "172.18.0.100" "beegoServer" "2728fb18-9a59-91ca-af40-e3278daf3a73" "catalog.istioinaction.svc.cluster.local:80" "172.18.255.202:15443" outbound|80||catalog.istioinaction.svc.cluster.local 10.10.0.13:59466 10.100.0.103:80 172.18.0.100:0 - default
...
|
13. webapp 자체 로그 출력 (웹 애플리케이션 로그)
1
| kwest logs -n istioinaction -l app=webapp -c webapp -f
|
✅ 출력
1
2
3
4
5
6
7
8
| 2025/05/24 18:03:01.289 [M] [router.go:1014] 172.18.0.100 - - [24/May/2025 06:03:01] "GET /api/catalog HTTP/1.1 200 0" 0.005905 curl/8.7.1
2025/05/24 18:03:02.344 [M] [router.go:1014] 172.18.0.100 - - [24/May/2025 06:03:02] "GET /api/catalog HTTP/1.1 200 0" 0.004955 curl/8.7.1
2025/05/24 18:03:03.417 [M] [router.go:1014] 172.18.0.100 - - [24/May/2025 06:03:03] "GET /api/catalog HTTP/1.1 200 0" 0.011300 curl/8.7.1
2025/05/24 18:03:04.491 [M] [router.go:1014] 172.18.0.100 - - [24/May/2025 06:03:04] "GET /api/catalog HTTP/1.1 200 0" 0.004346 curl/8.7.1
...
|
14. east 클러스터 istio-eastwestgateway 디버그 레벨 설정
1
| keast exec -it -n istio-system deploy/istio-eastwestgateway -- curl -X POST http://localhost:15000/logging\?level\=debug
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
| active loggers:
admin: debug
alternate_protocols_cache: debug
aws: debug
assert: debug
backtrace: debug
cache_filter: debug
client: debug
config: debug
connection: debug
conn_handler: debug
decompression: debug
dns: debug
dubbo: debug
envoy_bug: debug
ext_authz: debug
ext_proc: debug
rocketmq: debug
file: debug
filter: debug
forward_proxy: debug
grpc: debug
happy_eyeballs: debug
hc: debug
health_checker: debug
http: debug
http2: debug
hystrix: debug
init: debug
io: debug
jwt: debug
kafka: debug
key_value_store: debug
lua: debug
main: debug
matcher: debug
misc: debug
mongo: debug
multi_connection: debug
oauth2: debug
quic: debug
quic_stream: debug
pool: debug
rate_limit_quota: debug
rbac: debug
rds: debug
redis: debug
router: debug
runtime: debug
stats: debug
secret: debug
tap: debug
testing: debug
thrift: debug
tracing: debug
upstream: debug
udp: debug
wasm: debug
websocket: debug
|
15. east 클러스터 istio-eastwestgateway 로그 실시간 확인
1
| keast logs -n istio-system -l app=istio-eastwestgateway -f
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| ...
2025-05-24T18:10:55.812112Z debug envoy http external/envoy/source/common/http/conn_manager_impl.cc:1032 [C1851][S429397187266806652] request end stream thread=61
2025-05-24T18:10:55.812179Z debug envoy connection external/envoy/source/common/network/connection_impl.h:92 [C1851] current connecting state: false thread=61
2025-05-24T18:10:55.812244Z debug envoy router external/envoy/source/common/router/router.cc:470 [C1851][S429397187266806652] cluster 'agent' match for URL '/healthz/ready' thread=61
2025-05-24T18:10:55.812300Z debug envoy router external/envoy/source/common/router/router.cc:678 [C1851][S429397187266806652] router decoding headers:
':authority', '10.20.0.14:15021'
':path', '/healthz/ready'
':method', 'GET'
':scheme', 'http'
'user-agent', 'kube-probe/1.23'
'accept', '*/*'
'x-forwarded-proto', 'http'
'x-request-id', 'f015f4ba-a4cc-4f61-bc9e-be666f73eeab'
'x-envoy-expected-rq-timeout-ms', '15000'
thread=61
2025-05-24T18:10:55.812329Z debug envoy pool external/envoy/source/common/conn_pool/conn_pool_base.cc:265 [C72] using existing fully connected connection thread=61
2025-05-24T18:10:55.812338Z debug envoy pool external/envoy/source/common/conn_pool/conn_pool_base.cc:182 [C72] creating stream thread=61
2025-05-24T18:10:55.812355Z debug envoy router external/envoy/source/common/router/upstream_request.cc:581 [C1851][S429397187266806652] pool ready thread=61
2025-05-24T18:10:55.812395Z debug envoy client external/envoy/source/common/http/codec_client.cc:139 [C72] encode complete thread=61
2025-05-24T18:10:55.812914Z debug envoy client external/envoy/source/common/http/codec_client.cc:126 [C72] response complete thread=61
2025-05-24T18:10:55.812966Z debug envoy router external/envoy/source/common/router/router.cc:1363 [C1851][S429397187266806652] upstream headers complete: end_stream=true thread=61
2025-05-24T18:10:55.813031Z debug envoy http external/envoy/source/common/http/conn_manager_impl.cc:1629 [C1851][S429397187266806652] closing connection due to connection close header thread=61
2025-05-24T18:10:55.813055Z debug envoy http external/envoy/source/common/http/conn_manager_impl.cc:1687 [C1851][S429397187266806652] encoding headers via codec (end_stream=true):
':status', '200'
'date', 'Sat, 24 May 2025 18:10:55 GMT'
'content-length', '0'
'x-envoy-upstream-service-time', '0'
'server', 'envoy'
'connection', 'close'
thread=61
...
|
16. east 클러스터 catalog 애플리케이션 로그 확인
1
| keast logs -n istioinaction -l app=catalog -c catalog -f
|
✅ 출력
1
2
3
4
5
6
| request path: /items
blowups: {}
number of blowups: 0
GET catalog.istioinaction.svc.cluster.local:80 /items 200 502 - 0.314 ms
GET /items 200 0.314 ms - 502
...
|
17. west webapp pod에서 tcpdump로 패킷 캡처 (15443)
1
| kwest exec -it -n istioinaction deploy/webapp -c istio-proxy -- sudo tcpdump -i any tcp -nn
|
✅ 출력
1
2
3
4
| ...
18:13:17.455137 eth0 Out IP 10.10.0.13.60216 > 172.18.255.202.15443: Flags [P.], seq 2516704103:2516705481, ack 658697047, win 799, options [nop,nop,TS val 118811638 ecr 2377135503], length 1378
18:13:17.457228 eth0 In IP 172.18.255.202.15443 > 10.10.0.13.60216: Flags [P.], seq 1:1789, ack 1378, win 9777, options [nop,nop,TS val 2377137627 ecr 118811638], length 1788
...
|
18. east 클러스터 istio-eastwestgateway 외부 IP 재확인
1
| keast get svc -n istio-system istio-eastwestgateway
|
✅ 출력
1
2
| NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
istio-eastwestgateway LoadBalancer 10.200.0.64 172.18.255.202 15021:30177/TCP,15443:30700/TCP,15012:31464/TCP,15017:32767/TCP 64m
|
19. east catalog pod의 istio-proxy에서 tcpdump 실행 및 캡처 저장
1
| keast exec -it -n istioinaction deploy/catalog -c istio-proxy -- sudo tcpdump -i any tcp port 3000 -w /var/lib/istio/data/dump.pcap
|
✅ 출력
1
2
3
4
5
| tcpdump: data link type LINUX_SLL2
tcpdump: listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
^C72 packets captured
108 packets received by filter
0 packets dropped by kernel
|
20. dump 파일 존재 여부 확인
1
| keast exec -it -n istioinaction deploy/catalog -c istio-proxy -- ls -l /var/lib/istio/data/
|
✅ 출력
1
2
| total 64
-rw-r--r-- 1 tcpdump tcpdump 62268 May 24 18:17 dump.pcap
|
21. 출력 결과 파일을 로컬로 다운로드
1
| keast get pod -n istioinaction -l app=catalog -oname
|
✅ 출력
1
| pod/catalog-6cf4b97d-dd2dv
|
1
| keast cp -n istioinaction -c istio-proxy catalog-6cf4b97d-dd2dv:var/lib/istio/data/dump.pcap ./dump.pcap
|
22. Termshark로 패킷 캡처 파일 분석하기
23. 실습 후 kind 삭제
1
| kind delete cluster --name west && kind delete cluster --name east && docker rm -f mypc
|
✅ 출력
1
2
3
4
5
| Deleting cluster "west" ...
Deleted nodes: ["west-control-plane"]
Deleting cluster "east" ...
Deleted nodes: ["east-control-plane"]
mypc
|
📄 EnvoyFilter 리소스로 엔보이 필터 설정하기
1. k8s(1.23.17) 배포 & mypc 컨테이너
(1) 실습 코드 다운로드 및 경로 확인
1
2
3
| git clone https://github.com/AcornPublishing/istio-in-action
cd istio-in-action/book-source-code-master
pwd # 각자 자신의 pwd 경로
|
✅ 출력
1
| /home/devshin/workspace/istio/istio-in-action/book-source-code-master
|
(2) Kind 클러스터 (v1.23.17) 생성 및 포트 매핑 설정
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| kind create cluster --name myk8s --image kindest/node:v1.23.17 --config - <<EOF
kind: Cluster
apiVersion: kind.x-k8s.io/v1alpha4
nodes:
- role: control-plane
extraPortMappings:
- containerPort: 30000 # Sample Application (istio-ingrssgateway) HTTP
hostPort: 30000
- containerPort: 30001 # Prometheus
hostPort: 30001
- containerPort: 30002 # Grafana
hostPort: 30002
- containerPort: 30003 # Kiali
hostPort: 30003
- containerPort: 30004 # Tracing
hostPort: 30004
- containerPort: 30005 # Sample Application (istio-ingrssgateway) HTTPS
hostPort: 30005
- containerPort: 30006 # TCP Route
hostPort: 30006
- containerPort: 30007 # kube-ops-view
hostPort: 30007
extraMounts: # 해당 부분 생략 가능
- hostPath: /home/devshin/workspace/istio/istio-in-action/book-source-code-master # 각자 자신의 pwd 경로로 설정
containerPath: /istiobook
networking:
podSubnet: 10.10.0.0/16
serviceSubnet: 10.200.0.0/22
EOF
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
| Creating cluster "myk8s" ...
✓ Ensuring node image (kindest/node:v1.23.17) 🖼
✓ Preparing nodes 📦
✓ Writing configuration 📜
✓ Starting control-plane 🕹️
✓ Installing CNI 🔌
✓ Installing StorageClass 💾
Set kubectl context to "kind-myk8s"
You can now use your cluster with:
kubectl cluster-info --context kind-myk8s
Have a question, bug, or feature request? Let us know! https://kind.sigs.k8s.io/#community 🙂
|
(3) 설치 확인
✅ 출력
1
2
| CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
6ed4a8441bf9 kindest/node:v1.23.17 "/usr/local/bin/entr…" 34 seconds ago Up 32 seconds 0.0.0.0:30000-30007->30000-30007/tcp, 127.0.0.1:34629->6443/tcp myk8s-control-plane
|
(4) myk8s 컨트롤 플레인 컨테이너에 도구 설치
1
| docker exec -it myk8s-control-plane sh -c 'apt update && apt install tree psmisc lsof wget bridge-utils net-tools dnsutils tcpdump ngrep iputils-ping git vim -y'
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| ...
update-alternatives: using /usr/bin/vim.basic to provide /usr/bin/vim (vim) in auto mode
update-alternatives: using /usr/bin/vim.basic to provide /usr/bin/vimdiff (vimdiff) in auto mode
Setting up bind9-libs:amd64 (1:9.18.33-1~deb12u2) ...
Setting up openssh-client (1:9.2p1-2+deb12u6) ...
Setting up libxext6:amd64 (2:1.3.4-1+b1) ...
Setting up dbus-daemon (1.14.10-1~deb12u1) ...
Setting up libnet1:amd64 (1.1.6+dfsg-3.2) ...
Setting up libpcap0.8:amd64 (1.10.3-1) ...
Setting up dbus (1.14.10-1~deb12u1) ...
invoke-rc.d: policy-rc.d denied execution of start.
/usr/sbin/policy-rc.d returned 101, not running 'start dbus.service'
Setting up libgdbm-compat4:amd64 (1.23-3) ...
Setting up xauth (1:1.1.2-1) ...
Setting up bind9-host (1:9.18.33-1~deb12u2) ...
Setting up libperl5.36:amd64 (5.36.0-7+deb12u2) ...
Setting up tcpdump (4.99.3-1) ...
Setting up ngrep (1.47+ds1-5+b1) ...
Setting up perl (5.36.0-7+deb12u2) ...
Setting up bind9-dnsutils (1:9.18.33-1~deb12u2) ...
Setting up dnsutils (1:9.18.33-1~deb12u2) ...
Setting up liberror-perl (0.17029-2) ...
Setting up git (1:2.39.5-0+deb12u2) ...
Processing triggers for libc-bin (2.36-9+deb12u4) ...
|
(5) Kind 네트워크 정보 조회 및 구성 확인
1
2
| docker network ls
docker inspect kind
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
| NETWORK ID NAME DRIVER SCOPE
24c2dcf37d04 bridge bridge local
bb4d74152d4a host host local
dbf072d0a217 kind bridge local
056dcb2c01d1 none null local
[
{
"Name": "kind",
"Id": "dbf072d0a217f53e0b62f42cee01bcecc1b2f6ea216475178db001f2e38681f5",
"Created": "2025-01-26T16:18:22.33980443+09:00",
"Scope": "local",
"Driver": "bridge",
"EnableIPv4": true,
"EnableIPv6": true,
"IPAM": {
"Driver": "default",
"Options": {},
"Config": [
{
"Subnet": "172.18.0.0/16",
"Gateway": "172.18.0.1"
},
{
"Subnet": "fc00:f853:ccd:e793::/64",
"Gateway": "fc00:f853:ccd:e793::1"
}
]
},
"Internal": false,
"Attachable": false,
"Ingress": false,
"ConfigFrom": {
"Network": ""
},
"ConfigOnly": false,
"Containers": {
"6ed4a8441bf9ea8207a19ccdd5e7285a83f1c8cf191800d4866980638e9e276a": {
"Name": "myk8s-control-plane",
"EndpointID": "5d1870c71b50415a4900e9c58ac37ec722240e92ee9280d16cedcd78d49a6377",
"MacAddress": "8a:f4:78:5b:05:38",
"IPv4Address": "172.18.0.2/16",
"IPv6Address": "fc00:f853:ccd:e793::2/64"
}
},
"Options": {
"com.docker.network.bridge.enable_ip_masquerade": "true",
"com.docker.network.driver.mtu": "1500"
},
"Labels": {}
}
]
|
(6) mypc 컨테이너를 Kind 네트워크로 배포
1
| docker run -d --rm --name mypc --network kind --ip 172.18.0.100 nicolaka/netshoot sleep infinity
|
✅ 출력
1
| a68f4976bed02d5663ab59ffe41dde8ff8727e9d56203c01d91b90d9176160f9
|
(7) Kind 네트워크 내 컨테이너 IP 확인
1
| docker ps -q | xargs docker inspect --format ' '
|
✅ 출력
1
2
| /mypc 172.18.0.100
/myk8s-control-plane 172.18.0.2
|
(8) 컨테이너 간 네트워크 통신 확인 (IP & 도메인)
1
| docker exec -it mypc ping -c 1 172.18.0.2
|
✅ 출력
1
2
3
4
5
6
| PING 172.18.0.2 (172.18.0.2) 56(84) bytes of data.
64 bytes from 172.18.0.2: icmp_seq=1 ttl=64 time=0.102 ms
--- 172.18.0.2 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.102/0.102/0.102/0.000 ms
|
1
| docker exec -it mypc ping -c 1 myk8s-control-plane
|
✅ 출력
1
2
3
4
5
6
| PING myk8s-control-plane (172.18.0.2) 56(84) bytes of data.
64 bytes from myk8s-control-plane.kind (172.18.0.2): icmp_seq=1 ttl=64 time=0.041 ms
--- myk8s-control-plane ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.041/0.041/0.041/0.000 ms
|
1
| docker exec -it myk8s-control-plane ping -c 1 mypc
|
✅ 출력
1
2
3
4
5
6
| PING mypc(mypc.kind (fc00:f853:ccd:e793::3)) 56 data bytes
64 bytes from mypc.kind (fc00:f853:ccd:e793::3): icmp_seq=1 ttl=64 time=0.104 ms
--- mypc ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 0.104/0.104/0.104/0.000 ms
|
(1) MetalLB 컨트롤러 및 CRD 리소스 설치
1
| kubectl apply -f https://raw.githubusercontent.com/metallb/metallb/v0.14.9/config/manifests/metallb-native.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
| namespace/metallb-system created
customresourcedefinition.apiextensions.k8s.io/bfdprofiles.metallb.io created
customresourcedefinition.apiextensions.k8s.io/bgpadvertisements.metallb.io created
customresourcedefinition.apiextensions.k8s.io/bgppeers.metallb.io created
customresourcedefinition.apiextensions.k8s.io/communities.metallb.io created
customresourcedefinition.apiextensions.k8s.io/ipaddresspools.metallb.io created
customresourcedefinition.apiextensions.k8s.io/l2advertisements.metallb.io created
customresourcedefinition.apiextensions.k8s.io/servicel2statuses.metallb.io created
serviceaccount/controller created
serviceaccount/speaker created
role.rbac.authorization.k8s.io/controller created
role.rbac.authorization.k8s.io/pod-lister created
clusterrole.rbac.authorization.k8s.io/metallb-system:controller created
clusterrole.rbac.authorization.k8s.io/metallb-system:speaker created
rolebinding.rbac.authorization.k8s.io/controller created
rolebinding.rbac.authorization.k8s.io/pod-lister created
clusterrolebinding.rbac.authorization.k8s.io/metallb-system:controller created
clusterrolebinding.rbac.authorization.k8s.io/metallb-system:speaker created
configmap/metallb-excludel2 created
secret/metallb-webhook-cert created
service/metallb-webhook-service created
deployment.apps/controller created
daemonset.apps/speaker created
validatingwebhookconfiguration.admissionregistration.k8s.io/metallb-webhook-configuration created
|
(2) MetalLB Pod 상태 확인
1
| kubectl get pod -n metallb-system
|
✅ 출력
1
2
3
| NAME READY STATUS RESTARTS AGE
controller-686c7db689-brszk 1/1 Running 0 21s
speaker-lx89h 0/1 Running 0 21s
|
(3) IPAddressPool 및 L2Advertisement 설정
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| cat << EOF | kubectl apply -f -
apiVersion: metallb.io/v1beta1
kind: IPAddressPool
metadata:
name: default
namespace: metallb-system
spec:
addresses:
- 172.18.255.101-172.18.255.120
---
apiVersion: metallb.io/v1beta1
kind: L2Advertisement
metadata:
name: default
namespace: metallb-system
spec:
ipAddressPools:
- default
EOF
# 결과
ipaddresspool.metallb.io/default created
l2advertisement.metallb.io/default created
|
(4) 설정 리소스 조회
1
| kubectl get IPAddressPool,L2Advertisement -A
|
✅ 출력
1
2
3
4
5
| NAMESPACE NAME AUTO ASSIGN AVOID BUGGY IPS ADDRESSES
metallb-system ipaddresspool.metallb.io/default true false ["172.18.255.101-172.18.255.120"]
NAMESPACE NAME IPADDRESSPOOLS IPADDRESSPOOL SELECTORS INTERFACES
metallb-system l2advertisement.metallb.io/default ["default"]
|
3. 샘플 애플리케이션 배포 및 LoadBalancer 테스트
(1) NGINX 애플리케이션과 LoadBalancer 타입 서비스 배포
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| cat << EOF | kubectl apply -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
spec:
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:latest
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx-service
spec:
selector:
app: nginx
ports:
- port: 80
targetPort: 80
type: LoadBalancer
EOF
# 결과
deployment.apps/nginx created
service/nginx-service created
|
(2) 배포 리소스 상태 확인
1
| kubectl get deploy,pod,svc,ep
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
| NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/nginx 1/1 1 1 25s
NAME READY STATUS RESTARTS AGE
pod/nginx-8d545c96d-8b948 1/1 Running 0 25s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.200.0.1 <none> 443/TCP 5m39s
service/nginx-service LoadBalancer 10.200.3.1 172.18.255.101 80:30760/TCP 25s
NAME ENDPOINTS AGE
endpoints/kubernetes 172.18.0.2:6443 5m39s
endpoints/nginx-service 10.10.0.6:80 25s
|
(3) 외부 IP 확인 및 변수 설정
1
2
| kubectl get svc nginx-service -o jsonpath='{.status.loadBalancer.ingress[0].ip}'
LBIP=$(kubectl get svc nginx-service -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
|
✅ 출력
(4) 외부 접속 테스트
1
| docker exec -it mypc curl -s $LBIP
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <!DOCTYPE html>
<html>
<head>
<title>Welcome to nginx!</title>
<style>
html { color-scheme: light dark; }
body { width: 35em; margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif; }
</style>
</head>
<body>
<h1>Welcome to nginx!</h1>
<p>If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.</p>
<p>For online documentation and support please refer to
<a href="http://nginx.org/">nginx.org</a>.<br/>
Commercial support is available at
<a href="http://nginx.com/">nginx.com</a>.</p>
<p><em>Thank you for using nginx.</em></p>
</body>
</html>
|
1
| docker exec -it mypc curl -s $LBIP -v -I
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| * Trying 172.18.255.101:80...
* Connected to 172.18.255.101 (172.18.255.101) port 80
> HEAD / HTTP/1.1
> Host: 172.18.255.101
> User-Agent: curl/8.7.1
> Accept: */*
>
* Request completely sent off
< HTTP/1.1 200 OK
HTTP/1.1 200 OK
< Server: nginx/1.27.5
Server: nginx/1.27.5
< Date: Sat, 24 May 2025 18:40:49 GMT
Date: Sat, 24 May 2025 18:40:49 GMT
< Content-Type: text/html
Content-Type: text/html
< Content-Length: 615
Content-Length: 615
< Last-Modified: Wed, 16 Apr 2025 12:01:11 GMT
Last-Modified: Wed, 16 Apr 2025 12:01:11 GMT
< Connection: keep-alive
Connection: keep-alive
< ETag: "67ff9c07-267"
ETag: "67ff9c07-267"
< Accept-Ranges: bytes
Accept-Ranges: bytes
<
* Connection #0 to host 172.18.255.101 left intact
|
(5) 샘플 리소스 삭제
1
2
3
4
5
6
| kubectl delete deploy,svc --all
# 결과
deployment.apps "nginx" deleted
service "kubernetes" deleted
service "nginx-service" deleted
|
4. istio 1.17.8 설치
(1) Istio 설치 환경 준비 및 파일 확인
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
| docker exec -it myk8s-control-plane bash
root@myk8s-control-plane:/# tree /istiobook/ -L 1
/istiobook/
|-- 2025-04-27-190930_1_roundrobin.json
|-- 2025-04-27-191213_2_roundrobin.json
|-- 2025-04-27-191803_3_random.json
|-- 2025-04-27-220131_4_random.json
|-- 2025-04-27-221302_5_least_conn.json
|-- README.md
|-- appendices
|-- bin
|-- ch10
|-- ch11
|-- ch12
|-- ch13
|-- ch14
|-- ch2
|-- ch3
|-- ch4
|-- ch5
|-- ch6
|-- ch7
|-- ch8
|-- ch9
|-- dump.pcap
|-- east-kubeconfig
|-- forum-2.json
|-- prom-values-2.yaml
|-- services
|-- webapp-routes.json
`-- west-kubeconfig
17 directories, 12 files
|
(2) Istioctl 설치 및 환경변수 설정
1
2
3
4
5
| root@myk8s-control-plane:/# export ISTIOV=1.17.8
echo 'export ISTIOV=1.17.8' >> /root/.bashrc
curl -s -L https://istio.io/downloadIstio | ISTIO_VERSION=$ISTIOV sh -
cp istio-$ISTIOV/bin/istioctl /usr/local/bin/istioctl
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| Downloading istio-1.17.8 from https://github.com/istio/istio/releases/download/1.17.8/istio-1.17.8-linux-amd64.tar.gz ...
Istio 1.17.8 download complete!
The Istio release archive has been downloaded to the istio-1.17.8 directory.
To configure the istioctl client tool for your workstation,
add the /istio-1.17.8/bin directory to your environment path variable with:
export PATH="$PATH:/istio-1.17.8/bin"
Begin the Istio pre-installation check by running:
istioctl x precheck
Try Istio in ambient mode
https://istio.io/latest/docs/ambient/getting-started/
Try Istio in sidecar mode
https://istio.io/latest/docs/setup/getting-started/
Install guides for ambient mode
https://istio.io/latest/docs/ambient/install/
Install guides for sidecar mode
https://istio.io/latest/docs/setup/install/
Need more information? Visit https://istio.io/latest/docs/
|
(3) demo 프로파일 컨트롤 플레인 배포
1
| root@myk8s-control-plane:/# istioctl install --set profile=demo --set values.global.proxy.privileged=true -y
|
✅ 출력
1
2
3
4
5
6
7
| ✔ Istio core installed
✔ Istiod installed
✔ Egress gateways installed
✔ Ingress gateways installed
✔ Installation complete Making this installation the default for injection and validation.
Thank you for installing Istio 1.17. Please take a few minutes to tell us about your install/upgrade experience! https://forms.gle/hMHGiwZHPU7UQRWe9
|
(4) 보조 도구 설치
1
| root@myk8s-control-plane:/# kubectl apply -f istio-$ISTIOV/samples/addons
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| serviceaccount/grafana created
configmap/grafana created
service/grafana created
deployment.apps/grafana created
configmap/istio-grafana-dashboards created
configmap/istio-services-grafana-dashboards created
deployment.apps/jaeger created
service/tracing created
service/zipkin created
service/jaeger-collector created
serviceaccount/kiali created
configmap/kiali created
clusterrole.rbac.authorization.k8s.io/kiali-viewer created
clusterrole.rbac.authorization.k8s.io/kiali created
clusterrolebinding.rbac.authorization.k8s.io/kiali created
role.rbac.authorization.k8s.io/kiali-controlplane created
rolebinding.rbac.authorization.k8s.io/kiali-controlplane created
service/kiali created
deployment.apps/kiali created
serviceaccount/prometheus created
configmap/prometheus created
clusterrole.rbac.authorization.k8s.io/prometheus created
clusterrolebinding.rbac.authorization.k8s.io/prometheus created
service/prometheus created
deployment.apps/prometheus created
|
(5) 설치 환경에서 빠져나오기
1
2
| root@myk8s-control-plane:/# exit
exit
|
(6) 네임스페이스 생성 및 사이드카 자동 주입 설정
1
2
3
| kubectl create ns istioinaction
kubectl label namespace istioinaction istio-injection=enabled
kubectl get ns --show-labels
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
| namespace/istioinaction created
namespace/istioinaction labeled
NAME STATUS AGE LABELS
default Active 18m kubernetes.io/metadata.name=default
istio-system Active 96s kubernetes.io/metadata.name=istio-system
istioinaction Active 0s istio-injection=enabled,kubernetes.io/metadata.name=istioinaction
kube-node-lease Active 18m kubernetes.io/metadata.name=kube-node-lease
kube-public Active 18m kubernetes.io/metadata.name=kube-public
kube-system Active 18m kubernetes.io/metadata.name=kube-system
local-path-storage Active 18m kubernetes.io/metadata.name=local-path-storage
metallb-system Active 15m kubernetes.io/metadata.name=metallb-system,pod-security.kubernetes.io/audit=privileged,pod-security.kubernetes.io/enforce=privileged,pod-security.kubernetes.io/warn=privileged
|
(7) istio-ingressgateway 서비스 패치 (NodePort, LoadBalancer, 외부 IP 설정)
1
2
3
4
| kubectl patch svc -n istio-system istio-ingressgateway -p '{"spec": {"type": "LoadBalancer", "ports": [{"port": 80, "targetPort": 8080, "nodePort": 30000}]}}'
kubectl patch svc -n istio-system istio-ingressgateway -p '{"spec": {"type": "LoadBalancer", "ports": [{"port": 443, "targetPort": 8443, "nodePort": 30005}]}}'
kubectl patch svc -n istio-system istio-ingressgateway -p '{"spec":{"externalTrafficPolicy": "Local"}}'
kubectl describe svc -n istio-system istio-ingressgateway
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| service/istio-ingressgateway patched
service/istio-ingressgateway patched
service/istio-ingressgateway patched
Name: istio-ingressgateway
Namespace: istio-system
Labels: app=istio-ingressgateway
install.operator.istio.io/owning-resource=unknown
install.operator.istio.io/owning-resource-namespace=istio-system
istio=ingressgateway
istio.io/rev=default
operator.istio.io/component=IngressGateways
operator.istio.io/managed=Reconcile
operator.istio.io/version=1.17.8
release=istio
Annotations: metallb.io/ip-allocated-from-pool: default
Selector: app=istio-ingressgateway,istio=ingressgateway
Type: LoadBalancer
IP Family Policy: SingleStack
IP Families: IPv4
IP: 10.200.3.248
IPs: 10.200.3.248
LoadBalancer Ingress: 172.18.255.101
Port: status-port 15021/TCP
TargetPort: 15021/TCP
NodePort: status-port 32729/TCP
Endpoints: 10.10.0.9:15021
Port: http2 80/TCP
TargetPort: 8080/TCP
NodePort: http2 30000/TCP
Endpoints: 10.10.0.9:8080
Port: https 443/TCP
TargetPort: 8443/TCP
NodePort: https 30005/TCP
Endpoints: 10.10.0.9:8443
Port: tcp 31400/TCP
TargetPort: 31400/TCP
NodePort: tcp 30503/TCP
Endpoints: 10.10.0.9:31400
Port: tls 15443/TCP
TargetPort: 15443/TCP
NodePort: tls 32122/TCP
Endpoints: 10.10.0.9:15443
Session Affinity: None
External Traffic Policy: Local
Internal Traffic Policy: Cluster
HealthCheck NodePort: 31654
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal IPAllocated 2m3s metallb-controller Assigned IP ["172.18.255.101"]
Normal nodeAssigned 1s (x4 over 111s) metallb-speaker announcing from node "myk8s-control-plane" with protocol "layer2"
Normal ExternalTrafficPolicy 1s service-controller Cluster -> Local
|
(8) 관측 도구 NodePort 변경 (Prometheus, Grafana, Kiali, Tracing)
1
2
3
4
| kubectl patch svc -n istio-system prometheus -p '{"spec": {"type": "NodePort", "ports": [{"port": 9090, "targetPort": 9090, "nodePort": 30001}]}}'
kubectl patch svc -n istio-system grafana -p '{"spec": {"type": "NodePort", "ports": [{"port": 3000, "targetPort": 3000, "nodePort": 30002}]}}'
kubectl patch svc -n istio-system kiali -p '{"spec": {"type": "NodePort", "ports": [{"port": 20001, "targetPort": 20001, "nodePort": 30003}]}}'
kubectl patch svc -n istio-system tracing -p '{"spec": {"type": "NodePort", "ports": [{"port": 80, "targetPort": 16686, "nodePort": 30004}]}}'
|
✅ 출력
1
2
3
4
| service/prometheus patched
service/grafana patched
service/kiali patched
service/tracing patched
|
5. 탭 필터 구성 및 검증 절차
(1) 기존 EnvoyFilter 목록 확인
1
| kubectl get envoyfilter -A
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| NAMESPACE NAME AGE
istio-system stats-filter-1.13 4m11s
istio-system stats-filter-1.14 4m11s
istio-system stats-filter-1.15 4m11s
istio-system stats-filter-1.16 4m11s
istio-system stats-filter-1.17 4m11s
istio-system tcp-stats-filter-1.13 4m11s
istio-system tcp-stats-filter-1.14 4m11s
istio-system tcp-stats-filter-1.15 4m11s
istio-system tcp-stats-filter-1.16 4m11s
istio-system tcp-stats-filter-1.17 4m11s
|
(2) Catalog, Webapp, Gateway, Sleep 리소스 배포
1
2
3
4
| kubectl apply -f services/catalog/kubernetes/catalog.yaml -n istioinaction
kubectl apply -f services/webapp/kubernetes/webapp.yaml -n istioinaction
kubectl apply -f services/webapp/istio/webapp-catalog-gw-vs.yaml -n istioinaction
kubectl apply -f ch9/sleep.yaml -n istioinaction
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
| serviceaccount/catalog created
service/catalog created
deployment.apps/catalog created
serviceaccount/webapp created
service/webapp created
deployment.apps/webapp created
gateway.networking.istio.io/coolstore-gateway created
virtualservice.networking.istio.io/webapp-virtualservice created
serviceaccount/sleep created
service/sleep created
deployment.apps/sleep created
|
(3) Gateway 및 VirtualService 리소스 상태 확인
1
| kubectl get gw,vs,dr -n istioinaction
|
✅ 출력
1
2
3
4
5
| NAME AGE
gateway.networking.istio.io/coolstore-gateway 43s
NAME GATEWAYS HOSTS AGE
virtualservice.networking.istio.io/webapp-virtualservice ["coolstore-gateway"] ["webapp.istioinaction.io"] 43s
|
(4) Webapp 서비스 호출 테스트 (mypc 컨테이너)
1
2
| EXT_IP=$(kubectl -n istio-system get svc istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
docker exec -it mypc curl -s -H "Host: webapp.istioinaction.io" http://$EXT_IP/api/catalog
|
✅ 출력
1
| [{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
|
(5) 반복 호출 테스트 (mypc 컨테이너)
1
2
| EXT_IP=$(kubectl -n istio-system get svc istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
while true; do docker exec -it mypc curl -s -H "Host: webapp.istioinaction.io" http://$EXT_IP/api/catalog ; echo ; date "+%Y-%m-%d %H:%M:%S" ; sleep 1; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
| [{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
2025-05-25 03:50:58
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
2025-05-25 03:50:59
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
2025-05-25 03:51:00
...
|
(6) Webapp API 호출 테스트 (호스트 PC)
1
| curl -s http://webapp.istioinaction.io:30000/api/catalog
|
✅ 출력
1
| [{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
|
(7) EnvoyFilter 리소스 정의 확인
1
| cat ch14/tap-envoy-filter.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: tap-filter
namespace: istioinaction
spec:
workloadSelector:
labels:
app: webapp # 워크로드 셀렉터
configPatches:
- applyTo: HTTP_FILTER # 설정할 위치
match:
context: SIDECAR_INBOUND
listener:
portNumber: 8080
filterChain:
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch: # 엔보이 설정 패치
operation: INSERT_BEFORE
value:
name: envoy.filters.http.tap
typed_config:
"@type": "type.googleapis.com/envoy.extensions.filters.http.tap.v3.Tap"
commonConfig:
adminConfig:
configId: tap_config
|
(8) EnvoyFilter 리소스 배포 및 확인
1
2
3
4
| kubectl apply -f ch14/tap-envoy-filter.yaml
# 결과
envoyfilter.networking.istio.io/tap-filter created
|
1
| kubectl get envoyfilter -n istioinaction
|
✅ 출력
1
2
| NAME AGE
tap-filter 14s
|
(9) Proxy Listener 설정 확인
1
| docker exec -it myk8s-control-plane istioctl proxy-config listener deploy/webapp.istioinaction --port 15006
|
✅ 출력
1
2
3
4
5
6
7
8
9
| ADDRESS PORT MATCH DESTINATION
0.0.0.0 15006 Addr: *:15006 Non-HTTP/Non-TCP
0.0.0.0 15006 Trans: tls; App: istio-http/1.0,istio-http/1.1,istio-h2; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: raw_buffer; App: http/1.1,h2c; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: tls; App: TCP TLS; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: raw_buffer; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: tls; Addr: 0.0.0.0/0 InboundPassthroughClusterIpv4
0.0.0.0 15006 Trans: tls; App: istio,istio-peer-exchange,istio-http/1.0,istio-http/1.1,istio-h2; Addr: *:8080 Cluster: inbound|8080||
0.0.0.0 15006 Trans: raw_buffer; Addr: *:8080 Cluster: inbound|8080||
|
1
| docker exec -it myk8s-control-plane istioctl proxy-config listener deploy/webapp.istioinaction --port 15006 -o json
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| ...
{
"name": "envoy.filters.http.tap",
"typedConfig": {
"@type": "type.googleapis.com/envoy.extensions.filters.http.tap.v3.Tap",
"commonConfig": {
"adminConfig": {
"configId": "tap_config"
}
}
}
},
{
"name": "envoy.filters.http.router",
"typedConfig": {
"@type": "type.googleapis.com/envoy.extensions.filters.http.router.v3.Router"
}
}
...
|
(10) 터미널 1 : 포트 포워딩 설정 후 tap 시작
1
2
| kubectl port-forward -n istioinaction deploy/webapp 15000 &
curl -X POST -d @./ch14/tap-config.json localhost:15000/tap
|
✅ 출력
1
2
3
4
| [1] 178290
curl: (7) Failed to connect to localhost port 15000 after 0 ms: Could not connect to server
Forwarding from 127.0.0.1:15000 -> 15000
Forwarding from [::1]:15000 -> 15000
|
(11) 터미널 2 : 기존 반복 접속하는 것 활용
1
2
3
| EXT_IP=$(kubectl -n istio-system get svc istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
docker exec -it mypc curl -s -H "Host: webapp.istioinaction.io" http://$EXT_IP/api/catalog
docker exec -it mypc curl -s -H "x-app-tap: true" -H "Host: webapp.istioinaction.io" http://$EXT_IP/api/catalog
|
✅ 출력
1
| [{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}][{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
|
1
| while true; do docker exec -it mypc curl -s -H "x-app-tap: true" -H "Host: webapp.istioinaction.io" http://$EXT_IP/api/catalog ; echo ; date "+%Y-%m-%d %H:%M:%S" ; sleep 1; echo; done
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
| [{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
2025-05-25 03:58:33
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
2025-05-25 03:58:34
[{"id":1,"color":"amber","department":"Eyewear","name":"Elinor Glasses","price":"282.00"},{"id":2,"color":"cyan","department":"Clothing","name":"Atlas Shirt","price":"127.00"},{"id":3,"color":"teal","department":"Clothing","name":"Small Metal Shoes","price":"232.00"},{"id":4,"color":"red","department":"Watches","name":"Red Dragon Watch","price":"232.00"}]
2025-05-25 03:58:35
...
|
(12) Proxy 로그 레벨을 HTTP로 변경
1
| docker exec -it myk8s-control-plane istioctl proxy-config log deploy/webapp -n istioinaction --level http:debug
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
| webapp-7685bcb84-9sp9s.istioinaction:
active loggers:
admin: warning
alternate_protocols_cache: warning
aws: warning
assert: warning
backtrace: warning
cache_filter: warning
client: warning
config: warning
connection: warning
conn_handler: warning
decompression: warning
dns: warning
dubbo: warning
envoy_bug: warning
ext_authz: warning
ext_proc: warning
rocketmq: warning
file: warning
filter: warning
forward_proxy: warning
grpc: warning
happy_eyeballs: warning
hc: warning
health_checker: warning
http: debug
http2: warning
hystrix: warning
init: warning
io: warning
jwt: warning
kafka: warning
key_value_store: warning
lua: warning
main: warning
matcher: warning
misc: error
mongo: warning
multi_connection: warning
oauth2: warning
quic: warning
quic_stream: warning
pool: warning
rate_limit_quota: warning
rbac: warning
rds: warning
redis: warning
router: warning
runtime: warning
stats: warning
secret: warning
tap: warning
testing: warning
thrift: warning
tracing: warning
upstream: warning
udp: warning
wasm: warning
websocket: warning
|
(13) Proxy 로그 레벨을 tap으로 변경
1
| docker exec -it myk8s-control-plane istioctl proxy-config log deploy/webapp -n istioinaction --level tap:debug
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
| webapp-7685bcb84-9sp9s.istioinaction:
active loggers:
admin: warning
alternate_protocols_cache: warning
aws: warning
assert: warning
backtrace: warning
cache_filter: warning
client: warning
config: warning
connection: warning
conn_handler: warning
decompression: warning
dns: warning
dubbo: warning
envoy_bug: warning
ext_authz: warning
ext_proc: warning
rocketmq: warning
file: warning
filter: warning
forward_proxy: warning
grpc: warning
happy_eyeballs: warning
hc: warning
health_checker: warning
http: debug
http2: warning
hystrix: warning
init: warning
io: warning
jwt: warning
kafka: warning
key_value_store: warning
lua: warning
main: warning
matcher: warning
misc: error
mongo: warning
multi_connection: warning
oauth2: warning
quic: warning
quic_stream: warning
pool: warning
rate_limit_quota: warning
rbac: warning
rds: warning
redis: warning
router: warning
runtime: warning
stats: warning
secret: warning
tap: debug
testing: warning
thrift: warning
tracing: warning
upstream: warning
udp: warning
wasm: warning
websocket: warning
|
(14) Webapp의 istio-proxy 컨테이너 로그 확인
1
| kubectl logs -n istioinaction -l app=webapp -c istio-proxy -f
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| ...
2025-05-24T19:00:47.313254Z debug envoy http external/envoy/source/common/http/conn_manager_impl.cc:329 [C468] new stream thread=45
2025-05-24T19:00:47.313322Z debug envoy http external/envoy/source/common/http/conn_manager_impl.cc:1049 [C468][S3137310935028376502] request headers complete (end_stream=true):
':authority', 'webapp.istioinaction.io'
':path', '/api/catalog'
':method', 'GET'
'user-agent', 'curl/8.7.1'
'accept', '*/*'
'x-app-tap', 'true'
'x-forwarded-for', '172.18.0.100'
'x-forwarded-proto', 'http'
'x-envoy-internal', 'true'
'x-request-id', '9c223372-3e9a-9ead-ab8b-677e2e74b422'
'x-envoy-decorator-operation', 'webapp.istioinaction.svc.cluster.local:80/*'
...
|
🐌 엔보이 속도 제한 서버 설정하기
1. 속도 제한 설정 ConfigMap 확인
1
| cat ch14/rate-limit/rlsconfig.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| apiVersion: v1
kind: ConfigMap
metadata:
name: catalog-ratelimit-config
namespace: istioinaction
data:
config.yaml: |
domain: catalog-ratelimit
descriptors:
- key: header_match
value: no_loyalty
rate_limit:
unit: MINUTE
requests_per_unit: 1
- key: header_match
value: gold_request
rate_limit:
unit: MINUTE
requests_per_unit: 10
- key: header_match
value: silver_request
rate_limit:
unit: MINUTE
requests_per_unit: 5
- key: header_match
value: bronze_request
rate_limit:
unit: MINUTE
requests_per_unit: 3
|
2. EnvoyFilter로 요청 경로 속도 제한 룰 확인
1
| cat ch14/rate-limit/catalog-ratelimit-actions.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
| apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: catalog-ratelimit-actions
namespace: istioinaction
spec:
workloadSelector:
labels:
app: catalog
configPatches:
- applyTo: VIRTUAL_HOST
match:
context: SIDECAR_INBOUND
routeConfiguration:
vhost:
route:
action: ANY
patch:
operation: MERGE
# Applies the rate limit rules.
value:
rate_limits: # 속도 제한 조치
- actions:
- header_value_match:
descriptor_value: no_loyalty
expect_match: false
headers:
- name: "x-loyalty"
- actions:
- header_value_match:
descriptor_value: bronze_request
headers:
- name: "x-loyalty"
exact_match: bronze
- actions:
- header_value_match:
descriptor_value: silver_request
headers:
- name: "x-loyalty"
exact_match: silver
- actions:
- header_value_match:
descriptor_value: gold_request
headers:
- name: "x-loyalty"
exact_match: gold
|
3. 속도 제한 관련 배포 파일 구조 확인
k8s configmap 으로 규칙을 배포하고, 속도 제한 서버를 레디스 백엔드와 함께 배포하자.
✅ 출력
1
2
3
4
5
6
7
| ch14/rate-limit
├── catalog-ratelimit-actions.yaml
├── catalog-ratelimit.yaml
├── rlsconfig.yaml
└── rls.yaml
1 directory, 4 files
|
4. 속도 제한 설정 파일 및 배포 리소스 내용 확인
1
2
| cat ch14/rate-limit/rlsconfig.yaml
cat ch14/rate-limit/rls.yaml
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
| apiVersion: v1
kind: ConfigMap
metadata:
name: catalog-ratelimit-config
namespace: istioinaction
data:
config.yaml: |
domain: catalog-ratelimit
descriptors:
- key: header_match
value: no_loyalty
rate_limit:
unit: MINUTE
requests_per_unit: 1
- key: header_match
value: gold_request
rate_limit:
unit: MINUTE
requests_per_unit: 10
- key: header_match
value: silver_request
rate_limit:
unit: MINUTE
requests_per_unit: 5
- key: header_match
value: bronze_request
rate_limit:
unit: MINUTE
requests_per_unit: 3
# Copyright Istio Authors
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
apiVersion: v1
kind: Service
metadata:
name: redis
namespace: istioinaction
labels:
app: redis
spec:
ports:
- name: redis
port: 6379
selector:
app: redis
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: redis
namespace: istioinaction
spec:
replicas: 1
selector:
matchLabels:
app: redis
template:
metadata:
annotations:
sidecar.istio.io/inject: "false"
labels:
app: redis
spec:
containers:
- image: redis:alpine
imagePullPolicy: IfNotPresent
name: redis
ports:
- name: redis
containerPort: 6379
restartPolicy: Always
serviceAccountName: ""
---
apiVersion: v1
kind: Service
metadata:
name: ratelimit
namespace: istioinaction
labels:
app: ratelimit
spec:
ports:
- name: http-port
port: 8080
targetPort: 8080
protocol: TCP
- name: grpc-port
port: 8081
targetPort: 8081
protocol: TCP
- name: http-debug
port: 6070
targetPort: 6070
protocol: TCP
selector:
app: ratelimit
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: ratelimit
namespace: istioinaction
spec:
replicas: 1
selector:
matchLabels:
app: ratelimit
strategy:
type: Recreate
template:
metadata:
annotations:
sidecar.istio.io/inject: "false"
labels:
app: ratelimit
spec:
containers:
- image: envoyproxy/ratelimit:6f5de117
imagePullPolicy: IfNotPresent
name: ratelimit
command: ["/bin/ratelimit"]
env:
- name: LOG_LEVEL
value: debug
- name: REDIS_SOCKET_TYPE
value: tcp
- name: REDIS_URL
value: redis:6379
- name: USE_STATSD
value: "false"
- name: RUNTIME_ROOT
value: /data
- name: RUNTIME_SUBDIRECTORY
value: ratelimit
- name: RUNTIME_WATCH_ROOT
value: "false"
ports:
- containerPort: 8080
- containerPort: 8081
- containerPort: 6070
volumeMounts:
- name: config-volume
mountPath: /data/ratelimit/config/config.yaml
subPath: config.yaml
volumes:
- name: config-volume
configMap:
name: catalog-ratelimit-config
|
5. ConfigMap 및 속도 제한 서버 배포 (Redis 포함)
1
2
| kubectl apply -f ch14/rate-limit/rlsconfig.yaml -n istioinaction
kubectl apply -f ch14/rate-limit/rls.yaml -n istioinaction
|
✅ 출력
1
2
3
4
5
| configmap/catalog-ratelimit-config created
service/redis created
deployment.apps/redis created
service/ratelimit created
deployment.apps/ratelimit created
|
6. ConfigMap 배포 결과 확인
1
| kubectl get cm -n istioinaction catalog-ratelimit-config
|
✅ 출력
1
2
| NAME DATA AGE
catalog-ratelimit-config 1 33s
|
7. 속도 제한 서버 및 Redis Pod 상태 확인
1
| kubectl get pod -n istioinaction
|
✅ 출력
1
2
3
4
5
6
| NAME READY STATUS RESTARTS AGE
catalog-6cf4b97d-k5ph7 2/2 Running 0 19m
ratelimit-99d5d9c5-9xxjl 1/1 Running 0 55s
redis-6cf4ff9768-nw45l 1/1 Running 0 55s
sleep-6f8cfb8c8f-4cxxf 2/2 Running 0 19m
webapp-7685bcb84-9sp9s 2/2 Running 0 19m
|
8. EnvoyFilter 정의 내용 확인 (필터 + 룰)
1
2
| cat ch14/rate-limit/catalog-ratelimit.yaml
cat ch14/rate-limit/catalog-ratelimit-actions.yamlㄴ
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
| apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: catalog-ratelimit-filter
namespace: istioinaction
spec:
workloadSelector:
labels:
app: catalog
configPatches:
- applyTo: HTTP_FILTER
match:
context: SIDECAR_INBOUND
listener:
portNumber: 3000
filterChain:
filter:
name: "envoy.filters.network.http_connection_manager"
subFilter:
name: "envoy.filters.http.router"
patch:
operation: INSERT_BEFORE
value:
name: envoy.filters.http.ratelimit
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.http.ratelimit.v3.RateLimit
domain: catalog-ratelimit
failure_mode_deny: true
rate_limit_service:
grpc_service:
envoy_grpc:
cluster_name: outbound|8081||ratelimit.istioinaction.svc.cluster.local
timeout: 10s
transport_api_version: V3
apiVersion: networking.istio.io/v1alpha3
kind: EnvoyFilter
metadata:
name: catalog-ratelimit-actions
namespace: istioinaction
spec:
workloadSelector:
labels:
app: catalog
configPatches:
- applyTo: VIRTUAL_HOST
match:
context: SIDECAR_INBOUND
routeConfiguration:
vhost:
route:
action: ANY
patch:
operation: MERGE
# Applies the rate limit rules.
value:
rate_limits:
- actions:
- header_value_match:
descriptor_value: no_loyalty
expect_match: false
headers:
- name: "x-loyalty"
- actions:
- header_value_match:
descriptor_value: bronze_request
headers:
- name: "x-loyalty"
exact_match: bronze
- actions:
- header_value_match:
descriptor_value: silver_request
headers:
- name: "x-loyalty"
exact_match: silver
- actions:
- header_value_match:
descriptor_value: gold_request
headers:
- name: "x-loyalty"
exact_match: gold
|
9. EnvoyFilter 리소스 적용
1
2
3
4
5
6
| kubectl apply -f ch14/rate-limit/catalog-ratelimit.yaml -n istioinaction
kubectl apply -f ch14/rate-limit/catalog-ratelimit-actions.yaml -n istioinaction
# 결과
envoyfilter.networking.istio.io/catalog-ratelimit-filter created
envoyfilter.networking.istio.io/catalog-ratelimit-actions created
|
10. 적용된 EnvoyFilter 목록 확인
1
| kubectl get envoyfilter -A
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| NAMESPACE NAME AGE
istio-system stats-filter-1.13 26m
istio-system stats-filter-1.14 26m
istio-system stats-filter-1.15 26m
istio-system stats-filter-1.16 26m
istio-system stats-filter-1.17 26m
istio-system tcp-stats-filter-1.13 26m
istio-system tcp-stats-filter-1.14 26m
istio-system tcp-stats-filter-1.15 26m
istio-system tcp-stats-filter-1.16 26m
istio-system tcp-stats-filter-1.17 26m
istioinaction catalog-ratelimit-actions 16s
istioinaction catalog-ratelimit-filter 16s
istioinaction tap-filter 16m
|
11. Sleep 앱으로 catalog 서비스 호출 (기본 헤더)
1
| kubectl exec -it deploy/sleep -n istioinaction -c sleep -- curl http://catalog/items -v
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| * Host catalog:80 was resolved.
* IPv6: (none)
* IPv4: 10.200.2.96
* Trying 10.200.2.96:80...
* Connected to catalog (10.200.2.96) port 80
> GET /items HTTP/1.1
> Host: catalog
> User-Agent: curl/8.5.0
> Accept: */*
>
< HTTP/1.1 429 Too Many Requests
< x-envoy-ratelimited: true
< date: Sat, 24 May 2025 19:11:07 GMT
< server: envoy
< content-length: 0
< x-envoy-upstream-service-time: 13
<
* Connection #0 to host catalog left intact
|
12. Sleep 앱으로 catalog 서비스 호출 (silver 헤더)
1
| kubectl exec -it deploy/sleep -n istioinaction -c sleep -- curl -H "x-loyalty: silver" http://catalog/items -v
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
| * Host catalog:80 was resolved.
* IPv6: (none)
* IPv4: 10.200.2.96
* Trying 10.200.2.96:80...
* Connected to catalog (10.200.2.96) port 80
> GET /items HTTP/1.1
> Host: catalog
> User-Agent: curl/8.5.0
> Accept: */*
> x-loyalty: silver
>
< HTTP/1.1 200 OK
< x-powered-by: Express
< vary: Origin, Accept-Encoding
< access-control-allow-credentials: true
< cache-control: no-cache
< pragma: no-cache
< expires: -1
< content-type: application/json; charset=utf-8
< content-length: 502
< etag: W/"1f6-ih2h+hDQ0yLLcKIlBvwkWbyQGK4"
< date: Sat, 24 May 2025 19:12:27 GMT
< x-envoy-upstream-service-time: 9
< server: envoy
<
[
{
"id": 1,
"color": "amber",
"department": "Eyewear",
"name": "Elinor Glasses",
"price": "282.00"
},
{
"id": 2,
"color": "cyan",
"department": "Clothing",
"name": "Atlas Shirt",
"price": "127.00"
},
{
"id": 3,
"color": "teal",
"department": "Clothing",
"name": "Small Metal Shoes",
"price": "232.00"
},
{
"id": 4,
"color": "red",
"department": "Watches",
"name": "Red Dragon Watch",
"price": "232.00"
}
* Connection #0 to host catalog left intact
]
|
13. Envoy 라우트 설정 조회 (Passthrough Cluster)
1
| docker exec -it myk8s-control-plane istioctl proxy-config route deploy/catalog.istioinaction --name 'InboundPassthroughClusterIpv4'
|
✅ 출력
1
2
3
| NAME DOMAINS MATCH VIRTUAL SERVICE
InboundPassthroughClusterIpv4 * /*
InboundPassthroughClusterIpv4 * /*
|
14. Envoy 라우트 설정 조회 (inbound|3000||)
1
| docker exec -it myk8s-control-plane istioctl proxy-config route deploy/catalog.istioinaction --name 'inbound|3000||'
|
✅ 출력
1
2
3
| NAME DOMAINS MATCH VIRTUAL SERVICE
inbound|3000|| * /*
inbound|3000|| * /*
|
15. Envoy 라우트 설정 상세 출력 (rate_limit rules 포함)
1
| docker exec -it myk8s-control-plane istioctl proxy-config route deploy/catalog.istioinaction --name 'inbound|3000||' -o json
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
| ...
"rateLimits": [
{
"actions": [
{
"headerValueMatch": {
"descriptorValue": "no_loyalty",
"expectMatch": false,
"headers": [
{
"name": "x-loyalty"
}
]
}
}
]
},
{
"actions": [
{
"headerValueMatch": {
"descriptorValue": "bronze_request",
"headers": [
{
"name": "x-loyalty",
"exactMatch": "bronze"
}
]
}
}
]
},
{
"actions": [
{
"headerValueMatch": {
"descriptorValue": "silver_request",
"headers": [
{
"name": "x-loyalty",
"exactMatch": "silver"
}
]
}
}
]
},
{
"actions": [
{
"headerValueMatch": {
"descriptorValue": "gold_request",
"headers": [
{
"name": "x-loyalty",
"exactMatch": "gold"
}
]
}
}
]
}
]
}
],
"validateClusters": false
},
...
|
16. 실습 종료 후 리소스 정리
1
2
3
4
| kubectl delete envoyfilter -n istioinaction --all
kubectl get envoyfilter -A
kubectl delete -f ch14/rate-limit/rlsconfig.yaml -n istioinaction
kubectl delete -f ch14/rate-limit/rls.yaml -n istioinaction
|
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| envoyfilter.networking.istio.io "catalog-ratelimit-actions" deleted
envoyfilter.networking.istio.io "catalog-ratelimit-filter" deleted
envoyfilter.networking.istio.io "tap-filter" deleted
NAMESPACE NAME AGE
istio-system stats-filter-1.13 37m
istio-system stats-filter-1.14 37m
istio-system stats-filter-1.15 37m
istio-system stats-filter-1.16 37m
istio-system stats-filter-1.17 37m
istio-system tcp-stats-filter-1.13 37m
istio-system tcp-stats-filter-1.14 37m
istio-system tcp-stats-filter-1.15 37m
istio-system tcp-stats-filter-1.16 37m
istio-system tcp-stats-filter-1.17 37m
configmap "catalog-ratelimit-config" deleted
service "redis" deleted
deployment.apps "redis" deleted
service "ratelimit" deleted
deployment.apps "ratelimit" deleted
|