Cilium 5주차 정리
🔧 실습 환경 구성
1. VirtualBox 호환성 이슈
1
2
curl -O https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/Vagrantfile
vagrant up --provider=virtualbox
📢 오류 발생
1
2
3
4
5
6
7
8
9
10
11
vagrant up --provider=virtualbox
The provider 'virtualbox' that was requested to back the machine
'k8s-ctr' is reporting that it isn't usable on this system. The
reason is shown below:
Vagrant has detected that you have a version of VirtualBox installed
that is not supported by this version of Vagrant. Please install one of
the supported versions listed below to use Vagrant:
4.0, 4.1, 4.2, 4.3, 5.0, 5.1, 5.2, 6.0, 6.1, 7.0, 7.1
A Vagrant update may also be available that adds support for the version
you specified. Please check www.vagrantup.com/downloads.html to download
the latest version.
- Vagrant가 지원하는 VirtualBox는 최대
7.1버전 - Arch Linux 롤링 업데이트로 VirtualBox
7.2가 설치되어 호환 불가
2. 해결과정: libvirt 전환
(1) libvirt 환경 설정
1
2
3
sudo systemctl enable --now libvirtd
sudo usermod -a -G libvirt $USER
newgrp libvirt
(2) libvirt 플러그인 설치
1
vagrant plugin install vagrant-libvirt
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
Installing the 'vagrant-libvirt' plugin. This can take a few minutes...
Fetching xml-simple-1.1.9.gem
Fetching racc-1.8.1.gem
Building native extensions. This could take a while...
Fetching nokogiri-1.18.9-x86_64-linux-gnu.gem
Fetching ruby-libvirt-0.8.4.gem
Building native extensions. This could take a while...
Fetching formatador-1.2.0.gem
Fetching fog-core-2.6.0.gem
Fetching fog-xml-0.1.5.gem
Fetching fog-json-1.2.0.gem
Fetching fog-libvirt-0.13.2.gem
Fetching diffy-3.4.4.gem
Fetching vagrant-libvirt-0.12.2.gem
Installed the plugin 'vagrant-libvirt (0.12.2)'!
(3) 네트워크 패키지 설치
1
2
sudo pacman -S dnsmasq bridge-utils iptables-nft
sudo systemctl restart libvirtd
(4) 기본 네트워크 활성화
1
2
3
sudo virsh net-start default
sudo virsh net-autostart default
sudo virsh net-list --all
✅ 출력
1
2
3
4
5
6
Network default started
Network default marked as autostarted
Name State Autostart Persistent
--------------------------------------------
default active yes yes
(5) Vagrantfile 수정
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
# Variables
K8SV = '1.33.2-1.1' # Kubernetes Version
CONTAINERDV = '1.7.27-1' # Containerd Version
CILIUMV = '1.18.0' # Cilium CNI Version
N = 1 # max number of worker nodes
# Base Image
BOX_IMAGE = "bento/ubuntu-24.04"
BOX_VERSION = "202508.03.0"
Vagrant.configure("2") do |config|
#-ControlPlane Node
config.vm.define "k8s-ctr" do |subconfig|
subconfig.vm.box = BOX_IMAGE
subconfig.vm.box_version = BOX_VERSION
subconfig.vm.provider "libvirt" do |libvirt|
libvirt.cpus = 2
libvirt.memory = 2560
end
subconfig.vm.host_name = "k8s-ctr"
subconfig.vm.network "private_network", ip: "192.168.10.100"
subconfig.vm.network "forwarded_port", guest: 22, host: 60000, auto_correct: true, id: "ssh"
subconfig.vm.synced_folder "./", "/vagrant", disabled: true
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/init_cfg.sh", args: [ K8SV, CONTAINERDV ]
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/k8s-ctr.sh", args: [ N, CILIUMV, K8SV ]
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/route-add1.sh"
end
#-Worker Nodes Subnet1
(1..N).each do |i|
config.vm.define "k8s-w#{i}" do |subconfig|
subconfig.vm.box = BOX_IMAGE
subconfig.vm.box_version = BOX_VERSION
subconfig.vm.provider "libvirt" do |libvirt|
libvirt.cpus = 2
libvirt.memory = 1536
end
subconfig.vm.host_name = "k8s-w#{i}"
subconfig.vm.network "private_network", ip: "192.168.10.10#{i}"
subconfig.vm.network "forwarded_port", guest: 22, host: "6000#{i}", auto_correct: true, id: "ssh"
subconfig.vm.synced_folder "./", "/vagrant", disabled: true
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/init_cfg.sh", args: [ K8SV, CONTAINERDV]
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/k8s-w.sh"
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/route-add1.sh"
end
end
#-Router Node
config.vm.define "router" do |subconfig|
subconfig.vm.box = BOX_IMAGE
subconfig.vm.box_version = BOX_VERSION
subconfig.vm.provider "libvirt" do |libvirt|
libvirt.cpus = 1
libvirt.memory = 768
end
subconfig.vm.host_name = "router"
subconfig.vm.network "private_network", ip: "192.168.10.200"
subconfig.vm.network "forwarded_port", guest: 22, host: 60009, auto_correct: true, id: "ssh"
subconfig.vm.network "private_network", ip: "192.168.20.200", auto_config: false
subconfig.vm.synced_folder "./", "/vagrant", disabled: true
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/router.sh"
end
#-Worker Nodes Subnet2
config.vm.define "k8s-w0" do |subconfig|
subconfig.vm.box = BOX_IMAGE
subconfig.vm.box_version = BOX_VERSION
subconfig.vm.provider "libvirt" do |libvirt|
libvirt.cpus = 2
libvirt.memory = 1536
end
subconfig.vm.host_name = "k8s-w0"
subconfig.vm.network "private_network", ip: "192.168.20.100"
subconfig.vm.network "forwarded_port", guest: 22, host: 60010, auto_correct: true, id: "ssh"
subconfig.vm.synced_folder "./", "/vagrant", disabled: true
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/init_cfg.sh", args: [ K8SV, CONTAINERDV]
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/k8s-w.sh"
subconfig.vm.provision "shell", path: "https://raw.githubusercontent.com/gasida/vagrant-lab/refs/heads/main/cilium-study/5w/route-add2.sh"
end
end
- VirtualBox 관련 설정 제거 (
vb.customize,vb.name,vb.linked_clone) - provider를
libvirt로 변경
(6) 클러스터 실행
1
vagrant up --provider=libvirt
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
...
==> k8s-ctr: Running provisioner: shell...
k8s-ctr: Running: /tmp/vagrant-shell20250815-120434-uhtz9s.sh
k8s-ctr: >>>> K8S Controlplane config Start <<<<
k8s-ctr: [TASK 1] Initial Kubernetes
k8s-w1: >>>> Initial Config End <<<<
==> k8s-w1: Running provisioner: shell...
k8s-w1: Running: /tmp/vagrant-shell20250815-120434-susr2r.sh
k8s-w1: >>>> K8S Node config Start <<<<
k8s-w1: [TASK 1] K8S Controlplane Join
k8s-w0: >>>> Initial Config End <<<<
==> k8s-w0: Running provisioner: shell...
k8s-w0: Running: /tmp/vagrant-shell20250815-120434-gmyjn3.sh
k8s-w0: >>>> K8S Node config Start <<<<
k8s-w0: [TASK 1] K8S Controlplane Join
k8s-ctr: [TASK 2] Setting kube config file
k8s-ctr: [TASK 3] Source the completion
k8s-ctr: [TASK 4] Alias kubectl to k
k8s-ctr: [TASK 5] Install Kubectx & Kubens
k8s-ctr: [TASK 6] Install Kubeps & Setting PS1
k8s-ctr: [TASK 7] Install Cilium CNI
k8s-ctr: [TASK 8] Install Cilium / Hubble CLI
k8s-ctr: cilium
k8s-w1: >>>> K8S Node config End <<<<
==> k8s-w1: Running provisioner: shell...
k8s-w1: Running: /tmp/vagrant-shell20250815-120434-45fmm8.sh
k8s-w1: >>>> Route Add Config Start <<<<
k8s-w1: >>>> Route Add Config End <<<<
k8s-ctr: hubble
k8s-ctr: [TASK 9] Remove node taint
k8s-ctr: node/k8s-ctr untainted
k8s-ctr: [TASK 10] local DNS with hosts file
k8s-ctr: [TASK 11] Dynamically provisioning persistent local storage with Kubernetes
k8s-ctr: [TASK 13] Install Metrics-server
k8s-ctr: [TASK 14] Install k9s
k8s-ctr: >>>> K8S Controlplane Config End <<<<
==> k8s-ctr: Running provisioner: shell...
k8s-ctr: Running: /tmp/vagrant-shell20250815-120434-5mw3lc.sh
k8s-ctr: >>>> Route Add Config Start <<<<
k8s-ctr: >>>> Route Add Config End <<<<
k8s-w0: >>>> K8S Node config End <<<<
==> k8s-w0: Running provisioner: shell...
k8s-w0: Running: /tmp/vagrant-shell20250815-120434-dtpox6.sh
k8s-w0: >>>> Route Add Config Start <<<<
k8s-w0: >>>> Route Add Config End <<<<
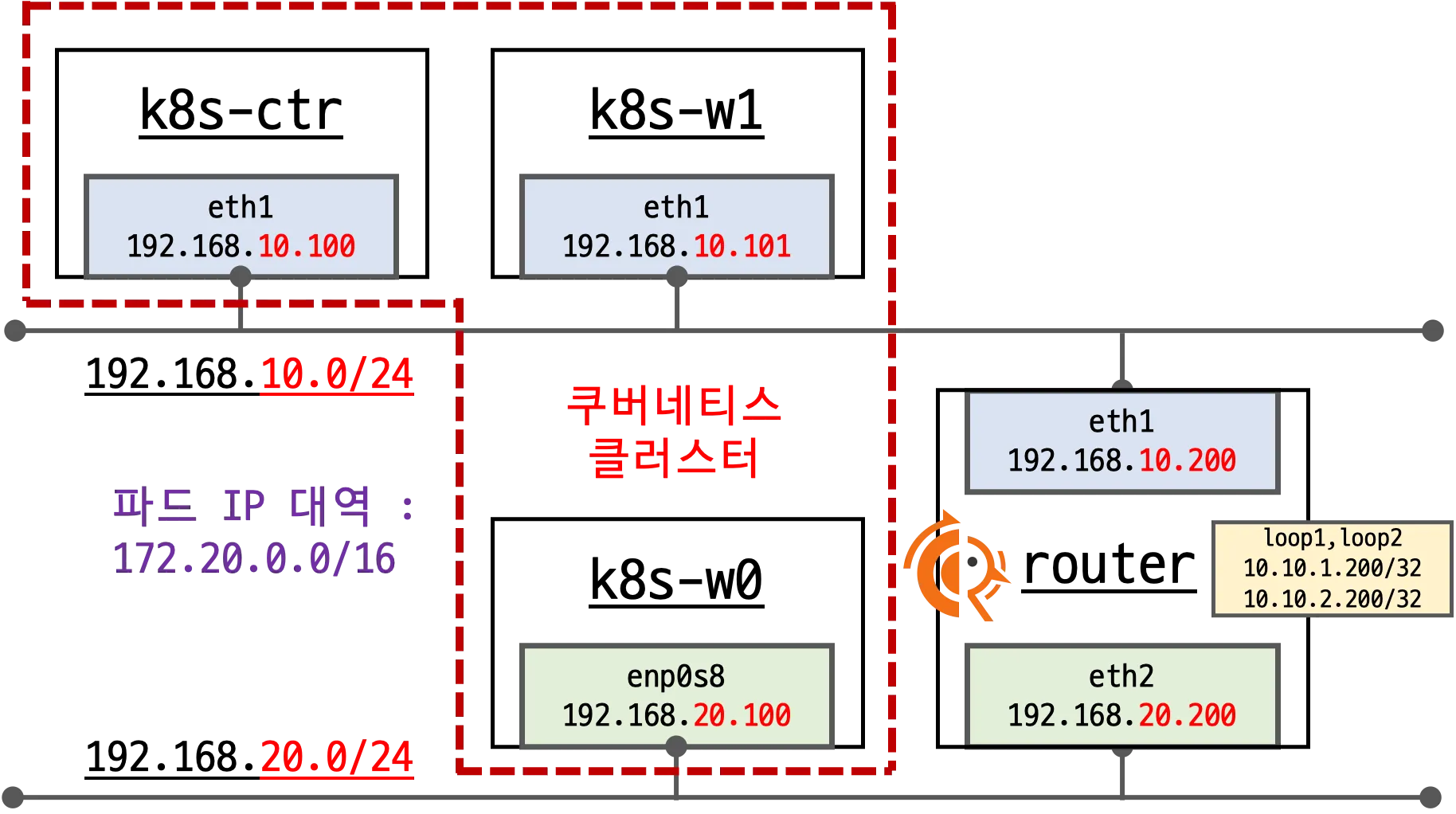
3. 라우팅 및 BGP 실습
- https://docs.frrouting.org/en/stable-10.4/about.html
- FRR(FRRouting) 설치 후 BGP 기반 네트워크 실습 구성
bgpControlPlane.enabled=true설정autoDirectNodeRoutes=false→ 같은 네트워크 노드에서 다른 노드의 pod CIDR 추가하는 것 비활성화
1
2
3
4
5
6
7
cat <<EOT>> /etc/netplan/50-vagrant.yaml
routes:
- to: 192.168.20.0/24
via: 192.168.10.200
# - to: 172.20.0.0/16
# via: 192.168.10.200
EOT
1
2
3
4
5
6
7
cat <<EOT>> /etc/netplan/50-vagrant.yaml
routes:
- to: 192.168.10.0/24
via: 192.168.20.200
# - to: 172.20.0.0/16
# via: 192.168.20.200
EOT
- 내부망 최소 라우팅 규칙만 추가
- BGP를 통해 라우팅 정보 교환 및 광고 설정
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
echo "[TASK 7] Configure FRR"
apt install frr -y >/dev/null 2>&1
sed -i "s/^bgpd=no/bgpd=yes/g" /etc/frr/daemons
NODEIP=$(ip -4 addr show eth1 | grep -oP '(?<=inet\s)\d+(\.\d+){3}')
cat << EOF >> /etc/frr/frr.conf
!
router bgp 65000
bgp router-id $NODEIP
bgp graceful-restart
no bgp ebgp-requires-policy
bgp bestpath as-path multipath-relax
maximum-paths 4
network 10.10.1.0/24
EOF
systemctl daemon-reexec >/dev/null 2>&1
systemctl restart frr >/dev/null 2>&1
systemctl enable frr >/dev/null 2>&1
- 라우터 VM에도 FRR 설치 및
bgpd=yes적용 후 BGP 라우터로 동작
🖥️ [k8s-ctr] 접속 후 기본 정보 확인
1. 컨트롤 플레인에서 각 노드(k8s-w0, k8s-w1, router)에 SSH 접근 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# for i in k8s-w0 k8s-w1 router ; do echo ">> node : $i <<"; sshpass -p 'vagrant' ssh -o StrictHostKeyChecking=no vagrant@$i hostname; echo; done
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
>> node : k8s-w0 <<
Warning: Permanently added 'k8s-w0' (ED25519) to the list of known hosts.
k8s-w0
>> node : k8s-w1 <<
Warning: Permanently added 'k8s-w1' (ED25519) to the list of known hosts.
k8s-w1
>> node : router <<
Warning: Permanently added 'router' (ED25519) to the list of known hosts.
router
2. 노드 Join 문제 확인
(1) 문제 상황
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get node -owide
✅ 출력
1
2
3
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
k8s-ctr Ready control-plane 4m25s v1.33.2 192.168.10.100 <none> Ubuntu 24.04.2 LTS 6.8.0-64-generic containerd://1.7.27
k8s-w1 Ready <none> 4m11s v1.33.2 192.168.10.101 <none> Ubuntu 24.04.2 LTS 6.8.0-64-generic containerd://1.7.27
kubectl get node결과에서k8s-w0노드가 표시되지 않음
(2) 원인 파악
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
vagrant ssh k8s-w0
root@k8s-w0:~# cat /root/kubeadm-join-worker-config.yaml
apiVersion: kubeadm.k8s.io/v1beta4
kind: JoinConfiguration
discovery:
bootstrapToken:
token: "123456.1234567890123456"
apiServerEndpoint: "192.168.10.100:6443"
unsafeSkipCAVerification: true
nodeRegistration:
criSocket: "unix:///run/containerd/containerd.sock"
kubeletExtraArgs:
- name: node-ip
value: "192.168.20.100"
- 설정파일에 더미토큰이 하드코딩 되어있어서 join 실패
(3) 해결 과정
1
2
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubeadm token create --ttl=72h
9llwjd.azxcrk0wd8lkrh45
- 컨트롤 플레인에서 새 토큰 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
root@k8s-w0:~# sudo sed -i 's/123456.1234567890123456/9llwjd.azxcrk0wd8lkrh45/g' /root/kubeadm-join-worker-config.yaml
root@k8s-w0:~# cat /root/kubeadm-join-worker-config.yaml
apiVersion: kubeadm.k8s.io/v1beta4
kind: JoinConfiguration
discovery:
bootstrapToken:
token: "9llwjd.azxcrk0wd8lkrh45"
apiServerEndpoint: "192.168.10.100:6443"
unsafeSkipCAVerification: true
nodeRegistration:
criSocket: "unix:///run/containerd/containerd.sock"
kubeletExtraArgs:
- name: node-ip
value: "192.168.20.100"
- 워커노드0 설정 파일 내 토큰 값 교체
1
2
root@k8s-w0:~# sudo kubeadm reset -f
root@k8s-w0:~# sudo kubeadm join --config="/root/kubeadm-join-worker-config.yaml"
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
[preflight] Running pre-flight checks
W0815 22:41:14.831416 4224 removeetcdmember.go:106] [reset] No kubeadm config, using etcd pod spec to get data directory
[reset] Deleted contents of the etcd data directory: /var/lib/etcd
[reset] Stopping the kubelet service
[reset] Unmounting mounted directories in "/var/lib/kubelet"
[reset] Deleting contents of directories: [/etc/kubernetes/manifests /var/lib/kubelet /etc/kubernetes/pki]
[reset] Deleting files: [/etc/kubernetes/admin.conf /etc/kubernetes/super-admin.conf /etc/kubernetes/kubelet.conf /etc/kubernetes/bootstrap-kubelet.conf /etc/kubernetes/controller-manager.conf /etc/kubernetes/scheduler.conf]
The reset process does not perform cleanup of CNI plugin configuration,
network filtering rules and kubeconfig files.
For information on how to perform this cleanup manually, please see:
https://k8s.io/docs/reference/setup-tools/kubeadm/kubeadm-reset/
[preflight] Running pre-flight checks
[preflight] Reading configuration from the "kubeadm-config" ConfigMap in namespace "kube-system"...
[preflight] Use 'kubeadm init phase upload-config --config your-config-file' to re-upload it.
[kubelet-start] Writing kubelet configuration to file "/var/lib/kubelet/config.yaml"
[kubelet-start] Writing kubelet environment file with flags to file "/var/lib/kubelet/kubeadm-flags.env"
[kubelet-start] Starting the kubelet
[kubelet-check] Waiting for a healthy kubelet at http://127.0.0.1:10248/healthz. This can take up to 4m0s
[kubelet-check] The kubelet is healthy after 1.002299091s
[kubelet-start] Waiting for the kubelet to perform the TLS Bootstrap
This node has joined the cluster:
* Certificate signing request was sent to apiserver and a response was received.
* The Kubelet was informed of the new secure connection details.
Run 'kubectl get nodes' on the control-plane to see this node join the cluster.
kubeadm reset -f후kubeadm join재실행
(4) 결과
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get nodes -owide
✅ 출력
1
2
3
4
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
k8s-ctr Ready control-plane 10m v1.33.2 192.168.10.100 <none> Ubuntu 24.04.2 LTS 6.8.0-64-generic containerd://1.7.27
k8s-w0 Ready <none> 53s v1.33.2 192.168.20.100 <none> Ubuntu 24.04.2 LTS 6.8.0-64-generic containerd://1.7.27
k8s-w1 Ready <none> 10m v1.33.2 192.168.10.101 <none> Ubuntu 24.04.2 LTS 6.8.0-64-generic containerd://1.7.27
- 모든 노드(
k8s-ctr,k8s-w0,k8s-w1) 정상 연결
⚙️ [k8s-ctr] cilium 설정 확인
Cilium에서 BGP Control Plane 기능 활성화 여부 확인
1
2
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium config view | grep -i bgp
✅ 출력
1
2
3
4
5
bgp-router-id-allocation-ip-pool
bgp-router-id-allocation-mode default
bgp-secrets-namespace kube-system
enable-bgp-control-plane true
enable-bgp-control-plane-status-report true
enable-bgp-control-plane = true상태 확인 완료
🌐 네트워크 정보 확인
1. router 네트워크 인터페이스 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router ip -br -c -4 addr
✅ 출력
1
2
3
4
5
6
lo UNKNOWN 127.0.0.1/8
eth0 UP 192.168.121.180/24 metric 100
eth1 UP 192.168.10.200/24
eth2 UP 192.168.20.200/24
loop1 UNKNOWN 10.10.1.200/24
loop2 UNKNOWN 10.10.2.200/24
2. 컨트롤 플레인 네트워크 인터페이스 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# ip -c -4 addr show dev eth1
✅ 출력
1
2
3
4
5
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
altname enp0s6
altname ens6
inet 192.168.10.100/24 brd 192.168.10.255 scope global eth1
valid_lft forever preferred_lft forever
3. 워커노드 네트워크 인터페이스 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# for i in w1 w0 ; do echo ">> node : k8s-$i <<"; sshpass -p 'vagrant' ssh vagrant@k8s-$i ip -c -4 addr show dev eth1; echo; done
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
>> node : k8s-w1 <<
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
altname enp0s6
altname ens6
inet 192.168.10.101/24 brd 192.168.10.255 scope global eth1
valid_lft forever preferred_lft forever
>> node : k8s-w0 <<
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
altname enp0s6
altname ens6
inet 192.168.20.100/24 brd 192.168.20.255 scope global eth1
valid_lft forever preferred_lft forever
k8s-w1:192.168.10.101/24→ 컨트롤 플레인과 같은 대역k8s-w0:192.168.20.100/24
4. router 라우팅 정보 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router ip -c route
✅ 출력
1
2
3
4
5
6
7
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.25 metric 100
10.10.1.0/24 dev loop1 proto kernel scope link src 10.10.1.200
10.10.2.0/24 dev loop2 proto kernel scope link src 10.10.2.200
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.200
192.168.20.0/24 dev eth2 proto kernel scope link src 192.168.20.200
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.25 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.25 metric 100
192.168.10.0/24와192.168.20.0/24라우팅 처리
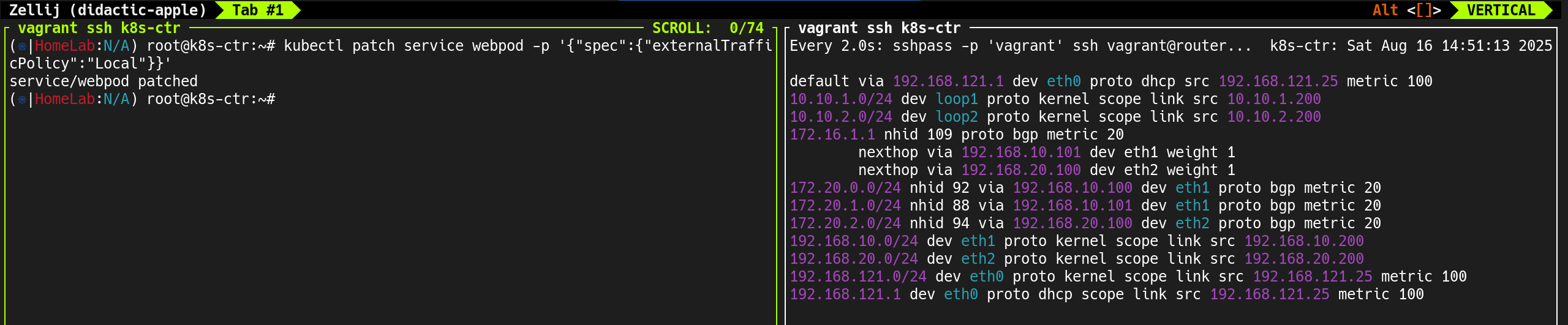
5. 컨트롤 플레인 라우팅 정보 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# ip -c route
✅ 출력
1
2
3
4
5
6
7
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.70 metric 100
172.20.0.0/24 via 172.20.0.230 dev cilium_host proto kernel src 172.20.0.230
172.20.0.230 dev cilium_host proto kernel scope link
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.100
192.168.20.0/24 via 192.168.10.200 dev eth1 proto static
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.70 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.70 metric 100
autoDirectNodeRoutes=false설정으로 인해 Pod CIDR 자동 경로 등록이 비활성화됨- 따라서 같은 네트워크 대역에 있더라도 상대방 Pod CIDR가 라우팅 테이블에 존재하지 않음
- 컨트롤 플레인(
k8s-ctr)은 자신의 PodCIDR(172.20.0.0/24)만 가지고 있음
6. 워커노드 라우팅 정보 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# for i in w1 w0 ; do echo ">> node : k8s-$i <<"; sshpass -p 'vagrant' ssh vagrant@k8s-$i ip -c route; echo; done
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
>> node : k8s-w1 <<
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.62 metric 100
172.20.1.0/24 via 172.20.1.4 dev cilium_host proto kernel src 172.20.1.4
172.20.1.4 dev cilium_host proto kernel scope link
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.101
192.168.20.0/24 via 192.168.10.200 dev eth1 proto static
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.62 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.62 metric 100
>> node : k8s-w0 <<
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.122 metric 100
172.20.2.0/24 via 172.20.2.89 dev cilium_host proto kernel src 172.20.2.89
172.20.2.89 dev cilium_host proto kernel scope link
192.168.10.0/24 via 192.168.20.200 dev eth1 proto static
192.168.20.0/24 dev eth1 proto kernel scope link src 192.168.20.100
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.122 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.122 metric 100
- 각 워커 노드(
k8s-w1,k8s-w0)도 자신의 PodCIDR만 등록되어 있음 autoDirectNodeRoutes=false때문에 다른 노드의 Pod CIDR은 자동으로 추가되지 않음
📦 샘플 애플리케이션 배포 및 통신 문제 확인
1. 샘플 애플리케이션 배포
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
(⎈|HomeLab:N/A) root@k8s-ctr:~# cat << EOF | kubectl apply -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: webpod
spec:
replicas: 3
selector:
matchLabels:
app: webpod
template:
metadata:
labels:
app: webpod
spec:
affinity:
podAntiAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
- labelSelector:
matchExpressions:
- key: app
operator: In
values:
- sample-app
topologyKey: "kubernetes.io/hostname"
containers:
- name: webpod
image: traefik/whoami
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: webpod
labels:
app: webpod
spec:
selector:
app: webpod
ports:
- protocol: TCP
port: 80
targetPort: 80
type: ClusterIP
EOF
# 결과
deployment.apps/webpod created
service/webpod created
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
(⎈|HomeLab:N/A) root@k8s-ctr:~# cat <<EOF | kubectl apply -f -
apiVersion: v1
kind: Pod
metadata:
name: curl-pod
labels:
app: curl
spec:
nodeName: k8s-ctr
containers:
- name: curl
image: nicolaka/netshoot
command: ["tail"]
args: ["-f", "/dev/null"]
terminationGracePeriodSeconds: 0
EOF
# 결과
pod/curl-pod created
2. Pod 스케줄링 및 서비스 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get deploy,svc,ep webpod -owide
✅ 출력
1
2
3
4
5
6
7
8
9
Warning: v1 Endpoints is deprecated in v1.33+; use discovery.k8s.io/v1 EndpointSlice
NAME READY UP-TO-DATE AVAILABLE AGE CONTAINERS IMAGES SELECTOR
deployment.apps/webpod 3/3 3 3 2m23s webpod traefik/whoami app=webpod
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
service/webpod ClusterIP 10.96.54.159 <none> 80/TCP 2m23s app=webpod
NAME ENDPOINTS AGE
endpoints/webpod 172.20.0.158:80,172.20.1.65:80,172.20.2.204:80 2m23s
podAntiAffinity설정으로 인해 파드가 노드별로 분산 배치됨- Service: ClusterIP
10.96.54.159할당 - Endpoints: 3개 파드 각각 다른 PodCIDR(
172.20.0.x,172.20.1.x,172.20.2.x)에 분산
3. Cilium Endpoint 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ciliumendpoints
✅ 출력
1
2
3
4
5
NAME SECURITY IDENTITY ENDPOINT STATE IPV4 IPV6
curl-pod 64126 ready 172.20.0.64
webpod-697b545f57-fbtbj 38082 ready 172.20.0.158
webpod-697b545f57-pxhvr 38082 ready 172.20.1.65
webpod-697b545f57-rpblf 38082 ready 172.20.2.204
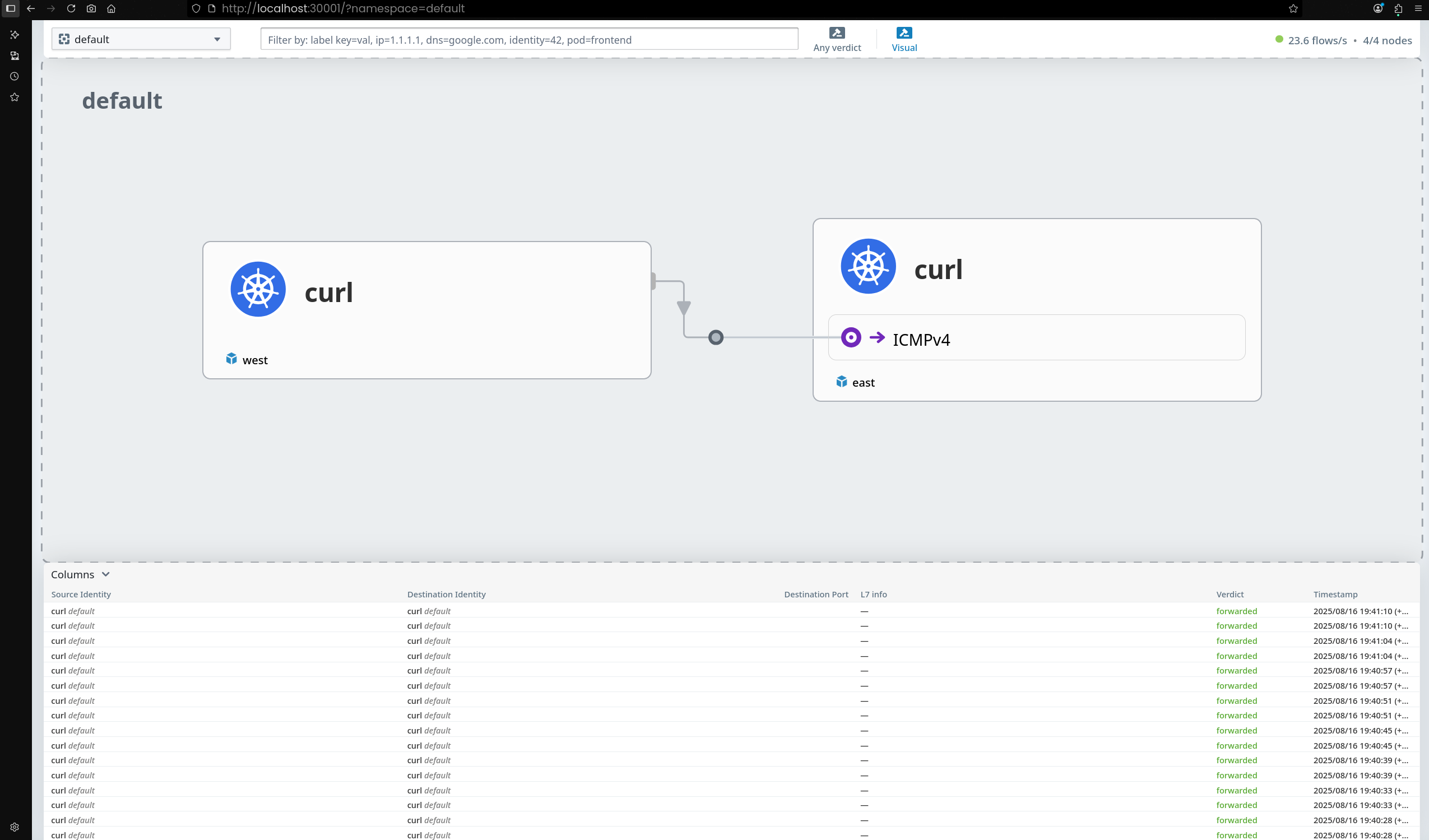
curl-pod→172.20.0.64(컨트롤 플레인)webpod3개 파드 →172.20.0.158,172.20.1.65,172.20.2.204
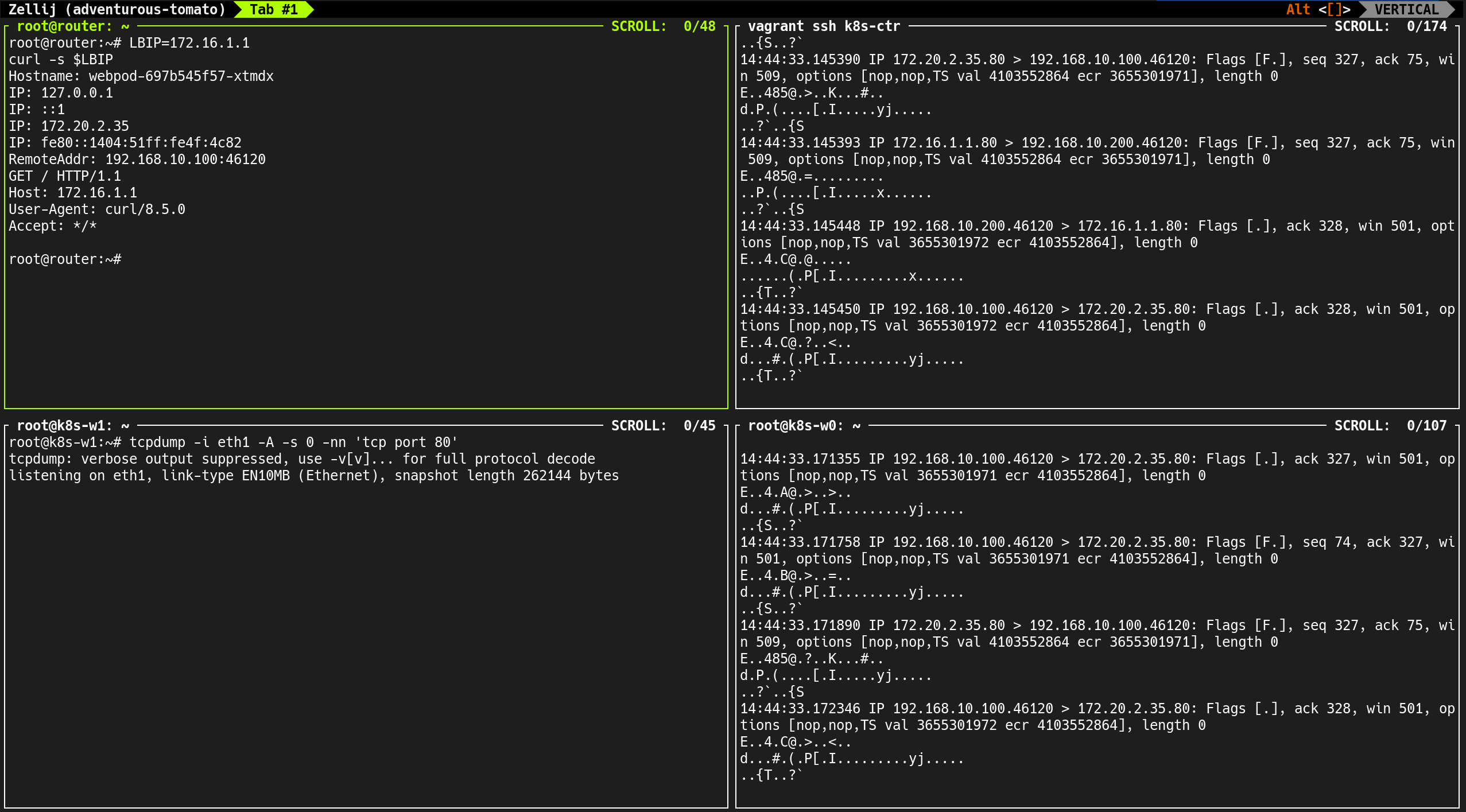
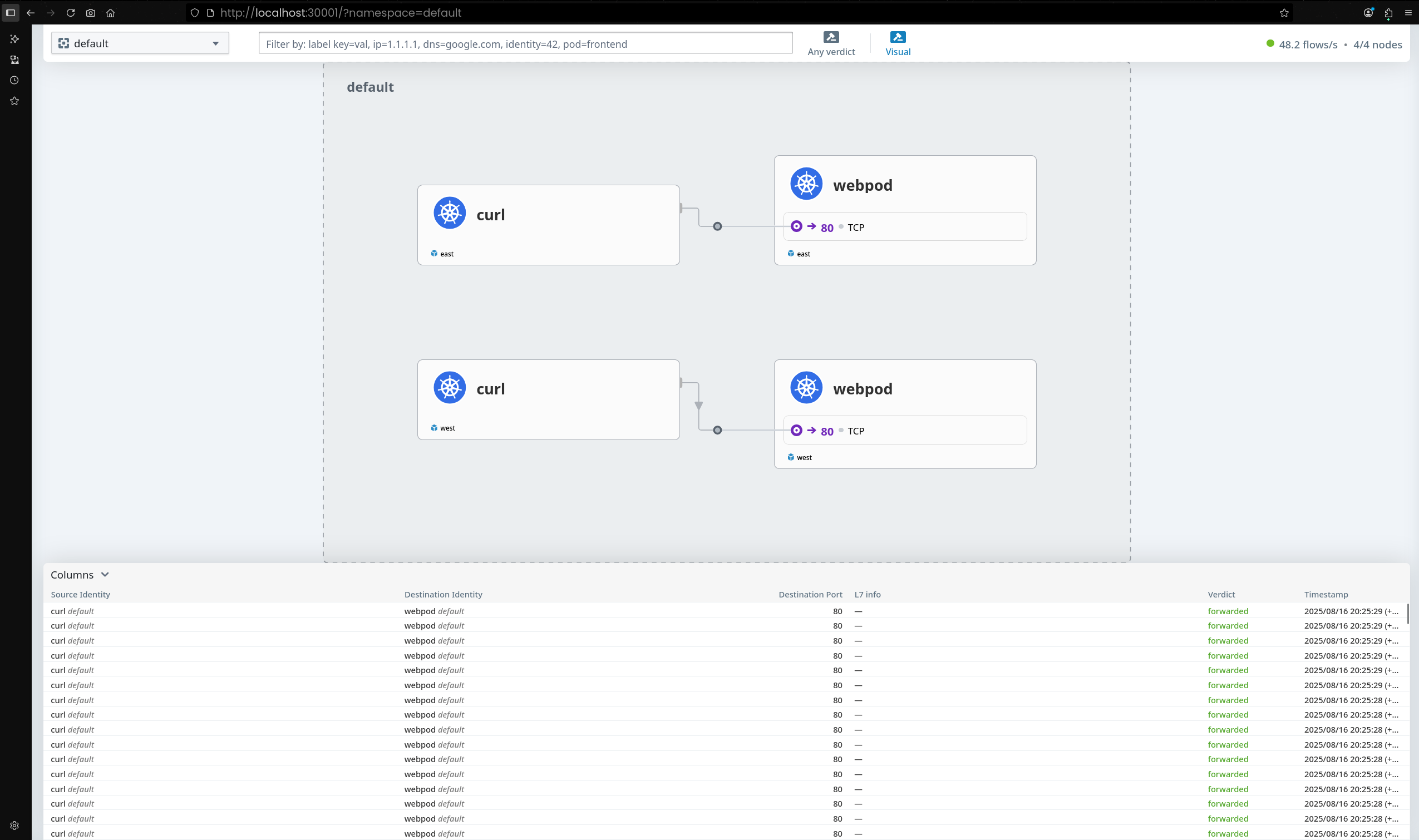
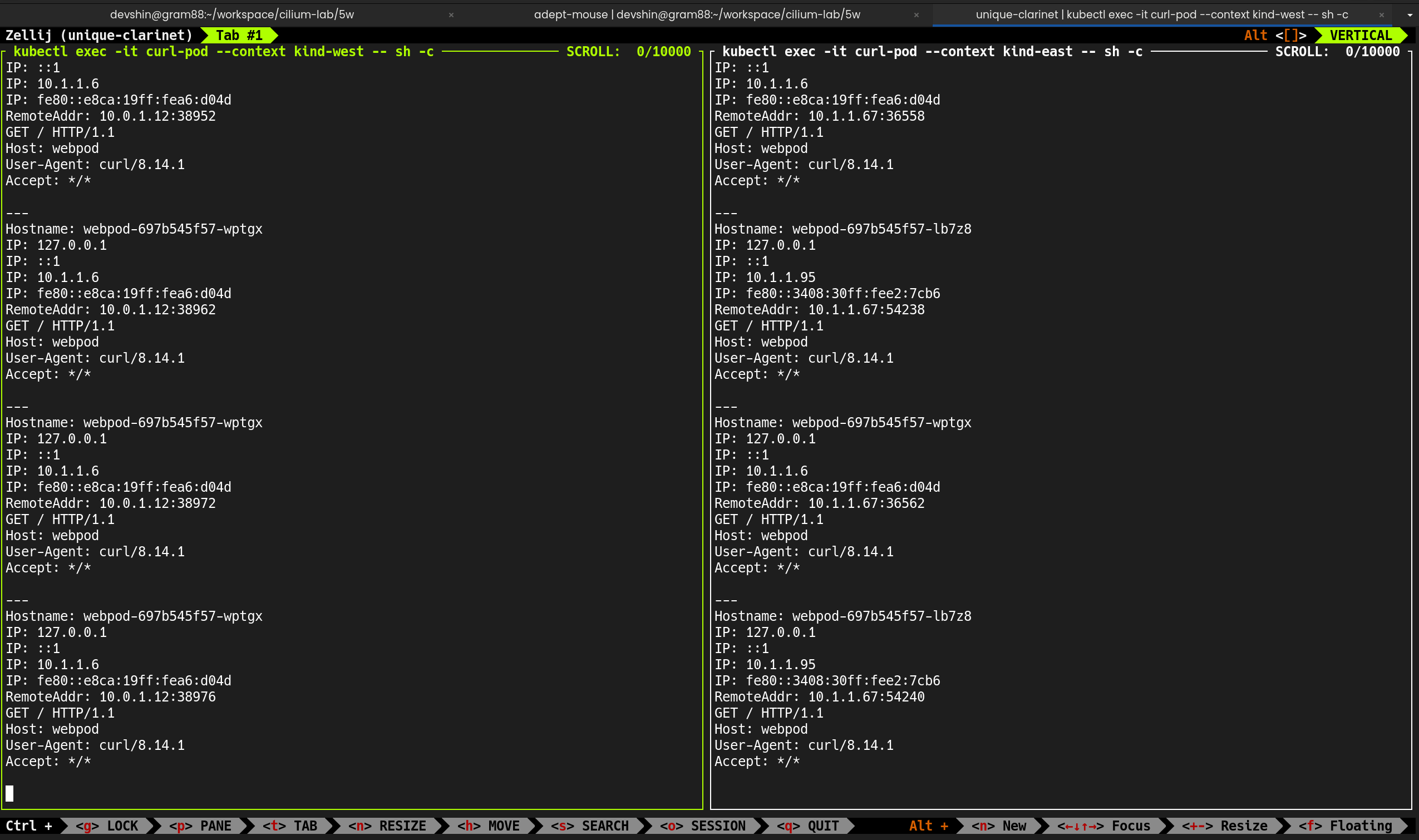
4. 통신 테스트 진행
curl-pod에서 webpod 서비스로 반복 요청 수행
1
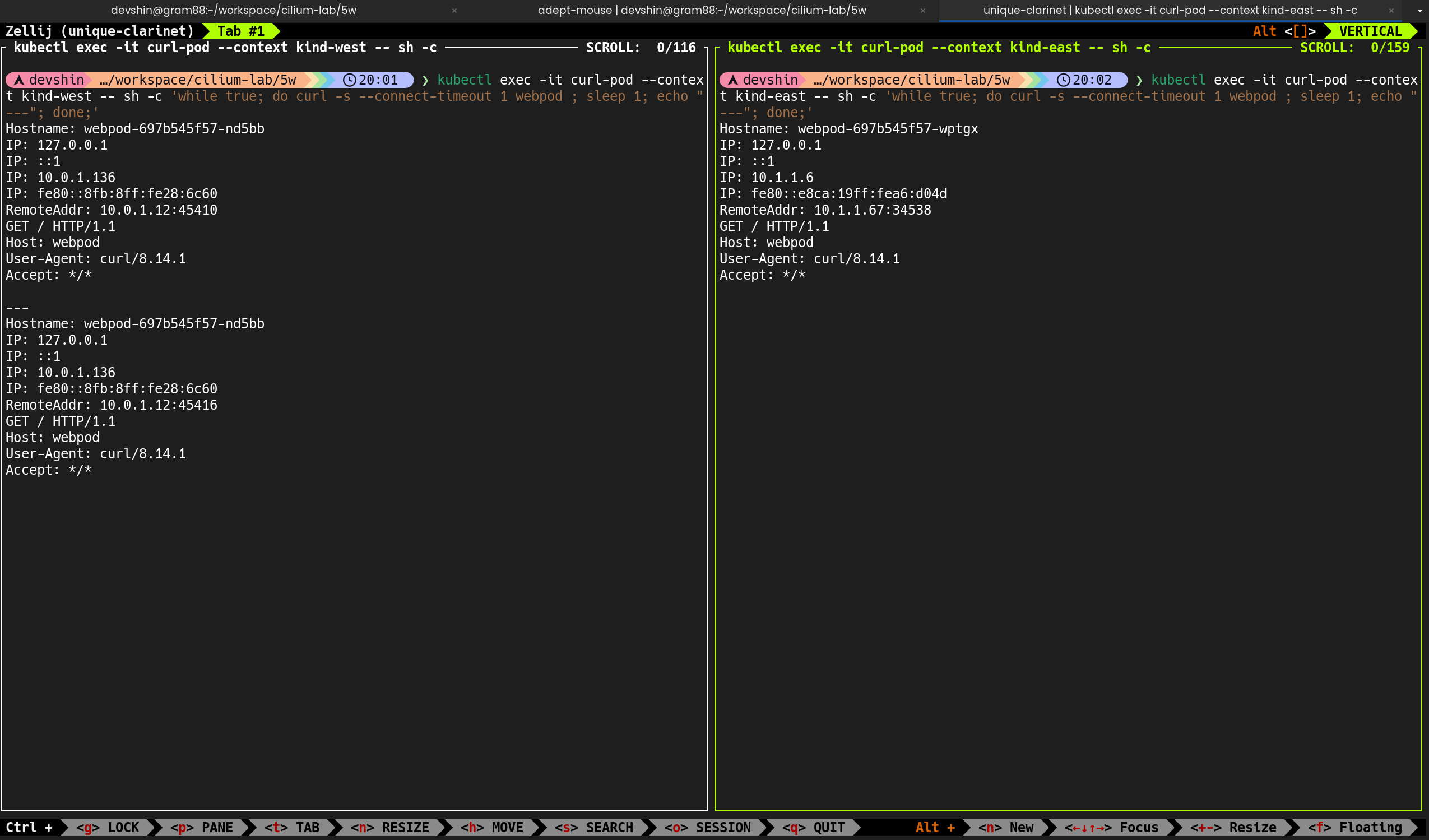
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl exec -it curl-pod -- sh -c 'while true; do curl -s --connect-timeout 1 webpod | grep Hostname; echo "---" ; sleep 1; done'
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
---
---
---
---
---
Hostname: webpod-697b545f57-fbtbj
---
---
---
Hostname: webpod-697b545f57-fbtbj
---
---
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-fbtbj
---
---
...
--connect-timeout 1옵션을 줘서 1초 이내 응답 없으면 연결 종료k8s-ctr에 배포된webpod파드(172.20.0.158)만 응답- 다른 노드(
k8s-w1,k8s-w0)에 위치한webpod파드들은 응답하지 못함
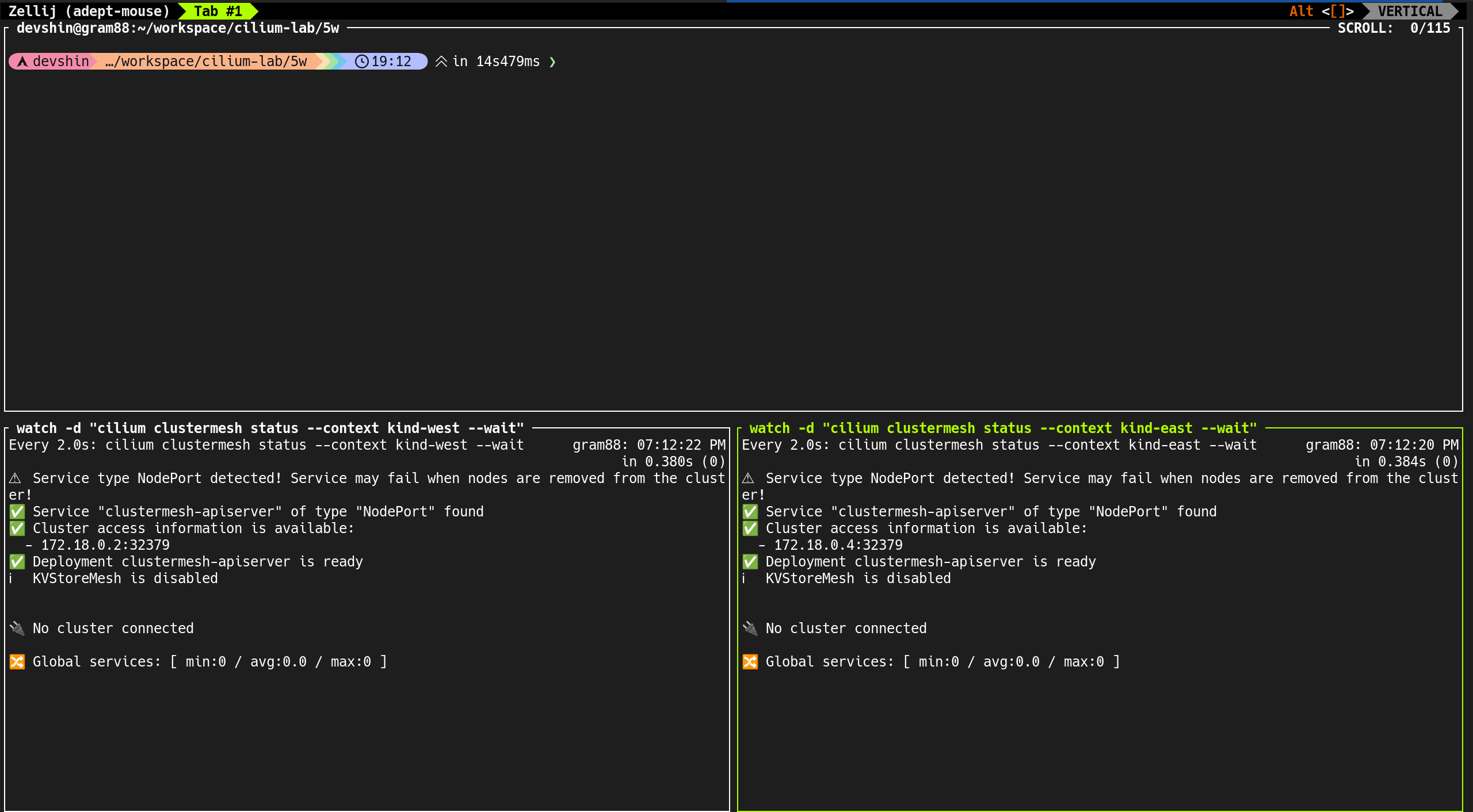
📡 Cilium BGP Control Plane
- https://docs.cilium.io/en/stable/network/bgp-control-plane/bgp-control-plane-v2/
- BGP 설정 후 통신 확인 : Cilium의 BGP는 기본적으로 외부 경로를 커널 라우팅 테이블에 주입하지 않음
1. FRR 프로세스 상태 확인
1
2
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router
root@router:~# ss -tnlp | grep -iE 'zebra|bgpd'
✅ 출력
1
2
3
4
LISTEN 0 3 127.0.0.1:2601 0.0.0.0:* users:(("zebra",pid=3827,fd=23))
LISTEN 0 3 127.0.0.1:2605 0.0.0.0:* users:(("bgpd",pid=3832,fd=18))
LISTEN 0 4096 0.0.0.0:179 0.0.0.0:* users:(("bgpd",pid=3832,fd=22))
LISTEN 0 4096 [::]:179 [::]:* users:(("bgpd",pid=3832,fd=23))
- BGP 관련 포트(
179) 리슨 중
1
root@router:~# ps -ef |grep frr
✅ 출력
1
2
3
4
5
root 3814 1 0 22:30 ? 00:00:00 /usr/lib/frr/watchfrr -d -F traditional zebra bgpd staticd
frr 3827 1 0 22:30 ? 00:00:00 /usr/lib/frr/zebra -d -F traditional -A 127.0.0.1 -s 90000000
frr 3832 1 0 22:30 ? 00:00:00 /usr/lib/frr/bgpd -d -F traditional -A 127.0.0.1
frr 3839 1 0 22:30 ? 00:00:00 /usr/lib/frr/staticd -d -F traditional -A 127.0.0.1
root 4417 4399 0 23:02 pts/1 00:00:00 grep --color=auto frr
watchfrr,zebra,bgpd,staticd프로세스 구동 확인
2. FRR 설정 확인 (vtysh)
1
root@router:~# vtysh -c 'show running'
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
Building configuration...
Current configuration:
!
frr version 8.4.4
frr defaults traditional
hostname router
log syslog informational
no ipv6 forwarding
service integrated-vtysh-config
!
router bgp 65000
bgp router-id 192.168.10.200
no bgp ebgp-requires-policy
bgp graceful-restart
bgp bestpath as-path multipath-relax
!
address-family ipv4 unicast
network 10.10.1.0/24
maximum-paths 4
exit-address-family
exit
!
end
- Router BGP AS 번호는
65000 - Loopback 네트워크
10.10.1.0/24를 광고하도록 설정됨 - 멀티패스(
maximum-paths 4) 허용 설정 적용
3. FRR 설정 파일 확인
1
root@router:~# cat /etc/frr/frr.conf
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
# default to using syslog. /etc/rsyslog.d/45-frr.conf places the log in
# /var/log/frr/frr.log
#
# Note:
# FRR's configuration shell, vtysh, dynamically edits the live, in-memory
# configuration while FRR is running. When instructed, vtysh will persist the
# live configuration to this file, overwriting its contents. If you want to
# avoid this, you can edit this file manually before starting FRR, or instruct
# vtysh to write configuration to a different file.
log syslog informational
!
router bgp 65000
bgp router-id 192.168.10.200
bgp graceful-restart
no bgp ebgp-requires-policy
bgp bestpath as-path multipath-relax
maximum-paths 4
network 10.10.1.0/24
/etc/frr/frr.conf파일에서 동일한 설정 확인 가능network 10.10.1.0/24광고 중
4. BGP 상태 확인
1
root@router:~# vtysh -c 'show ip bgp summary'
✅ 출력
1
% No BGP neighbors found in VRF default
- 아직 Neighbor 없음
1
root@router:~# vtysh -c 'show ip bgp'
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
BGP table version is 1, local router ID is 192.168.10.200, vrf id 0
Default local pref 100, local AS 65000
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop's vrf id, < announce-nh-self
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 10.10.1.0/24 0.0.0.0 0 32768 i
Displayed 1 routes and 1 total paths
- 자신이 보유한
10.10.1.0/24네트워크만 광고 중 - 외부 노드와 연결되지 않아 BGP 테이블은 단일 엔트리만 존재
5. router 네트워크 인터페이스 확인
1
root@router:~# ip -c addr
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:97:4b:c4 brd ff:ff:ff:ff:ff:ff
altname enp0s5
altname ens5
inet 192.168.121.25/24 metric 100 brd 192.168.121.255 scope global dynamic eth0
valid_lft 2869sec preferred_lft 2869sec
inet6 fe80::5054:ff:fe97:4bc4/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:24:2d:30 brd ff:ff:ff:ff:ff:ff
altname enp0s6
altname ens6
inet 192.168.10.200/24 brd 192.168.10.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::5054:ff:fe24:2d30/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 52:54:00:50:33:eb brd ff:ff:ff:ff:ff:ff
altname enp0s7
altname ens7
inet 192.168.20.200/24 brd 192.168.20.255 scope global eth2
valid_lft forever preferred_lft forever
inet6 fe80::5054:ff:fe50:33eb/64 scope link
valid_lft forever preferred_lft forever
5: loop1: <BROADCAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN group default qlen 1000
link/ether 22:63:e6:d9:f6:95 brd ff:ff:ff:ff:ff:ff
inet 10.10.1.200/24 scope global loop1
valid_lft forever preferred_lft forever
inet6 fe80::2063:e6ff:fed9:f695/64 scope link
valid_lft forever preferred_lft forever
6: loop2: <BROADCAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc noqueue state UNKNOWN group default qlen 1000
link/ether 6e:08:a4:e5:88:c0 brd ff:ff:ff:ff:ff:ff
inet 10.10.2.200/24 scope global loop2
valid_lft forever preferred_lft forever
inet6 fe80::6c08:a4ff:fee5:88c0/64 scope link
valid_lft forever preferred_lft forever
loop1:10.10.1.200/24
6. router 라우팅 테이블 확인
1
root@router:~# ip -c route
✅ 출력
1
2
3
4
5
6
7
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.25 metric 100
10.10.1.0/24 dev loop1 proto kernel scope link src 10.10.1.200
10.10.2.0/24 dev loop2 proto kernel scope link src 10.10.2.200
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.200
192.168.20.0/24 dev eth2 proto kernel scope link src 192.168.20.200
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.25 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.25 metric 100
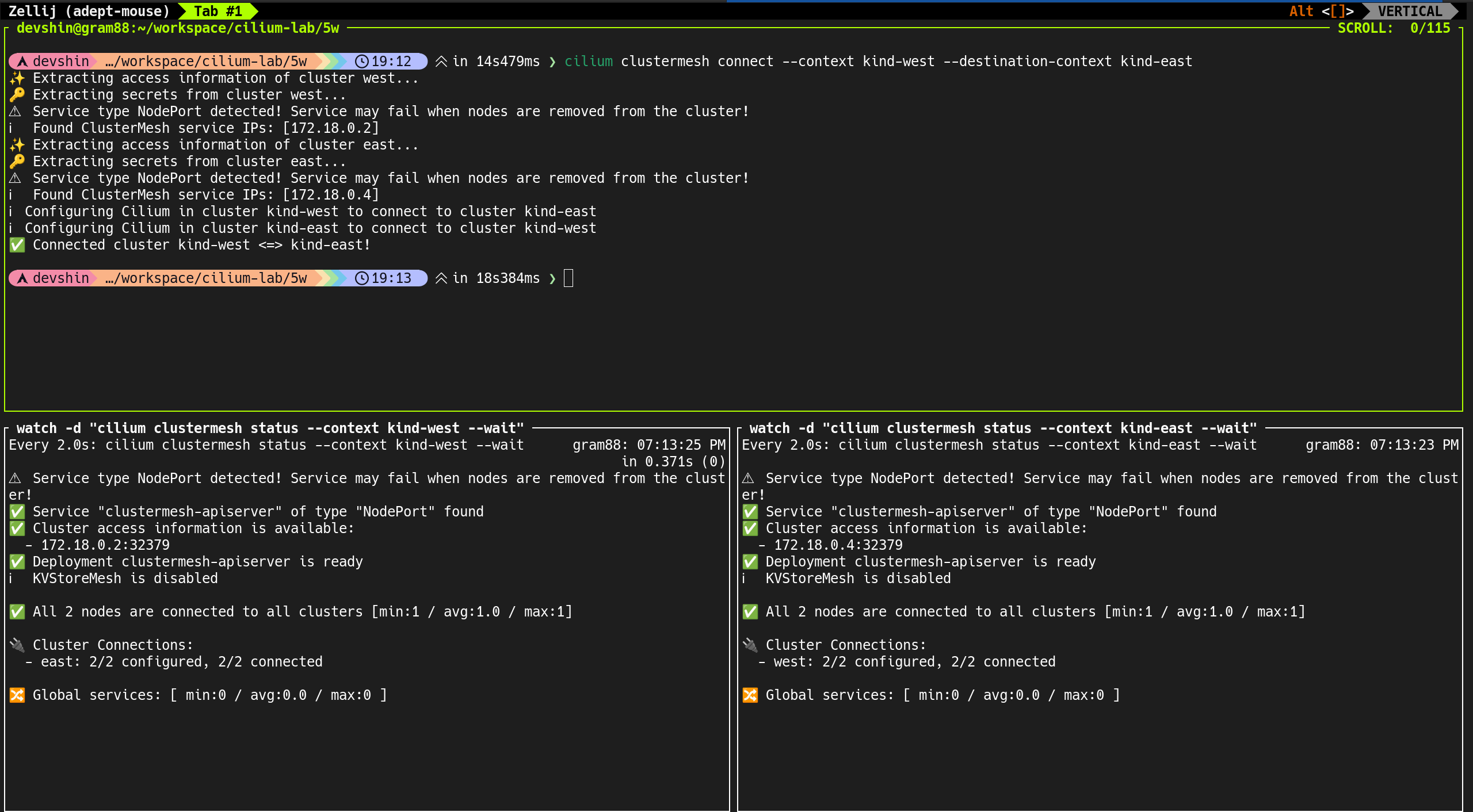
7. BGP Neighbor 설정 추가
router에서 Cilium 노드(k8s-ctr, k8s-w1, k8s-w0)를 Neighbor로 등록
1
2
3
4
5
6
7
root@router:~# cat << EOF >> /etc/frr/frr.conf
neighbor CILIUM peer-group
neighbor CILIUM remote-as external
neighbor 192.168.10.100 peer-group CILIUM
neighbor 192.168.10.101 peer-group CILIUM
neighbor 192.168.20.100 peer-group CILIUM
EOF
peer-groupCILIUM으로 묶어 관리 단순화remote-as external옵션으로 다른 AS 자동 수용
1
root@router:~# cat /etc/frr/frr.conf
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# default to using syslog. /etc/rsyslog.d/45-frr.conf places the log in
# /var/log/frr/frr.log
#
# Note:
# FRR's configuration shell, vtysh, dynamically edits the live, in-memory
# configuration while FRR is running. When instructed, vtysh will persist the
# live configuration to this file, overwriting its contents. If you want to
# avoid this, you can edit this file manually before starting FRR, or instruct
# vtysh to write configuration to a different file.
log syslog informational
!
router bgp 65000
bgp router-id 192.168.10.200
bgp graceful-restart
no bgp ebgp-requires-policy
bgp bestpath as-path multipath-relax
maximum-paths 4
network 10.10.1.0/24
neighbor CILIUM peer-group
neighbor CILIUM remote-as external
neighbor 192.168.10.100 peer-group CILIUM
neighbor 192.168.10.101 peer-group CILIUM
neighbor 192.168.20.100 peer-group CILIUM
- router AS:
65000, 노드 AS:65001
8. FRR 서비스 재시작 및 상태 확인
1
2
root@router:~# systemctl daemon-reexec && systemctl restart frr
root@router:~# systemctl status frr --no-pager --full
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
● frr.service - FRRouting
Loaded: loaded (/usr/lib/systemd/system/frr.service; enabled; preset: enabled)
Active: active (running) since Fri 2025-08-15 23:20:38 KST; 17s ago
Docs: https://frrouting.readthedocs.io/en/latest/setup.html
Process: 4540 ExecStart=/usr/lib/frr/frrinit.sh start (code=exited, status=0/SUCCESS)
Main PID: 4550 (watchfrr)
Status: "FRR Operational"
Tasks: 13 (limit: 757)
Memory: 19.5M (peak: 27.4M)
CPU: 321ms
CGroup: /system.slice/frr.service
├─4550 /usr/lib/frr/watchfrr -d -F traditional zebra bgpd staticd
├─4563 /usr/lib/frr/zebra -d -F traditional -A 127.0.0.1 -s 90000000
├─4568 /usr/lib/frr/bgpd -d -F traditional -A 127.0.0.1
└─4575 /usr/lib/frr/staticd -d -F traditional -A 127.0.0.1
Aug 15 23:20:38 router watchfrr[4550]: [YFT0P-5Q5YX] Forked background command [pid 4551]: /usr/lib/frr/watchfrr.sh restart all
Aug 15 23:20:38 router zebra[4563]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router bgpd[4568]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router staticd[4575]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] zebra state -> up : connect succeeded
Aug 15 23:20:38 router frrinit.sh[4540]: * Started watchfrr
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] bgpd state -> up : connect succeeded
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] staticd state -> up : connect succeeded
Aug 15 23:20:38 router watchfrr[4550]: [KWE5Q-QNGFC] all daemons up, doing startup-complete notify
Aug 15 23:20:38 router systemd[1]: Started frr.service - FRRouting.
9. 모니터링
1
root@router:~# journalctl -u frr -f
✅ 출력
1
2
3
4
5
6
7
8
9
10
Aug 15 23:20:38 router watchfrr[4550]: [YFT0P-5Q5YX] Forked background command [pid 4551]: /usr/lib/frr/watchfrr.sh restart all
Aug 15 23:20:38 router zebra[4563]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router bgpd[4568]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router staticd[4575]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] zebra state -> up : connect succeeded
Aug 15 23:20:38 router frrinit.sh[4540]: * Started watchfrr
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] bgpd state -> up : connect succeeded
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] staticd state -> up : connect succeeded
Aug 15 23:20:38 router watchfrr[4550]: [KWE5Q-QNGFC] all daemons up, doing startup-complete notify
Aug 15 23:20:38 router systemd[1]: Started frr.service - FRRouting.
🛰️ Cilium에 BGP 설정
1. BGP 활성화 노드 라벨 설정
1
2
3
4
5
6
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl label nodes k8s-ctr k8s-w0 k8s-w1 enable-bgp=true
# 결과
node/k8s-ctr labeled
node/k8s-w0 labeled
node/k8s-w1 labeled
- Cilium BGP를 실행할 노드에
enable-bgp=true라벨 부여
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get node -l enable-bgp=true
✅ 출력
1
2
3
4
NAME STATUS ROLES AGE VERSION
k8s-ctr Ready control-plane 53m v1.33.2
k8s-w0 Ready <none> 43m v1.33.2
k8s-w1 Ready <none> 53m v1.33.2
- 3개 노드 라벨링 확인
2. Cilium BGP 리소스 설정
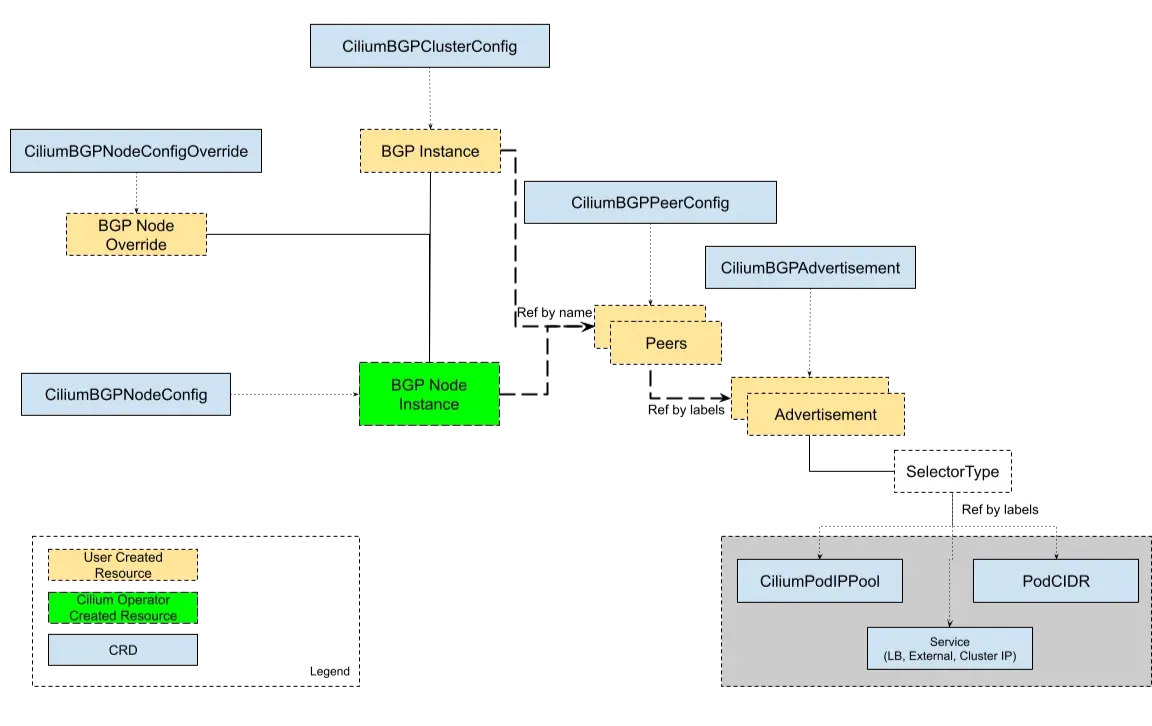
Cilium에서 BGP 동작을 정의하기 위해 3가지 CRD 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
(⎈|HomeLab:N/A) root@k8s-ctr:~# cat << EOF | kubectl apply -f -
apiVersion: cilium.io/v2
kind: CiliumBGPAdvertisement
metadata:
name: bgp-advertisements
labels:
advertise: bgp
spec:
advertisements:
- advertisementType: "PodCIDR"
---
apiVersion: cilium.io/v2
kind: CiliumBGPPeerConfig
metadata:
name: cilium-peer
spec:
timers:
holdTimeSeconds: 9
keepAliveTimeSeconds: 3
ebgpMultihop: 2
gracefulRestart:
enabled: true
restartTimeSeconds: 15
families:
- afi: ipv4
safi: unicast
advertisements:
matchLabels:
advertise: "bgp"
---
apiVersion: cilium.io/v2
kind: CiliumBGPClusterConfig
metadata:
name: cilium-bgp
spec:
nodeSelector:
matchLabels:
"enable-bgp": "true"
bgpInstances:
- name: "instance-65001"
localASN: 65001
peers:
- name: "tor-switch"
peerASN: 65000
peerAddress: 192.168.10.200 # router ip address
peerConfigRef:
name: "cilium-peer"
EOF
ciliumbgpadvertisement.cilium.io/bgp-advertisements created
ciliumbgppeerconfig.cilium.io/cilium-peer created
ciliumbgpclusterconfig.cilium.io/cilium-bgp created
CiliumBGPAdvertisementadvertisementType: PodCIDR설정 → 각 노드의 PodCIDR를 BGP로 광고
CiliumBGPPeerConfigadvertisements.matchLabels: advertise=bgp로 필터링
CiliumBGPClusterConfig- 라벨(
enable-bgp=true)이 지정된 노드만 BGP 동작 대상 - localASN: 65001, peerASN: 65000
- peerAddress:
192.168.10.200(Router IP) - Peer 설정은
cilium-peer레퍼런스를 참조
- 라벨(
1
2
3
4
5
6
7
8
9
10
11
12
13
Aug 15 23:20:38 router watchfrr[4550]: [YFT0P-5Q5YX] Forked background command [pid 4551]: /usr/lib/frr/watchfrr.sh restart all
Aug 15 23:20:38 router zebra[4563]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router bgpd[4568]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router staticd[4575]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] zebra state -> up : connect succeeded
Aug 15 23:20:38 router frrinit.sh[4540]: * Started watchfrr
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] bgpd state -> up : connect succeeded
Aug 15 23:20:38 router watchfrr[4550]: [QDG3Y-BY5TN] staticd state -> up : connect succeeded
Aug 15 23:20:38 router watchfrr[4550]: [KWE5Q-QNGFC] all daemons up, doing startup-complete notify
Aug 15 23:20:38 router systemd[1]: Started frr.service - FRRouting.
Aug 15 23:27:15 router bgpd[4568]: [M59KS-A3ZXZ] bgp_update_receive: rcvd End-of-RIB for IPv4 Unicast from 192.168.20.100 in vrf default
Aug 15 23:27:15 router bgpd[4568]: [M59KS-A3ZXZ] bgp_update_receive: rcvd End-of-RIB for IPv4 Unicast from 192.168.10.100 in vrf default
Aug 15 23:27:15 router bgpd[4568]: [M59KS-A3ZXZ] bgp_update_receive: rcvd End-of-RIB for IPv4 Unicast from 192.168.10.101 in vrf default
🔍 통신 확인
1. BGP 세션 연결 확인
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# ss -tnlp | grep 179
(⎈|HomeLab:N/A) root@k8s-ctr:~# ss -tnp | grep 179
ESTAB 0 0 192.168.10.100:35791 192.168.10.200:179 users:(("cilium-agent",pid=5170,fd=50))
ESTAB 0 0 [::ffff:192.168.10.100]:6443 [::ffff:172.20.0.179]:46928 users:(("kube-apiserver",pid=3868,fd=105))
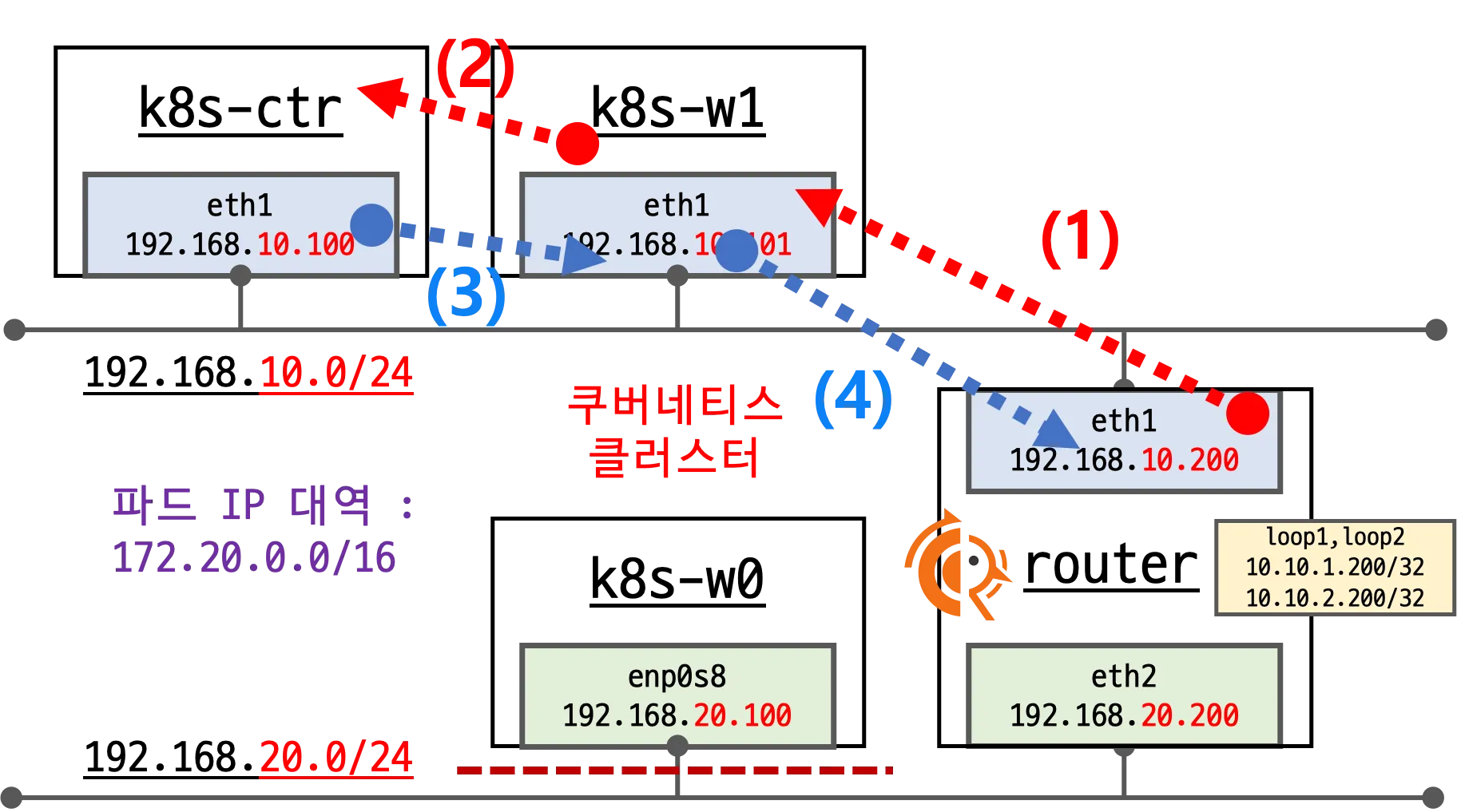
- Cilium은 BGP Listener가 아니라 Initiator로 동작하여 네트워크 장비(FRR 라우터)와 TCP 179 포트로 연결을 수립함
- 컨트롤 플레인 노드(
192.168.10.100:35791)가 라우터(192.168.10.200:179)와 세션을 맺은 상태 확인됨
2. Cilium BGP Peer 연결 상태 확인
1
2
3
4
5
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium bgp peers
Node Local AS Peer AS Peer Address Session State Uptime Family Received Advertised
k8s-ctr 65001 65000 192.168.10.200 established 10m59s ipv4/unicast 4 2
k8s-w0 65001 65000 192.168.10.200 established 10m59s ipv4/unicast 4 2
k8s-w1 65001 65000 192.168.10.200 established 10m59s ipv4/unicast 4 2
- 3개 노드(
k8s-ctr,k8s-w0,k8s-w1) 모두 라우터와 established 상태 확인 - Local ASN은 65001, Peer ASN은 65000으로 정상적으로 매칭
3. PodCIDR 광고 상태 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium bgp routes available ipv4 unicast
✅ 출력
1
2
3
4
Node VRouter Prefix NextHop Age Attrs
k8s-ctr 65001 172.20.0.0/24 0.0.0.0 12m43s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w0 65001 172.20.2.0/24 0.0.0.0 12m42s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w1 65001 172.20.1.0/24 0.0.0.0 12m43s [{Origin: i} {Nexthop: 0.0.0.0}]
- 각 노드의 PodCIDR 광고 확인됨
4. Cilium BGP 리소스 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ciliumbgpadvertisements,ciliumbgppeerconfigs,ciliumbgpclusterconfigs
✅ 출력
1
2
3
4
5
6
7
8
NAME AGE
ciliumbgpadvertisement.cilium.io/bgp-advertisements 13m
NAME AGE
ciliumbgppeerconfig.cilium.io/cilium-peer 13m
NAME AGE
ciliumbgpclusterconfig.cilium.io/cilium-bgp 13m
각 노드별 CiliumBGPNodeConfig 리소스 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ciliumbgpnodeconfigs -o yaml | yq
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
{
"apiVersion": "v1",
"items": [
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T14:27:12Z",
"generation": 1,
"name": "k8s-ctr",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "7578",
"uid": "a72d5068-f106-4b37-a0a7-2ad0e72e8f9d"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"establishedTime": "2025-08-15T14:27:14Z",
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peeringState": "established",
"routeCount": [
{
"advertised": 2,
"afi": "ipv4",
"received": 1,
"safi": "unicast"
}
],
"timers": {
"appliedHoldTimeSeconds": 9,
"appliedKeepaliveSeconds": 3
}
}
]
}
]
}
},
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T14:27:12Z",
"generation": 1,
"name": "k8s-w0",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "7575",
"uid": "395cc9e2-0f3e-47f3-bce0-169110494292"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"establishedTime": "2025-08-15T14:27:14Z",
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peeringState": "established",
"routeCount": [
{
"advertised": 2,
"afi": "ipv4",
"received": 1,
"safi": "unicast"
}
],
"timers": {
"appliedHoldTimeSeconds": 9,
"appliedKeepaliveSeconds": 3
}
}
]
}
]
}
},
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T14:27:12Z",
"generation": 1,
"name": "k8s-w1",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "7581",
"uid": "d98cdab1-5d96-4ecf-ae47-1cc3c80a3071"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"establishedTime": "2025-08-15T14:27:14Z",
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peeringState": "established",
"routeCount": [
{
"advertised": 2,
"afi": "ipv4",
"received": 1,
"safi": "unicast"
}
],
"timers": {
"appliedHoldTimeSeconds": 9,
"appliedKeepaliveSeconds": 3
}
}
]
}
]
}
}
],
"kind": "List",
"metadata": {
"resourceVersion": ""
}
}
- Local ASN 65001
- Peer Address
192.168.10.200, Peer ASN 65000 - Peering State
established - RouteCount:
advertised 2,received 1
5. 라우터 커널 라우팅 테이블 확인
1
2
3
4
root@router:~# ip -c route | grep bgp
172.20.0.0/24 nhid 29 via 192.168.10.100 dev eth1 proto bgp metric 20
172.20.1.0/24 nhid 30 via 192.168.10.101 dev eth1 proto bgp metric 20
172.20.2.0/24 nhid 28 via 192.168.20.100 dev eth2 proto bgp metric 20
- FRR 라우터 커널 라우팅 테이블에 Pod CIDR 경로가 BGP 프로토콜을 통해 학습되어 등록됨
- 특정 Pod 대역과 통신하려면 반드시 해당 노드로 전달되도록 라우팅 경로가 잡힘
6. BGP Neighbor 관계 확인
1
root@router:~# vtysh -c 'show ip bgp summary'
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
IPv4 Unicast Summary (VRF default):
BGP router identifier 192.168.10.200, local AS number 65000 vrf-id 0
BGP table version 4
RIB entries 7, using 1344 bytes of memory
Peers 3, using 2172 KiB of memory
Peer groups 1, using 64 bytes of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
192.168.10.100 4 65001 353 356 0 0 0 00:17:29 1 4 N/A
192.168.10.101 4 65001 353 356 0 0 0 00:17:29 1 4 N/A
192.168.20.100 4 65001 353 356 0 0 0 00:17:28 1 4 N/A
Total number of neighbors 3
- FRR 라우터(AS 65000)는 Cilium이 구동 중인 3개 노드(AS 65001)와 BGP neighbor를 맺음
- 모든 neighbor가
Established상태로 정상 연결됨
7. BGP 광고 경로 확인
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
root@router:~# vtysh -c 'show ip bgp'
BGP table version is 4, local router ID is 192.168.10.200, vrf id 0
Default local pref 100, local AS 65000
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop's vrf id, < announce-nh-self
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 10.10.1.0/24 0.0.0.0 0 32768 i
*> 172.20.0.0/24 192.168.10.100 0 65001 i
*> 172.20.1.0/24 192.168.10.101 0 65001 i
*> 172.20.2.0/24 192.168.20.100 0 65001 i
Displayed 4 routes and 4 total paths
- Pod CIDR (
172.20.0.0/24,172.20.1.0/24,172.20.2.0/24)가 모두 수신됨 - nexthop은 각각 노드의 내부 IP로 표시되며, BGP를 통해 올바르게 광고 전파가 이뤄진 것 확인
8. BGP Neighbor 설정 후 통신 불가 현상
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Hostname: webpod-697b545f57-fbtbj
---
---
---
---
---
---
---
---
---
---
---
Hostname: webpod-697b545f57-fbtbj
---
---
---
---
---
...
- Cilium의 특성상 BGP 세션을 맺더라도 기본적으로 커널 라우팅 테이블에 경로를 주입하지 않음 (
disable-fib상태)
🔀 BGP 정보 전달 확인
1. 컨트롤 플레인 tcpdump 진행
1
2
3
4
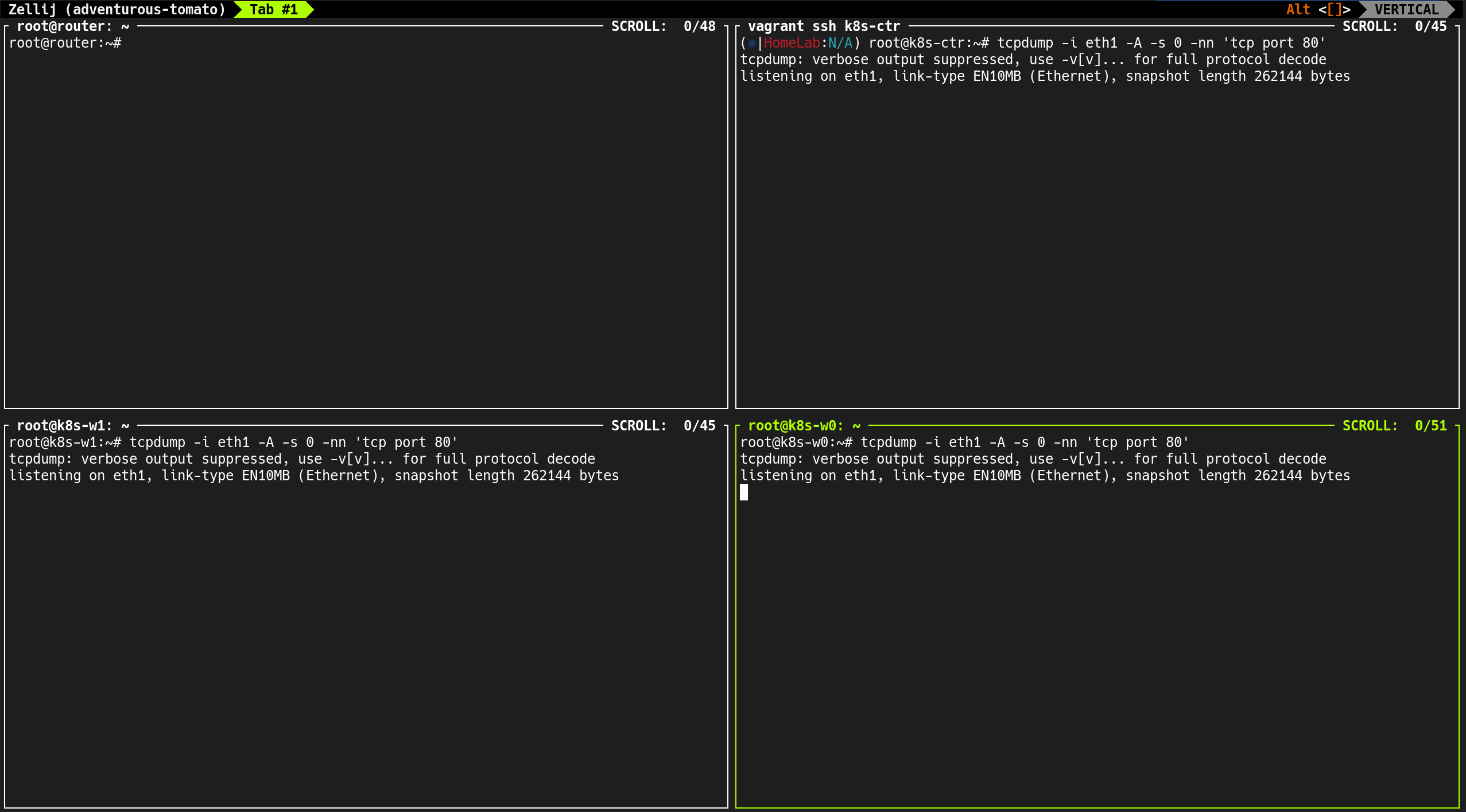
(⎈|HomeLab:N/A) root@k8s-ctr:~# tcpdump -i eth1 tcp port 179 -w /tmp/bgp.pcap
# 결과
tcpdump: listening on eth1, link-type EN10MB (Ethernet), snapshot length 262144 bytes
2. FRR 재시작 및 BGP 세션 확인
1
root@router:~# systemctl restart frr && journalctl -u frr -f
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
Aug 16 00:00:33 router watchfrr.sh[4856]: Cannot stop zebra: pid file not found
Aug 16 00:00:33 router zebra[4858]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 16 00:00:33 router bgpd[4863]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 16 00:00:33 router staticd[4870]: [VTVCM-Y2NW3] Configuration Read in Took: 00:00:00
Aug 16 00:00:33 router frrinit.sh[4835]: * Started watchfrr
Aug 16 00:00:33 router systemd[1]: Started frr.service - FRRouting.
Aug 16 00:00:33 router watchfrr[4845]: [QDG3Y-BY5TN] zebra state -> up : connect succeeded
Aug 16 00:00:33 router watchfrr[4845]: [QDG3Y-BY5TN] bgpd state -> up : connect succeeded
Aug 16 00:00:33 router watchfrr[4845]: [QDG3Y-BY5TN] staticd state -> up : connect succeeded
Aug 16 00:00:33 router watchfrr[4845]: [KWE5Q-QNGFC] all daemons up, doing startup-complete notify
Aug 16 00:00:39 router bgpd[4863]: [M59KS-A3ZXZ] bgp_update_receive: rcvd End-of-RIB for IPv4 Unicast from 192.168.10.100 in vrf default
Aug 16 00:00:39 router bgpd[4863]: [M59KS-A3ZXZ] bgp_update_receive: rcvd End-of-RIB for IPv4 Unicast from 192.168.10.101 in vrf default
Aug 16 00:00:40 router bgpd[4863]: [M59KS-A3ZXZ] bgp_update_receive: rcvd End-of-RIB for IPv4 Unicast from 192.168.20.100 in vrf default
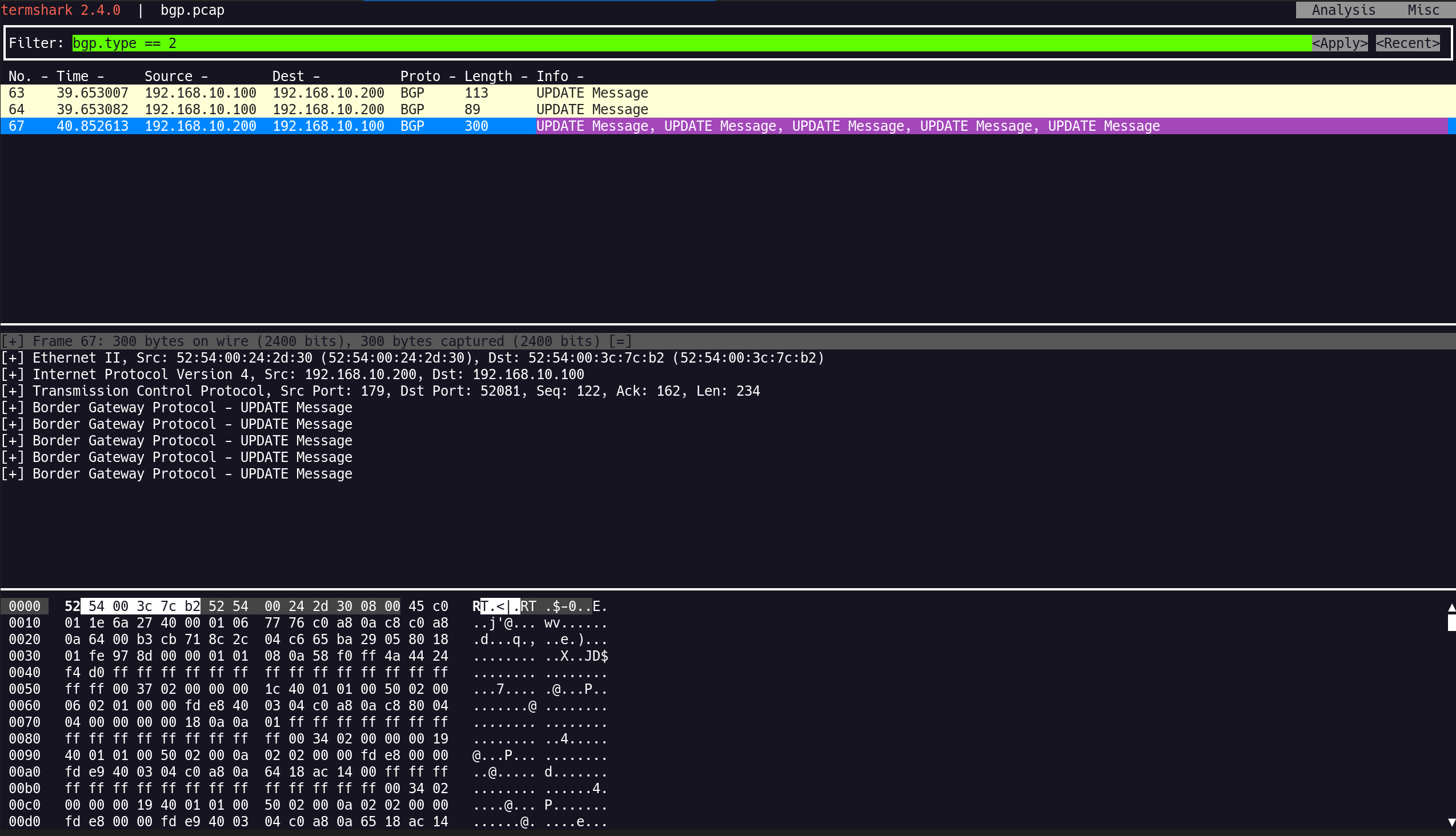
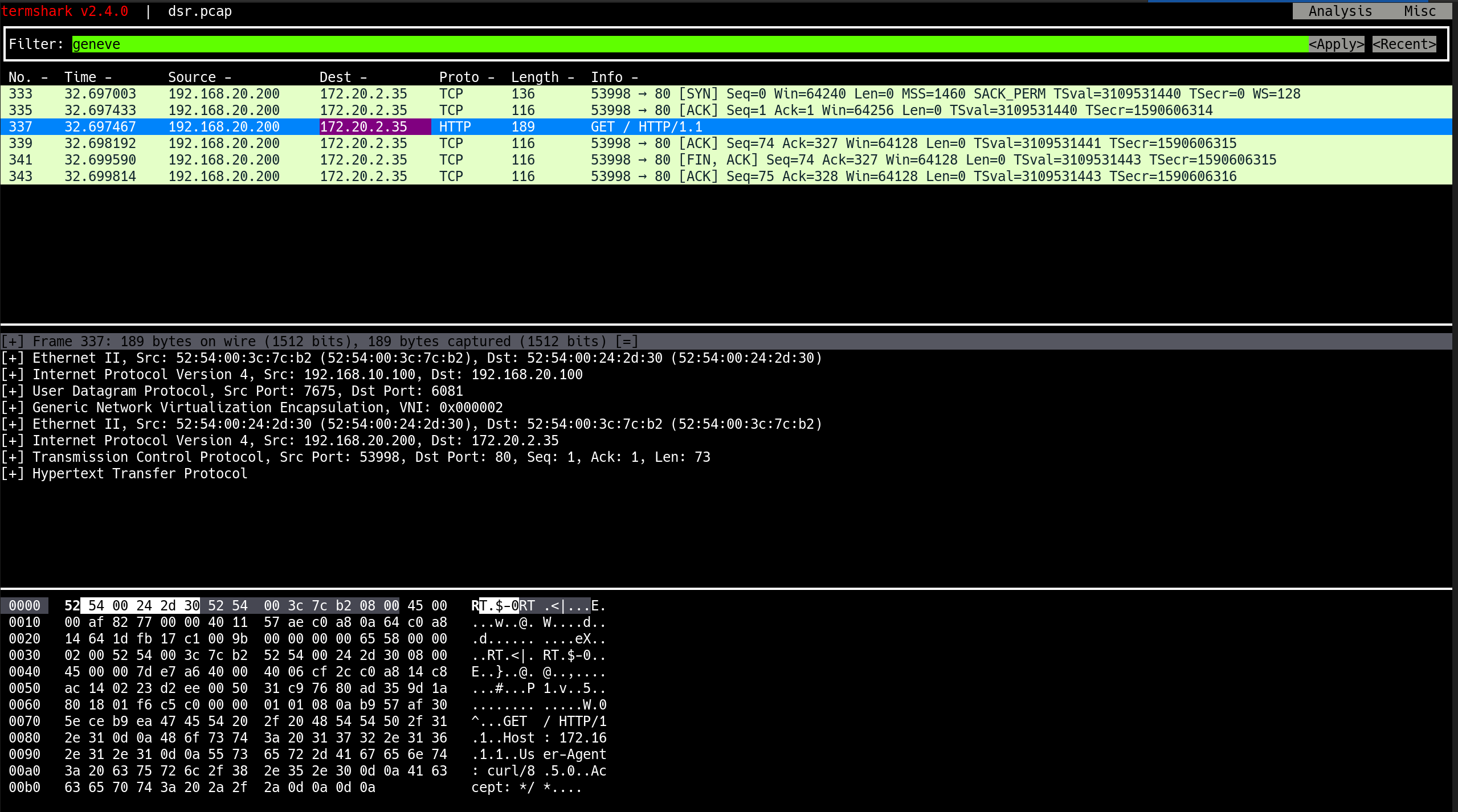
3. Termshark 확인
(1) BGP 패킷 캡처 파일 분석
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# termshark -r /tmp/bgp.pcap
(2) 패킷 분석 중, 컨트롤 플레인 연결이 끊김
1
vagrant halt k8s-ctr --force
- 컨트롤 플레인 VM 강제 종료
1
2
3
4
sudo virsh start 5w_k8s-ctr
# 결과
Domain '5w_k8s-ctr' started
- 컨트롤 플레인 VM 재기동
🛠️ 문제 해결 후 통신 확인
1. Cilium BGP 동작 특성 확인
- Cilium의 BGP는 기본적으로 외부 경로를 커널 라우팅 테이블에 주입하지 않음
disable-fib옵션으로 빌드되어 있음 → 커널 라우팅 테이블(FIB)에 BGP 경로를 반영하지 않겠다는 의미- 따라서 BGP 피어로부터 경로는 수신했지만,
ip route출력에는 해당 CIDR 대역이 나타나지 않음
2. BGP 경로 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# ip -c route
✅ 출력
1
2
3
4
5
6
7
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.70 metric 100
172.20.0.0/24 via 172.20.0.230 dev cilium_host proto kernel src 172.20.0.230
172.20.0.230 dev cilium_host proto kernel scope link
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.100
192.168.20.0/24 via 192.168.10.200 dev eth1 proto static
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.70 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.70 metric 100
172.20.1.0/24,172.20.2.0/24대역이 누락됨
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium bgp routes
✅ 출력
1
2
3
4
5
6
(Defaulting to `available ipv4 unicast` routes, please see help for more options)
Node VRouter Prefix NextHop Age Attrs
k8s-ctr 65001 172.20.0.0/24 0.0.0.0 9m26s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w0 65001 172.20.2.0/24 0.0.0.0 57m18s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w1 65001 172.20.1.0/24 0.0.0.0 57m18s [{Origin: i} {Nexthop: 0.0.0.0}]
- 각 노드 CIDR 경로가 BGP로 정상 수신된 상태 확인 가능
즉, BGP 수신은 정상적이나, 커널 라우팅 반영이 안 되어 통신 불가 상태임
1
2
3
4
5
6
7
8
9
10
11
12
13
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-fbtbj
---
---
---
---
---
---
Hostname: webpod-697b545f57-fbtbj
---
---
...
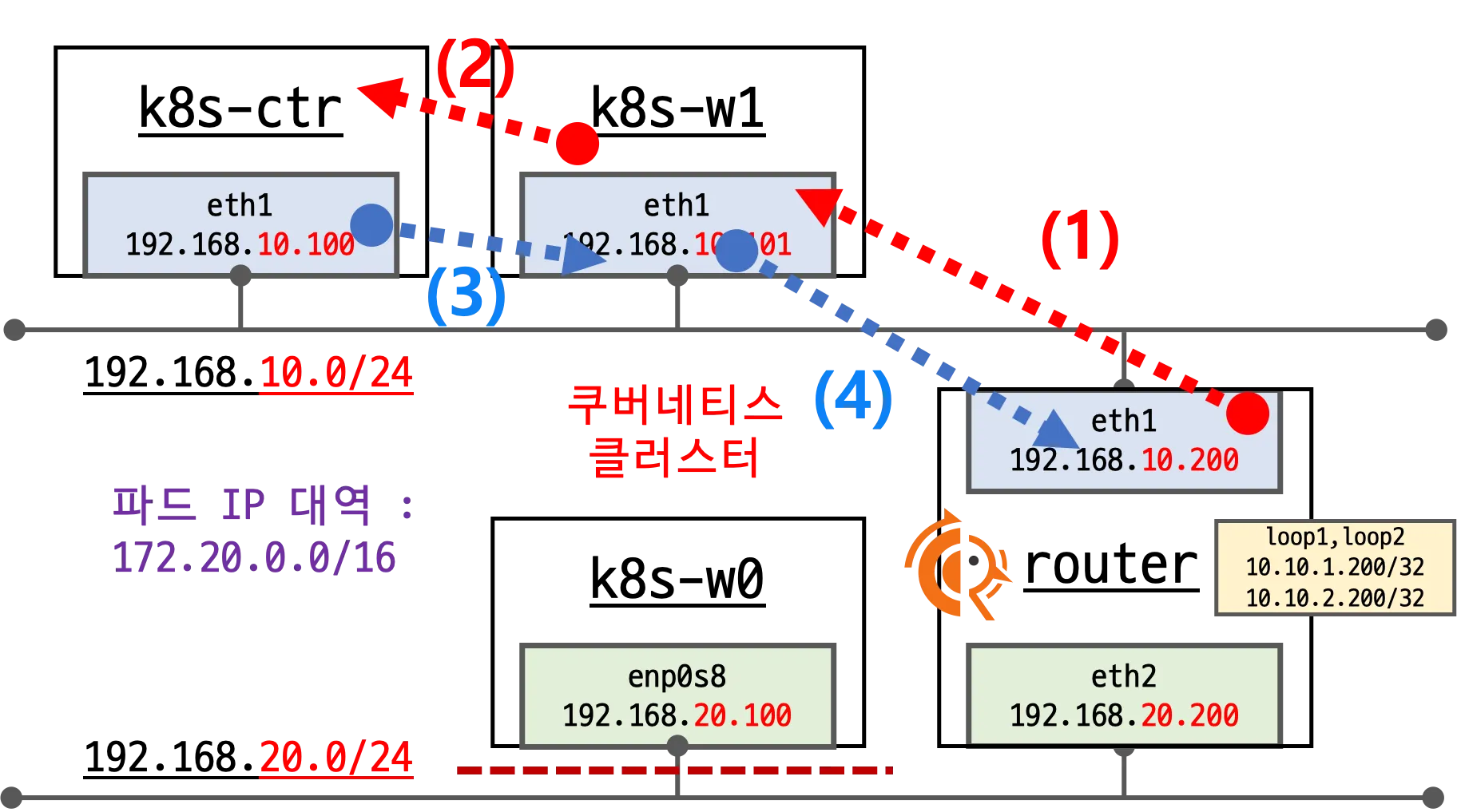
3. k8s 파드 대역 통신을 eth1 경로로 지정
1
2
3
(⎈|HomeLab:N/A) root@k8s-ctr:~# ip route add 172.20.0.0/16 via 192.168.10.200
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@k8s-w1 sudo ip route add 172.20.0.0/16 via 192.168.10.200
sshpass -p 'vagrant' ssh vagrant@k8s-w0 sudo ip route add 172.20.0.0/16 via 192.168.20.200
- eth0 → 인터넷 통신 전용
- eth1 → Kubernetes 파드 통신 전용
- 따라서 파드 대역(
172.20.0.0/16)을 eth1을 통해 라우팅하도록 명시적 경로 추가
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
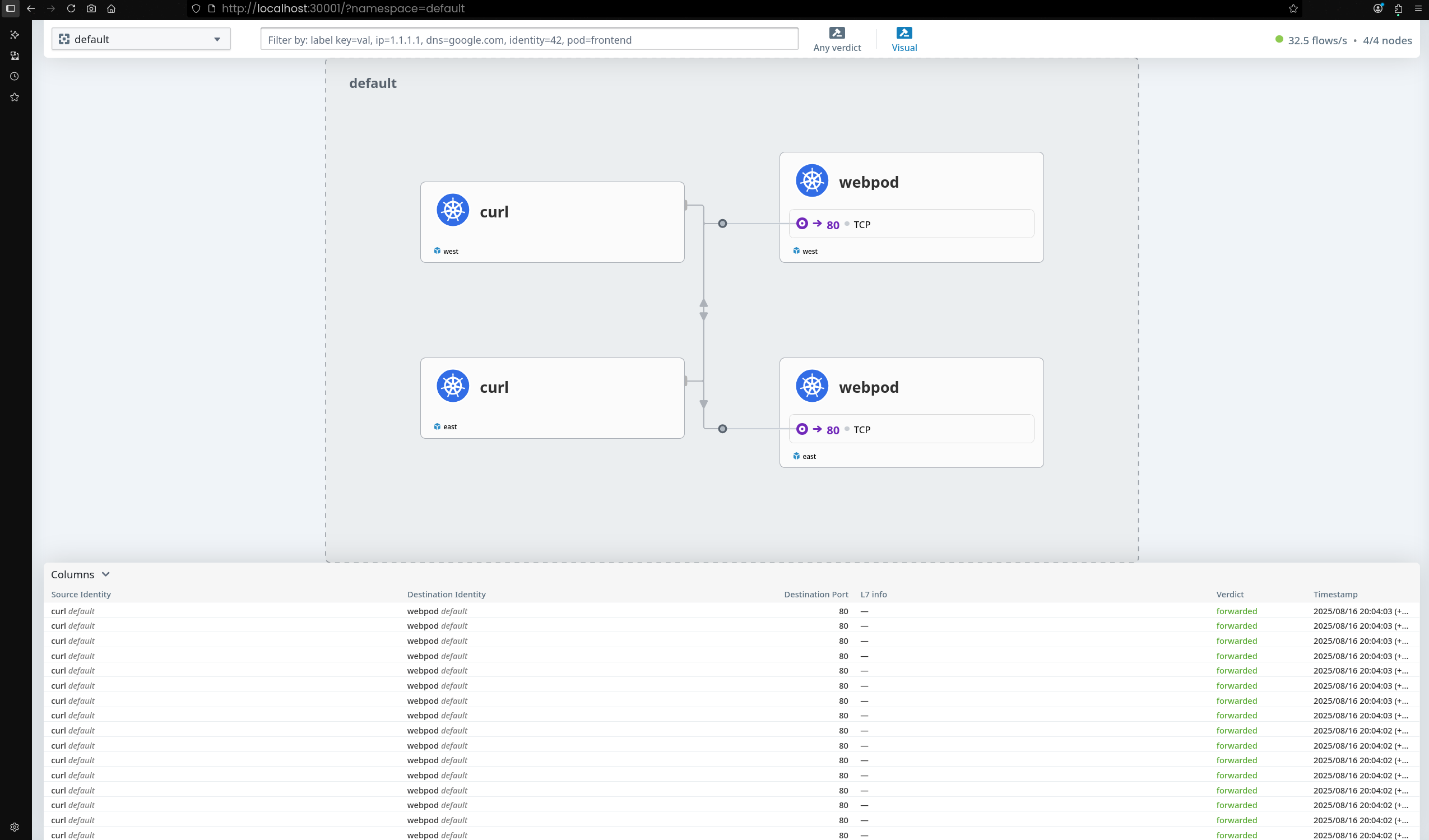
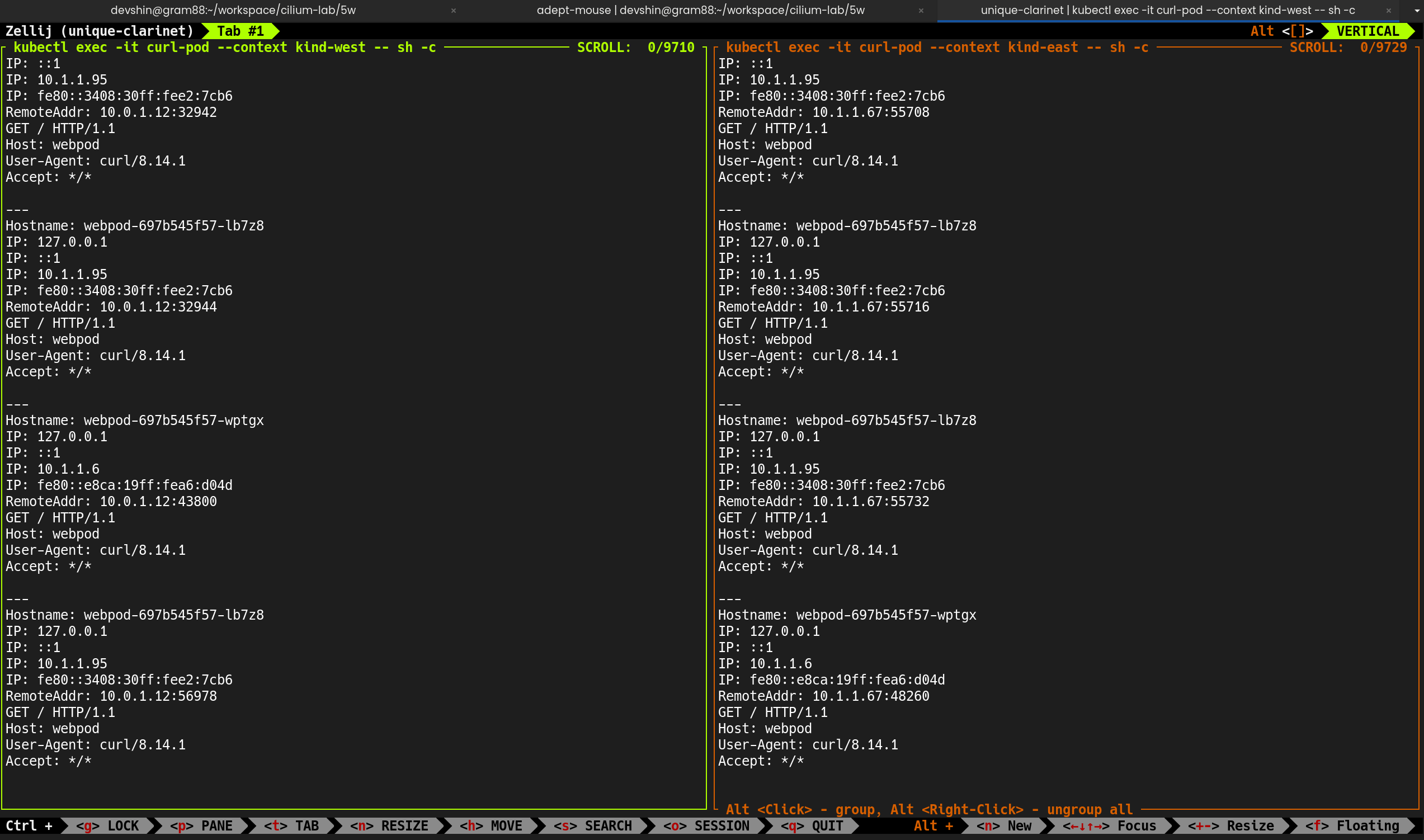
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-rpblf
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-rpblf
---
Hostname: webpod-697b545f57-rpblf
---
Hostname: webpod-697b545f57-rpblf
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-pxhvr
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-rpblf
---
Hostname: webpod-697b545f57-fbtbj
---
Hostname: webpod-697b545f57-pxhvr
---
...
- 경로 추가 후 파드 간 통신 정상 동작 확인
⏸️ 노드(k8s-w0) 유지보수 상황
1. 노드 유지보수 시작 (k8s-w0 Drain)
1
2
3
4
5
6
7
8
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl drain k8s-w0 --ignore-daemonsets
# 결과
node/k8s-w0 cordoned
Warning: ignoring DaemonSet-managed Pods: kube-system/cilium-envoy-8tgrn, kube-system/cilium-wszbk, kube-system/kube-proxy-xhjtq
evicting pod default/webpod-697b545f57-rpblf
pod/webpod-697b545f57-rpblf evicted
node/k8s-w0 drained
kubectl drain명령어를 사용하여k8s-w0노드의 파드를 안전하게 제거하고 스케줄링을 막음
2. BGP 기능 비활성화 (enable-bgp=false)
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl label nodes k8s-w0 enable-bgp=false --overwrite
# 결과
node/k8s-w0 labeled
- 유지보수를 위해
k8s-w0노드의enable-bgp라벨을false로 변경 - 이로 인해 Cilium의 BGP 데몬이 해당 노드에서는 동작하지 않게 됨
3. 노드 상태 확인 (SchedulingDisabled)
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get node
✅ 출력
1
2
3
4
NAME STATUS ROLES AGE VERSION
k8s-ctr Ready control-plane 124m v1.33.2
k8s-w0 Ready,SchedulingDisabled <none> 115m v1.33.2
k8s-w1 Ready <none> 124m v1.33.2
k8s-w0노드 상태가Ready,SchedulingDisabled로 표시됨
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ciliumbgpnodeconfigs
NAME AGE
k8s-ctr 70m
k8s-w1 70m
k8s-w0노드는 BGP NodeConfig 목록에서도 제외됨
4. BGP 라우트/피어 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium bgp routes
✅ 출력
1
2
3
4
5
(Defaulting to `available ipv4 unicast` routes, please see help for more options)
Node VRouter Prefix NextHop Age Attrs
k8s-ctr 65001 172.20.0.0/24 0.0.0.0 23m21s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w1 65001 172.20.1.0/24 0.0.0.0 1h11m13s [{Origin: i} {Nexthop: 0.0.0.0}]
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium bgp peers
✅ 출력
1
2
3
Node Local AS Peer AS Peer Address Session State Uptime Family Received Advertised
k8s-ctr 65001 65000 192.168.10.200 established 15m58s ipv4/unicast 3 2
k8s-w1 65001 65000 192.168.10.200 established 15m58s ipv4/unicast 3 2
- 출력에서
k8s-w0라우트 정보가 사라짐
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router "sudo vtysh -c 'show ip bgp summary'"
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
IPv4 Unicast Summary (VRF default):
BGP router identifier 192.168.10.200, local AS number 65000 vrf-id 0
BGP table version 5
RIB entries 5, using 960 bytes of memory
Peers 3, using 2172 KiB of memory
Peer groups 1, using 64 bytes of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
192.168.10.100 4 65001 400 404 0 0 0 00:19:48 1 3 N/A
192.168.10.101 4 65001 400 404 0 0 0 00:19:49 1 3 N/A
192.168.20.100 4 65001 266 267 0 0 0 00:06:48 Active 0 N/A
Total number of neighbors 3
- FRR 라우터에서도 상태가 Active 로 표시됨
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router "sudo vtysh -c 'show ip route bgp'"
✅ 출력
1
2
3
4
5
6
7
8
9
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
B>* 172.20.0.0/24 [20/0] via 192.168.10.100, eth1, weight 1, 00:18:28
B>* 172.20.1.0/24 [20/0] via 192.168.10.101, eth1, weight 1, 00:18:28
- 라우팅 테이블에서도
k8s-w0의 CIDR이 제거됨
5. 노드 복구 (enable-bgp=true & uncordon)
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl label nodes k8s-w0 enable-bgp=true --overwrite
# 결과
node/k8s-w0 labeled
- 유지보수가 끝난 후
k8s-w0라벨을 다시enable-bgp=true로 원복
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl uncordon k8s-w0
# 결과
node/k8s-w0 uncordoned
kubectl uncordon명령어로 스케줄링을 허용하여 정상 상태로 복구
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get node
kubectl get ciliumbgpnodeconfigs
cilium bgp routes
cilium bgp peers
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
NAME STATUS ROLES AGE VERSION
k8s-ctr Ready control-plane 132m v1.33.2
k8s-w0 Ready <none> 123m v1.33.2
k8s-w1 Ready <none> 132m v1.33.2
NAME AGE
k8s-ctr 77m
k8s-w0 47s
k8s-w1 77m
(Defaulting to `available ipv4 unicast` routes, please see help for more options)
Node VRouter Prefix NextHop Age Attrs
k8s-ctr 65001 172.20.0.0/24 0.0.0.0 29m55s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w0 65001 172.20.2.0/24 0.0.0.0 48s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w1 65001 172.20.1.0/24 0.0.0.0 1h17m47s [{Origin: i} {Nexthop: 0.0.0.0}]
Node Local AS Peer AS Peer Address Session State Uptime Family Received Advertised
k8s-ctr 65001 65000 192.168.10.200 established 22m2s ipv4/unicast 4 2
k8s-w0 65001 65000 192.168.10.200 established 46s ipv4/unicast 4 2
k8s-w1 65001 65000 192.168.10.200 established 22m2s ipv4/unicast 4 2
6. 노드별 파드 분배 실행
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get pod -owide
✅ 출력
1
2
3
4
5
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
curl-pod 1/1 Running 1 (31m ago) 117m 172.20.0.35 k8s-ctr <none> <none>
webpod-697b545f57-fbtbj 1/1 Running 1 (31m ago) 119m 172.20.0.6 k8s-ctr <none> <none>
webpod-697b545f57-lzxbc 1/1 Running 0 10m 172.20.1.98 k8s-w1 <none> <none>
webpod-697b545f57-pxhvr 1/1 Running 0 119m 172.20.1.65 k8s-w1 <none> <none>
1
2
3
4
5
6
7
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl scale deployment webpod --replicas 0
# 결과
deployment.apps/webpod scaled
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl scale deployment webpod --replicas 3
# 결과
deployment.apps/webpod scaled
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get pod -owide
✅ 출력
1
2
3
4
5
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
curl-pod 1/1 Running 1 (31m ago) 117m 172.20.0.35 k8s-ctr <none> <none>
webpod-697b545f57-5twrq 1/1 Running 0 7s 172.20.1.119 k8s-w1 <none> <none>
webpod-697b545f57-cp7xq 1/1 Running 0 7s 172.20.0.15 k8s-ctr <none> <none>
webpod-697b545f57-xtmdx 1/1 Running 0 7s 172.20.2.35 k8s-w0 <none> <none>
kubectl scale명령어로webpod배포를 줄였다가 다시 확장하여 파드가k8s-w0에도 정상 배치됨을 확인
🚫 CRD 상태 보고 비활성화
- https://docs.cilium.io/en/stable/network/bgp-control-plane/bgp-control-plane-operation/#disabling-crd-status-report
- Cilium BGP는 기본적으로
CiliumBGPNodeConfig리소스의status필드에 피어 상태, 세션, 라우트 정보를 기록함 - 그러나 대규모 클러스터에서는 상태 보고가 빈번히 발생해 Kubernetes API 서버에 부하를 줄 수 있음
- 따라서 공식 문서에서도
bgp status reporting off옵션 사용을 권장함
1. 현재 BGP 상태 확인 (Status Report 활성화 상태)
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ciliumbgpnodeconfigs -o yaml | yq
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
{
"apiVersion": "v1",
"items": [
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T14:27:12Z",
"generation": 1,
"name": "k8s-ctr",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "15080",
"uid": "a72d5068-f106-4b37-a0a7-2ad0e72e8f9d"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"establishedTime": "2025-08-15T15:22:57Z",
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peeringState": "established",
"routeCount": [
{
"advertised": 2,
"afi": "ipv4",
"received": 3,
"safi": "unicast"
}
],
"timers": {
"appliedHoldTimeSeconds": 9,
"appliedKeepaliveSeconds": 3
}
}
]
}
]
}
},
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T15:44:11Z",
"generation": 1,
"name": "k8s-w0",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "16068",
"uid": "fd222576-cc33-4f4f-b7cd-c8157fbc8009"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"establishedTime": "2025-08-15T15:44:13Z",
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peeringState": "established",
"routeCount": [
{
"advertised": 2,
"afi": "ipv4",
"received": 3,
"safi": "unicast"
}
],
"timers": {
"appliedHoldTimeSeconds": 9,
"appliedKeepaliveSeconds": 3
}
}
]
}
]
}
},
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T14:27:12Z",
"generation": 1,
"name": "k8s-w1",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "15076",
"uid": "d98cdab1-5d96-4ecf-ae47-1cc3c80a3071"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"establishedTime": "2025-08-15T15:22:57Z",
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peeringState": "established",
"routeCount": [
{
"advertised": 2,
"afi": "ipv4",
"received": 3,
"safi": "unicast"
}
],
"timers": {
"appliedHoldTimeSeconds": 9,
"appliedKeepaliveSeconds": 3
}
}
]
}
]
}
}
],
"kind": "List",
"metadata": {
"resourceVersion": ""
}
}
- 각 노드(
k8s-ctr,k8s-w0,k8s-w1)의status에 피어 연결 상태 (established), Advertised / Received Routes, Keepalive / HoldTime 값 등의 정보가 상세히 기록됨
2. Helm 업그레이드로 상태 보고 비활성화
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
(⎈|HomeLab:N/A) root@k8s-ctr:~# helm upgrade cilium cilium/cilium --version 1.18.0 --namespace kube-system --reuse-values \
--set bgpControlPlane.statusReport.enabled=false
# 결과
Release "cilium" has been upgraded. Happy Helming!
NAME: cilium
LAST DEPLOYED: Sat Aug 16 00:51:38 2025
NAMESPACE: kube-system
STATUS: deployed
REVISION: 2
TEST SUITE: None
NOTES:
You have successfully installed Cilium with Hubble Relay and Hubble UI.
Your release version is 1.18.0.
For any further help, visit https://docs.cilium.io/en/v1.18/gettinghelp
- 성공적으로
cilium차트가 재배포되며, 이후 BGP 상태 보고가 중단됨
3. Cilium DaemonSet 롤링 재시작
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl -n kube-system rollout restart ds/cilium
# 결과
daemonset.apps/cilium restarted
4. 결과 확인 (Status Report 제거됨)
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ciliumbgpnodeconfigs -o yaml | yq
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
{
"apiVersion": "v1",
"items": [
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T14:27:12Z",
"generation": 1,
"name": "k8s-ctr",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "17327",
"uid": "a72d5068-f106-4b37-a0a7-2ad0e72e8f9d"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {}
},
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T15:44:11Z",
"generation": 1,
"name": "k8s-w0",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "17231",
"uid": "fd222576-cc33-4f4f-b7cd-c8157fbc8009"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {}
},
{
"apiVersion": "cilium.io/v2",
"kind": "CiliumBGPNodeConfig",
"metadata": {
"creationTimestamp": "2025-08-15T14:27:12Z",
"generation": 1,
"name": "k8s-w1",
"ownerReferences": [
{
"apiVersion": "cilium.io/v2",
"controller": true,
"kind": "CiliumBGPClusterConfig",
"name": "cilium-bgp",
"uid": "e1f4b328-d375-4a7c-a99b-ed2658602a14"
}
],
"resourceVersion": "17229",
"uid": "d98cdab1-5d96-4ecf-ae47-1cc3c80a3071"
},
"spec": {
"bgpInstances": [
{
"localASN": 65001,
"name": "instance-65001",
"peers": [
{
"name": "tor-switch",
"peerASN": 65000,
"peerAddress": "192.168.10.200",
"peerConfigRef": {
"name": "cilium-peer"
}
}
]
}
]
},
"status": {}
}
],
"kind": "List",
"metadata": {
"resourceVersion": ""
}
}
status필드가 비어 있음 (status: {})- 더 이상 CRD를 통해 BGP 상태가 기록되지 않음 → API 서버 부하 감소 효과
🏷️ LoadBalancer External IP를 BGP로 광고
- https://docs.cilium.io/en/stable/network/bgp-control-plane/bgp-control-plane-v2/#service-virtual-ips
- Kubernetes Service 타입을
LoadBalancer로 변경하여 External IP를 할당받음 - L2 Announcement와 달리 BGP는 라우팅 기반이라, External IP가 노드 네트워크 대역과 달라도 광고 가능
1. Cilium LoadBalancer IP Pool 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
(⎈|HomeLab:N/A) root@k8s-ctr:~# cat << EOF | kubectl apply -f -
apiVersion: "cilium.io/v2"
kind: CiliumLoadBalancerIPPool
metadata:
name: "cilium-pool"
spec:
allowFirstLastIPs: "No"
blocks:
- cidr: "172.16.1.0/24"
EOF
# 결과
ciliumloadbalancerippool.cilium.io/cilium-pool created
CiliumLoadBalancerIPPoolCRD를 이용해172.16.1.0/24대역을 풀로 등록
1
2
3
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ippool
NAME DISABLED CONFLICTING IPS AVAILABLE AGE
cilium-pool false False 254 3m12s
/24대역(172.16.1.0/24) → 254개 IP 할당 가능
2. 서비스 타입 LoadBalancer 적용 및 External IP 확인
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl patch svc webpod -p '{"spec": {"type": "LoadBalancer"}}'
# 결과
service/webpod patched
- 기존
webpod서비스를LoadBalancer타입으로 변경하여 External IP를 할당받음
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get svc webpod
✅ 출력
1
2
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
webpod LoadBalancer 10.96.54.159 172.16.1.1 80:32567/TCP 15h
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get ippool
✅ 출력
1
2
NAME DISABLED CONFLICTING IPS AVAILABLE AGE
cilium-pool false False 253 4m50s
cilium-pool에서 1개 IP가 소모되어172.16.1.1이 외부 접근용 주소로 부여됨
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl describe svc webpod | grep 'Traffic Policy'
✅ 출력
1
2
External Traffic Policy: Cluster
Internal Traffic Policy: Cluster
- Traffic Policy는 기본적으로 Cluster 모드로 설정되어, 모든 노드로 트래픽이 분산됨
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl -n kube-system exec ds/cilium -c cilium-agent -- cilium-dbg service list
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
ID Frontend Service Type Backend
1 10.96.12.94:80/TCP ClusterIP 1 => 172.20.0.232:4245/TCP (active)
2 0.0.0.0:30003/TCP NodePort 1 => 172.20.0.13:8081/TCP (active)
5 10.96.33.159:80/TCP ClusterIP 1 => 172.20.0.13:8081/TCP (active)
6 10.96.198.41:443/TCP ClusterIP 1 => 172.20.0.122:10250/TCP (active)
7 10.96.0.1:443/TCP ClusterIP 1 => 192.168.10.100:6443/TCP (active)
8 10.96.137.113:443/TCP ClusterIP 1 => 192.168.10.101:4244/TCP (active)
9 10.96.0.10:53/TCP ClusterIP 1 => 172.20.0.82:53/TCP (active)
2 => 172.20.0.104:53/TCP (active)
10 10.96.0.10:53/UDP ClusterIP 1 => 172.20.0.82:53/UDP (active)
2 => 172.20.0.104:53/UDP (active)
11 10.96.0.10:9153/TCP ClusterIP 1 => 172.20.0.82:9153/TCP (active)
2 => 172.20.0.104:9153/TCP (active)
12 10.96.54.159:80/TCP ClusterIP 1 => 172.20.0.15:80/TCP (active)
2 => 172.20.1.119:80/TCP (active)
3 => 172.20.2.35:80/TCP (active)
14 0.0.0.0:32567/TCP NodePort 1 => 172.20.0.15:80/TCP (active)
2 => 172.20.1.119:80/TCP (active)
3 => 172.20.2.35:80/TCP (active)
17 172.16.1.1:80/TCP LoadBalancer 1 => 172.20.0.15:80/TCP (active)
2 => 172.20.1.119:80/TCP (active)
3 => 172.20.2.35:80/TCP (active)
172.16.1.1:80/TCPLoadBalancer 프론트엔드가 파드 3개(172.20.x.x) 백엔드와 매핑됨
1
2
3
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get svc webpod -o jsonpath='{.status.loadBalancer.ingress[0].ip}'
LBIP=$(kubectl get svc webpod -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
curl -s $LBIP
✅ 출력
1
2
3
4
5
6
7
8
9
10
172.16.1.1Hostname: webpod-697b545f57-5twrq
IP: 127.0.0.1
IP: ::1
IP: 172.20.1.119
IP: fe80::dcab:bcff:fee2:3765
RemoteAddr: 192.168.10.100:59608
GET / HTTP/1.1
Host: 172.16.1.1
User-Agent: curl/8.5.0
Accept: */*
- 클러스터 내부에서
curl 172.16.1.1테스트 시 정상적으로 서비스 응답 확인됨
3. router 라우팅 테이블 모니터링
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# watch "sshpass -p 'vagrant' ssh vagrant@router ip -c route"
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
Every 2.0s: sshpass -p 'vagrant' ssh vagrant@router ip -c route k8s-ctr: Sat Aug 16 14:04:23 2025
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.25 metric 100
10.10.1.0/24 dev loop1 proto kernel scope link src 10.10.1.200
10.10.2.0/24 dev loop2 proto kernel scope link src 10.10.2.200
172.20.0.0/24 nhid 92 via 192.168.10.100 dev eth1 proto bgp metric 20
172.20.1.0/24 nhid 88 via 192.168.10.101 dev eth1 proto bgp metric 20
172.20.2.0/24 nhid 94 via 192.168.20.100 dev eth2 proto bgp metric 20
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.200
192.168.20.0/24 dev eth2 proto kernel scope link src 192.168.20.200
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.25 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.25 metric 100
- 현재는 Cilium BGP를 통해 Pod CIDR 대역(
172.20.0.0/24,172.20.1.0/24,172.20.2.0/24) 이 광고된 상태
4. Cilium BGP Advertisement 확인 (Pod CIDR)
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get CiliumBGPAdvertisement
✅ 출력
1
2
NAME AGE
bgp-advertisements 14h
- 현재는 Pod CIDR를 광고하도록 설정된 정책만 존재
5. 새로운 BGP Advertisement 생성
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# k get svc
✅ 출력
1
2
3
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 15h
webpod LoadBalancer 10.96.54.159 172.16.1.1 80:32567/TCP 15h
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
(⎈|HomeLab:N/A) root@k8s-ctr:~# cat << EOF | kubectl apply -f -
apiVersion: cilium.io/v2
kind: CiliumBGPAdvertisement
metadata:
name: bgp-advertisements-lb-exip-webpod
labels:
advertise: bgp
spec:
advertisements:
- advertisementType: "Service"
service:
addresses:
- LoadBalancerIP
selector:
matchExpressions:
- { key: app, operator: In, values: [ webpod ] }
EOF
# 결과
ciliumbgpadvertisement.cilium.io/bgp-advertisements-lb-exip-webpod created
advertisementType: Service로 지정하여 Service의 LoadBalancer External IP만 광고하도록 설정- 특정 서비스(
app=webpod)의 LoadBalancer IP(172.16.1.1)가 광고 대상이 됨
6. router에서 LoadBalancer External IP 라우트 반영 확인
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Every 2.0s: sshpass -p 'vagrant' ssh vagrant@router ip -c route k8s-ctr: Sat Aug 16 14:13:23 2025
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.25 metric 100
10.10.1.0/24 dev loop1 proto kernel scope link src 10.10.1.200
10.10.2.0/24 dev loop2 proto kernel scope link src 10.10.2.200
172.16.1.1 nhid 105 proto bgp metric 20
nexthop via 192.168.10.101 dev eth1 weight 1
nexthop via 192.168.10.100 dev eth1 weight 1
nexthop via 192.168.20.100 dev eth2 weight 1
172.20.0.0/24 nhid 92 via 192.168.10.100 dev eth1 proto bgp metric 20
172.20.1.0/24 nhid 88 via 192.168.10.101 dev eth1 proto bgp metric 20
172.20.2.0/24 nhid 94 via 192.168.20.100 dev eth2 proto bgp metric 20
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.200
192.168.20.0/24 dev eth2 proto kernel scope link src 192.168.20.200
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.25 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.25 metric 100
- 새로운
CiliumBGPAdvertisement생성 후, 라우터 라우팅 테이블에172.16.1.1/32경로가 추가됨 - Nexthop은 클러스터 내 3개 노드 (
192.168.10.100,192.168.10.101,192.168.20.100) - 동일 우선순위로 multipath 라우팅이 구성됨
7. Cilium BGP Advertisement 및 정책 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get CiliumBGPAdvertisement
✅ 출력
1
2
3
NAME AGE
bgp-advertisements 14h
bgp-advertisements-lb-exip-webpod 2m58s
CiliumBGPAdvertisement에 새로운 정책(bgp-advertisements-lb-exip-webpod)이 추가됨
1
2
3
4
5
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl exec -it -n kube-system ds/cilium -- cilium-dbg bgp route-policies
VRouter Policy Name Type Match Peers Match Families Match Prefixes (Min..Max Len) RIB Action Path Actions
65001 allow-local import accept
65001 tor-switch-ipv4-PodCIDR export 192.168.10.200/32 172.20.1.0/24 (24..24) accept
65001 tor-switch-ipv4-Service-webpod-default-LoadBalancerIP export 192.168.10.200/32 172.16.1.1/32 (32..32) accept
- 정책 이름은 서비스별로 생성되며, 이번에는
tor-switch-ipv4-Service-webpod-default-LoadBalancerIP - 결과적으로 Pod CIDR + Service LoadBalancer IP(172.16.1.1/32) 가 동시에 export 됨
8. Cilium BGP Routes 확인 (노드별 광고 상태)
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium bgp routes available ipv4 unicast
✅ 출력
1
2
3
4
5
6
7
Node VRouter Prefix NextHop Age Attrs
k8s-ctr 65001 172.16.1.1/32 0.0.0.0 5m6s [{Origin: i} {Nexthop: 0.0.0.0}]
65001 172.20.0.0/24 0.0.0.0 13h23m31s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w0 65001 172.16.1.1/32 0.0.0.0 5m6s [{Origin: i} {Nexthop: 0.0.0.0}]
65001 172.20.2.0/24 0.0.0.0 13h23m43s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w1 65001 172.16.1.1/32 0.0.0.0 5m6s [{Origin: i} {Nexthop: 0.0.0.0}]
65001 172.20.1.0/24 0.0.0.0 13h23m44s [{Origin: i} {Nexthop: 0.0.0.0}]
- 클러스터의 모든 노드(k8s-ctr, k8s-w0, k8s-w1)가
172.16.1.1/32경로를 BGP로 광고 - 라우터는 이를 받아 모든 노드로 트래픽을 보낼 수 있게 됨
9. router BGP 테이블에서 Multipath 반영 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router "sudo vtysh -c 'show ip route bgp'"
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
B>* 172.16.1.1/32 [20/0] via 192.168.10.100, eth1, weight 1, 00:07:20
* via 192.168.10.101, eth1, weight 1, 00:07:20
* via 192.168.20.100, eth2, weight 1, 00:07:20
B>* 172.20.0.0/24 [20/0] via 192.168.10.100, eth1, weight 1, 00:29:43
B>* 172.20.1.0/24 [20/0] via 192.168.10.101, eth1, weight 1, 00:29:42
B>* 172.20.2.0/24 [20/0] via 192.168.20.100, eth2, weight 1, 00:29:42
- 라우터 BGP 테이블에서
172.16.1.1/32경로는 multipath 상태로 기록됨 192.168.10.100,192.168.10.101,192.168.20.100세 노드가 동일 프리픽스를 광고했기 때문에 라우터는 세 경로를 모두 유효(* valid)로 인식- BGP 경로 우선순위가 동일 → 커널 라우팅 테이블에 multipath로 동시에 반영됨
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router "sudo vtysh -c 'show ip bgp summary'"
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
IPv4 Unicast Summary (VRF default):
BGP router identifier 192.168.10.200, local AS number 65000 vrf-id 0
BGP table version 10
RIB entries 9, using 1728 bytes of memory
Peers 3, using 2172 KiB of memory
Peer groups 1, using 64 bytes of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
192.168.10.100 4 65001 1284 1294 0 0 0 00:31:06 2 5 N/A
192.168.10.101 4 65001 1284 1294 0 0 0 00:31:05 2 5 N/A
192.168.20.100 4 65001 1125 1132 0 0 0 00:31:05 2 5 N/A
Total number of neighbors 3
show ip bgp summary출력에서도 3개의 피어가 모두 동일 프리픽스를 광고했음을 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router "sudo vtysh -c 'show ip bgp'"
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
BGP table version is 10, local router ID is 192.168.10.200, vrf id 0
Default local pref 100, local AS 65000
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop's vrf id, < announce-nh-self
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 10.10.1.0/24 0.0.0.0 0 32768 i
*= 172.16.1.1/32 192.168.20.100 0 65001 i
*= 192.168.10.101 0 65001 i
*> 192.168.10.100 0 65001 i
*> 172.20.0.0/24 192.168.10.100 0 65001 i
*> 172.20.1.0/24 192.168.10.101 0 65001 i
*> 172.20.2.0/24 192.168.20.100 0 65001 i
Displayed 5 routes and 7 total paths
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
(⎈|HomeLab:N/A) root@k8s-ctr:~# sshpass -p 'vagrant' ssh vagrant@router "sudo vtysh -c 'show ip bgp 172.16.1.1/32'"
BGP routing table entry for 172.16.1.1/32, version 10
Paths: (3 available, best #3, table default)
Advertised to non peer-group peers:
192.168.10.100 192.168.10.101 192.168.20.100
65001
192.168.20.100 from 192.168.20.100 (192.168.20.100)
Origin IGP, valid, external, multipath
Last update: Sat Aug 16 14:10:56 2025
65001
192.168.10.101 from 192.168.10.101 (192.168.10.101)
Origin IGP, valid, external, multipath
Last update: Sat Aug 16 14:10:56 2025
65001
192.168.10.100 from 192.168.10.100 (192.168.10.100)
Origin IGP, valid, external, multipath, best (Router ID)
Last update: Sat Aug 16 14:10:56 2025
- 특정 경로(
172.16.1.1/32)만 조회해도 multipath 항목이 모두 표시되며,best경로는 Router ID 기준으로 선택됨
🛜 router에서 LB EX-IP 호출 확인
1. router에서 LoadBalancer External IP 호출 테스트
1
2
root@router:~# LBIP=172.16.1.1
curl -s $LBIP
✅ 출력
1
2
3
4
5
6
7
8
9
10
Hostname: webpod-697b545f57-cp7xq
IP: 127.0.0.1
IP: ::1
IP: 172.20.0.15
IP: fe80::4870:31ff:fe42:a8a6
RemoteAddr: 192.168.10.200:43094
GET / HTTP/1.1
Host: 172.16.1.1
User-Agent: curl/8.5.0
Accept: */*
- 라우터에서
curl명령으로 LB External IP(172.16.1.1) 호출
2. 라우터에서 부하분산 결과 확인
1
root@router:~# for i in {1..100}; do curl -s $LBIP | grep Hostname; done | sort | uniq -c | sort -nr
✅ 출력
1
2
3
36 Hostname: webpod-697b545f57-xtmdx
36 Hostname: webpod-697b545f57-5twrq
28 Hostname: webpod-697b545f57-cp7xq
- 100회 반복 호출 시 파드 3개로 트래픽이 분산되는 것을 확인
- 이는 Cilium LB가 multipath를 통해 정상적으로 부하분산을 수행하고 있음을 의미
3. 실시간 호출 모니터링으로 노드 분산 확인
1
root@router:~# while true; do curl -s $LBIP | egrep 'Hostname|RemoteAddr' ; sleep 0.1; done
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
Hostname: webpod-697b545f57-xtmdx
RemoteAddr: 192.168.10.100:34884
Hostname: webpod-697b545f57-xtmdx
RemoteAddr: 192.168.10.100:34900
Hostname: webpod-697b545f57-5twrq
RemoteAddr: 192.168.10.100:34916
Hostname: webpod-697b545f57-5twrq
RemoteAddr: 192.168.10.100:34924
Hostname: webpod-697b545f57-cp7xq
RemoteAddr: 192.168.10.200:34940
Hostname: webpod-697b545f57-cp7xq
RemoteAddr: 192.168.10.200:34946
Hostname: webpod-697b545f57-xtmdx
RemoteAddr: 192.168.10.100:34948
Hostname: webpod-697b545f57-cp7xq
RemoteAddr: 192.168.10.200:34954
Hostname: webpod-697b545f57-5twrq
RemoteAddr: 192.168.10.100:34964
Hostname: webpod-697b545f57-xtmdx
RemoteAddr: 192.168.10.100:34966
Hostname: webpod-697b545f57-cp7xq
RemoteAddr: 192.168.10.200:34974
Hostname: webpod-697b545f57-xtmdx
RemoteAddr: 192.168.10.100:34986
Hostname: webpod-697b545f57-cp7xq
RemoteAddr: 192.168.10.200:35002
...
curl반복 호출 시RemoteAddr확인 결과, 동일 LB IP 요청이 여러 노드(192.168.10.100,192.168.10.200)로 분산됨- 즉, 외부에서 LB IP로 접근 시 라우터는 multipath 라우팅을 통해 다수 노드로 트래픽을 전달함
4. Pod 수 축소 후에도 모든 노드가 광고되는 문제
1
2
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl scale deployment webpod --replicas 2
deployment.apps/webpod scaled
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get pod -owide
✅ 출력
1
2
3
4
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
curl-pod 1/1 Running 1 (14h ago) 15h 172.20.0.35 k8s-ctr <none> <none>
webpod-697b545f57-5twrq 1/1 Running 0 13h 172.20.1.119 k8s-w1 <none> <none>
webpod-697b545f57-xtmdx 1/1 Running 0 13h 172.20.2.35 k8s-w0 <none> <none>
webpod를 replicas=2로 줄여 파드가k8s-w0,k8s-w1에만 존재
1
2
3
4
5
6
7
8
9
10
(⎈|HomeLab:N/A) root@k8s-ctr:~# cilium bgp routes
(Defaulting to `available ipv4 unicast` routes, please see help for more options)
Node VRouter Prefix NextHop Age Attrs
k8s-ctr 65001 172.16.1.1/32 0.0.0.0 17m5s [{Origin: i} {Nexthop: 0.0.0.0}]
65001 172.20.0.0/24 0.0.0.0 13h35m30s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w0 65001 172.16.1.1/32 0.0.0.0 17m5s [{Origin: i} {Nexthop: 0.0.0.0}]
65001 172.20.2.0/24 0.0.0.0 13h35m42s [{Origin: i} {Nexthop: 0.0.0.0}]
k8s-w1 65001 172.16.1.1/32 0.0.0.0 17m5s [{Origin: i} {Nexthop: 0.0.0.0}]
65001 172.20.1.0/24 0.0.0.0 13h35m43s [{Origin: i} {Nexthop: 0.0.0.0}]
- 그러나 여전히 모든 노드(
k8s-ctr,k8s-w0,k8s-w1)가172.16.1.1/32를 광고 - 그 결과, 라우터에서 불필요한 노드(k8s-ctr)로도 트래픽이 전달됨 → 비효율적인 경로 발생
5. Pod 부재에도 라우터 경로가 유지되는 문제
- 현재 Pod가 존재하지 않음에도 불구하고, 라우터에는 여전히
172.16.1.1/32경로가 유지됨 - 이는 모든 노드가 External IP를 광고하기 때문에 발생하는 현상임
6. Tcpdump로 확인한 불필요 경로 흐름
1
tcpdump -i eth1 -A -s 0 -nn 'tcp port 80'
- 신규 터미널(k8s-w1, k8s-w2, k8s-w0)에서 tcpdump 수행
1
2
root@router:~# LBIP=172.16.1.1
curl -s $LBIP
172.16.1.1호출 시, 요청이 k8s-ctr → k8s-w0로 이동하는 패킷이 동시에 관찰됨- 즉, Pod가 없는 노드로도 트래픽이 유입되어 불필요한 경로가 완성됨
📍 ExternalTrafficPolicy(Local) 적용 및 ECMP 해시 정책 변경
1. ExternalTrafficPolicy(Local) 적용
1
2
3
4
5
# 모니터링
(⎈|HomeLab:N/A) root@k8s-ctr:~# watch "sshpass -p 'vagrant' ssh vagrant@router ip -c route"
# k8s-ctr
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl patch service webpod -p '{"spec":{"externalTrafficPolicy":"Local"}}'
kubectl patch명령으로 Service의externalTrafficPolicy를 Local로 변경
1
root@router:~# vtysh -c 'show ip bgp'
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
BGP table version is 11, local router ID is 192.168.10.200, vrf id 0
Default local pref 100, local AS 65000
Status codes: s suppressed, d damped, h history, * valid, > best, = multipath,
i internal, r RIB-failure, S Stale, R Removed
Nexthop codes: @NNN nexthop's vrf id, < announce-nh-self
Origin codes: i - IGP, e - EGP, ? - incomplete
RPKI validation codes: V valid, I invalid, N Not found
Network Next Hop Metric LocPrf Weight Path
*> 10.10.1.0/24 0.0.0.0 0 32768 i
*= 172.16.1.1/32 192.168.20.100 0 65001 i
*> 192.168.10.101 0 65001 i
*> 172.20.0.0/24 192.168.10.100 0 65001 i
*> 172.20.1.0/24 192.168.10.101 0 65001 i
*> 172.20.2.0/24 192.168.20.100 0 65001 i
Displayed 5 routes and 6 total paths
- 변경 전(
Cluster)에는 모든 노드가 BGP 광고를 수행 → pod가 없는 노드까지 경로에 포함됨 - 변경 후(
Local)에는 pod가 존재하는 노드만 BGP 광고 → 불필요한 라우팅 제거 - 현재는
w0,w1노드만 광고
2. Linux ECMP 기본 해시 정책
1
2
3
root@router:~# LBIP=172.16.1.1
root@router:~# for i in {1..100}; do curl -s $LBIP | grep Hostname; done | sort | uniq -c | sort -nr
100 Hostname: webpod-697b545f57-xtmdx
- 리눅스는 기본적으로 L3 기반 해시 정책 사용
- 소스/목적지 IP가 동일할 경우, 여러 경로가 있어도 하나의 경로만 사용
curl테스트 시 특정 Pod만 100% 응답
3. ECMP Hash Policy 변경
1
2
3
4
5
root@router:~# sudo sysctl -w net.ipv4.fib_multipath_hash_policy=1
echo "net.ipv4.fib_multipath_hash_policy=1" >> /etc/sysctl.conf
# 결과
net.ipv4.fib_multipath_hash_policy = 1
net.ipv4.fib_multipath_hash_policy=1설정으로 L4 포트 기반 해시 적용- 소스 포트가 달라질 경우 다른 경로를 활용 가능 → 부하분산 개선
1
2
3
root@router:~# for i in {1..100}; do curl -s $LBIP | grep Hostname; done | sort | uniq -c | sort -nr
54 Hostname: webpod-697b545f57-5twrq
46 Hostname: webpod-697b545f57-xtmdx
4. Deployment 확장
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl scale deployment webpod --replicas 3
# 결과
deployment.apps/webpod scaled
kubectl scale명령으로 webpod를 3개 Replica로 확장- 새로운 Pod가 생성되면 해당 노드에서 즉시 BGP 경로 광고 반영
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl get pod -owide
✅ 출력
1
2
3
4
5
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
curl-pod 1/1 Running 1 (14h ago) 16h 172.20.0.35 k8s-ctr <none> <none>
webpod-697b545f57-5twrq 1/1 Running 0 14h 172.20.1.119 k8s-w1 <none> <none>
webpod-697b545f57-npkj5 1/1 Running 0 8s 172.20.0.159 k8s-ctr <none> <none>
webpod-697b545f57-xtmdx 1/1 Running 0 14h 172.20.2.35 k8s-w0 <none> <none>
- k8s-ctr 노드에도 새로운 Pod(
webpod-697b545f57-npkj5)가 배치되어 3개 Pod가 모두 다른 노드에 위치
5. 라우팅 경로 확인
1
root@router:~# ip -c route
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
default via 192.168.121.1 dev eth0 proto dhcp src 192.168.121.25 metric 100
10.10.1.0/24 dev loop1 proto kernel scope link src 10.10.1.200
10.10.2.0/24 dev loop2 proto kernel scope link src 10.10.2.200
172.16.1.1 nhid 114 proto bgp metric 20
nexthop via 192.168.10.101 dev eth1 weight 1
nexthop via 192.168.10.100 dev eth1 weight 1
nexthop via 192.168.20.100 dev eth2 weight 1
172.20.0.0/24 nhid 92 via 192.168.10.100 dev eth1 proto bgp metric 20
172.20.1.0/24 nhid 88 via 192.168.10.101 dev eth1 proto bgp metric 20
172.20.2.0/24 nhid 94 via 192.168.20.100 dev eth2 proto bgp metric 20
192.168.10.0/24 dev eth1 proto kernel scope link src 192.168.10.200
192.168.20.0/24 dev eth2 proto kernel scope link src 192.168.20.200
192.168.121.0/24 dev eth0 proto kernel scope link src 192.168.121.25 metric 100
192.168.121.1 dev eth0 proto dhcp scope link src 192.168.121.25 metric 100
- k8s-ctr 반영
6. ExternalTrafficPolicy 효과
- Cluster 모드: Pod가 없는 노드도 경유 가능 → 비효율적인 라우팅 발생
- Local 모드: 요청이 도달한 노드의 Pod에서 직접 응답 → 불필요한 hop 제거
7. 트래픽 분산 검증
1
2
3
4
root@router:~# for i in {1..100}; do curl -s $LBIP | grep Hostname; done | sort | uniq -c | sort -nr
35 Hostname: webpod-697b545f57-npkj5
34 Hostname: webpod-697b545f57-5twrq
31 Hostname: webpod-697b545f57-xtmdx
curl반복 테스트로 100번 요청 시, 3개 Pod로 균등하게 분산- ExternalTrafficPolicy(Local) + 스케일 아웃 조합으로 안정적이고 효율적인 부하분산 달성
BGP + SNAT + Random → 권장 방식
- BGP(ECMP) 기반 라우팅과 K8S Service(LB EX-IP, ExternalTrafficPolicy: Local)를 조합
- SNAT 적용 + Random 알고리즘 → 가장 단순하고 일반적으로 권장되는 방식
🧮 DSR + Maglev 방식 → 그나마 괜찮은 방식
- BGP(ECMP) + Service(LB EX-IP, ExternalTrafficPolicy: Cluster) + DSR + Maglev
- Geneve 헤더 encapsulation 필요
1. DSR 도입 배경
2. Cilium 설정 확인
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl exec -it -n kube-system ds/cilium -- cilium status --verbose
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
...
KubeProxyReplacement Details:
Status: True
Socket LB: Enabled
Socket LB Tracing: Enabled
Socket LB Coverage: Full
Devices: eth0 fe80::5054:ff:fea7:8e7a 192.168.121.62, eth1 192.168.10.101 fe80::5054:ff:fefb:b52e (Direct Routing)
Mode: SNAT
Backend Selection: Random
Session Affinity: Enabled
NAT46/64 Support: Disabled
XDP Acceleration: Disabled
Services:
- ClusterIP: Enabled
- NodePort: Enabled (Range: 30000-32767)
- LoadBalancer: Enabled
- externalIPs: Enabled
- HostPort: Enabled
Annotations:
- service.cilium.io/node
- service.cilium.io/node-selector
- service.cilium.io/proxy-delegation
- service.cilium.io/src-ranges-policy
- service.cilium.io/type
...
- Mode: SNAT (초기 상태)
- Backend Selection: Random
3. 모듈 준비 (Geneve)
1
2
3
4
5
(⎈|HomeLab:N/A) root@k8s-ctr:~# modprobe geneve
(⎈|HomeLab:N/A) root@k8s-ctr:~# for i in w1 w0 ; do echo ">> node : k8s-$i <<"; sshpass -p 'vagrant' ssh vagrant@k8s-$i sudo modprobe geneve ; echo; done
>> node : k8s-w1 <<
>> node : k8s-w0 <<
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
(⎈|HomeLab:N/A) root@k8s-ctr:~# lsmod | grep -E 'vxlan|geneve'
geneve 49152 0
ip6_udp_tunnel 16384 1 geneve
udp_tunnel 32768 1 geneve
(⎈|HomeLab:N/A) root@k8s-ctr:~# for i in w1 w0 ; do echo ">> node : k8s-$i <<"; sshpass -p 'vagrant' ssh vagrant@k8s-$i sudo lsmod | grep -E 'vxlan|geneve' ; echo; done
>> node : k8s-w1 <<
geneve 49152 0
ip6_udp_tunnel 16384 1 geneve
udp_tunnel 32768 1 geneve
>> node : k8s-w0 <<
geneve 49152 0
ip6_udp_tunnel 16384 1 geneve
udp_tunnel 32768 1 geneve
- 모든 노드에 geneve 모듈 로드 완료
- geneve는 노드 간 파드 통신 전체에 쓰는 게 아니라, DSR 전송 경유 시에만 사용됨
4. Helm으로 Cilium DSR 모드 적용
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
(⎈|HomeLab:N/A) root@k8s-ctr:~# helm upgrade cilium cilium/cilium --version 1.18.0 --namespace kube-system --reuse-values \
--set tunnelProtocol=geneve --set loadBalancer.mode=dsr --set loadBalancer.dsrDispatch=geneve \
--set loadBalancer.algorithm=maglev
# 결과
Release "cilium" has been upgraded. Happy Helming!
NAME: cilium
LAST DEPLOYED: Sat Aug 16 17:29:45 2025
NAMESPACE: kube-system
STATUS: deployed
REVISION: 3
TEST SUITE: None
NOTES:
You have successfully installed Cilium with Hubble Relay and Hubble UI.
Your release version is 1.18.0.
For any further help, visit https://docs.cilium.io/en/v1.18/gettinghelp
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl -n kube-system rollout restart ds/cilium
# 결과
daemonset.apps/cilium restarted
1
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl exec -it -n kube-system ds/cilium -- cilium status --verbose
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
...
KubeProxyReplacement Details:
Status: True
Socket LB: Enabled
Socket LB Tracing: Enabled
Socket LB Coverage: Full
Devices: eth0 192.168.121.62 fe80::5054:ff:fea7:8e7a, eth1 192.168.10.101 fe80::5054:ff:fefb:b52e (Direct Routing)
Mode: DSR
DSR Dispatch Mode: Geneve
Backend Selection: Maglev (Table Size: 16381)
Session Affinity: Enabled
NAT46/64 Support: Disabled
XDP Acceleration: Disabled
Services:
- ClusterIP: Enabled
- NodePort: Enabled (Range: 30000-32767)
- LoadBalancer: Enabled
- externalIPs: Enabled
- HostPort: Enabled
Annotations:
- service.cilium.io/node
- service.cilium.io/node-selector
- service.cilium.io/proxy-delegation
- service.cilium.io/src-ranges-policy
- service.cilium.io/type
...
- Mode: DSR
- DSR Dispatch Mode: Geneve
- Backend Selection: Maglev
5. ExternalTrafficPolicy Cluster로 원복
1
2
3
4
(⎈|HomeLab:N/A) root@k8s-ctr:~# kubectl patch svc webpod -p '{"spec":{"externalTrafficPolicy":"Cluster"}}'
# 결과
service/webpod patched
- 다시 Cluster 모드로 복원
6. DSR 패킷 캡처
(1) 패킷 캡처 준비
1
tcpdump -i eth1 -w /tmp/dsr.pcap
- k8s-ctr, k8s-w1, k8s-w0 모두 tcpdump 실행
(2) 외부 접근 테스트
1
2
root@router:~# curl -s $LBIP
root@router:~# curl -s $LBIP
- 외부 라우터에서 LBIP로 curl 요청
(3) 캡처 파일 확인
1
2
3
4
5
6
7
8
vagrant plugin install vagrant-scp
# 결과
Installing the 'vagrant-scp' plugin. This can take a few minutes...
Building native extensions. This could take a while...
Building native extensions. This could take a while...
Fetching vagrant-scp-0.5.9.gem
Installed the plugin 'vagrant-scp (0.5.9)'!
- Vagrant scp 플러그인 설치
1
2
3
4
5
6
vagrant scp k8s-ctr:/tmp/dsr.pcap .
# 결과
[fog][WARNING] Unrecognized arguments: libvirt_ip_command
Warning: Permanently added '192.168.121.70' (ED25519) to the list of known hosts.
dsr.pcap 100% 94KB 46.4MB/s 00:00
- pcap 파일을 Host로 전송 후 Termshark로 열어 분석
1
termshark -r dsr.pcap
- 출발지 IP: 192.168.10.100
- 목적지 IP: 192.168.20.100 (k8s-w0)
- 외부 접근이 컨트롤플레인으로 들어온 뒤 워커 노드로 전달된 것 확인
- Geneve encapsulation 헤더 존재
- 컨트롤플레인(k8s-ctr)에서 외부 클라이언트(router) 로 바로 리턴하는 패킷 존재
- D.IP / D.Port = 최초 요청 시 S.IP / S.Port 그대로 유지됨
- 즉, SNAT이 아닌 DSR 방식으로 응답이 전달됨
🧩 ClusterMesh 환경 준비
1. West 클러스터 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
kind create cluster --name west --image kindest/node:v1.33.2 --config - <<EOF
kind: Cluster
apiVersion: kind.x-k8s.io/v1alpha4
nodes:
- role: control-plane
extraPortMappings:
- containerPort: 30000 # sample apps
hostPort: 30000
- containerPort: 30001 # hubble ui
hostPort: 30001
- role: worker
extraPortMappings:
- containerPort: 30002 # sample apps
hostPort: 30002
networking:
podSubnet: "10.0.0.0/16"
serviceSubnet: "10.2.0.0/16"
disableDefaultCNI: true
kubeProxyMode: none
EOF
# 결과
Creating cluster "west" ...
✓ Ensuring node image (kindest/node:v1.33.2) 🖼
✓ Preparing nodes 📦 📦
✓ Writing configuration 📜
✓ Starting control-plane 🕹️
✓ Installing StorageClass 💾
✓ Joining worker nodes 🚜
Set kubectl context to "kind-west"
You can now use your cluster with:
kubectl cluster-info --context kind-west
Have a question, bug, or feature request? Let us know! https://kind.sigs.k8s.io/#community 🙂
2. East 클러스터 생성
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
kind create cluster --name east --image kindest/node:v1.33.2 --config - <<EOF
kind: Cluster
apiVersion: kind.x-k8s.io/v1alpha4
nodes:
- role: control-plane
extraPortMappings:
- containerPort: 31000 # sample apps
hostPort: 31000
- containerPort: 31001 # hubble ui
hostPort: 31001
- role: worker
extraPortMappings:
- containerPort: 31002 # sample apps
hostPort: 31002
networking:
podSubnet: "10.1.0.0/16"
serviceSubnet: "10.3.0.0/16"
disableDefaultCNI: true
kubeProxyMode: none
EOF
# 결과
Creating cluster "east" ...
✓ Ensuring node image (kindest/node:v1.33.2) 🖼
✓ Preparing nodes 📦 📦
✓ Writing configuration 📜
✓ Starting control-plane 🕹️
✓ Installing StorageClass 💾
✓ Joining worker nodes 🚜
Set kubectl context to "kind-east"
You can now use your cluster with:
kubectl cluster-info --context kind-east
Not sure what to do next? 😅 Check out https://kind.sigs.k8s.io/docs/user/quick-start/
3. 컨텍스트 확인
1
kubectl config get-contexts
✅ 출력
1
2
3
CURRENT NAME CLUSTER AUTHINFO NAMESPACE
* kind-east kind-east kind-east
kind-west kind-west kind-west
- 두 클러스터가 kubeconfig에 정상 등록됨 확인
4. 노드 기본 툴 설치
1
2
3
4
docker exec -it west-control-plane sh -c 'apt update && apt install tree psmisc lsof wget net-tools dnsutils tcpdump ngrep iputils-ping git -y'
docker exec -it west-worker sh -c 'apt update && apt install tree psmisc lsof wget net-tools dnsutils tcpdump ngrep iputils-ping git -y'
docker exec -it east-control-plane sh -c 'apt update && apt install tree psmisc lsof wget net-tools dnsutils tcpdump ngrep iputils-ping git -y'
docker exec -it east-worker sh -c 'apt update && apt install tree psmisc lsof wget net-tools dnsutils tcpdump ngrep iputils-ping git -y'
5. Context 전환 및 노드 조회
1
2
3
4
kubectl config set-context kind-east
# 결과
Context "kind-east" modified.
- 기본 context를 east로 변경
1
kubectl get node -v=6 --context kind-east
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
I0816 18:18:58.547416 180043 loader.go:402] Config loaded from file: /home/devshin/.kube/config
I0816 18:18:58.547878 180043 envvar.go:172] "Feature gate default state" feature="WatchListClient" enabled=false
I0816 18:18:58.547890 180043 envvar.go:172] "Feature gate default state" feature="ClientsAllowCBOR" enabled=false
I0816 18:18:58.547898 180043 envvar.go:172] "Feature gate default state" feature="ClientsPreferCBOR" enabled=false
I0816 18:18:58.547901 180043 envvar.go:172] "Feature gate default state" feature="InformerResourceVersion" enabled=false
I0816 18:18:58.561481 180043 round_trippers.go:560] GET https://127.0.0.1:38631/api?timeout=32s 200 OK in 13 milliseconds
I0816 18:18:58.564716 180043 round_trippers.go:560] GET https://127.0.0.1:38631/apis?timeout=32s 200 OK in 1 milliseconds
I0816 18:18:58.598067 180043 round_trippers.go:560] GET https://127.0.0.1:38631/api/v1/nodes?limit=500 200 OK in 14 milliseconds
NAME STATUS ROLES AGE VERSION
east-control-plane NotReady control-plane 7m31s v1.33.2
east-worker NotReady <none> 7m20s v1.33.2
1
kubectl get node -v=6
✅ 출력
1
2
3
4
5
6
7
8
9
I0816 18:19:58.446920 180152 loader.go:402] Config loaded from file: /home/devshin/.kube/config
I0816 18:19:58.449078 180152 envvar.go:172] "Feature gate default state" feature="ClientsAllowCBOR" enabled=false
I0816 18:19:58.449176 180152 envvar.go:172] "Feature gate default state" feature="ClientsPreferCBOR" enabled=false
I0816 18:19:58.449218 180152 envvar.go:172] "Feature gate default state" feature="InformerResourceVersion" enabled=false
I0816 18:19:58.449263 180152 envvar.go:172] "Feature gate default state" feature="WatchListClient" enabled=false
I0816 18:19:58.465153 180152 round_trippers.go:560] GET https://127.0.0.1:38631/api/v1/nodes?limit=500 200 OK in 7 milliseconds
NAME STATUS ROLES AGE VERSION
east-control-plane NotReady control-plane 8m31s v1.33.2
east-worker NotReady <none> 8m20s v1.33.2
- east 클러스터 노드 정보 출력
1
kubectl get node -v=6 --context kind-west
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
I0816 18:21:10.714221 180273 loader.go:402] Config loaded from file: /home/devshin/.kube/config
I0816 18:21:10.719211 180273 envvar.go:172] "Feature gate default state" feature="WatchListClient" enabled=false
I0816 18:21:10.719796 180273 envvar.go:172] "Feature gate default state" feature="ClientsAllowCBOR" enabled=false
I0816 18:21:10.719902 180273 envvar.go:172] "Feature gate default state" feature="ClientsPreferCBOR" enabled=false
I0816 18:21:10.719986 180273 envvar.go:172] "Feature gate default state" feature="InformerResourceVersion" enabled=false
I0816 18:21:10.741286 180273 round_trippers.go:560] GET https://127.0.0.1:43999/api?timeout=32s 200 OK in 19 milliseconds
I0816 18:21:10.743285 180273 round_trippers.go:560] GET https://127.0.0.1:43999/apis?timeout=32s 200 OK in 1 milliseconds
I0816 18:21:10.751821 180273 round_trippers.go:560] GET https://127.0.0.1:43999/api/v1/nodes?limit=500 200 OK in 4 milliseconds
NAME STATUS ROLES AGE VERSION
west-control-plane NotReady control-plane 10m v1.33.2
west-worker NotReady <none> 10m v1.33.2
--context옵션을 주면 west 클러스터 정보도 확인 가능
6. 노드 상태 확인
1
kubectl get pod -A
✅ 출력
1
2
3
4
5
6
7
8
NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system coredns-674b8bbfcf-2tm2l 0/1 Pending 0 10m
kube-system coredns-674b8bbfcf-c9qsg 0/1 Pending 0 10m
kube-system etcd-east-control-plane 1/1 Running 0 10m
kube-system kube-apiserver-east-control-plane 1/1 Running 0 10m
kube-system kube-controller-manager-east-control-plane 1/1 Running 0 10m
kube-system kube-scheduler-east-control-plane 1/1 Running 0 10m
local-path-storage local-path-provisioner-7dc846544d-mwfdc 0/1 Pending 0 10m
- 현재 kube-proxy와 CNI를 설치하지 않았기 때문에 모든 노드 상태는 NotReady
- System Pod(coredns, local-path-provisioner 등)도 Pending 상태
7. Context Alias 설정
1
2
alias kwest='kubectl --context kind-west'
alias keast='kubectl --context kind-east'
8. 노드 상세 정보
1
2
3
4
5
kwest get node -owide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
west-control-plane NotReady control-plane 14m v1.33.2 172.18.0.2 <none> Debian GNU/Linux 12 (bookworm) 6.16.0-arch2-1 containerd://2.1.3
west-worker NotReady <none> 14m v1.33.2 172.18.0.3 <none> Debian GNU/Linux 12 (bookworm) 6.16.0-arch2-1 containerd://2.1.3
1
2
3
4
5
keast get node -owide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
east-control-plane NotReady control-plane 13m v1.33.2 172.18.0.4 <none> Debian GNU/Linux 12 (bookworm) 6.16.0-arch2-1 containerd://2.1.3
east-worker NotReady <none> 13m v1.33.2 172.18.0.5 <none> Debian GNU/Linux 12 (bookworm) 6.16.0-arch2-1 containerd://2.1.3
🕸️ Cilium CNI 배포 : ClusterMesh
1. Cilium CLI 설치
1
2
3
4
5
6
7
8
9
10
CILIUM_CLI_VERSION=$(curl -s https://raw.githubusercontent.com/cilium/cilium-cli/main/stable.txt)
CLI_ARCH=amd64
if [ "$(uname -m)" = "aarch64" ]; then CLI_ARCH=arm64; fi
curl -L --fail --remote-name-all \
https://github.com/cilium/cilium-cli/releases/download/${CILIUM_CLI_VERSION}/cilium-linux-${CLI_ARCH}.tar.gz{,.sha256sum}
sha256sum --check cilium-linux-${CLI_ARCH}.tar.gz.sha256sum
sudo tar xzvfC cilium-linux-${CLI_ARCH}.tar.gz /usr/local/bin
rm cilium-linux-${CLI_ARCH}.tar.gz{,.sha256sum}
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
100 56.6M 100 56.6M 0 0 16.1M 0 0:00:03 0:00:03 --:--:-- 18.2M
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
100 92 100 92 0 0 338 0 --:--:-- --:--:-- --:--:-- 338
cilium-linux-amd64.tar.gz: OK
cilium
- Host OS에
ciliumCLI 설치
2. West 클러스터에 Cilium 설치
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
cilium install --version 1.17.6 --set ipam.mode=kubernetes \
--set kubeProxyReplacement=true --set bpf.masquerade=true \
--set endpointHealthChecking.enabled=false --set healthChecking=false \
--set operator.replicas=1 --set debug.enabled=true \
--set routingMode=native --set autoDirectNodeRoutes=true --set ipv4NativeRoutingCIDR=10.0.0.0/16 \
--set ipMasqAgent.enabled=true --set ipMasqAgent.config.nonMasqueradeCIDRs='{10.1.0.0/16}' \
--set cluster.name=west --set cluster.id=1 \
--context kind-west
# 결과
🔮 Auto-detected Kubernetes kind: kind
ℹ️ Using Cilium version 1.17.6
ℹ️ Using cluster name "west"
ℹ️ Detecting real Kubernetes API server addr and port on Kind
🔮 Auto-detected kube-proxy has not been installed
ℹ️ Cilium will fully replace all functionalities of kube-proxy
cilium install명령어로 1.17.6 버전 설치routingMode=native,autoDirectNodeRoutes=true,ipv4NativeRoutingCIDR=10.0.0.0/16cluster.name=west,cluster.id=1
3. East 클러스터에 Cilium 설치
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
cilium install --version 1.17.6 --set ipam.mode=kubernetes \
--set kubeProxyReplacement=true --set bpf.masquerade=true \
--set endpointHealthChecking.enabled=false --set healthChecking=false \
--set operator.replicas=1 --set debug.enabled=true \
--set routingMode=native --set autoDirectNodeRoutes=true --set ipv4NativeRoutingCIDR=10.1.0.0/16 \
--set ipMasqAgent.enabled=true --set ipMasqAgent.config.nonMasqueradeCIDRs='{10.0.0.0/16}' \
--set cluster.name=east --set cluster.id=2 \
--context kind-east
# 결과
🔮 Auto-detected Kubernetes kind: kind
ℹ️ Using Cilium version 1.17.6
ℹ️ Using cluster name "east"
ℹ️ Detecting real Kubernetes API server addr and port on Kind
🔮 Auto-detected kube-proxy has not been installed
ℹ️ Cilium will fully replace all functionalities of kube-proxy
routingMode=native,autoDirectNodeRoutes=true,ipv4NativeRoutingCIDR=10.1.0.0/16cluster.name=east,cluster.id=2
4. 설치 확인 (West/East Pod 상태)
1
kwest get pod -A && keast get pod -A
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system cilium-9jlht 1/1 Running 0 2m22s
kube-system cilium-envoy-5gpxx 1/1 Running 0 2m22s
kube-system cilium-envoy-skv7b 1/1 Running 0 2m22s
kube-system cilium-operator-7dbb574d5b-drtg2 1/1 Running 0 2m22s
kube-system cilium-qvpkv 1/1 Running 0 2m22s
kube-system coredns-674b8bbfcf-kwxv5 1/1 Running 0 34m
kube-system coredns-674b8bbfcf-nb96t 1/1 Running 0 34m
kube-system etcd-west-control-plane 1/1 Running 0 34m
kube-system kube-apiserver-west-control-plane 1/1 Running 0 34m
kube-system kube-controller-manager-west-control-plane 1/1 Running 0 34m
kube-system kube-scheduler-west-control-plane 1/1 Running 0 34m
local-path-storage local-path-provisioner-7dc846544d-jrdw8 1/1 Running 0 34m
NAMESPACE NAME READY STATUS RESTARTS AGE
kube-system cilium-envoy-mrzw8 1/1 Running 0 94s
kube-system cilium-envoy-vq5r7 1/1 Running 0 94s
kube-system cilium-kxddr 1/1 Running 0 94s
kube-system cilium-operator-867f8dc978-44zqb 1/1 Running 0 94s
kube-system cilium-qn52j 1/1 Running 0 94s
kube-system coredns-674b8bbfcf-2tm2l 1/1 Running 0 33m
kube-system coredns-674b8bbfcf-c9qsg 1/1 Running 0 33m
kube-system etcd-east-control-plane 1/1 Running 0 33m
kube-system kube-apiserver-east-control-plane 1/1 Running 0 33m
kube-system kube-controller-manager-east-control-plane 1/1 Running 0 33m
kube-system kube-scheduler-east-control-plane 1/1 Running 0 33m
local-path-storage local-path-provisioner-7dc846544d-mwfdc 1/1 Running 0 33m
- Cilium DaemonSet, Envoy, Operator 정상 실행 (Running)
- CoreDNS, etcd, apiserver, controller, scheduler, local-path-provisioner 모두 정상
1
cilium status --context kind-west
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
/¯¯\
/¯¯\__/¯¯\ Cilium: OK
\__/¯¯\__/ Operator: OK
/¯¯\__/¯¯\ Envoy DaemonSet: OK
\__/¯¯\__/ Hubble Relay: disabled
\__/ ClusterMesh: disabled
DaemonSet cilium Desired: 2, Ready: 2/2, Available: 2/2
DaemonSet cilium-envoy Desired: 2, Ready: 2/2, Available: 2/2
Deployment cilium-operator Desired: 1, Ready: 1/1, Available: 1/1
Containers: cilium Running: 2
cilium-envoy Running: 2
cilium-operator Running: 1
clustermesh-apiserver
hubble-relay
Cluster Pods: 3/3 managed by Cilium
Helm chart version: 1.17.6
Image versions cilium quay.io/cilium/cilium:v1.17.6@sha256:544de3d4fed7acba72758413812780a4972d47c39035f2a06d6145d8644a3353: 2
cilium-envoy quay.io/cilium/cilium-envoy:v1.33.4-1752151664-7c2edb0b44cf95f326d628b837fcdd845102ba68@sha256:318eff387835ca2717baab42a84f35a83a5f9e7d519253df87269f80b9ff0171: 2
cilium-operator quay.io/cilium/operator-generic:v1.17.6@sha256:91ac3bf7be7bed30e90218f219d4f3062a63377689ee7246062fa0cc3839d096: 1
1
cilium status --context kind-east
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
/¯¯\
/¯¯\__/¯¯\ Cilium: OK
\__/¯¯\__/ Operator: OK
/¯¯\__/¯¯\ Envoy DaemonSet: OK
\__/¯¯\__/ Hubble Relay: disabled
\__/ ClusterMesh: disabled
DaemonSet cilium Desired: 2, Ready: 2/2, Available: 2/2
DaemonSet cilium-envoy Desired: 2, Ready: 2/2, Available: 2/2
Deployment cilium-operator Desired: 1, Ready: 1/1, Available: 1/1
Containers: cilium Running: 2
cilium-envoy Running: 2
cilium-operator Running: 1
clustermesh-apiserver
hubble-relay
Cluster Pods: 3/3 managed by Cilium
Helm chart version: 1.17.6
Image versions cilium quay.io/cilium/cilium:v1.17.6@sha256:544de3d4fed7acba72758413812780a4972d47c39035f2a06d6145d8644a3353: 2
cilium-envoy quay.io/cilium/cilium-envoy:v1.33.4-1752151664-7c2edb0b44cf95f326d628b837fcdd845102ba68@sha256:318eff387835ca2717baab42a84f35a83a5f9e7d519253df87269f80b9ff0171: 2
cilium-operator quay.io/cilium/operator-generic:v1.17.6@sha256:91ac3bf7be7bed30e90218f219d4f3062a63377689ee7246062fa0cc3839d096: 1
DaemonSet,Envoy,Operator→ Desired와 Ready 수 일치 (정상 배포 완료)- ClusterMesh, Hubble Relay → 아직 disabled 상태
5. IP Masquerading 설정 확인
1
kwest -n kube-system exec ds/cilium -c cilium-agent -- cilium-dbg bpf ipmasq list
✅ 출력
1
2
3
IP PREFIX/ADDRESS
10.1.0.0/16
169.254.0.0/16
1
keast -n kube-system exec ds/cilium -c cilium-agent -- cilium-dbg bpf ipmasq list
✅ 출력
1
2
3
IP PREFIX/ADDRESS
10.0.0.0/16
169.254.0.0/16
- 서로 상대 클러스터의 Pod CIDR 대역이 non-masquerade 처리 되어 있음
6. CoreDNS 설정 확인
1
kubectl describe cm -n kube-system coredns --context kind-west | grep kubernetes
✅ 출력
1
kubernetes cluster.local in-addr.arpa ip6.arpa {
1
kubectl describe cm -n kube-system coredns --context kind-west | grep kubernetes
✅ 출력
1
kubernetes cluster.local in-addr.arpa ip6.arpa {
cluster.local도메인 사용- ConfigMap 출력에서
kubernetes cluster.local in-addr.arpa ip6.arpa확인
🚀 Setting up Cluster Mesh
1. 초기 상태: 상호 Pod CIDR 알 수 없음
1
2
3
4
docker exec -it west-control-plane ip -c route
docker exec -it west-worker ip -c route
docker exec -it east-control-plane ip -c route
docker exec -it east-worker ip -c route
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
default via 172.18.0.1 dev eth0
10.0.0.0/24 via 10.0.0.19 dev cilium_host proto kernel src 10.0.0.19
10.0.0.19 dev cilium_host proto kernel scope link
10.0.1.0/24 via 172.18.0.3 dev eth0 proto kernel
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.2
default via 172.18.0.1 dev eth0
10.0.0.0/24 via 172.18.0.2 dev eth0 proto kernel
10.0.1.0/24 via 10.0.1.99 dev cilium_host proto kernel src 10.0.1.99
10.0.1.99 dev cilium_host proto kernel scope link
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.3
default via 172.18.0.1 dev eth0
10.1.0.0/24 via 10.1.0.165 dev cilium_host proto kernel src 10.1.0.165
10.1.0.165 dev cilium_host proto kernel scope link
10.1.1.0/24 via 172.18.0.5 dev eth0 proto kernel
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.4
default via 172.18.0.1 dev eth0
10.1.0.0/24 via 172.18.0.4 dev eth0 proto kernel
10.1.1.0/24 via 10.1.1.122 dev cilium_host proto kernel src 10.1.1.122
10.1.1.122 dev cilium_host proto kernel scope link
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.5
kind환경은 Docker 네트워크 위에서 동작하고 BGP를 사용하지 않음- 따라서 West ↔ East 클러스터 간 Pod CIDR 라우팅 정보가 기본적으로 존재하지 않음
ip route확인 결과, 각 클러스터는 자기 Pod CIDR만 알고 있고 상대방의 Pod CIDR은 알 수 없음
2. CA Secret 동기화
1
2
3
4
5
6
7
8
9
keast get secret -n kube-system cilium-ca
NAME TYPE DATA AGE
cilium-ca Opaque 2 14m
keast delete secret -n kube-system cilium-ca
secret "cilium-ca" deleted
keast get secret -n kube-system cilium-ca
Error from server (NotFound): secrets "cilium-ca" not found
east클러스터의 기본cilium-caSecret 삭제
1
2
3
4
5
kubectl --context kind-west get secret -n kube-system cilium-ca -o yaml | \
kubectl --context kind-east create -f -
# 결과
secret/cilium-ca created
west클러스터의cilium-caSecret을east클러스터로 가져와 생성
1
2
3
keast get secret -n kube-system cilium-ca
NAME TYPE DATA AGE
cilium-ca Opaque 2 62s
- 양쪽 클러스터가 동일한 CA를 공유하여 상호 TLS 인증 기반 통신 가능
3. ClusterMesh 상태 모니터링
1
2
cilium clustermesh status --context kind-west --wait
cilium clustermesh status --context kind-east --wait
4. ClusterMesh 활성화
1
cilium clustermesh enable --service-type NodePort --enable-kvstoremesh=false --context kind-west
1
cilium clustermesh enable --service-type NodePort --enable-kvstoremesh=false --context kind-east
- 각 클러스터에서
cilium clustermesh enable실행
5. West 클러스터 Service/Endpoint 확인
1
kwest get svc,ep -n kube-system clustermesh-apiserver --context kind-west
✅ 출력
1
2
3
4
5
6
Warning: v1 Endpoints is deprecated in v1.33+; use discovery.k8s.io/v1 EndpointSlice
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/clustermesh-apiserver NodePort 10.2.126.217 <none> 2379:32379/TCP 2m57s
NAME ENDPOINTS AGE
endpoints/clustermesh-apiserver 10.0.1.8:2379 2m57s
clustermesh-apiserverService 생성, 타입은 NodePort- ClusterIP:
10.2.126.217, Port:2379:32379/TCP NodePort (32379)로 외부 노드 간 통신 채널 개방- Endpoint:
10.0.1.8:2379
6. West 클러스터 Pod 상태 확인
1
kwest get pod -n kube-system -owide | grep clustermesh
✅ 출력
1
2
clustermesh-apiserver-5cf45db9cc-2g847 2/2 Running 0 4m29s 10.0.1.8 west-worker <none> <none>
clustermesh-apiserver-generate-certs-pl6ws 0/1 Completed 0 4m29s 172.18.0.3 west-worker <none> <none>
7. East 클러스터 Service/Endpoint 확인
1
keast get svc,ep -n kube-system clustermesh-apiserver --context kind-east
✅ 출력
1
2
3
4
5
6
Warning: v1 Endpoints is deprecated in v1.33+; use discovery.k8s.io/v1 EndpointSlice
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/clustermesh-apiserver NodePort 10.3.173.28 <none> 2379:32379/TCP 3m47s
NAME ENDPOINTS AGE
endpoints/clustermesh-apiserver 10.1.1.62:2379 3m47s
- ClusterIP:
10.3.173.28, Port:2379:32379/TCP - Endpoint:
10.1.1.62:2379
8. ClusterMesh 상태 모니터링
1
2
watch -d "cilium clustermesh status --context kind-west --wait"
watch -d "cilium clustermesh status --context kind-east --wait"
9. ClusterMesh 연결 실행 (West → East)
1
cilium clustermesh connect --context kind-west --destination-context kind-east
10. ClusterMesh 정상 연결 확인 (West/East)
1
cilium status --context kind-west
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
/¯¯\
/¯¯\__/¯¯\ Cilium: OK
\__/¯¯\__/ Operator: OK
/¯¯\__/¯¯\ Envoy DaemonSet: OK
\__/¯¯\__/ Hubble Relay: disabled
\__/ ClusterMesh: OK
DaemonSet cilium Desired: 2, Ready: 2/2, Available: 2/2
DaemonSet cilium-envoy Desired: 2, Ready: 2/2, Available: 2/2
Deployment cilium-operator Desired: 1, Ready: 1/1, Available: 1/1
Deployment clustermesh-apiserver Desired: 1, Ready: 1/1, Available: 1/1
Containers: cilium Running: 2
cilium-envoy Running: 2
cilium-operator Running: 1
clustermesh-apiserver Running: 1
hubble-relay
Cluster Pods: 4/4 managed by Cilium
Helm chart version: 1.17.6
Image versions cilium quay.io/cilium/cilium:v1.17.6@sha256:544de3d4fed7acba72758413812780a4972d47c39035f2a06d6145d8644a3353: 2
cilium-envoy quay.io/cilium/cilium-envoy:v1.33.4-1752151664-7c2edb0b44cf95f326d628b837fcdd845102ba68@sha256:318eff387835ca2717baab42a84f35a83a5f9e7d519253df87269f80b9ff0171: 2
cilium-operator quay.io/cilium/operator-generic:v1.17.6@sha256:91ac3bf7be7bed30e90218f219d4f3062a63377689ee7246062fa0cc3839d096: 1
clustermesh-apiserver quay.io/cilium/clustermesh-apiserver:v1.17.6@sha256:f619e97432db427e1511bf91af3be8ded418c53a353a09629e04c5880659d1df: 2
1
cilium status --context kind-east
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
/¯¯\
/¯¯\__/¯¯\ Cilium: OK
\__/¯¯\__/ Operator: OK
/¯¯\__/¯¯\ Envoy DaemonSet: OK
\__/¯¯\__/ Hubble Relay: disabled
\__/ ClusterMesh: OK
DaemonSet cilium Desired: 2, Ready: 2/2, Available: 2/2
DaemonSet cilium-envoy Desired: 2, Ready: 2/2, Available: 2/2
Deployment cilium-operator Desired: 1, Ready: 1/1, Available: 1/1
Deployment clustermesh-apiserver Desired: 1, Ready: 1/1, Available: 1/1
Containers: cilium Running: 2
cilium-envoy Running: 2
cilium-operator Running: 1
clustermesh-apiserver Running: 1
hubble-relay
Cluster Pods: 4/4 managed by Cilium
Helm chart version: 1.17.6
Image versions cilium quay.io/cilium/cilium:v1.17.6@sha256:544de3d4fed7acba72758413812780a4972d47c39035f2a06d6145d8644a3353: 2
cilium-envoy quay.io/cilium/cilium-envoy:v1.33.4-1752151664-7c2edb0b44cf95f326d628b837fcdd845102ba68@sha256:318eff387835ca2717baab42a84f35a83a5f9e7d519253df87269f80b9ff0171: 2
cilium-operator quay.io/cilium/operator-generic:v1.17.6@sha256:91ac3bf7be7bed30e90218f219d4f3062a63377689ee7246062fa0cc3839d096: 1
clustermesh-apiserver quay.io/cilium/clustermesh-apiserver:v1.17.6@sha256:f619e97432db427e1511bf91af3be8ded418c53a353a09629e04c5880659d1df: 2
cilium status확인 결과, 양쪽 클러스터 모두 ClusterMesh: OK 출력- DaemonSet, Envoy, Operator, clustermesh-apiserver 모두 Running 상태이며, 연결 안정적
11. 상세 상태 확인 (Verbose Mode)
1
kwest exec -it -n kube-system ds/cilium -- cilium status --verbose
✅ 출력
1
2
3
4
5
6
7
...
ClusterMesh: 1/1 remote clusters ready, 0 global-services
east: ready, 2 nodes, 4 endpoints, 3 identities, 0 services, 0 MCS-API service exports, 0 reconnections (last: never)
└ etcd: 1/1 connected, leases=0, lock leases=0, has-quorum=true: endpoint status checks are disabled, ID: b88364e6e9ad8658
└ remote configuration: expected=true, retrieved=true, cluster-id=2, kvstoremesh=false, sync-canaries=true, service-exports=disabled
└ synchronization status: nodes=true, endpoints=true, identities=true, services=true
...
1
keast exec -it -n kube-system ds/cilium -- cilium status --verbose
✅ 출력
1
2
3
4
5
6
7
...
ClusterMesh: 1/1 remote clusters ready, 0 global-services
west: ready, 2 nodes, 4 endpoints, 3 identities, 0 services, 0 MCS-API service exports, 0 reconnections (last: never)
└ etcd: 1/1 connected, leases=0, lock leases=0, has-quorum=true: endpoint status checks are disabled, ID: 700452e5b45c47e8
└ remote configuration: expected=true, retrieved=true, cluster-id=1, kvstoremesh=false, sync-canaries=true, service-exports=disabled
└ synchronization status: nodes=true, endpoints=true, identities=true, services=true
...
- west 클러스터에서 east, east 클러스터에서 west 상태를 상세 조회
- 동기화 항목:
nodes=true,endpoints=true,identities=true,services=true→ 동기화 정상 - etcd 연결도 1/1 connected, quorum 확보됨
12. Pod CIDR 라우팅 자동 주입 확인
1
2
3
4
docker exec -it west-control-plane ip -c route
docker exec -it west-worker ip -c route
docker exec -it east-control-plane ip -c route
docker exec -it east-worker ip -c route
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
default via 172.18.0.1 dev eth0
10.0.0.0/24 via 10.0.0.19 dev cilium_host proto kernel src 10.0.0.19
10.0.0.19 dev cilium_host proto kernel scope link
10.0.1.0/24 via 172.18.0.3 dev eth0 proto kernel
10.1.0.0/24 via 172.18.0.4 dev eth0 proto kernel
10.1.1.0/24 via 172.18.0.5 dev eth0 proto kernel
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.2
default via 172.18.0.1 dev eth0
10.0.0.0/24 via 172.18.0.2 dev eth0 proto kernel
10.0.1.0/24 via 10.0.1.99 dev cilium_host proto kernel src 10.0.1.99
10.0.1.99 dev cilium_host proto kernel scope link
10.1.0.0/24 via 172.18.0.4 dev eth0 proto kernel
10.1.1.0/24 via 172.18.0.5 dev eth0 proto kernel
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.3
default via 172.18.0.1 dev eth0
10.0.0.0/24 via 172.18.0.2 dev eth0 proto kernel
10.0.1.0/24 via 172.18.0.3 dev eth0 proto kernel
10.1.0.0/24 via 10.1.0.165 dev cilium_host proto kernel src 10.1.0.165
10.1.0.165 dev cilium_host proto kernel scope link
10.1.1.0/24 via 172.18.0.5 dev eth0 proto kernel
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.4
default via 172.18.0.1 dev eth0
10.0.0.0/24 via 172.18.0.2 dev eth0 proto kernel
10.0.1.0/24 via 172.18.0.3 dev eth0 proto kernel
10.1.0.0/24 via 172.18.0.4 dev eth0 proto kernel
10.1.1.0/24 via 10.1.1.122 dev cilium_host proto kernel src 10.1.1.122
10.1.1.122 dev cilium_host proto kernel scope link
172.18.0.0/16 dev eth0 proto kernel scope link src 172.18.0.5
- ClusterMesh 연결 후, 각 클러스터의 노드 라우팅 테이블에 상대 클러스터의 PodCIDR 자동 주입 확인
- 결과적으로, 양쪽 클러스터 Pod 간 직접 통신 가능 상태로 전환됨
👁️ Hubble enable
1. Cilium Helm 저장소 추가 및 업데이트
1
2
helm repo add cilium https://helm.cilium.io/
helm repo update
✅ 출력
1
2
3
4
5
"cilium" has been added to your repositories
Hang tight while we grab the latest from your chart repositories...
...Successfully got an update from the "cilium" chart repository
Update Complete. ⎈Happy Helming!⎈
2. West 클러스터에 Hubble 활성화
1
2
3
helm upgrade cilium cilium/cilium --version 1.17.6 --namespace kube-system --reuse-values \
--set hubble.enabled=true --set hubble.relay.enabled=true --set hubble.ui.enabled=true \
--set hubble.ui.service.type=NodePort --set hubble.ui.service.nodePort=30001 --kube-context kind-west
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
Release "cilium" has been upgraded. Happy Helming!
NAME: cilium
LAST DEPLOYED: Sat Aug 16 19:29:04 2025
NAMESPACE: kube-system
STATUS: deployed
REVISION: 4
TEST SUITE: None
NOTES:
You have successfully installed Cilium with Hubble Relay and Hubble UI.
Your release version is 1.17.6.
For any further help, visit https://docs.cilium.io/en/v1.17/gettinghelp
3. West 클러스터 Cilium DaemonSet 재시작
1
2
3
4
kwest -n kube-system rollout restart ds/cilium
# 결과
daemonset.apps/cilium restarted
4. East 클러스터에 Hubble 활성화
1
2
3
helm upgrade cilium cilium/cilium --version 1.17.6 --namespace kube-system --reuse-values \
--set hubble.enabled=true --set hubble.relay.enabled=true --set hubble.ui.enabled=true \
--set hubble.ui.service.type=NodePort --set hubble.ui.service.nodePort=31001 --kube-context kind-east
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
Release "cilium" has been upgraded. Happy Helming!
NAME: cilium
LAST DEPLOYED: Sat Aug 16 19:30:52 2025
NAMESPACE: kube-system
STATUS: deployed
REVISION: 4
TEST SUITE: None
NOTES:
You have successfully installed Cilium with Hubble Relay and Hubble UI.
Your release version is 1.17.6.
For any further help, visit https://docs.cilium.io/en/v1.17/gettinghelp
5. East 클러스터 Cilium DaemonSet 재시작
1
2
3
4
kwest -n kube-system rollout restart ds/cilium
# 결과
daemonset.apps/cilium restarted
6. Hubble UI 접속 확인
↔️ west ↔ east 파드간 직접 통신(tcpdump 검증)
1. 테스트용 파드 배포 (west/east 각각)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
cat << EOF | kubectl apply --context kind-west -f -
apiVersion: v1
kind: Pod
metadata:
name: curl-pod
labels:
app: curl
spec:
containers:
- name: curl
image: nicolaka/netshoot
command: ["tail"]
args: ["-f", "/dev/null"]
terminationGracePeriodSeconds: 0
EOF
cat << EOF | kubectl apply --context kind-east -f -
apiVersion: v1
kind: Pod
metadata:
name: curl-pod
labels:
app: curl
spec:
containers:
- name: curl
image: nicolaka/netshoot
command: ["tail"]
args: ["-f", "/dev/null"]
terminationGracePeriodSeconds: 0
EOF
# 결과
pod/curl-pod created
pod/curl-pod created
2. 파드 상태 및 IP 확인
1
kwest get pod -A && keast get pod -A
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
NAMESPACE NAME READY STATUS RESTARTS AGE
default curl-pod 1/1 Running 0 55s
kube-system cilium-6l82v 1/1 Running 0 5m16s
kube-system cilium-envoy-5gpxx 1/1 Running 0 54m
kube-system cilium-envoy-skv7b 1/1 Running 0 54m
kube-system cilium-lrpcr 1/1 Running 0 5m16s
kube-system cilium-operator-7dbb574d5b-drtg2 1/1 Running 0 54m
kube-system clustermesh-apiserver-5cf45db9cc-2g847 2/2 Running 0 32m
kube-system clustermesh-apiserver-generate-certs-xvddz 0/1 Completed 0 7m53s
kube-system coredns-674b8bbfcf-kwxv5 1/1 Running 0 86m
kube-system coredns-674b8bbfcf-nb96t 1/1 Running 0 86m
kube-system etcd-west-control-plane 1/1 Running 0 86m
kube-system hubble-relay-5dcd46f5c-rqrvl 1/1 Running 0 7m54s
kube-system hubble-ui-76d4965bb6-xkn8k 2/2 Running 0 7m54s
kube-system kube-apiserver-west-control-plane 1/1 Running 0 86m
kube-system kube-controller-manager-west-control-plane 1/1 Running 0 86m
kube-system kube-scheduler-west-control-plane 1/1 Running 0 86m
local-path-storage local-path-provisioner-7dc846544d-jrdw8 1/1 Running 0 86m
NAMESPACE NAME READY STATUS RESTARTS AGE
default curl-pod 1/1 Running 0 55s
kube-system cilium-7z2kz 1/1 Running 0 24m
kube-system cilium-envoy-mrzw8 1/1 Running 0 53m
kube-system cilium-envoy-vq5r7 1/1 Running 0 53m
kube-system cilium-operator-867f8dc978-44zqb 1/1 Running 0 53m
kube-system cilium-thtxk 1/1 Running 0 24m
kube-system clustermesh-apiserver-5cf45db9cc-7wfwz 2/2 Running 0 31m
kube-system clustermesh-apiserver-generate-certs-5csbq 0/1 Completed 0 6m4s
kube-system coredns-674b8bbfcf-2tm2l 1/1 Running 0 85m
kube-system coredns-674b8bbfcf-c9qsg 1/1 Running 0 85m
kube-system etcd-east-control-plane 1/1 Running 0 85m
kube-system hubble-relay-5dcd46f5c-6qzn7 1/1 Running 0 6m5s
kube-system hubble-ui-76d4965bb6-jg78b 2/2 Running 0 6m5s
kube-system kube-apiserver-east-control-plane 1/1 Running 0 85m
kube-system kube-controller-manager-east-control-plane 1/1 Running 0 85m
kube-system kube-scheduler-east-control-plane 1/1 Running 0 85m
local-path-storage local-path-provisioner-7dc846544d-mwfdc 1/1 Running 0 85m
1
kwest get pod -owide && keast get pod -owide
✅ 출력
1
2
3
4
5
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
curl-pod 1/1 Running 0 114s 10.0.1.12 west-worker <none> <none>
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
curl-pod 1/1 Running 0 114s 10.1.1.67 east-worker <none> <none>
3. west → east 파드간 Ping 테스트
1
kubectl exec -it curl-pod --context kind-west -- ping 10.1.1.67
✅ 출력
1
2
3
4
5
6
7
PING 10.1.1.67 (10.1.1.67) 56(84) bytes of data.
64 bytes from 10.1.1.67: icmp_seq=1 ttl=62 time=0.070 ms
64 bytes from 10.1.1.67: icmp_seq=2 ttl=62 time=0.188 ms
64 bytes from 10.1.1.67: icmp_seq=3 ttl=62 time=0.093 ms
64 bytes from 10.1.1.67: icmp_seq=4 ttl=62 time=0.120 ms
64 bytes from 10.1.1.67: icmp_seq=5 ttl=62 time=0.153 ms
....
- 정상적으로 응답(Reply) 수신 → Pod 간 직접 통신 가능 확인
4. 목적지 파드에서 tcpdump 확인
east 파드 내부에서 tcpdump 실행
1
kubectl exec -it curl-pod --context kind-east -- tcpdump -i eth0 -nn
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
10:43:50.833580 IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 199, length 64
10:43:50.833627 IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 199, length 64
10:43:51.857541 IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 200, length 64
10:43:51.857578 IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 200, length 64
10:43:52.880956 IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 201, length 64
10:43:52.881075 IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 201, length 64
10:43:53.904522 IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 202, length 64
10:43:53.904555 IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 202, length 64
10:43:54.928512 IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 203, length 64
10:43:54.928540 IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 203, length 64
10:43:55.952560 IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 204, length 64
10:43:55.952593 IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 204, length 64
10:43:56.976694 IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 205, length 64
10:43:56.976763 IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 205, length 64
...
- west 파드의 IP(
10.0.1.12)에서 직접 들어오는 ICMP 요청 및 응답 확인 - NAT 변환 없이 Pod ↔ Pod 다이렉트 라우팅 검증
5. 목적지 클러스터 노드에서 tcpdump 확인
east-control-plane, east-worker 노드에서 tcpdump 실행
1
docker exec -it east-control-plane tcpdump -i any icmp -nn
✅ 출력
1
2
3
tcpdump: data link type LINUX_SLL2
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
1
docker exec -it east-worker tcpdump -i any icmp -nn
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
tcpdump: data link type LINUX_SLL2
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on any, link-type LINUX_SLL2 (Linux cooked v2), snapshot length 262144 bytes
10:46:31.473504 eth0 In IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 356, length 64
10:46:31.473530 lxccd8da9e761ca In IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 356, length 64
10:46:31.473540 eth0 Out IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 356, length 64
10:46:31.988151 eth0 In IP 172.18.0.1 > 172.18.0.5: ICMP 172.18.0.1 udp port 53 unreachable, length 53
10:46:32.496507 eth0 In IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 357, length 64
10:46:32.496535 lxccd8da9e761ca In IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 357, length 64
10:46:32.496545 eth0 Out IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 357, length 64
10:46:33.488946 eth0 In IP 172.18.0.1 > 172.18.0.5: ICMP 172.18.0.1 udp port 53 unreachable, length 53
10:46:33.520513 eth0 In IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 358, length 64
10:46:33.520542 lxccd8da9e761ca In IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 358, length 64
10:46:33.520554 eth0 Out IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 358, length 64
10:46:33.569979 eth0 In IP 172.18.0.1 > 172.18.0.5: ICMP 172.18.0.1 udp port 53 unreachable, length 53
10:46:34.544531 eth0 In IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 359, length 64
10:46:34.544557 lxccd8da9e761ca In IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 359, length 64
10:46:34.544569 eth0 Out IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 359, length 64
10:46:34.990071 eth0 In IP 172.18.0.1 > 172.18.0.5: ICMP 172.18.0.1 udp port 53 unreachable, length 53
10:46:35.568525 eth0 In IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 360, length 64
10:46:35.568555 lxccd8da9e761ca In IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 360, length 64
10:46:35.568573 eth0 Out IP 10.1.1.67 > 10.0.1.12: ICMP echo reply, id 2, seq 360, length 64
10:46:36.492093 eth0 In IP 172.18.0.1 > 172.18.0.5: ICMP 172.18.0.1 udp port 53 unreachable, length 53
10:46:36.572589 eth0 In IP 172.18.0.1 > 172.18.0.5: ICMP 172.18.0.1 udp port 53 unreachable, length 53
10:46:36.593535 eth0 In IP 10.0.1.12 > 10.1.1.67: ICMP echo request, id 2, seq 361, length 64
...
- west 파드에서 들어온 패킷이 노드에서 직접 파드로 전달되는 과정 확인
- 중간 NAT 게이트웨이나 터널링 없이 direct routing 동작 검증
⚖️ Load-balancing & Service Discovery
1. 글로벌 서비스 배포 (west / east 클러스터)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
cat << EOF | kubectl apply --context kind-west -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: webpod
spec:
replicas: 2
selector:
matchLabels:
app: webpod
template:
metadata:
labels:
app: webpod
spec:
affinity:
podAntiAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
- labelSelector:
matchExpressions:
- key: app
operator: In
values:
- sample-app
topologyKey: "kubernetes.io/hostname"
containers:
- name: webpod
image: traefik/whoami
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: webpod
labels:
app: webpod
annotations:
service.cilium.io/global: "true"
spec:
selector:
app: webpod
ports:
- protocol: TCP
port: 80
targetPort: 80
type: ClusterIP
EOF
# 결과
deployment.apps/webpod created
service/webpod created
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
cat << EOF | kubectl apply --context kind-east -f -
apiVersion: apps/v1
kind: Deployment
metadata:
name: webpod
spec:
replicas: 2
selector:
matchLabels:
app: webpod
template:
metadata:
labels:
app: webpod
spec:
affinity:
podAntiAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
- labelSelector:
matchExpressions:
- key: app
operator: In
values:
- sample-app
topologyKey: "kubernetes.io/hostname"
containers:
- name: webpod
image: traefik/whoami
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: webpod
labels:
app: webpod
annotations:
service.cilium.io/global: "true"
spec:
selector:
app: webpod
ports:
- protocol: TCP
port: 80
targetPort: 80
type: ClusterIP
EOF
# 결과
deployment.apps/webpod created
service/webpod created
webpodDeployment과 Service를 양쪽 클러스터에 동일하게 배포service.cilium.io/global: "true"어노테이션을 추가하여 글로벌 서비스로 등록- ClusterIP 타입 서비스 생성, 포트 80 노출
2. 엔드포인트 확인
1
kwest get svc,ep webpod && keast get svc,ep webpod
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
Warning: v1 Endpoints is deprecated in v1.33+; use discovery.k8s.io/v1 EndpointSlice
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/webpod ClusterIP 10.2.167.94 <none> 80/TCP 118s
NAME ENDPOINTS AGE
endpoints/webpod 10.0.1.136:80,10.0.1.69:80 118s
Warning: v1 Endpoints is deprecated in v1.33+; use discovery.k8s.io/v1 EndpointSlice
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/webpod ClusterIP 10.3.128.46 <none> 80/TCP 56s
NAME ENDPOINTS AGE
endpoints/webpod 10.1.1.6:80,10.1.1.95:80 56s
- west →
10.0.1.136,10.0.1.69 - east →
10.1.1.6,10.1.1.95 - 두 클러스터 모두
webpod서비스가 존재하고, 각각의 Pod IP들이 글로벌 서비스에 등록됨
3. 글로벌 서비스 매핑 확인 (west)
1
kwest exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
ID Frontend Service Type Backend
1 10.2.0.1:443/TCP ClusterIP 1 => 172.18.0.2:6443/TCP (active)
2 10.2.182.189:443/TCP ClusterIP 1 => 172.18.0.3:4244/TCP (active)
3 10.2.0.10:53/UDP ClusterIP 1 => 10.0.1.177:53/UDP (active)
2 => 10.0.1.115:53/UDP (active)
4 10.2.0.10:53/TCP ClusterIP 1 => 10.0.1.177:53/TCP (active)
2 => 10.0.1.115:53/TCP (active)
5 10.2.0.10:9153/TCP ClusterIP 1 => 10.0.1.177:9153/TCP (active)
2 => 10.0.1.115:9153/TCP (active)
6 10.2.126.217:2379/TCP ClusterIP 1 => 10.0.1.8:2379/TCP (active)
7 172.18.0.3:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
9 10.2.1.9:80/TCP ClusterIP 1 => 10.0.1.120:4245/TCP (active)
10 10.2.233.237:80/TCP ClusterIP 1 => 10.0.1.158:8081/TCP (active)
11 172.18.0.3:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
12 0.0.0.0:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
13 10.2.167.94:80/TCP ClusterIP 1 => 10.0.1.69:80/TCP (active)
2 => 10.0.1.136:80/TCP (active)
3 => 10.1.1.6:80/TCP (active)
4 => 10.1.1.95:80/TCP (active)
webpod (10.2.167.94:80/TCP)→ west, east 클러스터의 모든 Pod IP로 분산- west :
10.0.1.69:80,10.0.1.136:80 - east :
10.1.1.6:80,10.1.1.95:80
- west :
4. 글로벌 서비스 매핑 확인 (east)
1
keast exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
ID Frontend Service Type Backend
1 10.3.0.1:443/TCP ClusterIP 1 => 172.18.0.4:6443/TCP (active)
2 10.3.107.176:443/TCP ClusterIP 1 => 172.18.0.5:4244/TCP (active)
3 10.3.0.10:9153/TCP ClusterIP 1 => 10.1.1.45:9153/TCP (active)
2 => 10.1.1.21:9153/TCP (active)
4 10.3.0.10:53/UDP ClusterIP 1 => 10.1.1.45:53/UDP (active)
2 => 10.1.1.21:53/UDP (active)
5 10.3.0.10:53/TCP ClusterIP 1 => 10.1.1.45:53/TCP (active)
2 => 10.1.1.21:53/TCP (active)
6 10.3.173.28:2379/TCP ClusterIP 1 => 10.1.1.62:2379/TCP (active)
7 172.18.0.5:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
9 10.3.54.60:80/TCP ClusterIP 1 => 10.1.1.198:4245/TCP (active)
10 10.3.1.28:80/TCP ClusterIP 1 => 10.1.1.236:8081/TCP (active)
11 172.18.0.5:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
12 0.0.0.0:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
13 10.3.128.46:80/TCP ClusterIP 1 => 10.0.1.69:80/TCP (active)
2 => 10.0.1.136:80/TCP (active)
3 => 10.1.1.6:80/TCP (active)
4 => 10.1.1.95:80/TCP (active)
- 동일하게
cilium service list --clustermesh-affinity실행 webpod (10.3.128.46:80/TCP)→ 동일한 4개 엔드포인트로 분산
5. 크로스 클러스터 호출
1
2
kubectl exec -it curl-pod --context kind-west -- sh -c 'while true; do curl -s --connect-timeout 1 webpod ; sleep 1; echo "---"; done;'
kubectl exec -it curl-pod --context kind-east -- sh -c 'while true; do curl -s --connect-timeout 1 webpod ; sleep 1; echo "---"; done;'
- west의 curl-pod → webpod 호출 시 west + east 엔드포인트로 로드밸런싱
- east의 curl-pod → webpod 호출 시 east + west 엔드포인트로 로드밸런싱
- 즉, 서비스 VIP 호출만으로 두 클러스터의 Pod 모두 대상이 됨
6. 레플리카 수 축소 (west 2 → 1)
1
2
3
4
kwest scale deployment webpod --replicas 1
# 결과
deployment.apps/webpod scaled
1
kwest exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
ID Frontend Service Type Backend
1 10.2.0.1:443/TCP ClusterIP 1 => 172.18.0.2:6443/TCP (active)
2 10.2.182.189:443/TCP ClusterIP 1 => 172.18.0.3:4244/TCP (active)
3 10.2.0.10:53/UDP ClusterIP 1 => 10.0.1.177:53/UDP (active)
2 => 10.0.1.115:53/UDP (active)
4 10.2.0.10:53/TCP ClusterIP 1 => 10.0.1.177:53/TCP (active)
2 => 10.0.1.115:53/TCP (active)
5 10.2.0.10:9153/TCP ClusterIP 1 => 10.0.1.177:9153/TCP (active)
2 => 10.0.1.115:9153/TCP (active)
6 10.2.126.217:2379/TCP ClusterIP 1 => 10.0.1.8:2379/TCP (active)
7 172.18.0.3:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
9 10.2.1.9:80/TCP ClusterIP 1 => 10.0.1.120:4245/TCP (active)
10 10.2.233.237:80/TCP ClusterIP 1 => 10.0.1.158:8081/TCP (active)
11 172.18.0.3:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
12 0.0.0.0:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
13 10.2.167.94:80/TCP ClusterIP 1 => 10.0.1.69:80/TCP (active)
2 => 10.1.1.6:80/TCP (active)
3 => 10.1.1.95:80/TCP (active)
- west에 남은 Pod 1개 + east의 Pod 2개로 서비스 트래픽이 분산됨
- 글로벌 서비스는 Pod 개수에 따라 자동 반영
1
keast exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
ID Frontend Service Type Backend
1 10.3.0.1:443/TCP ClusterIP 1 => 172.18.0.4:6443/TCP (active)
2 10.3.107.176:443/TCP ClusterIP 1 => 172.18.0.5:4244/TCP (active)
3 10.3.0.10:9153/TCP ClusterIP 1 => 10.1.1.45:9153/TCP (active)
2 => 10.1.1.21:9153/TCP (active)
4 10.3.0.10:53/UDP ClusterIP 1 => 10.1.1.45:53/UDP (active)
2 => 10.1.1.21:53/UDP (active)
5 10.3.0.10:53/TCP ClusterIP 1 => 10.1.1.45:53/TCP (active)
2 => 10.1.1.21:53/TCP (active)
6 10.3.173.28:2379/TCP ClusterIP 1 => 10.1.1.62:2379/TCP (active)
7 172.18.0.5:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
9 10.3.54.60:80/TCP ClusterIP 1 => 10.1.1.198:4245/TCP (active)
10 10.3.1.28:80/TCP ClusterIP 1 => 10.1.1.236:8081/TCP (active)
11 172.18.0.5:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
12 0.0.0.0:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
13 10.3.128.46:80/TCP ClusterIP 1 => 10.0.1.69:80/TCP (active)
2 => 10.1.1.6:80/TCP (active)
3 => 10.1.1.95:80/TCP (active)
7. 레플리카 0 (west)
1
2
3
4
kwest scale deployment webpod --replicas 0
# 결과
deployment.apps/webpod scaled
- west의 모든 Pod 삭제 후에도 서비스 정상 동작
1
kwest exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
ID Frontend Service Type Backend
1 10.2.0.1:443/TCP ClusterIP 1 => 172.18.0.2:6443/TCP (active)
2 10.2.182.189:443/TCP ClusterIP 1 => 172.18.0.3:4244/TCP (active)
3 10.2.0.10:53/UDP ClusterIP 1 => 10.0.1.177:53/UDP (active)
2 => 10.0.1.115:53/UDP (active)
4 10.2.0.10:53/TCP ClusterIP 1 => 10.0.1.177:53/TCP (active)
2 => 10.0.1.115:53/TCP (active)
5 10.2.0.10:9153/TCP ClusterIP 1 => 10.0.1.177:9153/TCP (active)
2 => 10.0.1.115:9153/TCP (active)
6 10.2.126.217:2379/TCP ClusterIP 1 => 10.0.1.8:2379/TCP (active)
7 172.18.0.3:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
9 10.2.1.9:80/TCP ClusterIP 1 => 10.0.1.120:4245/TCP (active)
10 10.2.233.237:80/TCP ClusterIP 1 => 10.0.1.158:8081/TCP (active)
11 172.18.0.3:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
12 0.0.0.0:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
13 10.2.167.94:80/TCP ClusterIP 1 => 10.1.1.6:80/TCP (active)
2 => 10.1.1.95:80/TCP (active)
1
keast exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
ID Frontend Service Type Backend
1 10.3.0.1:443/TCP ClusterIP 1 => 172.18.0.4:6443/TCP (active)
2 10.3.107.176:443/TCP ClusterIP 1 => 172.18.0.5:4244/TCP (active)
3 10.3.0.10:9153/TCP ClusterIP 1 => 10.1.1.45:9153/TCP (active)
2 => 10.1.1.21:9153/TCP (active)
4 10.3.0.10:53/UDP ClusterIP 1 => 10.1.1.45:53/UDP (active)
2 => 10.1.1.21:53/UDP (active)
5 10.3.0.10:53/TCP ClusterIP 1 => 10.1.1.45:53/TCP (active)
2 => 10.1.1.21:53/TCP (active)
6 10.3.173.28:2379/TCP ClusterIP 1 => 10.1.1.62:2379/TCP (active)
7 172.18.0.5:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
9 10.3.54.60:80/TCP ClusterIP 1 => 10.1.1.198:4245/TCP (active)
10 10.3.1.28:80/TCP ClusterIP 1 => 10.1.1.236:8081/TCP (active)
11 172.18.0.5:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
12 0.0.0.0:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
13 10.3.128.46:80/TCP ClusterIP 1 => 10.1.1.6:80/TCP (active)
2 => 10.1.1.95:80/TCP (active)
- east의 Pod 엔드포인트만 살아있으므로, 트래픽은 자동으로 east 클러스터로 라우팅
8. 레플리카 원복
1
2
kwest scale deployment webpod --replicas 2
deployment.apps/webpod scaled
- west의 레플리카 다시 2개로 복구
- 글로벌 서비스 엔드포인트 목록에 다시 west Pod IP가 추가
🎯 Service Affinity
1. 서비스 어노테이션 설정
1
2
3
4
5
6
7
kwest annotate service webpod service.cilium.io/affinity=local --overwrite
# 결과
service/webpod annotated
keast annotate service webpod service.cilium.io/affinity=local --overwrite
# 결과
service/webpod annotated
1
2
3
4
5
6
7
8
9
10
11
kwest describe svc webpod | grep Annotations -A3
Annotations: service.cilium.io/affinity: local
service.cilium.io/global: true
Selector: app=webpod
Type: ClusterIP
keast describe svc webpod | grep Annotations -A3
Annotations: service.cilium.io/affinity: local
service.cilium.io/global: true
Selector: app=webpod
Type: ClusterIP
- west, east 클러스터의
webpod서비스에service.cilium.io/affinity=local어노테이션 추가
2. Affinity 동작 확인 (west)
1
kwest exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
ID Frontend Service Type Backend
1 10.2.0.1:443/TCP ClusterIP 1 => 172.18.0.2:6443/TCP (active)
2 10.2.182.189:443/TCP ClusterIP 1 => 172.18.0.3:4244/TCP (active)
3 10.2.0.10:53/UDP ClusterIP 1 => 10.0.1.177:53/UDP (active)
2 => 10.0.1.115:53/UDP (active)
4 10.2.0.10:53/TCP ClusterIP 1 => 10.0.1.177:53/TCP (active)
2 => 10.0.1.115:53/TCP (active)
5 10.2.0.10:9153/TCP ClusterIP 1 => 10.0.1.177:9153/TCP (active)
2 => 10.0.1.115:9153/TCP (active)
6 10.2.126.217:2379/TCP ClusterIP 1 => 10.0.1.8:2379/TCP (active)
7 172.18.0.3:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
9 10.2.1.9:80/TCP ClusterIP 1 => 10.0.1.120:4245/TCP (active)
10 10.2.233.237:80/TCP ClusterIP 1 => 10.0.1.158:8081/TCP (active)
11 172.18.0.3:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
12 0.0.0.0:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
13 10.2.167.94:80/TCP ClusterIP 1 => 10.1.1.6:80/TCP (active)
2 => 10.1.1.95:80/TCP (active)
3 => 10.0.1.159:80/TCP (active) (preferred)
4 => 10.0.1.107:80/TCP (active) (preferred)
webpod서비스 엔드포인트에서 로컬 Pod IP(10.0.1.x)가(preferred)로 표시- 즉, 클러스터 내부 클라이언트 요청은 기본적으로 로컬 엔드포인트로 우선 라우팅됨
3. Affinity 동작 확인 (east)
1
keast exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
ID Frontend Service Type Backend
1 10.3.0.1:443/TCP ClusterIP 1 => 172.18.0.4:6443/TCP (active)
2 10.3.107.176:443/TCP ClusterIP 1 => 172.18.0.5:4244/TCP (active)
3 10.3.0.10:9153/TCP ClusterIP 1 => 10.1.1.45:9153/TCP (active)
2 => 10.1.1.21:9153/TCP (active)
4 10.3.0.10:53/UDP ClusterIP 1 => 10.1.1.45:53/UDP (active)
2 => 10.1.1.21:53/UDP (active)
5 10.3.0.10:53/TCP ClusterIP 1 => 10.1.1.45:53/TCP (active)
2 => 10.1.1.21:53/TCP (active)
6 10.3.173.28:2379/TCP ClusterIP 1 => 10.1.1.62:2379/TCP (active)
7 172.18.0.5:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
9 10.3.54.60:80/TCP ClusterIP 1 => 10.1.1.198:4245/TCP (active)
10 10.3.1.28:80/TCP ClusterIP 1 => 10.1.1.236:8081/TCP (active)
11 172.18.0.5:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
12 0.0.0.0:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
13 10.3.128.46:80/TCP ClusterIP 1 => 10.1.1.6:80/TCP (active) (preferred)
2 => 10.1.1.95:80/TCP (active) (preferred)
3 => 10.0.1.159:80/TCP (active)
4 => 10.0.1.107:80/TCP (active)
- east 클러스터에서도 동일하게 로컬 Pod IP(
10.1.1.x)가(preferred)로 표시 - 글로벌 서비스지만, 자신의 클러스터에 있는 Pod → 최우선 처리
4. 서비스 호출 테스트
1
2
kubectl exec -it curl-pod --context kind-west -- sh -c 'while true; do curl -s --connect-timeout 1 webpod ; sleep 1; echo "---"; done;'
kubectl exec -it curl-pod --context kind-east -- sh -c 'while true; do curl -s --connect-timeout 1 webpod ; sleep 1; echo "---"; done;'
- 서비스 호출이 동일 클러스터 내 엔드포인트로 집중됨
5. 레플리카 수 축소 (west 2 → 0)
1
2
kwest scale deployment webpod --replicas 0
deployment.apps/webpod scaled
- west 클러스터에서 모든
webpodPod 삭제
1
kwest exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
✅ 출력
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
ID Frontend Service Type Backend
1 10.2.0.1:443/TCP ClusterIP 1 => 172.18.0.2:6443/TCP (active)
2 10.2.182.189:443/TCP ClusterIP 1 => 172.18.0.3:4244/TCP (active)
3 10.2.0.10:53/UDP ClusterIP 1 => 10.0.1.177:53/UDP (active)
2 => 10.0.1.115:53/UDP (active)
4 10.2.0.10:53/TCP ClusterIP 1 => 10.0.1.177:53/TCP (active)
2 => 10.0.1.115:53/TCP (active)
5 10.2.0.10:9153/TCP ClusterIP 1 => 10.0.1.177:9153/TCP (active)
2 => 10.0.1.115:9153/TCP (active)
6 10.2.126.217:2379/TCP ClusterIP 1 => 10.0.1.8:2379/TCP (active)
7 172.18.0.3:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.0.1.8:2379/TCP (active)
9 10.2.1.9:80/TCP ClusterIP 1 => 10.0.1.120:4245/TCP (active)
10 10.2.233.237:80/TCP ClusterIP 1 => 10.0.1.158:8081/TCP (active)
11 172.18.0.3:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
12 0.0.0.0:30001/TCP NodePort 1 => 10.0.1.158:8081/TCP (active)
13 10.2.167.94:80/TCP ClusterIP 1 => 10.1.1.6:80/TCP (active)
2 => 10.1.1.95:80/TCP (active)
- affinity 정책상 로컬 Pod를 선호하지만, 로컬에 Pod가 없으므로 원격 east Pod로 요청 전달
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
keast exec -it -n kube-system ds/cilium -c cilium-agent -- cilium service list --clustermesh-affinity
ID Frontend Service Type Backend
1 10.3.0.1:443/TCP ClusterIP 1 => 172.18.0.4:6443/TCP (active)
2 10.3.107.176:443/TCP ClusterIP 1 => 172.18.0.5:4244/TCP (active)
3 10.3.0.10:9153/TCP ClusterIP 1 => 10.1.1.45:9153/TCP (active)
2 => 10.1.1.21:9153/TCP (active)
4 10.3.0.10:53/UDP ClusterIP 1 => 10.1.1.45:53/UDP (active)
2 => 10.1.1.21:53/UDP (active)
5 10.3.0.10:53/TCP ClusterIP 1 => 10.1.1.45:53/TCP (active)
2 => 10.1.1.21:53/TCP (active)
6 10.3.173.28:2379/TCP ClusterIP 1 => 10.1.1.62:2379/TCP (active)
7 172.18.0.5:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
8 0.0.0.0:32379/TCP NodePort 1 => 10.1.1.62:2379/TCP (active)
9 10.3.54.60:80/TCP ClusterIP 1 => 10.1.1.198:4245/TCP (active)
10 10.3.1.28:80/TCP ClusterIP 1 => 10.1.1.236:8081/TCP (active)
11 172.18.0.5:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
12 0.0.0.0:31001/TCP NodePort 1 => 10.1.1.236:8081/TCP (active)
13 10.3.128.46:80/TCP ClusterIP 1 => 10.1.1.6:80/TCP (active) (preferred)
2 => 10.1.1.95:80/TCP (active) (preferred)
- east 클러스터는 여전히 로컬 Pod가 살아있어 자신의 Pod로 우선 응답
6. 원복 (west replicas=2)
1
2
kwest scale deployment webpod --replicas 2
deployment.apps/webpod scaled
- west에 다시 2개의 Pod 생성 → 로컬 Pod IP가 다시
(preferred)로 표시됨 - 서비스 호출 시 로컬 우선 정책이 다시 적용됨